Google Cloud Security Community,
In this community blog, let’s take a closer look at network fingerprinting and how we can leverage Google Threat Intelligence (GTI) to search for IOCs that match what’s known as a JA4 fingerprint. We’ll explore this topic in detail and end with an exercise that puts this information to practical use in GTI.
The nature of encrypted communication makes it difficult to derive information about the content of the resulting communication stream. This is where fingerprinting techniques like JA4 come into play, offering a powerful way to gain visibility into encrypted traffic without the need to perform decryption or eavesdrop on the traffic itself.
Let's dive into what JA4 is and how it helps us better understand the clients connecting to our services.
What is a JA4 Fingerprint?
At its core, a JA4 fingerprint is a 36-character identifier for a client's SSL/TLS configuration. It's an evolution of the earlier JA3 method, designed to be more robust and accurate in identifying the specific software stack initiating a secure connection. It’s one of multiple fingerprinting methods in the JA4+ suite.
When a client (your browser, an application, or even malware) wants to establish a secure connection, it first sends a TLS Client Hello packet. This initial, unencrypted handshake message contains a wealth of information about the client's preferred TLS capabilities – what TLS versions it supports, its preferred cipher suites, extensions, and more. The JA4 algorithm takes this information and distills it into a structured string.
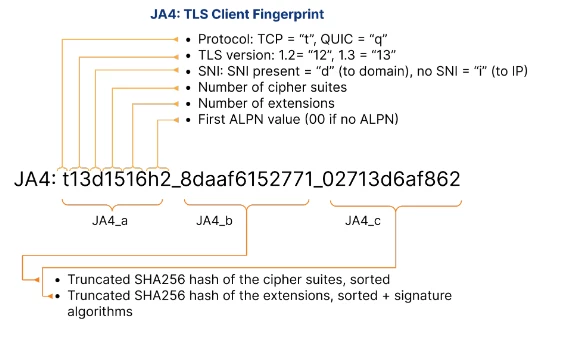
http://blog.cloudflare.com/ja4-signals/
JA4 fingerprints identify the Client, Not the Server
A crucial point to remember is that the JA4 fingerprints represent the client.
It's generated solely from the information the client sends in its initial TLS Client Hello packet. This makes it a fantastic tool for identifying the specific client software, its underlying operating system, and the TLS library configuration it's using.
Can Multiple Clients Have the Same JA4 Fingerprint? (Yes, and that's the point!)
This is a common and important question. The answer is yes. A JA4 fingerprint is not designed to uniquely identify an individual device or user. Instead, it identifies the TLS application stack used by the client. This means that JA4 provides a high-fidelity signature for the specific libraries and configurations used by client software, which provides critical information about the configuration of the client, even if the subsequent communication in transit is encrypted. This allows analysts to identify and track malicious or anomalous activity without needing to decrypt the session content.
Why This is Incredibly Useful for Security Teams:
Security professionals leverage this shared characteristic for the following:
Malware and Bot Detection
Malware often uses unique or custom-built libraries for its network communication (e.g., Command and Control (C2) traffic). These specific libraries generate a consistent, unique JA4 fingerprint.
Threat Hunting
A threat hunter can discover a single instance of a suspicious JA4 fingerprint and then pivot their search across all network logs to find every other connection that shares that exact same fingerprint.
Grouping Adversaries and Tools
Because the fingerprint is tied to the client's underlying software stack (e.g., the programming language, OS, or specific version of a library), it can group seemingly unrelated network connections to the same threat actor or malware family.
Rate Limiting and Access Control
In edge devices like Web Application Firewalls (WAFs) and load balancers, JA4 is used to enforce rules based on the client's identity rather than just its IP address, which is crucial for defending against distributed attacks.
The Broader JA4+ Ecosystem
It's also worth noting that JA4 is part of a larger suite called JA4+, which aims to provide even more comprehensive network fingerprinting:
- JA4 (Client): The client's TLS Client Hello.
- JA4S (Server): A complementary fingerprint derived from the TLS Server Hello packet, representing the server's chosen TLS configuration for that session.
- JA4H (HTTP): Fingerprints for HTTP/1 and HTTP/2 characteristics, further enhancing identification.
