Co-Authors: Vinod D’Souza, Sri Gourisetti
In today's dynamic manufacturing landscape, a strategic, threat-informed, and risk-centric approach to security is essential to align with overarching business goals and safeguard operations. This blog explores the multifaceted challenges and proactive strategies that fortify defenses to support business objectives.
In the previous blog of the Security Inclusive Site Management blog series, the CISO’s first principle was discussed along with a CISO’s role in manufacturing transformation. This blog builds upon that narrative focusing on a strategic and operational approach to security.
Manufacturing security: A CISO’s strategy and operations
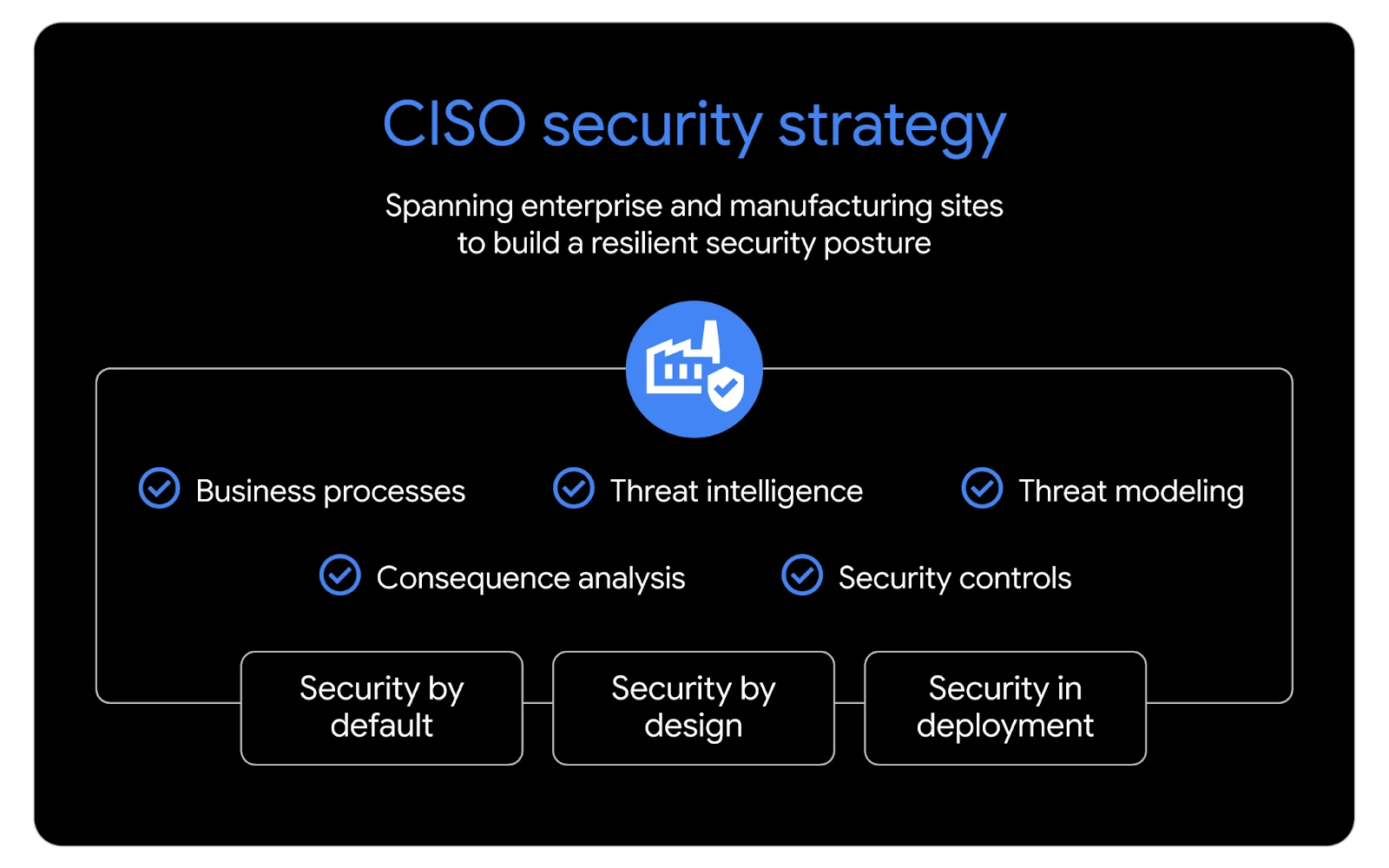
There needs to be strategic and operational alignment between security, manufacturing, and digital goals. CISO’s security strategy spanning across the enterprise and all manufacturing sites should be to achieve cyber-physical resilience to meet the business objectives. Resilient security posture is built on a combination of business processes, threat intelligence, threat modeling, consequence analysis, and security controls. CISOs must apply security by default, security by design, and security in deployment to ensure safety, productivity, and availability of manufacturing processes. To ensure operational resilience, CISOs must strike a balance between proactive and reactive security strategies across the enterprise and the manufacturing sites or factories.
