Author: Robert Parker
Phase Three: Website Content and Maliciousness Assessment
After analyzing domain and infrastructure details, the next phase involves a safe and thorough assessment of the website's content to confirm its malicious nature and gather actionable intelligence.
A. Safe Content Review
It is imperative to reiterate that suspicious URLs should never be visited directly on a standard web browser on a production machine due to the inherent risks of malware or system compromise. Instead, specialized online URL scanners and sandboxing services are to be utilized for safe analysis. The private scanning sandboxing engine within Google Threat Intelligence executes the URL in an isolated environment, providing screenshots, phishing/scam classifications, and technical details without risk to the analyst's workstation.
Web archiving services like the Wayback Machine (archive.org/web) and archive.is, are invaluable for forensic analysis. These services provide historical snapshots of websites, allowing investigators to track changes over time, verify a site's original purpose, and identify if a legitimate domain has been repurposed for fraudulent activities. Phishing sites are often designed to be ephemeral and dynamic, quickly changing their content or disappearing entirely to evade detection and takedown efforts. Web archiving services provide a crucial forensic capability to document the malicious content at the precise time of discovery, even if the live site is subsequently altered or taken offline by the attacker. This historical context is invaluable for building a comprehensive and indisputable evidence package for takedown requests and for understanding the evolving methodologies of threat actors.
During the safe content review, several key indicators should be scrutinized:
- Brand Impersonation: Look for direct clones of legitimate websites, unauthorized use of corporate logos, and overall brand impersonation, where the malicious site attempts to visually replicate a trusted entity.
- Deceptive Elements: Identify suspicious embedded links that lead to unexpected destinations, unauthorized redirects to other domains, and intrusive pop-ups that immediately request personal information upon landing on the page.
- Malware Indicators: Look for signs of malware distribution, such as drive-by downloads where malicious software is installed without explicit user interaction, or malicious files disguised as legitimate updates or documents (.exe files). Does submission of the URL into a sandbox indicate any malicious activity or drive-by downloads? Do any suspicious redirects occur in the sandbox reports?
- Quality Assessment: Evaluate the overall quality of the website. Red flags include poor grammar, spelling errors, low resolution images, awkward design layouts, and a conspicuous lack of an "About Us" page or comprehensive contact information, which are typically hallmarks of legitimate businesses.
B. IP Address Reputation and Hosting Provider Identification
Understanding the IP address and its hosting environment is crucial for identifying the responsible parties for a takedown.
Determining IP Address Geolocation, ASN, and ISP: Utilize functionality within Google Threat Intelligence which can provide detailed IP location, Autonomous System Number (ASN), and Internet Service Provider (ISP) information, as this helps in understanding the hosting environment and potential jurisdiction.
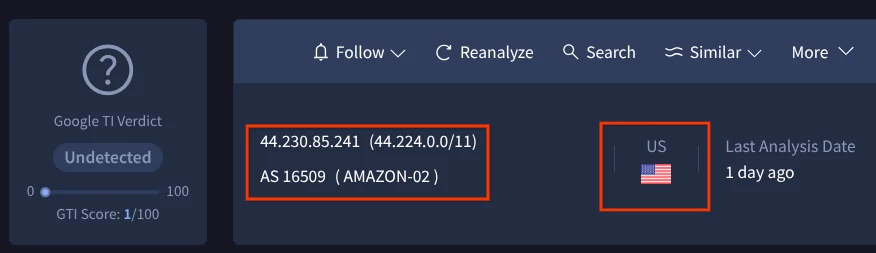
Google Threat Intelligence showing information about an IP Address (ASN, Country, etc.)
Identifying the Hosting Provider: Once the IP address is known, use functionality built into Google Threat Intelligence to directly identify the web hosting provider. It is also beneficial to cross reference the IP address with self published IP ranges of major cloud providers (Amazon AWS, Google Cloud) to determine if the site is hosted on a common cloud infrastructure. Additionally, performing WHOIS/RDAP lookups on the IP address itself can be effective; the "OrgName" or "descr" fields in the WHOIS output often directly identify the hosting provider or the organization responsible for that IP block.
