Authors: Ana Martinez Gomez, Elliot Chernofsky, Sara Rincon, Mustafa Nasser
It's been an exciting journey for FLARE-VM over the past couple of years, and we're thrilled to share a roundup of the significant enhancements, quality of life updates, and newest capabilities that have been incorporated into your favorite reverse engineering and malware analysis distribution. From expanding our core toolset to ensuring robust compatibility with Windows 11, our focus remains on providing an automated cutting-edge, stable, and comprehensive environment for security professionals and enthusiasts alike. This post will walk you through some of the key updates, highlighting how these changes empower you to tackle the latest threats and streamline your analysis workflows.
A Revamped GUI for the FLARE-VM installer
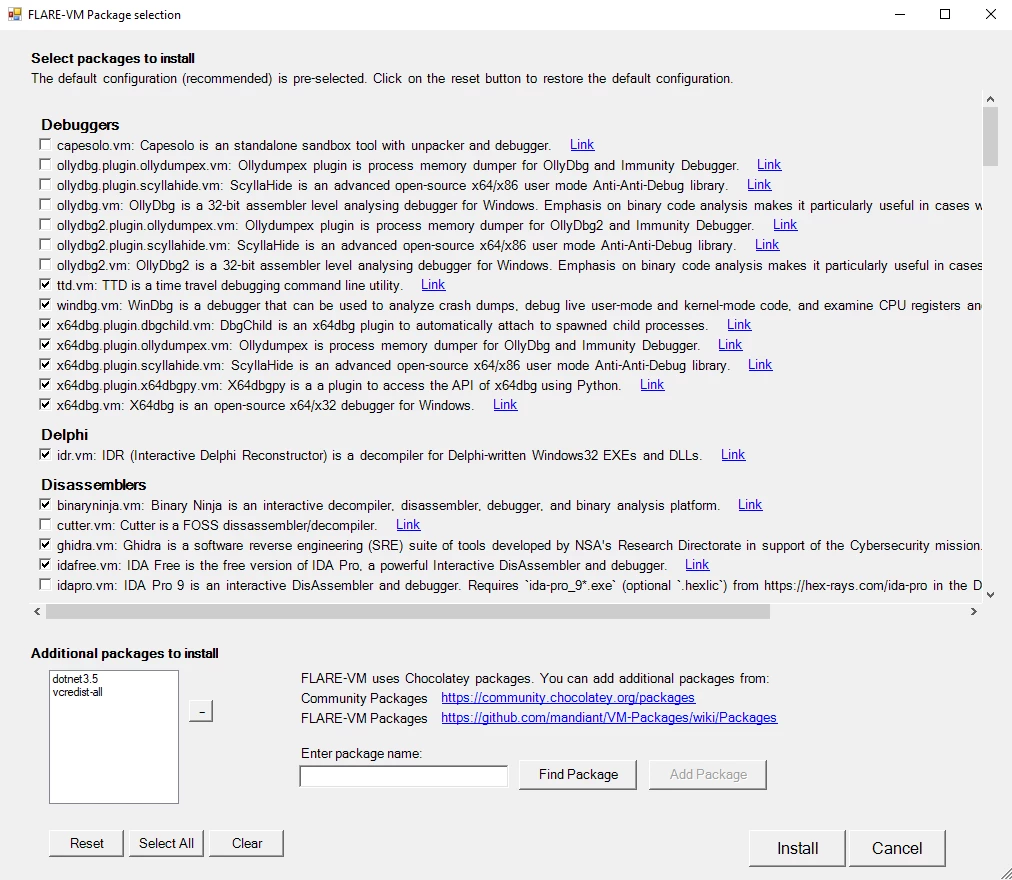
Get ready to forge your perfect analysis environment! We've completely revamped the FLARE-VM installer GUI to put you in command of your analysis toolkit. The installer provides an expert-curated default configuration, the same setup the FLARE analysts rely on for their daily work, and you have complete freedom to customize your VM selecting from a wide range of packages.
With the growing number of available packages, it was becoming difficult to decide which tools suited your needs in the GUI. We've solved that by intelligently grouping packages into categories, displaying clear descriptions, and providing direct links to tool homepages. Now you can effortlessly discover powerful new utilities and build a VM that’s perfectly tailored to your workflow, without the guesswork.
In addition, the new GUI unlocks a wider universe of software, allowing you to search and install any package you need, including those for Commando VM or from the standard Chocolatey package repository. These packages are now displayed in a separate list in the installer GUI, making them visible and configurable as well.
