Special thanks to Sid Shibiraj and Pradeep Nair for their contributions to this blog.
In today's rapidly evolving threat landscape, robust security measures are paramount. Google Cloud Next Generation Firewall (NGFW) Enterprise and Security Command Center (SCC) Enterprise are cloud-native security solutions that provide network protection, threat detection, and built-in response capabilities ,including case management and playbooks. This blog will detail how you can integrate threat findings from NGFW with SCC to help you improve your cloud security posture.
Understanding Cloud NGFW Enterprise
Cloud NGFW Enterprise is a fully distributed, cloud-native firewall service that provides stateful advanced threat protection. Its micro-segmentation capabilities allow for granular control over network traffic, enhancing your ability to isolate and protect critical workloads. NGFW Enterprise provides advanced Intrusion Detection and Prevention Service (IDPS) capabilities, powered by Palo Alto Networks technology, and includes vulnerability, anti-spyware and antivirus signatures capabilities.
Cloud NGFW Enterprise can also be configured as an Intrusion Detection System (IDS) to monitor and log potential threats without actively blocking traffic.
The Power of Security Command Center Enterprise
Security Command Center (SCC) Enterprise is a cloud security and risk management solution. It offers native Google Cloud log ingestion, including the ability to seamlessly ingest Cloud NGFW firewall and threat logs. SCC Enterprise includes built-in parsers that automatically map these logs to the unified data model, simplifying analysis and correlation.
Streamline your detection and response with NGFW and SCC
Integrating Cloud NGFW Enterprise with SCC Enterprise helps you to streamline cloud security operations by combining network threat detection in NGFW Enterprise with the security automation and response capabilities in SCC. Here's how it works:
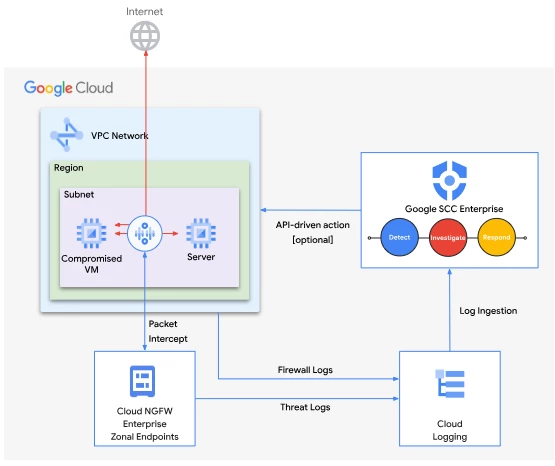
- Network Threat Detection: Cloud NGFW Enterprise identifies a potential threat, and logs an event in Cloud Logging which will be exported to SCC Enterprise.
- Unified view: SCC Enterprise automatically ingests this log entry. The built-in parser maps the log fields to the Unified Data Model structure, ensuring consistency and ease of analysis.
- Prioritized findings: You can create custom detection rules within SCC Enterprise to identify specific events of interest. These rules generate alerts, which will be aggregated into actionable cases.
- Automated response: Playbooks can be attached to cases for automated response. For instance, a custom playbook might automatically add an IAM-governed tag to a compromised workload, isolating it for further investigation or remediation.
Sample Integration Workflow for Threat Findings
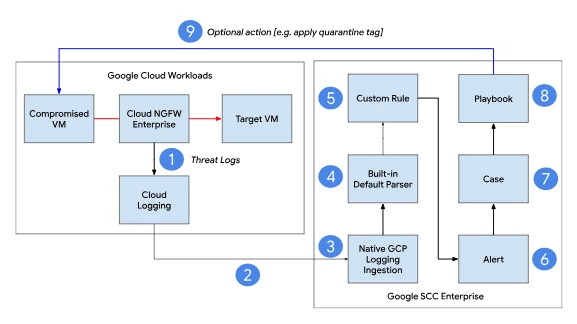
Google Cloud’s NGFW Enterprise and SCC Enterprise can be seamlessly integrated in your environment without any additional agents or software. As per the workflow diagram above, once Cloud NGFW Enterprise identifies a threat, it creates an event in Cloud Logging [1], the log entry is automatically forwarded to Google SCC Enterprise [2] which will natively ingest the threat finding [3] and has a default parser [4] that will map the fields using the Unified Data Model structure.