If chief manufacturing officers (CMOs) are the revenue generators, CISOs are the revenue protectors of the organization. To show a clear business benefit, the manufacturing CISOs must integrate any security threat mitigations with the business objectives of a CMO, chief quality office (CQO), and the chief risk officer (CRO), In some cases, this extends to gaining buy-in from the chief legal officer (CLO), chief operating officer (COO), and the chief financial officer (CFO).
CISOs should define the security objectives and achievements in business-friendly terms for senior business leaders and board members. For example, instead of discussing patched vulnerabilities, explain how patching improves system reliability and uptime, which in turn directly protects revenue. This strategic alignment demonstrates how security contributes to resilient and reliable manufacturing operations.
In Manufacturing, CISOs face a complex environment of enterprise and industrial operations, engineering processes, and supply chain management. Therefore, manufacturing CISOs are responsible for enterprise and information security, as well as factory, industrial, operational, and physical security. To optimize their efforts, manufacturing CISOs must define security’s goals across all strategic pillars, ensuring they are aligned with organizational goals and have measurable outcomes.
Leveraging threat intelligence and threat modeling combined with consequence/impact analysis allows the CISOs to approach Security in a repeatable, risk-based, and objective manner. For example, if a company is opening a new factory or a site, the CISO should collaborate with the site leadership to understand the production processes and business goals, the IT and OT systems that will be implemented, equipment and staff that will be on site, and the suppliers and integrators that will be used. The CISO's team should then evaluate threat intelligence to evaluate the current threat landscape in light of the new factory or site operations. The security team should then perform threat modeling to ensure that the identified threats and pertinent risks are mitigated. The CISO's team should also ensure that as the factory is being equipped, that the right security telemetry and controls are implemented to ensure that operations remain well monitored and anomalies detected.
Manufacturing faces both malicious and unintentional threats. Unintended threats often occur when organizations modernize operations without security best practices like threat modeling, risk assessments, and red teaming, while maintaining legacy systems across geographically distributed factories or sites. This often leads to fragile integration, causing systems to ultimately fail. This is the equivalent of what is an "own goal" in soccer – something that could have been potentially avoided.
Malicious threats are those caused by adversaries, motivated by a number of reasons such as financial gain, espionage, political and ideological objective, to name a few. CISOs will continue to face skilled adversaries, while trying to manage the convergence of IT and OT systems and networks. Because these environments are hard to change once in operations, it drives a need for strong proactive security using appropriate threat intelligence.
CISO’s teams can use security standards (e.g., NIST CSF, 800-53, 800-82, CIS Benchmarks, IEC 62443 or a combination) and threat modeling frameworks (such as using STRIDE, MITRE ATT&CK - Enterprise and ICS, Security PHA, or similar) to assess these changes and identify the necessary security measures.
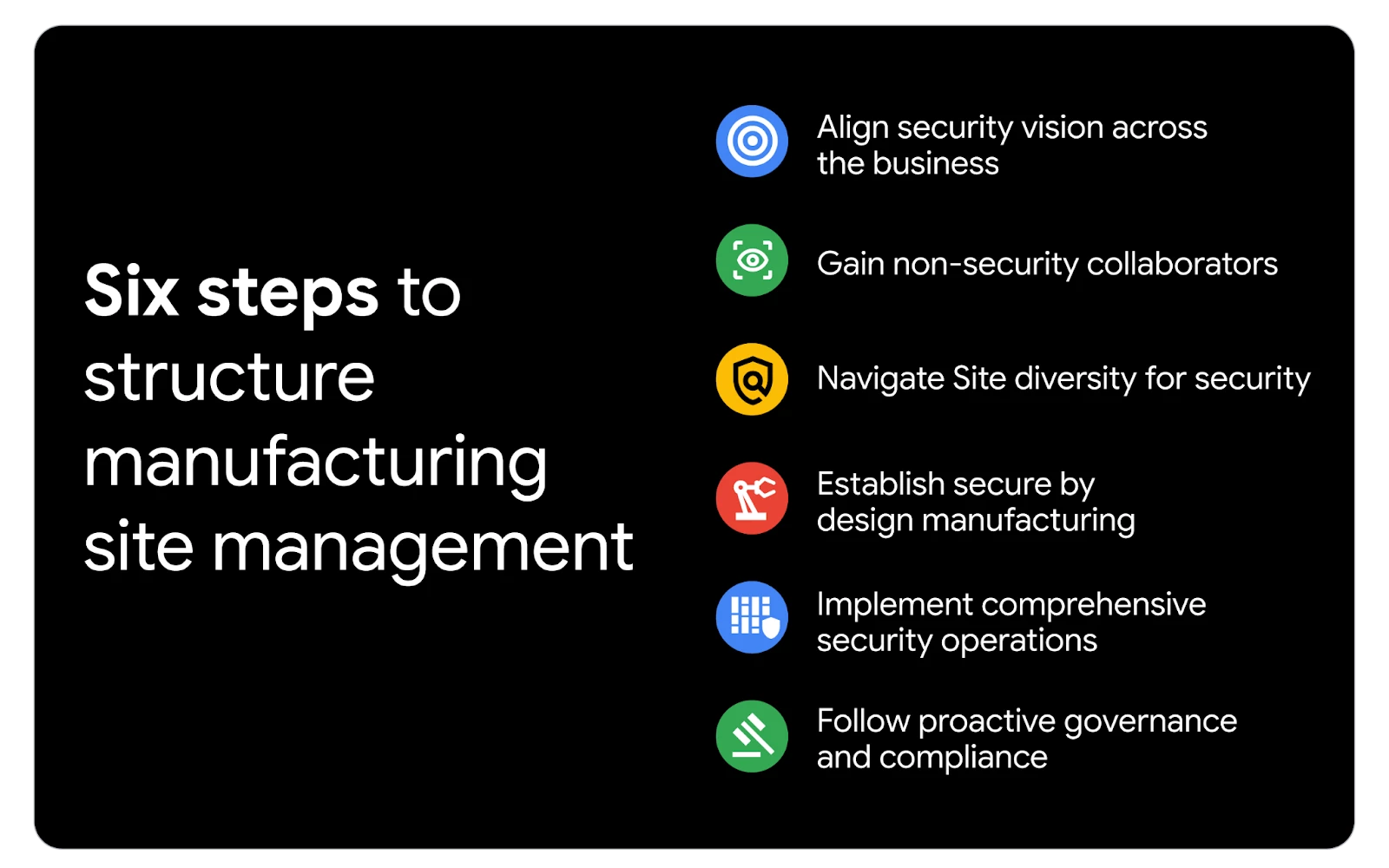
