Today, I’m sharing how I built and deployed a Gemini Enterprise custom agent that uses Google Cloud Security Model Context Protocol (MCP) Tools and retrieval augmented generation (RAG) for a set of Runbooks for the Agentic SOC.
Those runbooks help turn a large language model agent into your companion SOC analyst. They provide the agent the knowledge needed for threat research, threat hunting, alert triage, containment, eradication, SOAR playbook execution, and much, much more.
While the runbooks provide the knowledge, the Google Cloud Security MCP servers provide the tools to perform that work. In my deployment, the MCP servers are packaged and built into the agent, so they are running right alongside it in Agent Engine. Google will be providing hosted versions of those agents soon, but you don’t have to wait—you can use these tools today.
I’ve previously shown these tools and runbooks running with ADK Web (that is Google’s Agent Development Kit) and I encourage you to check that out. This YouTube video showing ADK agent delegation during execution of an Incident Response Plan was a surprise hit!

ADK Runbooks - Malware IRP on YouTube
The two things that I’m showing you here today that are new are:
- Putting the runbooks into a Vertex AI RAG corpus
- Deploying the custom agent to Gemini Enterprise
I initially experimented with using a Google Drive datastore for the runbooks, but ultimately realized that RAG has got what Agents crave: embeddings. This allows the agent to perform semantic search—finding the most conceptually relevant procedures based on the intent of a query, not just matching the exact keywords. RAG “grounds agents in your business reality”[1].
Gemini Enterprise is the answer to all of the questions I’ve been asked about visibility, privacy, security, scaling, and governance. Up to now, my response had been that I’m showing a preview of these tools for early adopters. I do want to stress how important that is: developers need time with tools to gain proficiency, so giving us a safe space to experiment is critical to success.
