LLMs promise significant gains for security teams to augment human expertise in areas like threat detection, investigation, and response orchestration. However, a critical bottleneck is the integration gap between security tools (SIEM, SOAR, threat intelligence, cloud security, endpoints, network etc.). Currently, connecting tools together demands bespoke, resource-intensive integrations, leading to fragmented security workflows with missing capabilities and context.
Enter the Model Context Protocol: Simplifying AI Integration
To overcome the integration gap and unlock advanced AI workflows, the community is rallying around the Model Context Protocol (MCP). MCP is an open standard that simplifies connecting LLMs to external data sources and tools. It aims to streamline how models can retrieve information, trigger actions, and interact with applications. This abstraction layer standardizes AI's interaction with tools. MCP enables natural language interaction across product and business boundaries, making the power of AI available to all users and not just developers. This is a massive democratization of ad hoc workflow creation, making bespoke tools readily accessible.
MCP works alongside protocols like Agent2Agent (A2A), which enables AI agents to directly interact and collaborate. While A2A facilitates inter-agent communication with built-in support for dynamic interactions, MCP standardizes how agents or models connect to and utilize external tools and data sources with structured inputs and outputs. MCP complements A2A by bringing context to the multi-agent systems A2A enables.
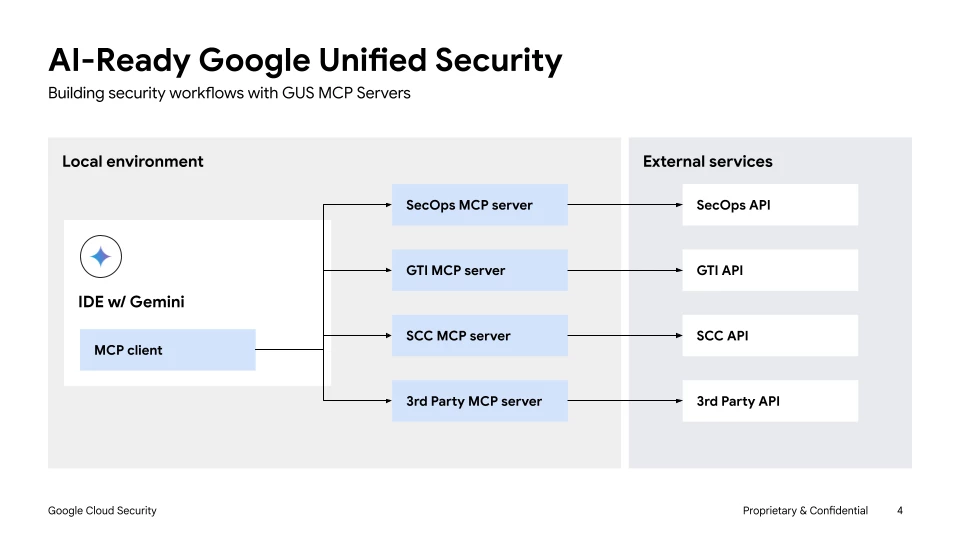
Today we are releasing MCP server implementations for Google Security Operations, Google Threat Intelligence, and Security Command Center, to accelerate the creation and adoption of security workflows utilizing this protocol.
We believe MCP will enable the future of distributed analytics and will require broad industry collaboration to deliver on its full potential for security use cases. That's why Google Cloud is thrilled to announce a shared commitment with leading security innovators Cloudflare, CrowdStrike, Okta, and Wiz to foster an open and interoperable AI security ecosystem.
"Security leaders need to harness the power of AI, without sacrificing visibility, control, or protection. That’s why CrowdStrike is proud to work with Google Cloud to simplify secure AI adoption across the entire security stack,” said Daniel Bernard, Chief Business Officer at CrowdStrike. “This collaboration is a powerful example of our commitment to innovation, interoperability, and giving defenders the advantage to stop breaches.”
For security teams and security engineers, this means less time spent on complex integration "plumbing" tasks and more time focused on leveraging AI for high-value outcomes like advanced analysis and automated response.
Bringing Security Use Cases to Life with MCP
Imagine the possibilities unlocked when all an analyst has to do is describe their intent, without worrying about individual API calls, input/output formats, or even which security tool is being used to return a result:
Cross-Product Orchestration: Now imagine these capabilities across your entire security stack. An AI assistant can start with a SecOps alert, then use MCP to query a customer’s other security tools for additional critical information – instantly checking for network alerts (Cloudflare), IoAs associated with an endpoint (CrowdStrike), user risk signals (Okta), or cloud risks (Wiz). Armed with this holistic understanding, the assistant can orchestrate coordinated responses across these platforms, like disabling compromised accounts or isolating affected machines, with all actions tracked centrally via the LLM.
