Special thanks to Alexa Rzasa
- Shadow IT & Unknown Assets

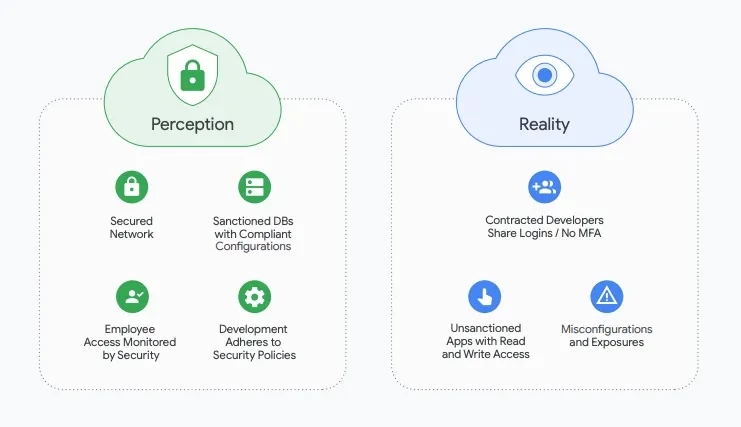
Mandiant ASM begins with known assets like DNS data, IP address, URIs, etc., and expands to uncover "shadow IT" – resources existing outside standard IT practices. Examples include:
- Outdated marketing websites with security flaws
- Internal login pages mistakenly exposed to the internet
- SaaS plugins lacking multi-factor authentication (MFA)
- Legacy technologies running on neglected infrastructure
Mandiant ASM uses the known assets provided or an integration into a DNS zone to perform recursive discovery, fingerprint and analyzes technologies running on your infrastructure, flagging unmanaged assets, or unsanctioned technologies. This might reveal unexpected instances of WordPress, GlobalProtect with default credentials, or outdated software like Microsoft Lynx.
Beyond identifying shadow IT, Mandiant ASM validates findings like vulnerabilities, misconfigurations, and other exposures.
Equipped with this information, you can coordinate remediation efforts. Often, this involves patching or updating software after determining the responsible owner. However, some cases require hardening and custom solutions due to dependencies on older technologies where remediation is impractical.
You can find documentation for Workflow creation below, and External Discovery and Assessment should be selected for this Use Case https://docs.mandiant.com/home/asm-create-a-collection
- Hybrid & Multi-Cloud Vulnerabilities

In the realm of External Attack Surface Management (EASM), the cloud poses a specific concern regarding potential exposure. The primary focus lies in identifying externally exposed cloud assets, particularly misconfigurations like open storage buckets. Ideally, there should be minimal findings in this area, as most cloud infrastructure is not intended for external access.
You can find documentation for Workflow creation below, and Authenticated Cloud Discovery & Assessment should be selected for this Use Case https://docs.mandiant.com/home/asm-create-a-collection
- Leaked Secrets in Code Repositories

Code repositories pose significant risk, often due to external contractors who may fork code or maintain repositories containing company-owned code without adhering to internal security procedures. This can introduce vulnerabilities into your system.
Scanning both internal and public repositories is crucial. Look for exposed keys and phrases that might lead to relevant repositories.
To minimize risk, security teams should implement the following practices continuously:
- Scan for secrets: Use specialized or open-source tools to detect sensitive information within code repositories.
- Enforce pre-commit hooks: Ensure all committed code undergoes secret scanning before being integrated.
- Enable logging: Maintain detailed logs of activities within code repositories.
- Purge commit history: Remove any past code commits containing secrets to eliminate historical risks.
- Enforce MFA: Require multi-factor authentication for all users to enhance access security.
- Create IP allowlists: Restrict access to code repositories to trusted locations only.
- Disable public repositories: Prevent users from creating publicly accessible repositories.
- Disable forking: Restrict users from creating copies (forks) of existing repositories.
