We are excited to share that Composite Detections in Google SecOps is now available in preview, empowering security teams with new levels of flexibility, modularity, and sophistication in their threat detection strategies! This powerful new capability allows you to build advanced rule sets by combining insights from existing detections, leading to more targeted and contextual alerts, reduced noise, and a deeper understanding of complex attack patterns.
What are Composite Detections?
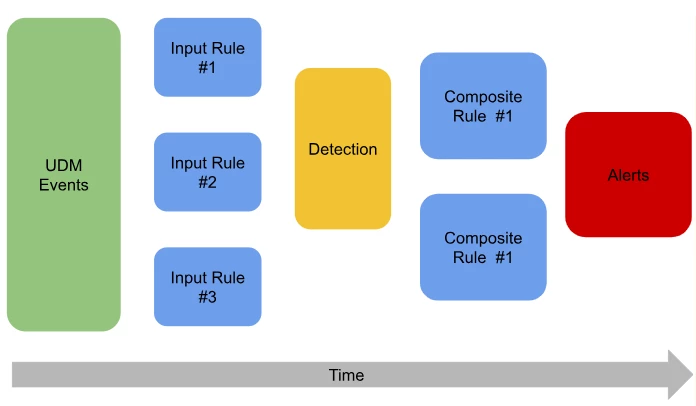
In today’s evolving threat landscape, attacks frequently unfold in multiple stages, involving a series of seemingly innocuous activities. Identifying these complex sequences with point-in-time is challenging for analysts to manually correlate and construct into larger attack narratives. Developing and maintaining large, monolithic correlation rules can be a challenging task for detection engineers. Composite Detection rules address this challenge by allowing you to break down intricate detection logic into smaller, reusable units called “Input Rules.” These “Input Rules” focus on identifying specific, atomic behaviors or aggregated events as input signals.
The true strength of Composite Detections lies in its ability to then combine these “input signals”(which can be detections or alerts) of these input rules in what we call composite rules. These rules act as correlation engines, identifying patterns and relationships across multiple underlying detections within a defined timeframe. This approach builds upon the familiar YARA-L rule language, ensuring a smooth transition and leveraging your existing detection investments.
Why should I care about Composite Detections?
This feature empowers detection engineers and threat hunters to improve their threat detection abilities:
- Enhance detection accuracy: By correlating multiple low-level signals, you can significantly reduce false positives and focus on genuine threats.
- Advanced attack sequences: Identity multi-stage attacks by detecting combinations of behaviors that individual rules might miss.
- Increased flexibility and reusability: Generate automatic “Input Rules” once and reuse them in various Composite Detection rules for different scenarios, saving time and effort.
- Improved context and prioritization: Composite Detection rules can aggregate risk scores from underlying detections and incorporate context like MITRE ATT&CK tactics and techniques to provide richer insight for analysts.
- Integration with diverse data: Composite Detection rules can not only combine detections but also incorporate data from UDM events and the Entity Graph, including threat intelligence like Google Safe Browsing and IP prevalence. This allows for truly contextualized detections.
- Simplified Rule Management: Break down complex, unwieldy rules into smaller, more manageable components, improving maintainability.
Top Use Case Examples
- Aggregating risk for high-value alerts: Combine various low risk input detections targeting a specific user or assets as signals to trigger high risk alerts when a cumulative risk score threshold is reached.
- Combining custom and curated detections: Leverage threat coverage over your organization’s unique business needs alongside Google Security Operations’ curated detections to build composite detections against endpoint threat classes.
- Detecting sequences events indicative of malicious activity: Identify specific sequences of events, such as enumerating groups and members followed by group creation, which could indicate malicious activity.
How can I get started with Composite Detections:
Composite Detection is now in public preview for all Google Security Operations users.
- Familiarize yourself with the concept
- Analyze your existing rules for opportunities to decompose into modular input rules
- Experiment with some composite rules in Google Security Operations, check out our public documentation here
- Reach out to your reps to check out our golden examples for inspiration
- Contact your sales rep for resources
- Post questions in CloudSec public community
Meet us at RSAC
Coming to RSAC? Connect with our experts and see Google Cloud Security tech in action:
- Meet us at our booth: Find us on the show floor at booth #N-6062 Moscone Center, North Hall to meet with our security experts and learn how you can make Google part of your security team. Check out our live presentations and 1:1 demos, and test your knowledge at M-Trends trivia — prizes included!
- Join our RSAC’25 Community User Group session where John Stoner will be running a workshop for Composite Detections