The Agentic SOC isn't a distant goal; it's a journey we are already embarking on with our customers. Building the future of security is a collaborative effort, one that requires a deep partnership with the defenders on the front lines. Our vision for an Agentic SOC involves building specialized AI agents such as the Alert Investigation agent, which is currently in preview, and helping customers build AI agents unique to their environment by supporting tools like an open source Google Security Operations MCP server. With the strong momentum seen for the Alert Investigation agent and Google Security Operations MCP servers, we want to accelerate getting powerful, cutting-edge ideas into the hands of practitioners as early as possible.
We’re taking the next step in this journey with SecOps Labs. SecOps Labs provides early access to AI pilots, through a dedicated space within the product for you to test, explore, and influence the next generation of Google Security Operations technologies. For example, your feedback on the detection coverage analyst pilot in SecOps Labs will be incorporated into one of our key agentic pillars - detection engineering.
In this post, we'll explore how SecOps Labs works and provide a first look at the five initial experimental AI pilots you can start using today.
How SecOps Labs Works
We designed SecOps Labs to be a streamlined and safe environment for you to engage with our emerging technologies without disrupting your core workflow. Think of it as a dedicated sandbox built directly into the Google Security Operations platform.
Here’s what you can expect:
- A Centralized Hub for Experiments: Within the Google Security Operations interface, you will find a new, dedicated SecOps Labs page. This hub provides a single place to discover and enable all available experimental pilots. For existing + customers, this is enabled by default.
- Clear and Actionable Insights: Each pilot in SecOps Labs comes with clear instructions on its purpose, how to use it, and what security challenge it’s designed to address. You can easily toggle different pilots on or off, giving your team full control over which experimental features you want to evaluate.
- Designed for Safety and Feedback: These pilots are experimental in nature, and while they are powerful, they are not yet production-grade features and are meant for evaluation. The most critical part of the workflow is the ability to provide direct feedback, allowing you to share your evaluation and influence which ideas are prioritized and graduated into the main product.
To get started with SecOps Labs, simply navigate to the flask icon in the upper righthand corner of your Google Security Operations tenant.