JA4 in Google Threat Intelligence
In GTI, some IOCs will have a JA4 fingerprint associated with them. You can find this value by navigating to the Behavior tab for an IOC and expanding the TLS node(s) under Network Communication.
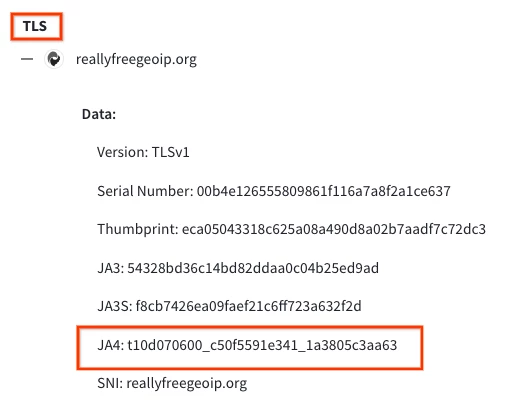
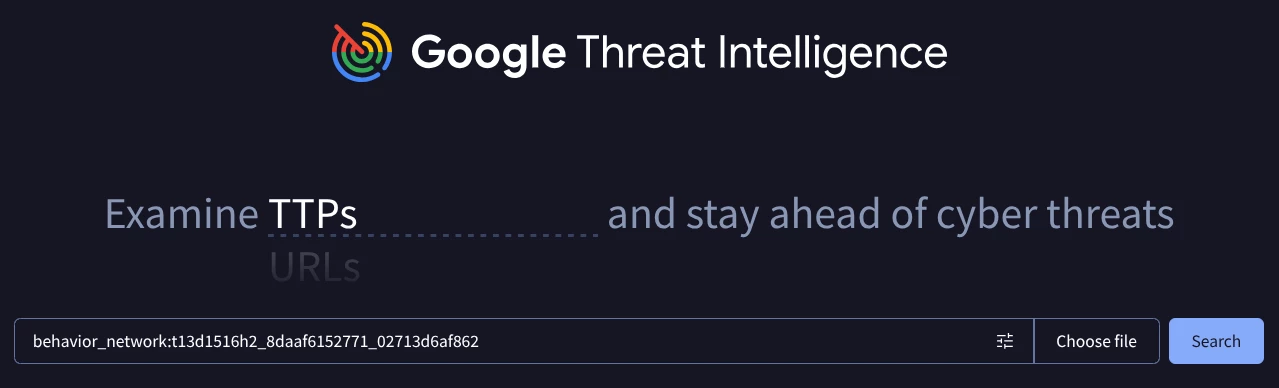
You can search for a specific JA4 fingerprint using the behavior_network search modifier.
For example: behavior_network:t13d1516h2_8daaf6152771_02713d6af862
Exercise
Let’s walk through an example where we investigate a specific JA4 fingerprint. We’ll follow this up with an exercise where you can put your skills with JA4 to use in Google Threat Intelligence.
In a post on the VirusTotal blog from October 2024, we see an example JA4 fingerprint value of t10d070600_c50f5591e341_1a3805c3aa63.
The blog describes the process of pivoting to a search based on this fingerprint by clicking the fingerprint value within the TLS section of the Behavior tab for the IOC. The resulting IOCs show a mixture of GTI scores and filenames, indicating that these files share a common TLS implementation even if the actual files themselves vary and might have entirely different hashes.
Now let’s put these skills to use in GTI. Can you use GTI to answer the following questions about the following JA4 fingerprint?
t12d240700_9295eb73ea51_71440d09e7ee
- How many IOCs are associated with this JA4 fingerprint in Google Threat Intelligence?
- How many of those IOCs are malicious?
- What is the highest score among those IOCs?
- How many of the IOCs were seen in the last month, and also have 5 or more detections?
- Does GTI attribute a score to the fingerprint?
- Which TLS version is associated with this fingerprint?
- Which section of the fingerprint did you use to determine this?
- How many cipher suites are associated with this fingerprint?
- Which section of the fingerprint did you use to determine this?
Closing Thoughts
What are your thoughts on JA4? Have you implemented it in your security operations, or do you see potential for its use in your environment? Share your insights below!