Checking IP and Domain Blacklists: A crucial step is to check if the suspicious domain or its associated IP address is listed on known blacklists for spam, phishing, or malware distribution. This provides immediate validation of malicious intent.
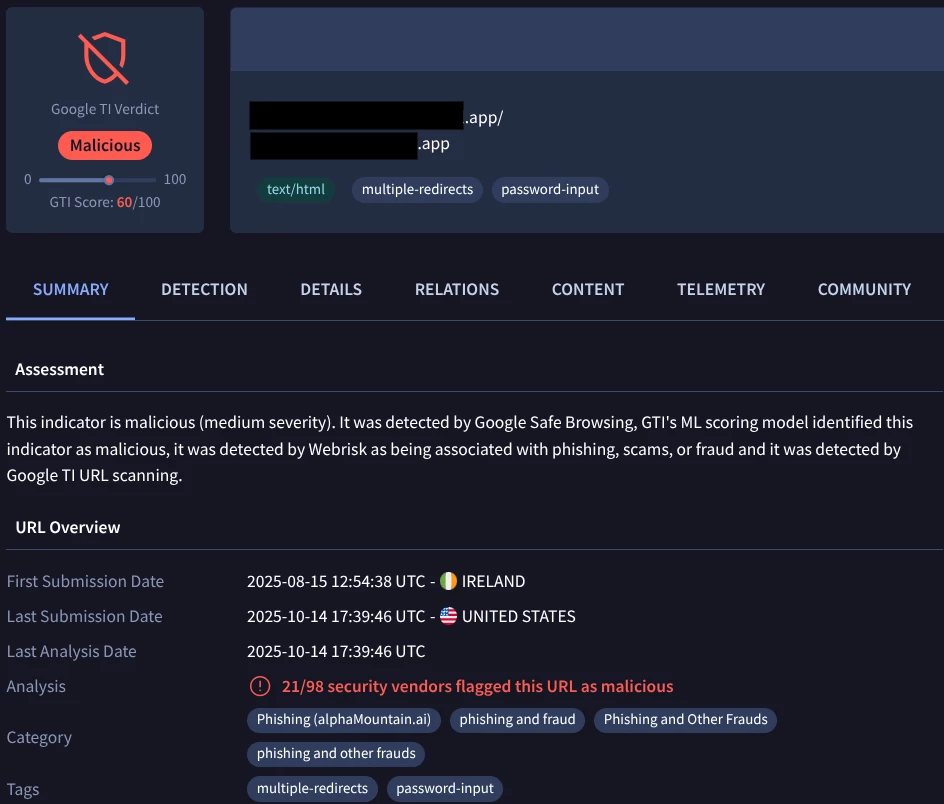
A malicious URL showing its assessment, categories, and related tags
The reputation of an IP address and the domains hosted on it are intrinsically linked. A malicious domain will almost certainly resolve to an IP address with a poor reputation or one that is already listed on a blacklist. Conversely, a blacklisted IP address is likely hosting multiple malicious domains. Blacklists serve not just as reactive indicators but as critical sources of real-time threat intelligence that can be integrated into security systems for proactive blocking. Checking multiple blacklists provides a more comprehensive and validated view of the threat actor's infrastructure and their history of abuse.
C. Leveraging Threat Intelligence Feeds and Tools
Integrating Data from Reputable Threat Intelligence Sources: Threat intelligence feeds provide real-time, actionable information on emerging attacks, including malicious IP addresses, domains, and malware signatures. Tools like ‘Check with VirusTotal’ within Google Threat Intelligence are excellent for aggregating data from dozens of antivirus engines, sandbox solutions, and security vendors, providing a comprehensive verdict on a URL or file. Google Threat Intelligence offers various different categorized threat lists, and IOC Feeds based on your licensing.