- Regular SAST & DAST scanning: Conduct both static and dynamic application security testing to identify vulnerabilities in your codebase.
You can find documentation for Workflow creation below, and Code Repository Discovery and Assessment should be selected for this Use Case https://docs.mandiant.com/home/asm-create-a-collection
-
Third-Party Monitoring
The more third-party vendors your organization works with, the more avenues of potential risk that the security team should consider. A vulnerability in a vendor's system could expose your customer or employee data, or even disrupt your business operations if their infrastructure fails. This makes them a critical component of your extended attack surface.
To manage this risk, you need to understand the vendor's security practices and assess the potential impact they could have on your organization. This involves evaluating their attack surface, albeit at a less granular level than you would for your own assets.
Mitigation strategies depend on your relationship with the vendor. Continuous monitoring and open communication are key. If a vendor consistently introduces significant risk, you might need to adjust the terms of your relationship and restrict data sharing.
Mandiant ASM customers who want to monitor suppliers can subscribe to three read-only third-party Collections.
You can find documentation for Workflow creation below, and Third Party Monitoring should be selected for this Use Case: https://docs.mandiant.com/home/asm-create-a-collection
- Potential Domain Typosquats
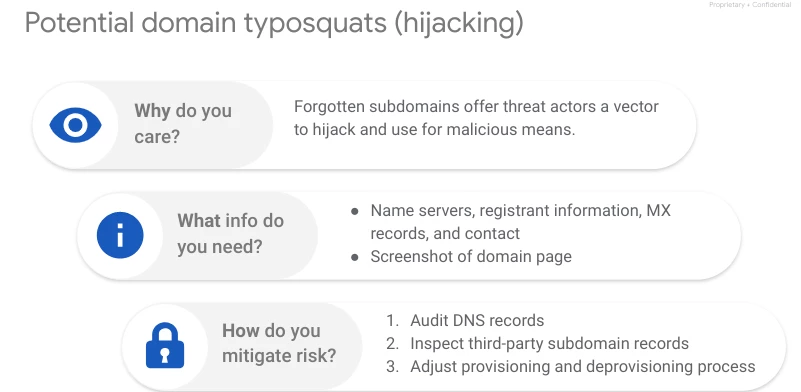
Typosquatting encompasses a range of risks, from hijacked domains to brand impersonation aimed at phishing. To assess the threat level, it's crucial to analyze the site's content. Mere brand impersonation, while undesirable, doesn't pose a direct security risk, unlike phishing attempts. For instance, a company might clone your website to steal business, as happened at a digital agency, rather than engage in phishing.
Key indicators of malicious intent include:
- Site content: Does the site closely resemble your own, using stolen graphics?
- MX records: Does the site have mail setup, suggesting a higher level of malicious activity?
- Website host and owner: Identifying these helps in remediation efforts.
To mitigate hijacking risks, conduct regular DNS audits and ensure a robust deprovisioning process for domains. Takedown services, requiring information like the website host and proof of infringement, offer effective solutions to address typosquatting issues.