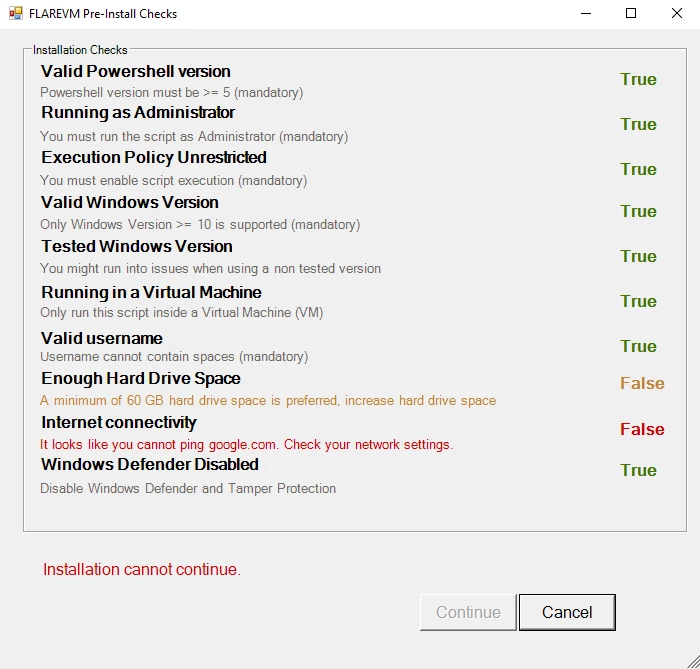
To ensure a smooth start, a new pre-installation window provides an at-a-glance status of all requirements, with guidance for any issues and the options to proceed.
The Power Behind the Tools: Our Shared VM-Packages Repository
The tools you install are powered by our VM-Packages repository, which we proudly share with the Commando VM project, benefiting from common tools and useful features. We constantly update the repository with new tools to keep pace with the evolving needs and trends of reverse engineers. To showcase this incredible tool arsenal of over 288 tools, we’ve launched an automatically generated Packages Wiki page that is always kept up-to-date. This page documents the available tools in FLARE-VM and Commando VM as well the default FLARE-VM configuration.
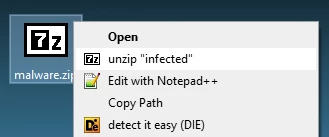
In addition to installing the tools, many of the packages also add valuable customizations to enhance your workflow. For example, the 7zip.vm package includes 7z-build-nsis, a special build of 7-Zip allowing for efficient analysis of NSIS installers by unpacking both the installer files and the decompiled NSIS script. The package also adds an "unzip infected" right-click option to easily handle malware archives protected with the standard password. Likewise, we pre-install useful plugins for tools like Notepad++ (e.g., ComparePlus, JSToolNPP) and x64dbg (e.g., DbgChild, ScyllaHide) to make them more powerful right out of the box.
Disassemblers & IDA integration
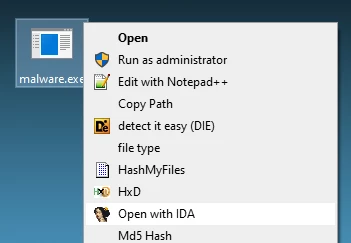
A disassembler is the cornerstone of any reverse engineering toolkit. 🛠️ That's why FLARE-VM includes the latest versions of the most popular free disassemblers, including IDA Free, Ghidra, and Binary Ninja Free. FLARE-VM further enhances the experience by adding a convenient "Open with IDA" right-click option that opens your binary directly with the latest version of IDA. Furthermore, it facilitates the installation of IDA Pro and your favourite IDA plugins, allowing users to dive into binary analysis without additional setup.
Installing IDA Pro is very easy, you just need to place your IDA Pro installer (and optionally, your license file) on the Desktop and install the idapro.vm package. You can also use FLARE-VM as an IDA package manager to easily install numerous useful IDA plugins such as:
- capa-explorer: Quickly identifies the capabilities of a program by integrating capa directly into the IDA interface.
- CoMiDa: Assists in analyzing complex Windows binaries that use Component Object Model (COM) interfaces.
- deREferencing: Enhances register and stack views by displaying dereferenced pointers and other useful context.
- Diaphora: Performs advanced binary diffing to compare assembly, pseudo-code, functions, and data structures between files.
