Introduction
Healthcare data and associated information systems are attractive targets for threat actors, particularly financially-motivated attackers. Cybercriminals often target these systems because they know medical professionals require access to them to care for patients, and healthcare organizations are likely to pay to get systems back online as soon as possible.
M-Trends 2025 shows healthcare is a top five most targeted industry, which has been relatively consistent in recent years. Figure one shows Healthcare only 0.2% behind the Government. The healthcare industry can expect even more frequent, targeted attacks as healthcare technology continues to evolve and change.
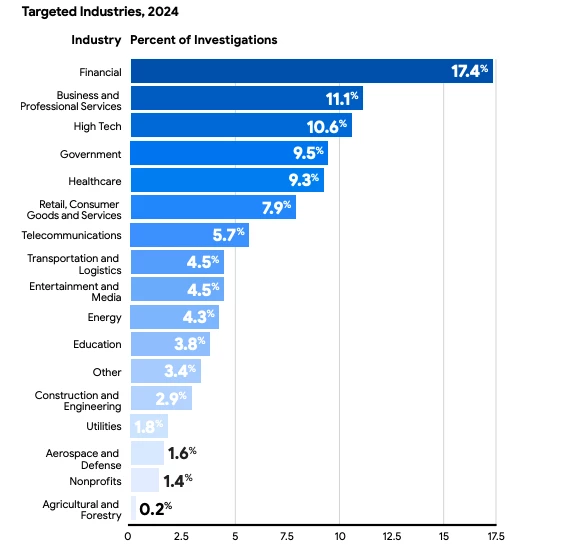
Figure 1: Healthcare remains a highly targeted industry
Mandiant’s Red Team understands how attackers target the healthcare industry, and replicates and emulates these tactics, techniques, and procedures (TTPs) to ensure healthcare customers are protected against the threats that matter most to them. These TTPs include the very social engineering, lateral movement, and privilege escalation attempts observed during responses to real-world breaches of healthcare organizations.
Through our deep research and years of hands-on-keyboard red teaming, Mandiant has identified several common areas where healthcare organizations struggle with security. This blog post discusses these risk areas, describes how attackers exploit them, and offers mitigation and hardening recommendations to better prevent and defend against threats. These findings can help healthcare organizations strengthen their defenses, and feel more confident in their readiness. This analysis also demonstrates the power of using red teaming as part of an organization’s security strategy.
This blog post also contains the appropriately referenced MITRE ATT&CK technique IDs for data consumption. These will be listed throughout the blog in the format of “(T###)”.
Observation 1: Lack of Multi-Factor Authentication
Mandiant frequently encounters critical and other healthcare systems lacking multi-factor authentication (MFA), providing a dangerously easy path for attackers to enter networks. In May 2024, a healthcare company announced that lack of MFA led to disruptive cyberattack earlier that year. In cases where MFA is enforced, oftentimes it is not FIDO2 compliant and/or not hardened, making the security measure easier to bypass.
Web-based portals, patient portals, administrative interfaces, and remote access solutions are among the most targeted applications on the public Internet. Based on our Mandiant incident response investigations, web compromises are a top five initial infection vector, and appear to be on the rise. M-Trends 2025 shows the percentage of intrusions that began with web compromise increased to 9%, from 5% in 2023, and 7% in 2023. Figure two depicts the complete breakdown of initial infection vectors observed over the past year.
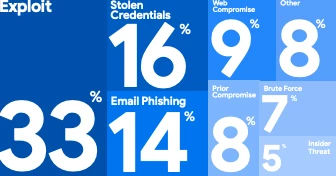
Figure 2: Intrusions from web continue to increase year over year
In the healthcare industry, these web portals and applications are intended to be public facing, and readily available to patients, medical professionals, and providers. Nearly all of them require users to have an account, and are accessed using credentials on a login screen, oftentimes a username and password.
On engagements with healthcare organizations, Mandiant’s Red Team often finds user accounts configured with weak, default, or blank passwords on critical healthcare devices, and in some instances these devices may be exposed to the public Internet. Many of these are sensitive accounts with administrative function or access to private health information (PHI). Correctly implemented MFA on these accounts or devices could have made a difference in preventing our red team from achieving our goals. Note that, according to M-Trends 2025, stolen credentials has risen to the second most frequently observed initial infection vector, driven largely by the rising popularity of infostealers. This increased focus on large-scale targeting of accounts means that account security is as important than ever.
Attack Paths
- Credential Stuffing (T1110.004): Using lists of known compromised credentials to attempt to log in to web applications and systems. This technique is effective against organizations that do not enforce strong password policies or MFA.
- Password Spraying (T1110.003): Attempts to log in to multiple accounts with a small set of common passwords. This technique is effective against organizations with weak password policies or where users reuse passwords across multiple systems.