The following guidance serves to help security teams maintain strong DNS hygiene:
- Audit DNS Records
- Amass / Aquatone / Sublist3r
- Remove stale CNAME records from DNS Zone file
- Inspect third-party subdomain records
- Create a unique TXT record
- Enforce entropy in instance names
- Disallow clients from reclaiming name
- Listening to wildcard DNS
- Revamp the provisioning and deprovisioning process for subdomains
- Create the instance first, then create subdomain and point it to instance
- Remove the CNAME record first, then delete the instance
You can find documentation for Workflow creation below, and Suspicious Domain Discovery should be selected for this Use Case: https://docs.mandiant.com/home/asm-create-a-collection
- Fake Branded Apps
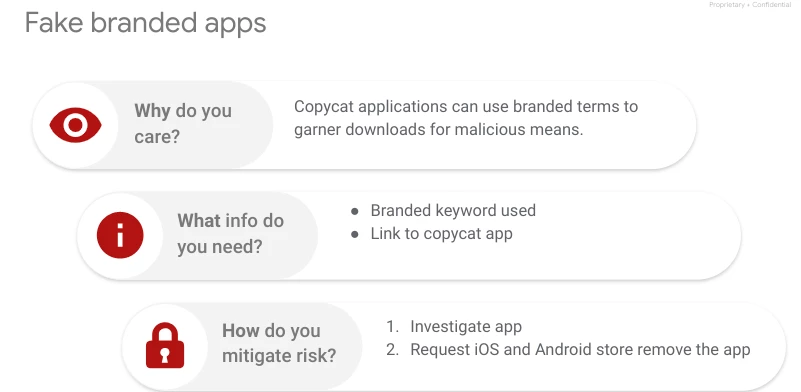
While mobile app stores are often considered secure, malicious apps can still slip through, offering free services to lure users. This raises concerns about user safety across both Play and iOS stores, highlighting how brand infringement can escalate into a security risk when malicious actors exploit this loophole.
Interestingly, some apps become malicious after being approved, especially those using a web app wrapper based on HTML. This allows changing the HTML code without requiring a new app submission, effectively bypassing security checks.
Organizations can uncover such threats by searching for apps using their brand keywords. If found, details like the app name, developer, and a link to the store can be used to report the issue through the app store's support channels.
You can find documentation for Workflow creation below, and Mobile App Discovery should be selected for this Use Case https://docs.mandiant.com/home/asm-create-a-collection
-
Merger & Acquisitions and subsidiary monitoring
For organizations that need to assess the security hygiene of an acquisition target, you can gain visibility into unknown systems and a comprehensive asset inventory. Your security team can define and enforce security posture requirements before and after the deal closes, mitigating risks and ensuring a smooth transition. We recommend customers use the standard External Discovery and Assessment workflow to capture a view of the acquisition target’s posture.
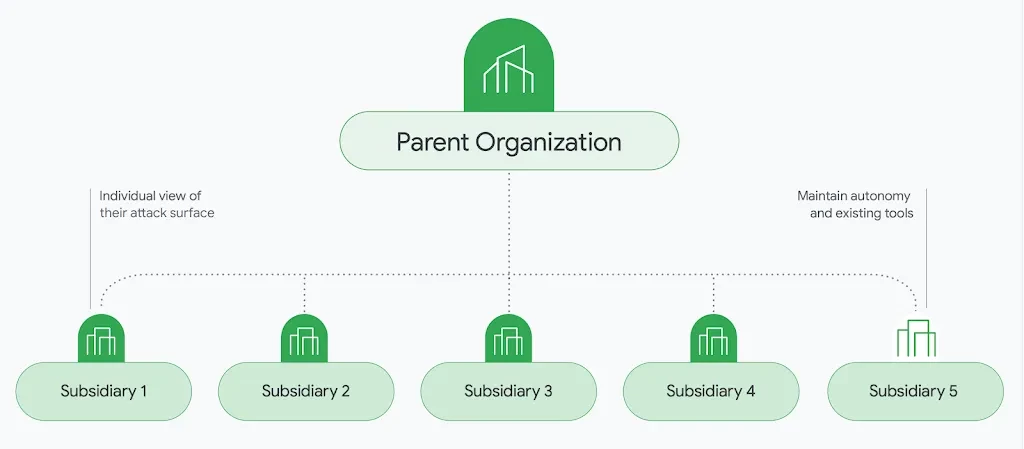
Organizations with numerous independent or semi-independent subsidiaries face extended portfolio risk. While it's crucial to understand the conglomerate's overall risk, managing each subsidiary's infrastructure and security controls can be impractical. Mandiant ASM offers role-based access control (RBAC) and hierarchy system with Projects and Collections to empower each subsidiary to independently monitor and manage its attack surface while providing centralized visibility for the parent organization. This enables you to assess the risk posed by each subsidiary without compromising their operational independence.