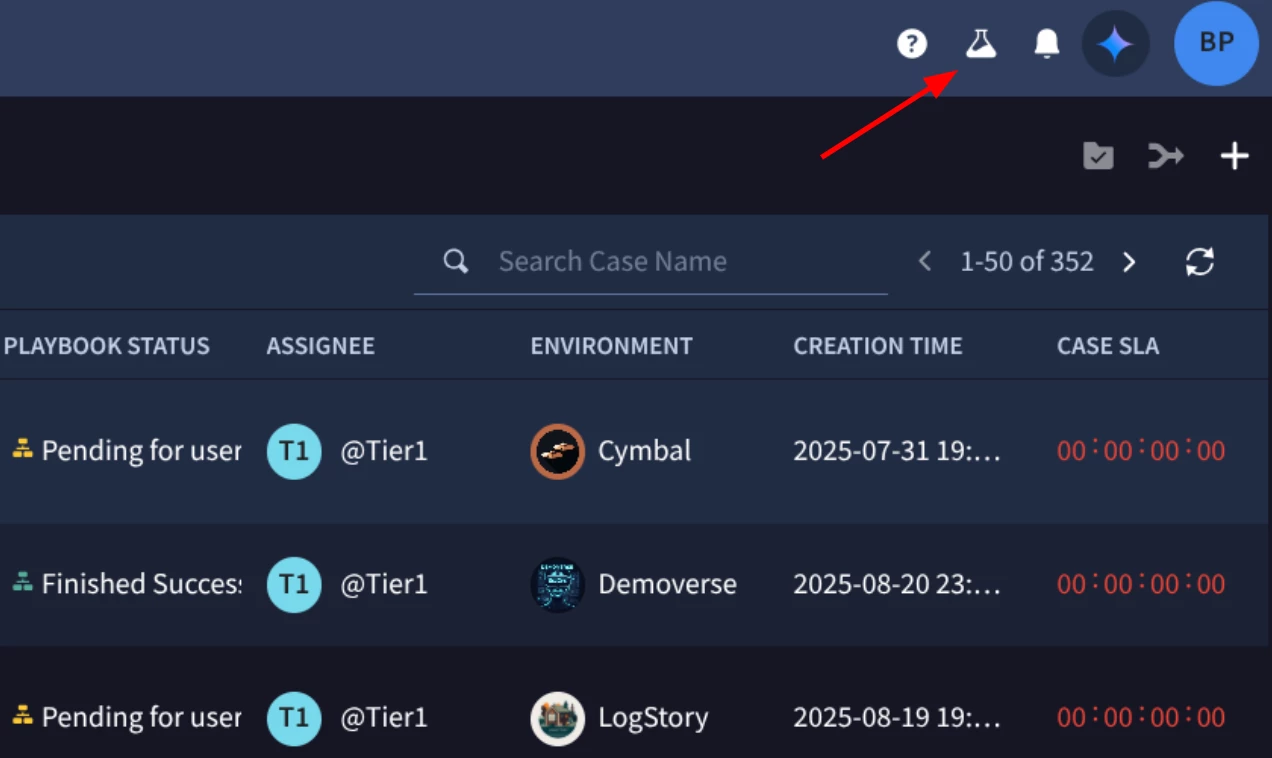
Figure 1: Select the flask in the flask icon to access SecOps Labs.
A First Look at SecOps Labs Pilots
The first wave of pilots in SecOps Labs incorporate AI to address some of the most persistent operational challenges faced by security analysts. From automating tedious data normalization tasks to accelerating threat analysis and migration efforts, these experiments aim to improve SOC efficiency and effectiveness.
Here is a look at the five pilots available today:
Detection Coverage Analyst
This pilot helps evaluate the effectiveness and coverage of your detections by generating synthetic logs. You can input specific behavioral indicators, and it will generate synthetic UDM events to assess which detection rules would likely trigger. It specifically targets threats represented by behavioral indicators, such as command-line arguments, URLs, or IP addresses.
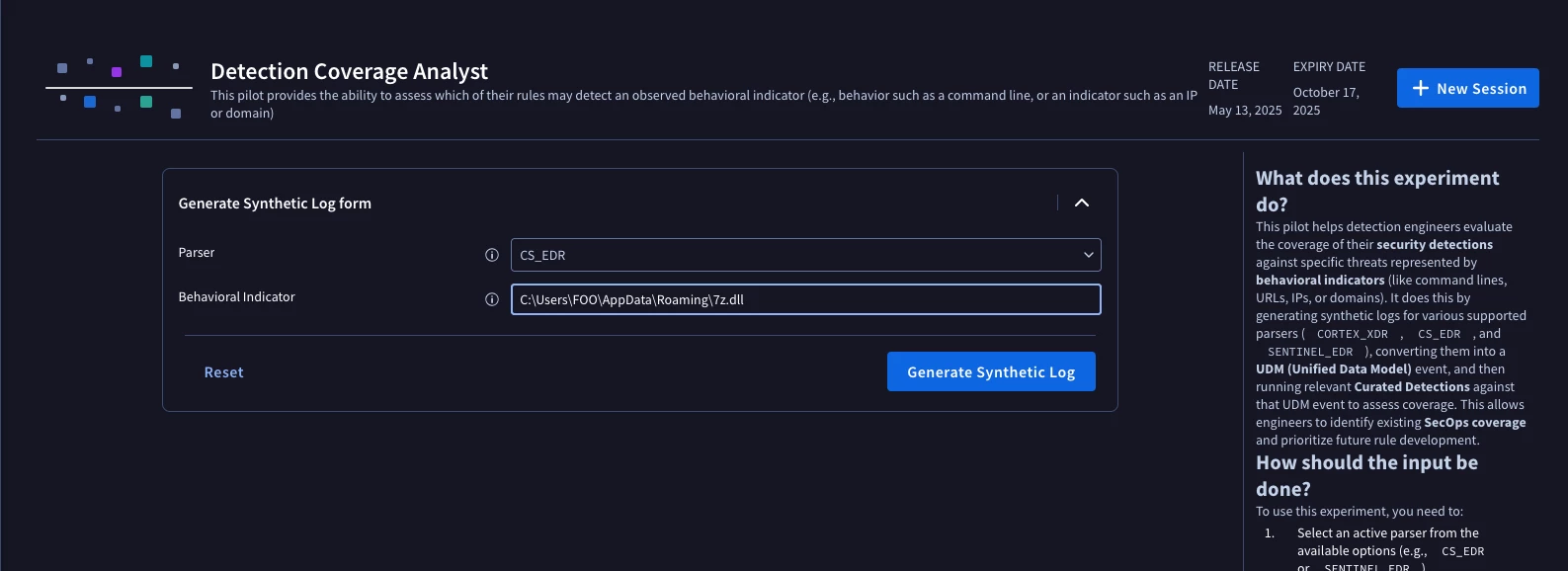
Figure 2: Input observed indicator and generate synthetic log
Here’s how it works:
- Select an active parser (e.g., CS_EDR or SENTINEL_EDR) and input a specific behavioral indicator you want to test
- The agent then automatically generates UDM logs that represent different ways the threat could manifest
- We evaluate our rules against these logs to determine whether we detected the inputted indicator