- hrtng: A versatile plugin for decryption, deobfuscation, patching, and recognizing library code.
- Interactive Functions List (IFL): Provides a dynamic and organized view for navigating function references with ease.
- X-Ray: Colorizes and filters the Hex-Rays decompiler output, making complex code much easier to analyze.
- XRefer: A custom navigation interface with path graphs and Gemini-powered descriptions to speed up analysis.
Upgraded Arsenal for Today's Complex Malware
To counter the growing sophistication of malware across diverse development platforms, we’ve expanded our toolkit to handle a wider spectrum of complex and obfuscated threats. We’ve seen a rise in Python-based malware using marshalled code or modern .pyc files, where a decompiler is essential for efficient analysis. FLARE-VM now includes pycdas, pycdc, and uncompyle6 to meet this need, along with numerous Python libraries to help run and dissect complex scripts. This focus on specialized decompilers extends to Visual Basic malware, for which the toolkit includes VB Decompiler and VBDec.
For the .NET framework, the toolkit includes indispensable tools like the ILSpy decompiler, the dnSpyEx decompiler and debugger, de4dot-cex for handling protectors like ConfuserEx, and DotDumper to extract crucial data from running processes. In the mobile landscape, analysts can now use Apktool to unpack Android applications and dex2jar to convert them, before diving deep into the code with powerful editors like Recaf and Bytecode Viewer. For Go we provide GoReSym to recover symbols and GoStringUngarbler to recover strings from binaries obfuscated by garble. Finally, to get through any packaging, the toolkit is equipped with extractors like the all-purpose Universal Extractor 2, and specialized tools for Electron (asar), AutoIt (AutoIt-Ripper), and InnoSetup installers.
You can explore the full list of available tools on our GitHub wiki.
Ready for Credential Stealers: Pre-Installed Chrome Extensions
To better facilitate the dynamic analysis of credential-stealing malware, the chrome.extensions.vm package installs several commonly targeted Chrome extensions. This eliminates manual setup and provides a realistic environment, including popular cryptocurrency wallets (MetaMask, Phantom, etc.) and password managers (Avira, KeePassXC-Browser).
Smart Debloating
A reliable analysis environment starts with a clean slate. Our debloat.vm package serves as a powerful optimization tool that strips away unnecessary pre-installed applications, tunes non-essential services, and disables preset scheduled tasks. It applies significant OS optimizations tailored to your specific Windows version, minimizing the operating system's footprint to maximize performance and reduce potential interference during analysis.
Stay Isolated: The Internet Detector
Maintaining a strictly isolated environment is crucial for safe malware analysis. To provide a powerful layer of protection, our internet_detector.vm package installs the Internet Detector tool that continuously checks if the VM is connected to the internet in the background. If internet accessibility is detected, the analyst is alerted by changing the Windows theme color to pink, updating the desktop wallpaper with the message "INTERNET ENABLED" and sending a system tray notification. Once isolation is restored, everything is restored to its previous state. The tool checks the internet connection by sending ICMP requests to a list of hardcoded well-known IP addresses, so it may cause noise for the network analysis tools (e.g. Wireshark).

Automated FLARE-VM builds
Automation is central to FLARE-VM. The installer leverages Chocolatey for tool installation, and GitHub Actions automates repository workflows like tool testing, updates, package releases, and creation from issues. Recent enhancements further automate documentation generation, proactive package repair, and expanded tool support.
Continuing our mission to automate everything related to FLARE-VM, we invite you to say goodbye to manual VM creation! Our new script, vbox-build-flare-vm.py, automates the build of customized VMs with FLARE-VM using VirtualBox. The script handles everything from restoring a clean Windows image to installing FLARE-VM with your favorite tools, running cleanup, and exporting a secure, internet-disabled OVA file. In addition, the virtualbox folder also includes other useful scripts for managing snapshots and even building REMnux VMs.
Join the Community
Finally, we want to extend a huge thank you to our community. Many of these enhancements are the direct result of your valuable feedback, suggestions, and code contributions. This project is a collaborative effort, and working with our users, supportive tool maintainers, and dedicated contributors is the most rewarding part of what we do.
If you're ready to dive in, we encourage you to prepare a Windows VM and follow the installation instructions in our FLARE-VM README. If you’d like to help shape the future of the project, please check the contributing documentation links and get involved! Your contributions, big or small, are what drive this project forward!