- Exploiting Misconfigured MFA: Ways to bypass or exploit misconfigured MFA include:
- MFA fatigue attacks (bombarding users with MFA prompts) (T1621)
- Exploiting vulnerabilities in MFA implementations
- Exploiting Default Credentials (T1078.001): Checking for default credentials on systems and applications, especially on medical devices and legacy systems.
- Weak Passwords (T1110): Attempts to crack weak passwords using various tools and techniques.
Mitigation and Hardening
- Implement Strong MFA: Enforce MFA on all web applications, remote access solutions, and systems that contain sensitive data. FIDO2-compliant MFA is strongly recommended and should be applied whenever possible.
- Enforce Strong Password Policies: Implement and enforce strong password policies that require complex passwords and regular password changes. Prohibit the use of default or common passwords.
- Account Lockout Policies: Implement account lockout policies to prevent brute-force attacks.
- Credential Monitoring: Monitor for compromised credentials using threat intelligence feeds and security tools.
- Regular Audits: Conduct regular audits of authentication configurations and password policies.
- Conditional Access Policies (CAPs): Implement CAPs to enforce stricter authentication requirements based on context, such as location, device, or user behavior.
Observation 2: Virtual Environment Breakouts
Many healthcare organizations are opting for their medical workforce to adopt a virtual desktop infrastructure (VDI) environment. While this has many benefits and empowers healthcare professionals, these virtual environments need to be securely configured to prevent malicious use of system administration tools. Most of these tools or functions are behind layers of security, but determined attackers are breaking out of these environments. This allows the attacker access to the underlying system or server hosting that virtual workstation. Some of these break outs are as similar as trying to print a document.
Attack Paths
- Exploiting VDI Software Vulnerabilities (T1611): Looking for known vulnerabilities in the VDI software or hypervisor that can be exploited to gain access to the underlying host system.
- Misconfigurations: Identifying and exploiting misconfigurations in the VDI environment, such as:
- Insufficient isolation between VDI sessions
- Lack of proper access controls
- Insecure file sharing or clipboard settings
- Abusing System Administration Tools (T1548): Attempting to abuse legitimate system administration tools within the VDI session to gain elevated privileges or access to the host system. This can involve:
- Exploiting vulnerabilities in these tools
- Using them in unintended ways to bypass security controls
- Leveraging them to execute malicious code
- Printer Exploits (T1068): Using printer exploits to gain access to the host system. This can involve exploiting vulnerabilities in printer drivers or using printer functionality to execute malicious code.
Mitigation and Hardening
- Keep VDI Software Up to Date: Regularly patch and update VDI software and hypervisors to address known vulnerabilities.
- Secure Configuration: Implement secure configuration settings for the VDI environment, including:
- Strong isolation between VDI sessions
- Proper access controls
- Secure file sharing and clipboard settings
- Principle of Least Privilege
- If possible, make VDI endpoints ephemeral so malware cannot persist in the environment if other security controls fail
- System Administration Tool Restrictions: Restrict access to system administration tools within VDI sessions. Implement application allowlisting or other controls to prevent the execution of unauthorized software.
- Printer Security: Secure printers and printer drivers. Disable unnecessary printer functionality.
- Intrusion Detection: Implement intrusion detection systems (IDS) to monitor VDI environments for suspicious activity.
- Regular Testing: Conduct regular penetration tests to identify and address vulnerabilities in VDI environments.
Observation 3: Understand How Ransomware Operates
Google Threat Intelligence Group (GTIG) assesses with high confidence that financially motivated cyber crime represents a very high-frequency and serious to catastrophic threat to healthcare organizations worldwide and will continue to do so for the near to mid-term. Both 2024 and 2025 saw significant ransomware incidents in the healthcare sector that negatively impacted patient care.
Most ransomware spreads through specific network services or ports, usually the same ones used for legitimate network operations. Mandiant takes a holistic approach when performing red team assessments for healthcare organizations, looking not only at those network services, but also how they interact with users and file shares. Oftentimes Mandiant identifies overly permissive file shares or user permissions that allow ransomware to encrypt or propagate in areas that ransomware simulators cannot access.
Healthcare organizations must go beyond simply having a ransomware response plan, and instead actively test their defenses—including network segmentation and access controls—to identify and close gaps. Mandiant’s Red Team highly recommends regularly testing backup and recovery procedures, paying considerate attention to immutable backups. Ransomware-related events accounted for just over one-fifth (21%) of all Mandiant incident response investigations in 2024, as shown in figure three.