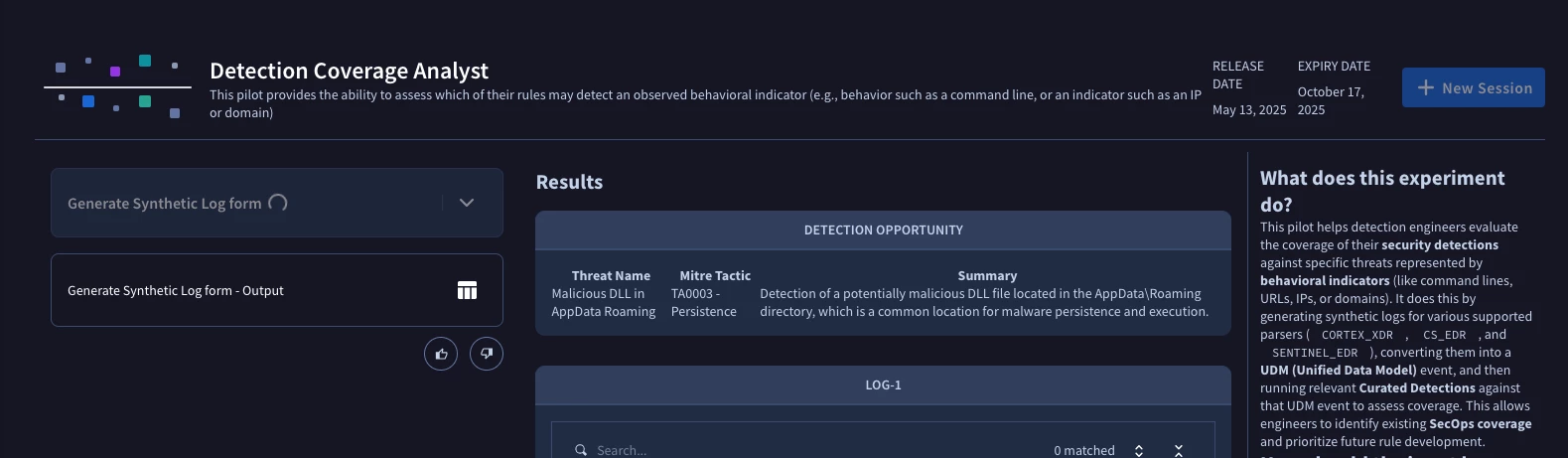
Figure 3: Detection Coverage Analyst pilot thinking and working
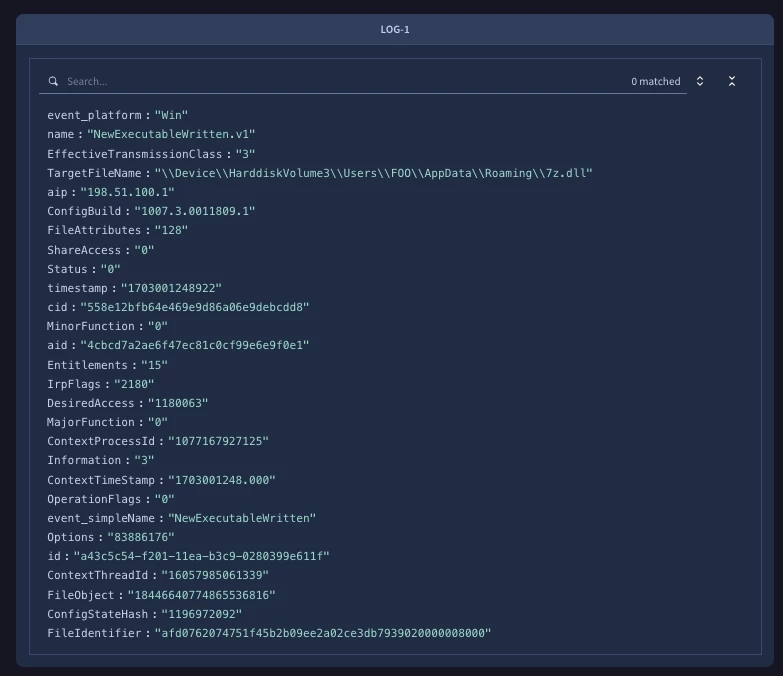
Figure 4: Example synthetic log generated by Detection Coverage Analyst pilot
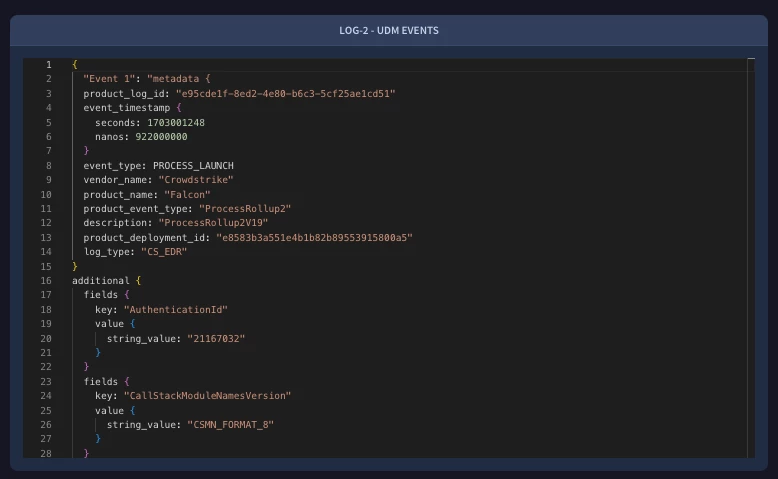
Figure 5: Summary of the completed analysis, UDM events, and matching rules.
Once the process is complete, the output provides a comprehensive analysis, including parsed UDM logs, tables of any YL2 matches found, and the logic of the matching rule if it's public. This pilot not only gives you clear insights into your detection performance, but also a limited preview of what will be possible in the future with a full-fledged detection engineering agent.
Automatic Parser Extension
Getting data ingested and normalized correctly is fundamental to security operations. This pilot accelerates the process by allowing you to generate a parser extension simply by describing the log format you need in natural language.
SPL Rule Translator
For organizations migrating to Google Security Operations, translating existing detection logic from legacy SIEMs can be a significant hurdle. The SPL Rule Translator pilot assists teams by performing a best-effort translation of Splunk SPL (Search Processing Language) queries into YARA-L logic.