For your production deployment, you want assurance that you can secure, audit, and meet compliance and data sovereignty requirements for your agents. Gemini Enterprise is all of that. You can read more about it in the docs and the FAQ.
With that said, what I’m showing is building and registering a custom ADK Agent in Gemini Enterprise, which is a cutting edge feature still in preview. There are pre-built agents and marketplace agents but my custom agent incorporates MCP servers and tools that I define myself and I’ve shared the configuration on GitHub.
In addition to the configuration of the agent itself, I built a lot of tooling for this, which is also shared in that GitHub repo, agentic_soc_agentspace. That tooling is a set of python utilities that separate the code and configuration of your agent. The configuration is kept in a single “dot env” file (.env). A Makefile wraps those python utilities to provide a single interface for the whole process and provides make targets like agent-engine-deploy.
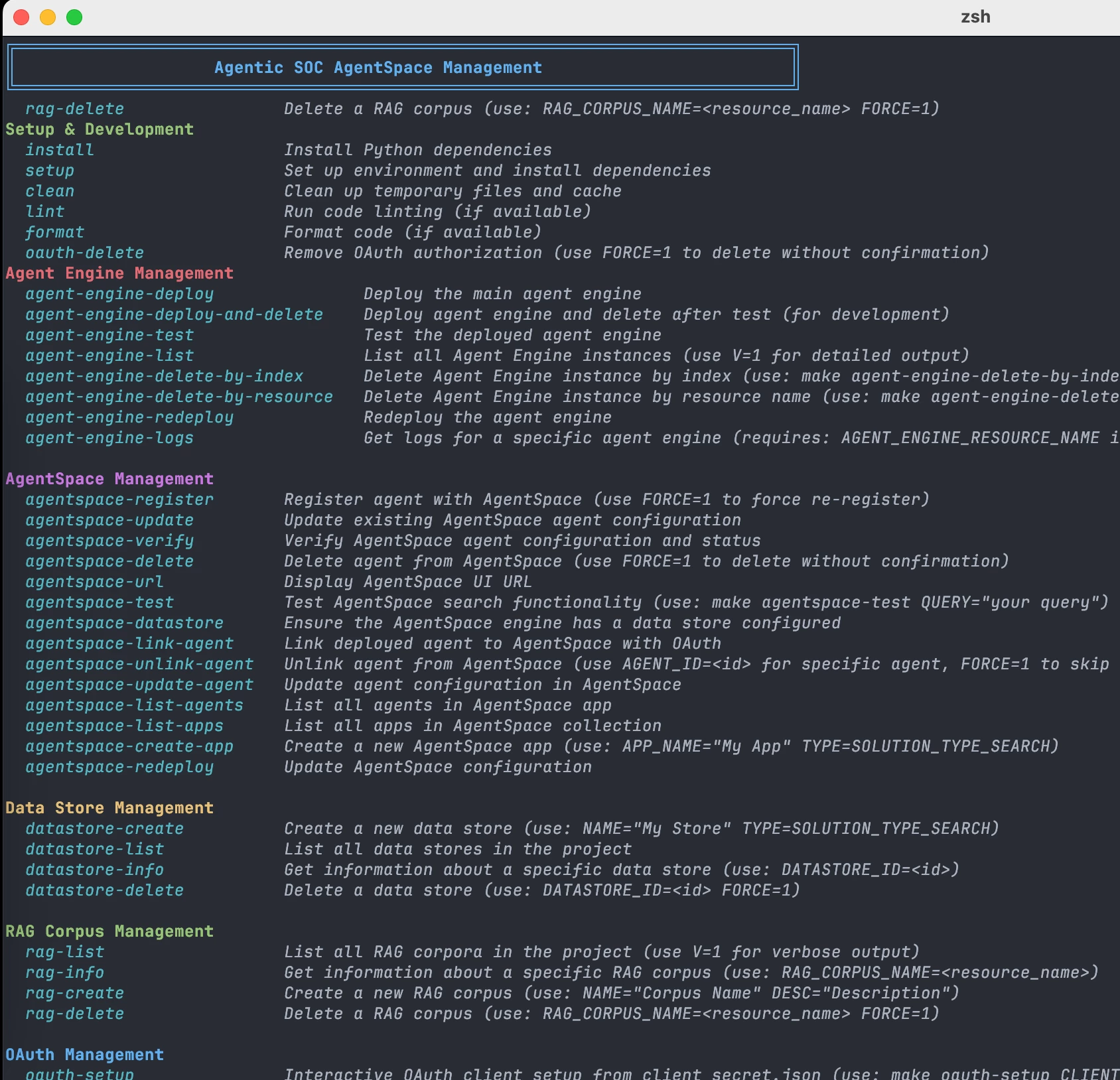
Makefile targets
Here is a high-level overview: previously we were packaging our custom ADK agent up into a container and then deploying the container to Cloud Run. In Cloud Run, we manage the container ourselves. With Gemini Enterprise, a container is built in Cloud Build and hosted in Vertex AI Agent Engine, which is a fully managed runtime[2]. That adds Google Cloud Trace, Cloud Monitoring, and Cloud Logging—giving you all of the visibility that a production agent needs[3]. One of the make targets, agent-engine-logs, retrieves log events from Cloud Logging. Convenient access to the logs saved me some time while I was troubleshooting a Python dependency issue.
The final steps are to create a Gemini Enterprise App and then link our custom Agent Engine to that App.
That distills down to just three make targets:
agent-engine-deployagentspace-create-appagentspace-register
Once done, the Gemini Enterprise App has the stock agents like Deep Research, Idea Generation, and NotebookLM and it has the custom agent we’ve defined ourselves, the MCP Security Agent.