Correlating Findings with Known Indicators of Compromise (IOCs): A key step is to correlate the identified suspicious IP addresses, domains, and URLs with known Indicators of Compromise (IOCs) and documented adversary campaigns. The Entity Graph functionality within Google Threat Intelligence is specifically designed to aid in mapping adversary infrastructure and streamlining investigations, allowing analysts to connect disparate pieces of information to form a clearer picture of the threat or a campaign. This allows for a more comprehensive understanding of the threat actor's operations and footprint.
Entity relationship graph tools like the example illustrated below in Google Threat Intelligence are crucial for helping to identify and detect patterns in adversary infrastructure.
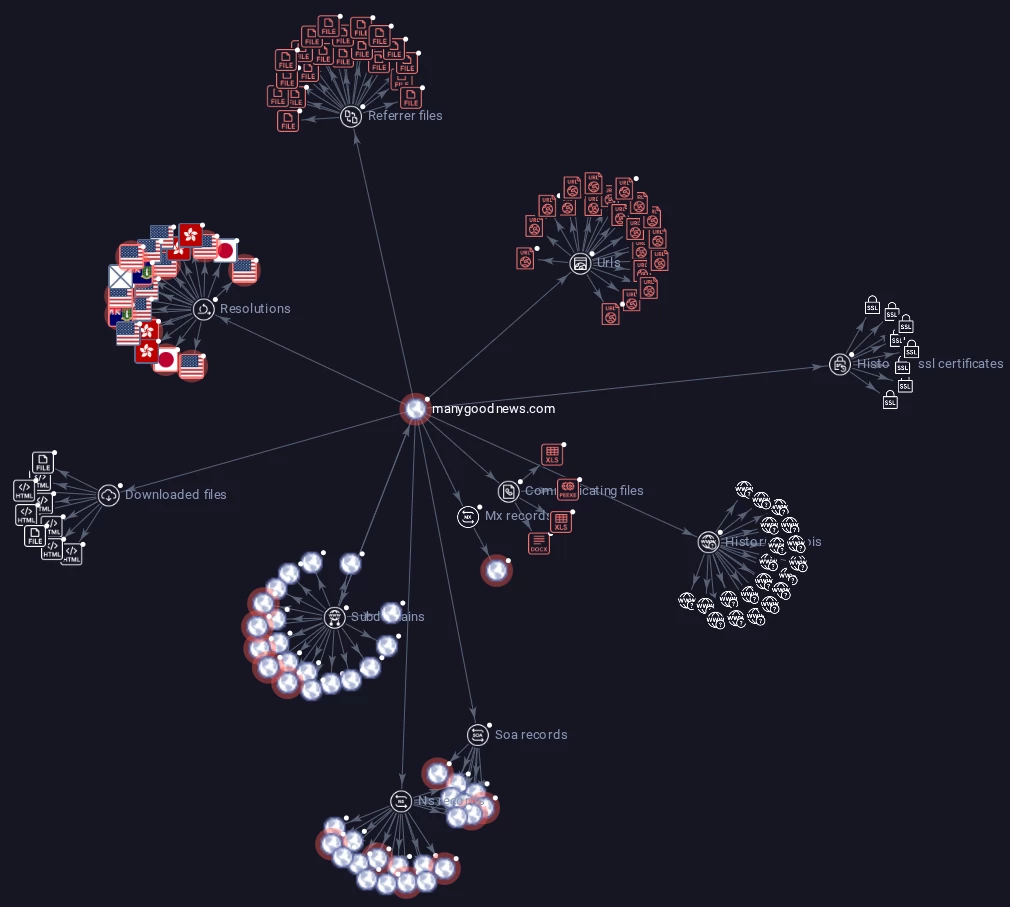
Entity graph illustrating relationships and data points for a sample domain being analyzed
The table below provides an overview of essential tools and their utility for phishing domain investigations. While this list contains tools, services, sites, or vendors outside of Google Threat Intelligence, it's important to have other tools within the toolkit of analysts and responders. This will make you a better analyst and help to mitigate biases when using a single source for Intelligence data. These can also be additional actions or steps to perform within a Security Orchestration and Automated Response (SOAR) playbook.