"Securing the connected world requires seamless integration and knowledge sharing," said Michael Tremante, Senior Director of Product, Cloudflare. "MCP provides a solid framework for standardizing how AI applications interact with essential security controls, which will make insights more user-friendly and accessible, without the need to jump across different applications. Together with Google Cloud and our partners, we're committed to building an open ecosystem that benefits all security teams."
“As an industry, it's critical that we prioritize interoperability and enable our mutual customers to seamlessly integrate best-of-breed solutions and effectively leverage AI across diverse security tools.” - Stephen Lee, Vice President of Technical Strategy & Partnerships at Okta.
Embracing an Open Ecosystem with Google Unified Security
We recently introduced Google Unified Security (GUS) to help teams remove silos and accelerate security outcomes with a single security fabric infused with AI. To help our customers connect GUS products to the broader security ecosystem, we are excited to announce the open-source release of MCP server implementations for Google Security Operations, Google Threat Intelligence, and Security Command Center.
- Google Security Operations (SecOps) APIs: Enabling AI interaction with security events, alerts, entities, and rules & facilitating AI-driven orchestration and response actions within SecOps.
- Google Threat Intelligence (GTI) APIs: Providing standardized AI access to Google's frontline threat intelligence on indicators of compromise, threat actors, and campaigns.
- Google Security Command Center (SCC) APIs: Integrating posture findings and virtual red team outputs for Google Cloud workloads.
With today’s announcement and future announcements from our ecosystem partners, security practitioners can effectively use LLMs to power integrated workflows in GUS products and across their entire security stack.
Our goal is to empower the security community to innovate easily and build the next generation of AI-powered workflows. Providing practical building blocks is the fastest way to unlock the creative potential of developers, partners, and our customers within the MCP ecosystem. Specifically, this release aims to:
- Provide Building Blocks for Innovation: Dramatically lowers the entry barrier, enabling anyone – customers, partners, researchers – to begin tangible development and experimentation with MCP.
- Accelerate Partner and Customer Solutions: Accelerate journeys across best-of-breed products from Cloudflare, Crowdstrike, Okta, and Wiz.
- Complement Agent Development Efforts: Support the foundation for more sophisticated multi-agent systems.
What's Included in Today’s Launch?
Hosted on GitHub (under an Apache 2.0 license) in the google/mcp-security repository, you'll find:
- Runnable Python MCP server examples for Google Security Operations, Google Threat Intelligence, and Google Cloud Security Command Center.
- Clear README files detailing setup and configuration.
- Implementations of key MCP tools and resources supporting high-priority security workflows.
- Basic contribution guidelines to encourage community involvement and cross-vendor use cases.
Important Note: You may use any MCP compatible client. These are reference implementations intended to serve as examples and accelerators. They are not officially supported, SLA-backed production services. They are designed primarily for local execution or deployment within user-managed environments, reflecting the current common pattern for MCP servers.
“Reducing cloud risks effectively requires seeing the full picture and remediating quickly. Wiz is deeply committed to expanding our integration ecosystem to empower customers and support their operational workflows. We’re proud to support Google Cloud’s MCP initiative and help bring AI-driven defense to life across the ecosystem—for both security and development teams." - Oron Noah, VP Product, Extensibility & Partnerships at Wiz" - Oron Noah, VP Product, Extensibility & Partnerships at Wiz
The Road Ahead
Today's open-source release marks a foundational step towards a more connected and AI-driven security future. While MCP holds immense promise, we recognize challenges remain, particularly around establishing robust standards and enterprise-grade infrastructure for secure and scalable MCP interactions. Google Cloud is actively committed to overcoming these hurdles, working alongside the community and our partners to develop practical solutions.
Alongside native Gemini experiences in GUS products, like the alert triage and malware analysis agents, GUS MCP servers empower developer-minded practitioners with the local tools necessary to experiment and innovate with AI. Looking further ahead, we envision an ecosystem complementing GUS, where AI agents seamlessly and securely leverage capabilities from a wide array of security tools using MCP and collaborate with each other using A2A. Realizing this future depends on continued, active collaboration across the industry, bringing together AI platform providers, the open-source community, and security leaders including Google Cloud and our partners like Cloudflare, Crowdstrike, Okta, and Wiz. Together, we can accelerate the development and adoption of open standards that benefit all defenders
Get Started Today
We invite you to explore the new google/mcp-security repository on GitHub. Clone the code, experiment with the examples, and see how you can connect the power of LLMs to Google's leading security products. We welcome your feedback, contributions, and ideas as we collectively build the future of AI-driven security operations.
If you're at RSA Conference 2025, visit us on the show floor at booth #N-6062 Moscone Center, North Hall to see us showcase these MCP integrations in action, and to chat with our security experts.
As you use GUS product MCP servers, we encourage you to ask questions and share your learnings in the Google Cloud Security Community by using the “MCP” label on your post.