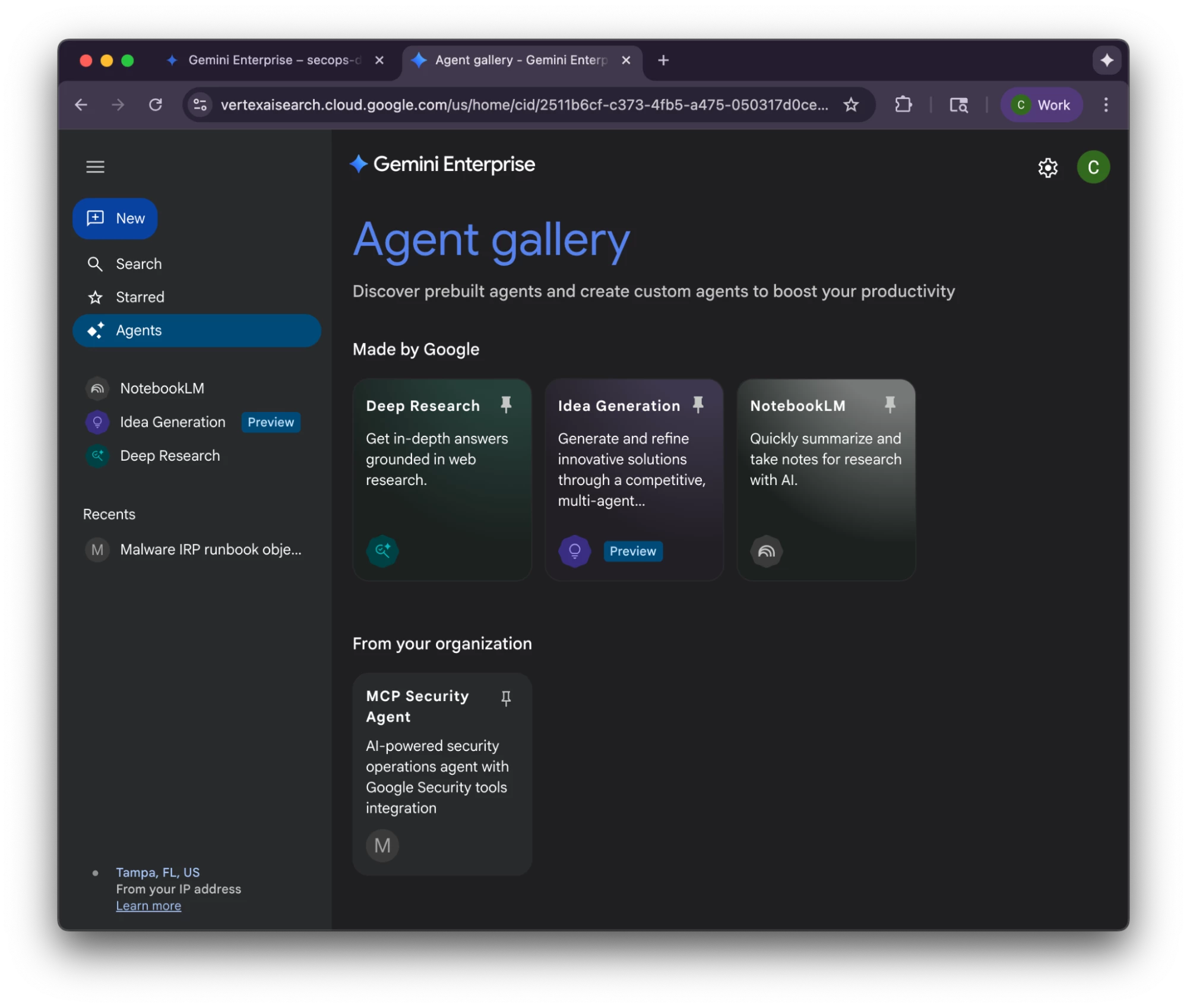
Gemini Enterprise Agent gallery
That custom agent can then answer questions like “What is the objective of my Malware Incident Response Plan?” by retrieving runbook content from the Retrieval Augmented Generation Corpus. Even better, it can go full agentic with a prompt like “Execute the Malware Incident Response Plan for Case 123” just like we saw in my previous demo.
I’m sharing a screencast demo below. I start with a few sessions that show the RAG and MCP Tools put through their paces. After that, I walk through the process used to create this custom Gemini Enterprise agent. I’ve got some pro tips on the development and testing process that should make your custom build much easier. For example, the build-and-delete make target helps you iterate without accumulating dozens of non-functioning agents and the get-logs make target gets you the stack trace on why your last build didn’t work. So, if you only intend to be a user of Gemini Enterprise agents, you might bail out of the video after the demo, but stick around to the end if you are a builder.
Gemini Enterprise SOC Agent on YouTube
If you’re not interested in building your own agents, you can learn more about agentic AI capabilities, such as alert triage and malware analysis, available in Google Security Operations with Gemini in Security.
[1] https://cloud.google.com/gemini-enterprise
[2] https://docs.cloud.google.com/vertex-ai/generative-ai/docs/agent-engine/overview
[3] https://docs.cloud.google.com/vertex-ai/generative-ai/docs/agent-engine/overview