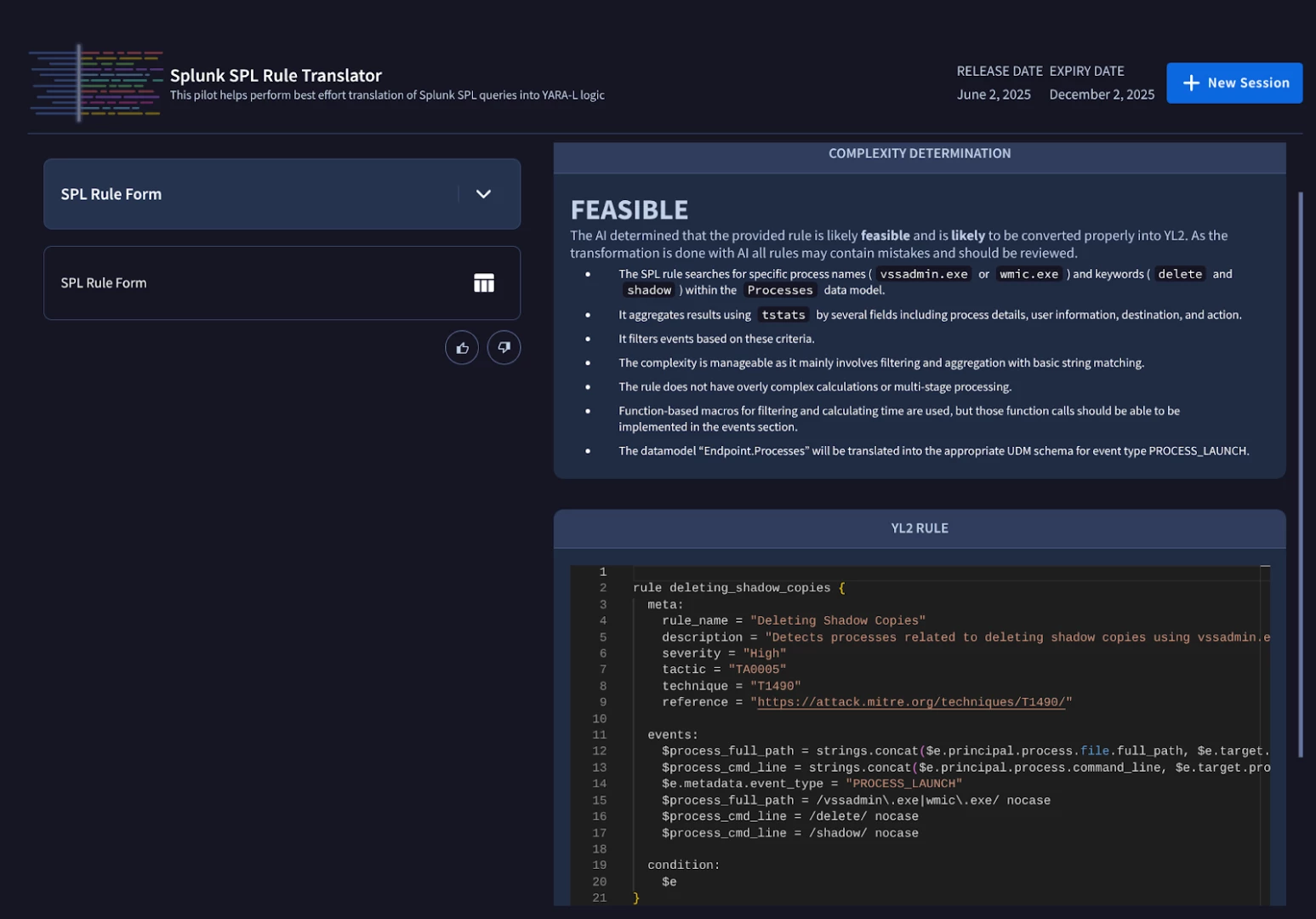
Figure 6: Converting an SPL detection for deleting shadow copies into a YARA-L logic.
Curated Detection Threat Mapping
This pilot introduces an intuitive chat experience for interacting with Google Security Operations Curated Detections. Analysts can ask natural language questions about what rule sets cover a particular MITRE ATT&CK technique.