Additional Tools and Their Utility for Phishing Domain Investigations
| Resource Name | Category | Key Information Provided |
| Malware Verdict Aggregation
| Maliciousness verdict, associated files/URLs, IOCs | |
| URL Scanner | Screenshots, classification, hosting, IP, domain age, registrar | |
| URL Scanner | Screenshots, HTTP requests, redirects, associated IPs | |
| Website Security Checker | Malware, blacklisting status, security issues | |
| WHOIS/DNS Intelligence | Current/historical WHOIS, passive DNS, web content, risk score | |
| Certificate Transparency Logs | Certificate details, issuer, SANs, issuance dates | |
| IP/Domain Blacklist | Blacklisting status for spam, phishing, malware | |
| Phishing Database | Phishing status, submission details | |
| Malware URL Exchange | Malware URLs, associated IPs, domains | |
| IP Geolocation/Reputation | Geolocation, ASN, ISP, abuse reports | |
| Web Archiving Services | Past website content, design changes, domain history |
Phase Four: Takedown Determination and Action
Once sufficient evidence of malicious activity has been gathered, the next critical step is to determine if a takedown request is warranted and to initiate the appropriate actions.
A. Criteria for Takedown Request
Consolidating Evidence of Malicious Intent: Initiating a takedown request requires a robust and undeniable body of evidence demonstrating that the domain is fraudulent and warrants removal. Clear and verifiable evidence of malicious intent, such as credential theft (fake login pages designed to steal user credentials), malware distribution (driveby downloads, hosting of malicious files), or blatant brand impersonation/infringement (unauthorized logo use, direct cloning of a legitimate website), is essential. Identifying a look-alike domain that’s parked but shows no malicious indicators is typically not enough evidence to obtain a successful takedown. Without compelling evidence of malicious internet or clear Intellectual property infringement, takedown requests are frequently rejected or significantly delayed.
Assessing the Risk and Impact of the Malicious Domain: Before requesting a takedown, a rapid risk assessment should be conducted to determine the potential impact of the malicious domain. Considerations include whether the domain poses an immediate threat to users, could lead to significant customer confusion, cause reputational damage to the legitimate brand, or facilitate fraudulent financial transactions. Domains that closely resemble the legitimate brand or directly use its branding should be treated as high risk and prioritized for immediate takedown due to their potential for widespread deception and harm.
B. Evidence Collection for Takedown
A comprehensive and meticulously documented evidence package is required for a successful and expedited takedown. This minimizes ambiguity and facilitates prompt action from the responsible parties.
Detailed Requirements for a Takedown Package: The evidence package should typically include:
- Full URL(s): The exact, complete URL(s) of the malicious domain(s).
- Screenshots: High quality visual proof of the phishing page, specifically highlighting login fields, fake checkout pages, or clear instances of logo misuse and brand impersonation.
- Brand Impersonation/Logo Misuse: Explicit details and visual examples of how the legitimate brand is being exploited or infringed upon.
- Hosting and Registrar Information: Comprehensive details obtained from WHOIS lookups and IP analysis, including the domain registrar, hosting provider, and their respective abuse contacts.
- Passive DNS Data: Evidence of associated infrastructure, historical activity, or shared hosting that links the malicious domain to known threat actor networks.
- Malware Payloads/Redirections: Any evidence of malicious code, driveby downloads, or redirects observed during safe content review.
- User Complaints: Documented real world examples or reports from users detailing how the domain has caused problems or attempted to defraud them.
The table below provides a high level checklist for analysts to ensure all necessary evidence is systematically collected.