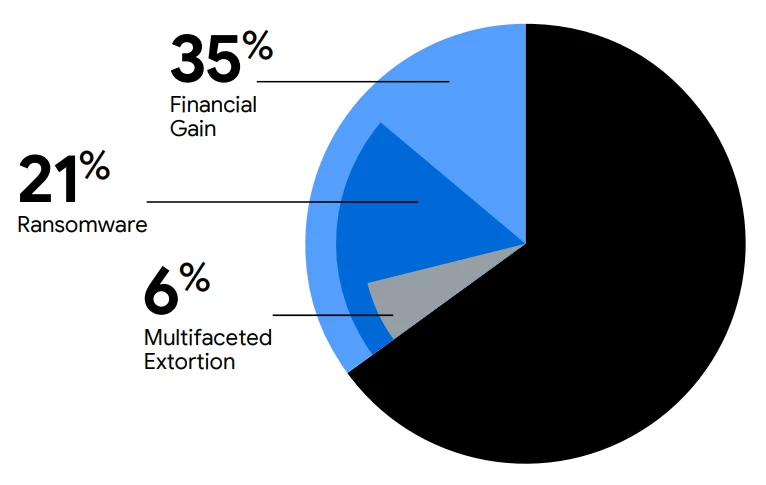
Figure 3: Ransomware-related events drove 21% of Mandiant’s incident response in 2024
Attack Paths
- Exploiting Vulnerabilities for Initial Access (T1190): Exploiting vulnerabilities in systems and applications to gain initial access to the network.
- Lateral Movement (TA0008) and Privilege Escalation (TA0004): Using techniques to move laterally within the network and escalate privileges, which is how ransomware spreads and gains access to more systems.
- File Share Enumeration and Abuse (T1135): Identifying and exploiting overly permissive file shares and user permissions, which is how ransomware can quickly encrypt data across the network.
- Disabling Security Controls (T1562): Disabling or bypassing security controls, such as antivirus software or EDR, which is how ransomware can evade detection.
- Data Exfiltration (TA0010): Ransomware attacks often involve theft of sensitive information.
Mitigation and Hardening
- Vulnerability Management: Implement a robust vulnerability management program to identify and patch vulnerabilities in systems and applications.
- Network Segmentation: Implement network segmentation to limit the spread of ransomware.
- Host Based Firewalls: Prevent lateral movement to sensitive systems, network segments, specific subnets.
- Access Control: Enforce the principle of least privilege and implement strong access controls to restrict user access to sensitive data and systems.
- Endpoint Detection and Response (EDR): Deploy EDR solutions to detect and respond to ransomware activity on endpoints.
- File Share Security: Secure file shares and user permissions to prevent unauthorized access and encryption.
- Backup and Recovery: Implement a robust backup and recovery plan with immutable backups to ensure data can be restored in the event of a ransomware attack.
- Incident Response Plan: Develop and regularly test a comprehensive incident response plan for ransomware attacks.
- Honey Pots: Consider implementing a honey pot for early detection of potential ransomware activities. Canaries configured to alert on these honey pots can increase the responsiveness and efficiency of responders.
Observation 4: Network Segmentation Matters
Mandiant's Red Team assessments consistently reveal that a lack of robust network segmentation is a significant vulnerability within healthcare organizations. This issue is frequently exacerbated by the industry's trend of mergers and acquisitions, which often leads to poorly integrated networks and an increased attack surface.
Key issues observed include:
- Flat Networks and Lack of Segmentation: Many healthcare environments operate with flat networks or insufficient segmentation, allowing attackers to move laterally with ease once they gain initial access. This frequently includes sensitive medical devices that are not fault-tolerant to network probing or attacker activity. This means that a breach in one area of the network can quickly lead to compromise of critical systems and data elsewhere.
- Insecure Interconnections: Mergers and acquisitions often result in the rapid and insecure interconnection of networks. Red Teams frequently encounter issues such as:
- Insecure Bidirectional Trusts: To expedite integration, organizations may implement bidirectional Active Directory trusts without properly assessing the security implications. These trusts can provide attackers with unintended access and the ability to pivot between networks.
- Overly Permissive Firewall Rules: Similar to insecure trusts, overly permissive firewall rules are often put in place to maintain operational functionality post-acquisition, but they weaken security posture.
- Difficulty in Enforcing Security Boundaries: The complexity of healthcare environments, with a mix of legacy systems, medical devices, and various departments, makes it challenging to implement and enforce effective network segmentation.
Attack Paths
- Lateral Movement (TA0008): Techniques to move between network segments include:
- Trust Abuse (T1482): Insecure trust relationships, such as bidirectional Active Directory trusts, enable gaining access to resources in different domains or forests.
- Firewall Bypass: Attempts to bypass firewall rules or segmentation controls by:
- Exploiting misconfigurations
- Using application-layer protocols to tunnel traffic (T1090)
- Leveraging vulnerabilities in firewall devices
- VLAN Hopping: Techniques to move between VLANs without proper authorization.