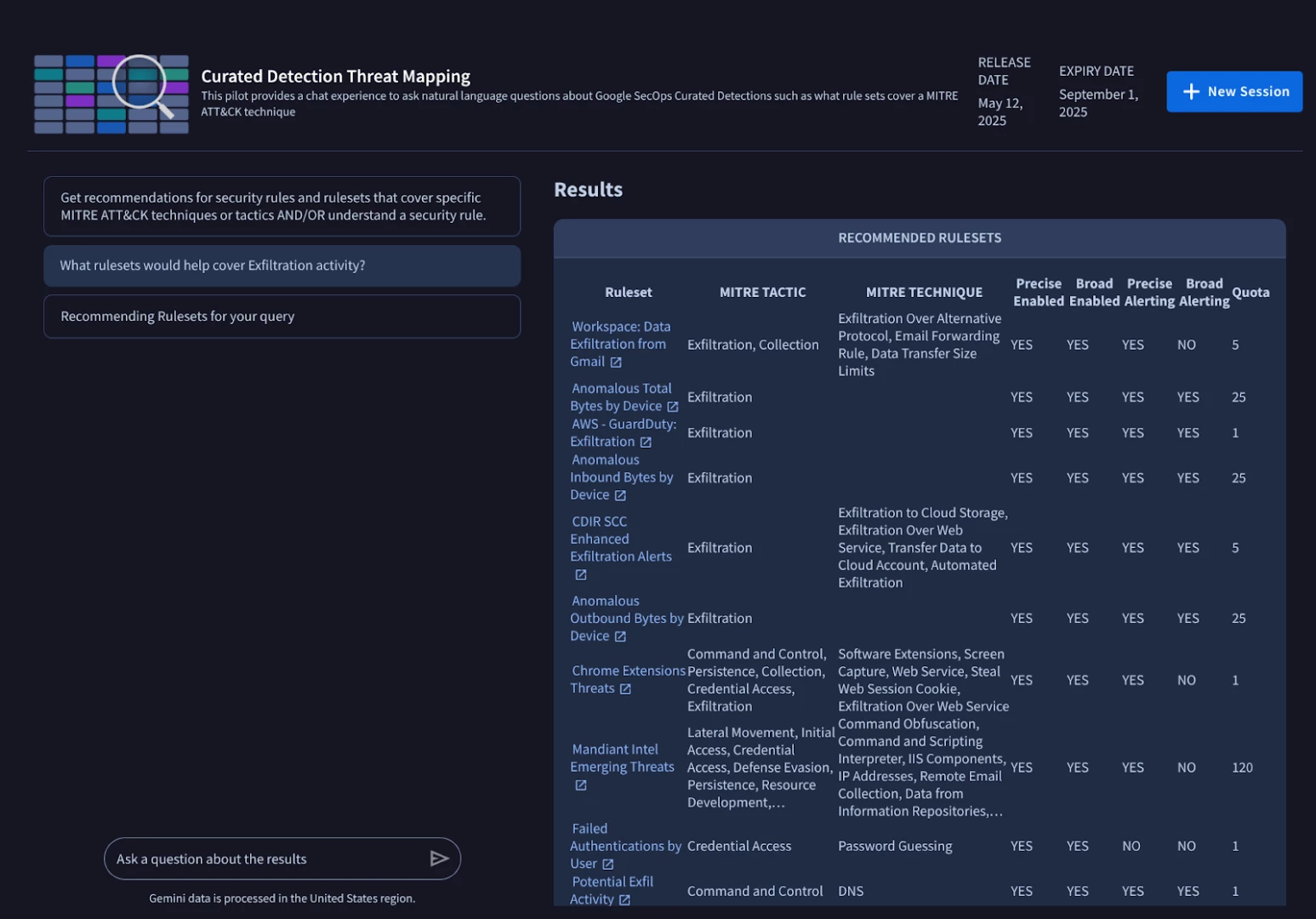
Figure 7: Identifying curated detection rules that would cover exfiltration activity.
Alert Response
Improving the speed and consistency of alert triage is a top priority for every SOC. The Alert Response pilot leverages your organization’s historical alert resolutions and outcomes. It then uses this context to suggest actionable recommendations for new, open security alerts.
Shape the Future of AI in SecOps
SecOps Labs is a shift towards a more collaborative and accelerated model for how we introduce AI features to our customers. By testing these early-stage pilots and providing your direct feedback, you play a critical role in shaping the tools that will define the next era of security.
These five pilots are just the beginning, and we are incredibly excited to see how your insights will help these ideas evolve.