Evidence Requirements for Phishing Takedown Requests
| Evidence Type | Specific Details Required | Importance |
| Malicious URL | Full, exact URL(s) of the phishing site | Primary identifier for the malicious resource |
| Screenshots | High resolution images of phishing page, login fields, brand impersonation | Visual proof of malicious content and intent |
| WHOIS Data | Registrant, Registrar, Creation Date, Expiration Date | Identifies domain ownership and registrar for reporting |
| Passive DNS Data | Associated IPs, nameservers, historical resolutions | Maps adversary infrastructure, shared hosting |
| Malware Analysis Report | Hash, behavioral analysis, detected malware type | Confirms malware presence, aids in blocking |
| Brand Impersonation Details | Specific examples of logo misuse, cloned content | Demonstrates intent to deceive, legal infringement |
| User Complaints | Dates, descriptions of impact, affected users | Provides real world context, demonstrates harm |
C. Reporting and Takedown Process
Once the evidence package is complete, the process of reporting the malicious domain and initiating takedown procedures can begin.
The first point of contact for content removal is typically the hosting provider. Once identified (using IP lookups from Phase 2), their abuse department should be contacted. Most hosting providers maintain dedicated abuse contact email addresses (abuse@hostingprovider.com) or provide online reporting forms. When reporting, it is crucial to provide specific URLs and the compiled evidence, explicitly referencing the hosting provider's abuse policies that prohibit malicious activity. This direct approach often leads to faster content removal.
Simultaneously, the domain registrar should be informed. The registrar is identified using WHOIS lookups. Contact their abuse email (abuse@namecheap.com) or use their designated reporting form.
Working with a 3rd Party Take Down Service: Additionally, you may choose to work with a 3rd party service provider who assists with domain takedowns. Service partners like this include ZeroFox or Phishfort. Customers of Google Threat Intelligence who have also purchased Expertise on Demand (EoD) credits can utilize those credits for takedown services as well.
It is important to understand the nuance of takedown mechanisms, distinguishing between direct abuse reporting and formal legal avenues. Simple phishing (credential theft, malware distribution) can often be addressed through direct abuse reports to hosting providers and registrars, citing violations of their acceptable use policies. However, cases primarily involving brand infringement (trademark or copyright), parked domains, or other forms of cybersquatting often necessitate formal legal processes.
- UDRP (Uniform Domain Name Dispute Resolution Policy): This is a legal process applicable for cases of trademark infringement (cybersquatting). It requires demonstrating proof of trademark ownership, evidence of bad faith registration and use, and confusing similarity to the trademark. UDRP processes are often costly and time consuming.
- DMCA (Digital Millennium Copyright Act) Takedown Notices: Applicable for copyright infringement (unauthorized use of logos or copyrighted content). This requires a formal legal statement and proof of original ownership. DMCA takedowns can be faster than UDRP but may have inconsistent enforcement outside the United States.
This distinction implies that SOCs need to understand these legal nuances and may require collaboration with legal counsel, clearly differentiating between technical abuse and intellectual property disputes.
Escalation Paths When Initial Reports are Ignored: Takedown processes can be notoriously slow and, at times, unsuccessful, especially when dealing with less regulated regions or unresponsive providers. If the hosting provider is unresponsive, the issue should be escalated to the domain registrar. If the registrar also fails to act, an escalation path exists to the relevant domain registry (Public Interest Registry (PIR) for .org domains). While ICANN does not directly suspend domains, it oversees registrar compliance and can investigate failures to adhere to agreements.
Persistent and professional follow up is crucial throughout this process to ensure action is taken. The bureaucratic challenges and escalation matrix in takedowns highlight that they are not a simple, instantaneous process. They involve navigating a complex ecosystem of registrars, registries, hosting providers, and legal frameworks, each with varying response times, policies, and compliance levels. This necessitates a meticulously defined escalation matrix and persistent, professional follow up. It also illustrates the inherent value of specialized takedown services that have established relationships and automated workflows to navigate these complexities more efficiently, reducing the burden and toil on internal SOC teams.