At an operational level, processes and supporting technologies like Google Cloud’s Control Navigator, Compliance Manager, Audit Manager in Security Command Center, and Security Posture Assessment can be instrumental in this process. Adhering to the security first principles, CISOs can structure their site management strategy around the following facets:
-
Business-Aligned Security Vision: Define the security vision, mission, roadmap, short-term, and long-term goals in close alignment with the CMO and CD/TO. To effectively support any transformation they drive, CISOs must first thoroughly understand the business goals, objectives of their manufacturing sites, and identify the most critical processes and systems. Empower the security teams to analyze how these systems connect and the data flows essential to operations. The security teams must then determine which systems and applications could move to the cloud and how this will change the organization's risk, potential attack surface, and overall business impact.
-
Gain non-security collaborators: From an operational lens, a CISO must collaborate with the non-security teams to identify personnel to collaborate with the security teams. In doing so, security becomes an intrinsic and organic component of all decisions impacting the enterprise, from high-level strategic initiatives to site-specific factory operations. Furthermore, the security and non-security personnel can cross-learn and gain new unique perspectives. For instance, consistent collaboration between product quality and security teams fosters mutual understanding of objectives and challenges, educating both on their respective perspectives and building empathy and alignment for each other's roles.
-
Navigate Site diversity for security: A manufacturing enterprise typically comprises multiple sites, each with distinct functions—from production and packaging to storage. These sites often house diverse systems and processes; while the enterprise-level IT infrastructure may be consistent, the industrial operational technology (OT) layer frequently varies significantly. This complexity is further exacerbated by growth through mergers and acquisitions, leading to substantial differences in hosted systems, processes, and site operating models. Therefore, CISOs must possess a thorough understanding of these unique sites to design effective and tailored security strategies and operations.
-
Secure by Design Manufacturing: Ensure security is integrated into ideation, design, architecture, integration, and testing (e.g., site acceptance testing (SAT) and factory acceptance testing (FAT) phases across manufacturing and factory floor automation from the outset. This implementation ensures secure deployment and development of systems.
-
Comprehensive Security Operations: Implement Security Operations that encompass all four strategic pillars discussed earlier, staffed with IT, OT, and cloud expertise to address the unique security needs of manufacturing. These operations should be demonstrably contributing to business objectives.
-
Proactive Governance and Compliance: Ensure autonomous and proactive alignment with governance, risk, compliance, regulatory, and legal requirements, with a goal to demonstrate business continuity and reliability. This includes establishing policies, procedures, guidelines, and tooling to ensure a strong security program.
A threat-informed, risk-centric approach to security is not merely a recommendation but an absolute necessity in the manufacturing sector. CISO should align security strategies with business goals to ensure that security efforts translate to tangible business benefits. By adopting a proactive stance, integrating security into design, and fostering a culture of security awareness, organizations can build resilient operations that can withstand the evolving threat landscape. In the next blog of this series, we will discuss the tactical security approach to safe manufacturing operations.