Mitigation and Hardening
- Medical Devices: Many medical devices require around-the-clock availability, and should be constrained to sensitive enclaves to avoid any inadvertent network activity that could disrupt patient care. Medical devices also commonly operate with little to no encryption, posing as great initial vectors (T1040) for attackers and red teamers. Extra care should be taken when isolating and securing medical devices.
- Network Segmentation: Design and implement a robust network segmentation strategy that divides the network into logical zones based on function, sensitivity, and risk.
- Zero Trust Architecture: Consider adopting a Zero Trust security model, which assumes that no user or device can be trusted by default, even those inside the network perimeter.
- Firewall Configuration: Implement and enforce strict firewall rules that control traffic flow between network segments. Regularly review and update firewall rules to ensure they are still effective.
- Active Directory Security: Secure Active Directory environments, including:
- Implementing the principle of least privilege
- Securing trust relationships
- Monitoring for suspicious activity
- Intrusion Detection and Prevention Systems (IDS/IPS): Deploy IDS/IPS at network segmentation points to detect and prevent unauthorized access or lateral movement.
- Network Monitoring: Implement comprehensive network monitoring to detect anomalous traffic patterns and potential breaches of network segmentation.
- Microsegmentation: Consider implementing microsegmentation to further isolate critical assets and applications.
Observation 5: Social Engineering is Stronger than Ever
Mandiant red teamers have had high success impersonating help desk employees (as well as nurses and doctors) within healthcare settings. AI-powered voice phishing (vishing) has increased the believability of many of these social engineering attacks. When social engineering is combined with payload detonation or credential harvesting, it increases the foothold an attacker has within your network.
Attack Paths
- Phishing Emails (T1566): Crafting highly targeted phishing emails designed to mimic legitimate communications from within the healthcare organization or from trusted third parties. These emails often contain malicious attachments or links that, when clicked, deliver malware or redirect users to phishing websites. A common threat emulation that Mandiant’s Red Team will perform is malware impersonation of legitimate VDI solutions or third-party medical devices/technologies.
- AI Voice Phishing (Vishing): Use of voice spoofing technology to impersonate IT support, help desk personnel, or even executives. Calls to employees may request credentials or sensitive information, or trick them into installing malicious software. Learn more about this vishing technique.
- SMS Phishing (Smishing): Similar to vishing, except SMS messages are used to deliver phishing attacks. These messages may contain links to malicious websites or encourage users to call a phone number for further social engineering.
- In-Person Impersonation: Impersonate vendors or IT staff to gain physical access to facilities or systems. This can involve wearing uniforms, using fake IDs, or social engineering their way past security checkpoints.
- Targeting the Help Desk: Help desk employees are regularly targeted due to their access to account reset tools and other sensitive information. Social engineering techniques are used to convince help desk staff to grant access to accounts or systems (T1078). Learn about browser-in-the-middle attacks, (T1649) which aid in successful social engineering attacks against help desk employees.
Mitigation and Hardening
- Robust Security Awareness Training: Implement comprehensive security awareness training that covers various social engineering tactics, including phishing, vishing, and smishing. Emphasize the importance of verifying requests for credentials or sensitive information.
- Phishing Simulations: Conduct regular phishing simulations to test employee awareness and identify those who may be vulnerable to attacks. Track results and provide targeted training to employees who fail simulations.
- Help Desk Security: Implement strict verification procedures for help desk operations, especially for password resets or remote access requests. Require multiple forms of verification and log all help desk activity. Mandiant can work with you and your team to test your help desk policies via tailored social engineering assessments to validate the efficacy of your controls and policies.
- Email Security Solutions: Deploy advanced email security solutions with threat protection to filter out phishing emails and detect malicious attachments or links.
- Voice and SMS Security: Educate employees about the risks of vishing and smishing. Implement measures to verify the authenticity of phone calls and SMS messages, such as verifying the caller or opting for alternative secure communication channels.
- Physical Security: Implement strong physical security controls to prevent impersonation, such as access control systems, security cameras, and employee training on identifying suspicious individuals. Mandiant commonly gets requests to perform physical security assessments of Healthcare organizations, including hospitals, patient rooms, and anywhere sensitive data, assets, or network connections are exposed.
Conclusion
Healthcare organizations can significantly improve their resilience against cyberattacks by focusing on understanding the key areas outlined in this blog post, and implementing the recommended mitigation and hardening strategies. Proactive security measures, combined with a deep understanding of attacker tactics, are essential for protecting patient safety and data in the face of evolving threats. If you are interested in having any of your security controls, policies, or procedures tested and technically validated please check out Mandiant’s Red Team Services for more details.