Conclusion: Continuous Monitoring and Proactive Defense
A successful takedown of a phishing domain, while a critical achievement, is rarely a permanent solution. Threat actors are highly agile and will frequently spin up a new version of the site under a slightly altered domain, a different TLD, or on a new hosting platform within hours or days. This persistent reemergence of threats necessitates continuous monitoring to detect these reappearing threats and avoid a perpetual "digital whack-a-mole" scenario.
Tools like Digital Threat Monitoring inside Google Threat Intelligence offer ongoing monitoring and alerts for newly associated variations of monitored terms, providing early warning of reestablished malicious infrastructure. The "whack-a-mole" problem highlights the persistent and adaptive nature of the threat; along with the need to automate the responses to these alerts.
Continuous, automated monitoring of newly registered domains, DNS changes, and certificate issuances for brand look-alikes is not merely a follow up step but a fundamental, ongoing operational requirement to maintain effective brand protection and incident response.
This reinforces the necessity for organizations to invest in and leverage automated monitoring solutions to proactively identify and respond to emerging threats.
Given the sheer volume, increasing sophistication, and rapid evolution of phishing threats, a purely reactive incident response strategy is insufficient. A truly effective cybersecurity posture necessitates a strong emphasis on proactive defense and automation of these efforts once a repeatable process is defined and implemented by a Threat Intelligence team.
Recommendations for Proactive Measures:
- Employee Training: Implement regular, comprehensive security awareness training programs to educate employees on recognizing common phishing tactics, safe browsing practices, and the critical importance of reporting suspicious activity. Employees serve as a vital "human firewall." Newsletters or periodic communications out to employees with even a few of the commonly seen typosquatting tactics outlined on this report can help bring awareness to to being able to visually recognize tricks like combosquatting, TLD swaps, or character repeat techniques which are commonly used by threat actors to trick users.
- Proactive Domain Monitoring Services: Utilize DTM’s Domain Protection monitors for continuous domain risk monitoring and early detection of brand impersonation attempts. These services can identify typosquatted domains and other look-alikes as they are registered, often before they are widely used in attacks. Such proactive measures aim to prevent attacks or significantly minimize their impact even before they are fully launched, thereby catching domains as part of malicious campaigns before they are fully weaponized.
- Blocking Newly Seen Domains: Blocking newly seen or recently generated domains in your environment can help reduce the risk of recently created and setup phishing and look alike domains. While this may be subjected to false positives, having a policy around how quickly a newly seen domain can be accessed, along with an exception and unblocking process should also be implemented.
- Engage Early with Takedown Service Providers: Being previously contracted or setup with a takedown provider can help expedite the often difficult and convoluted process for performing a successful takedown request with registrars and/or hosting providers. These organizations will also help to ensure you’ve collected the correct evidence for your takedown request. Oftentimes, providers doing the proactive monitoring for domain protection services also provide takedown assistance services.
By understanding typosquatting techniques, along with integrating these proactive measures with a structured and thorough investigation and takedown procedure, organizations can build a more resilient defense against the persistent threat of phishing and investigating suspicious domains. When maturing a Domain Protection response process, organizations can continue to improve their threat intelligence operations and response maturity by working to further automate these actions outlined in this Adoption Guide using SOAR playbooks. We reviewed a lot of steps, tools, verifications, and intelligence to gather when reviewing suspicious domains. What if SOAR and API calls could bring all that to the case wall for an analyst so they can make a decision about allowing or blocking a domain just moments from initially getting assigned the case?
For the next part of this series, we will review how to automate several of these Domain Protection enrichment activities and analyst workflows using Google SecOps and the Digital Threat Monitor Integration for pulling in case alerts and performing initial enrichment, triage, and case assignment.
We hope this helps your teams develop a process for responding to suspicious domains, as well as think about how you’d want to automate your SOC response workflows when doing investigations on suspicious domain protection alerts from DTM.