A custom rule using the YARA-L 2.0 language [5] will be created to identify the relevant events and generate alerts [6] that will be aggregated to raise a Case [7]. A playbook [8] can be attached to the case to be run automatically and optionally take an action such as adding a secure tag to a potentially compromised workload [9].
Unifying security with built-in cloud security controls
These core capabilities in NGFW Enterprise and SCC Enterprise will help you effectively detect and respond to threats in your environment:
Rules, alerts, and cases
Google Cloud's Security Command Center (SCC) Enterprise utilizes rules, alerts, and cases to streamline threat detection and response. Custom rules can be established to identify specific security events or anomalies within ingested logs. When a rule is triggered, an alert is generated, notifying security teams of potential issues. Related alerts will then be aggregated into actionable cases, providing a centralized view of security incidents. This process enables efficient investigation and response, allowing security teams to prioritize and address threats effectively.
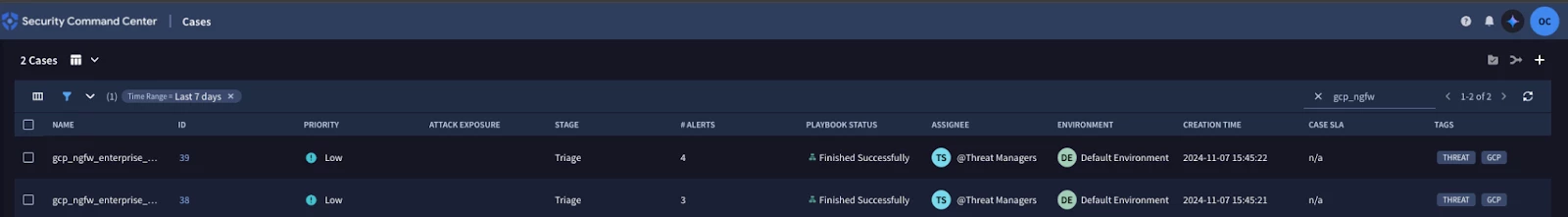 Figure: Security Command Center Cases
Figure: Security Command Center Cases
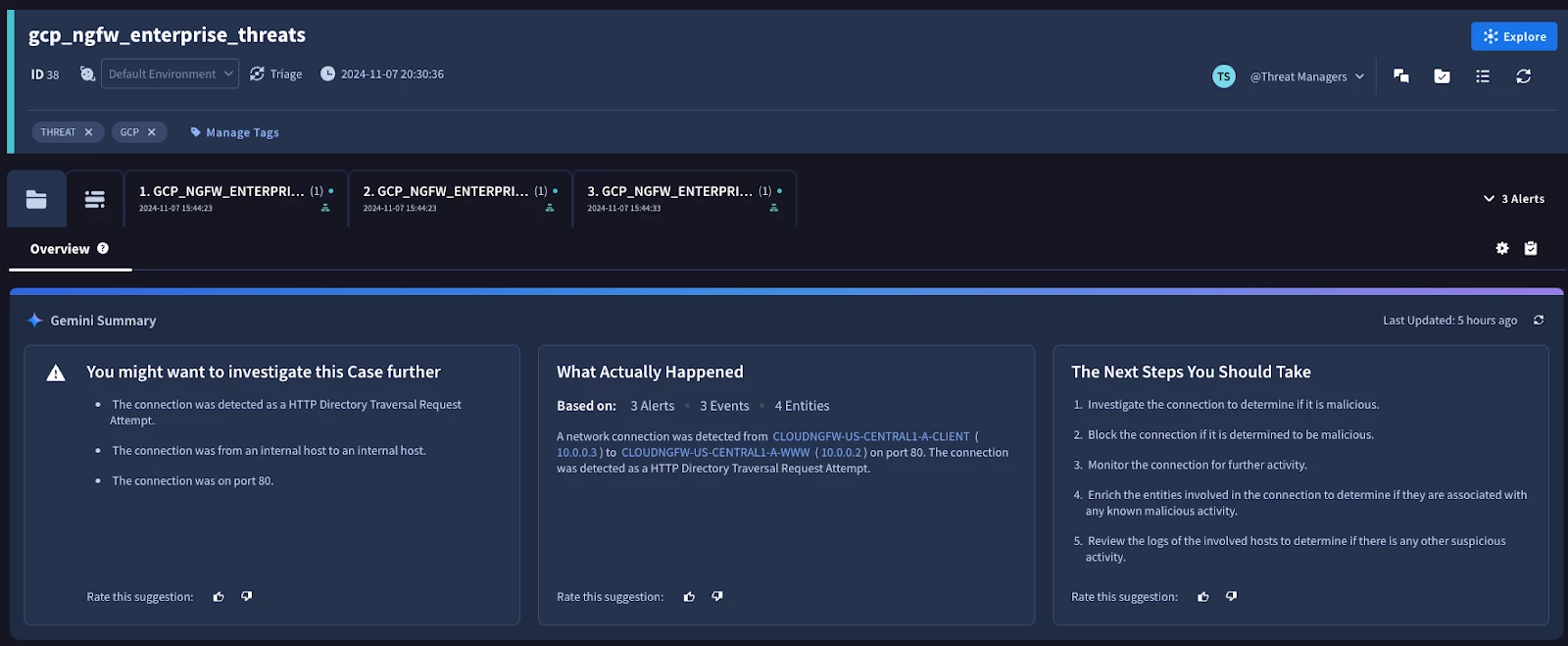 Figure: Security Command Center Case Overview
Figure: Security Command Center Case Overview
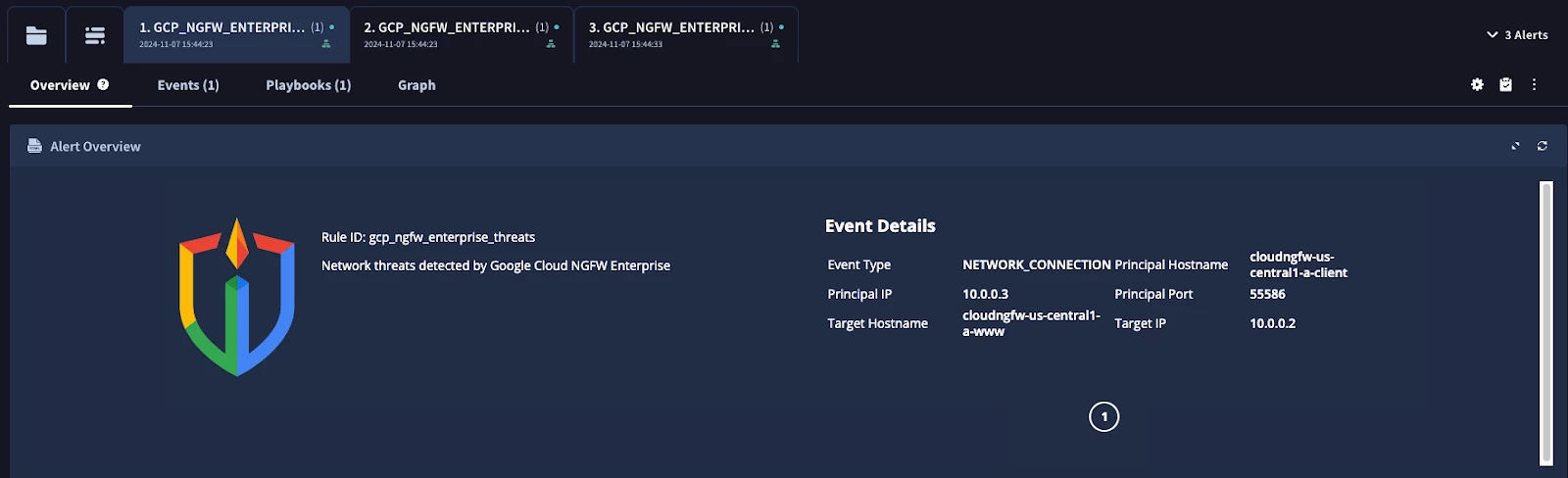 Figure: Security Command Center Alert Overview
Figure: Security Command Center Alert Overview
Search
Security Command Center Enterprise offers robust SIEM capabilities, including search and graph functionalities that enable users to quickly and effectively analyze security data. The search feature allows for filtering and querying of ingested logs, while the graph functionality provides a visual representation of relationships between entities, aiding in the identification of potential security incidents and attack patterns. This combination of capabilities helps security teams efficiently detect, investigate, and respond to threats.
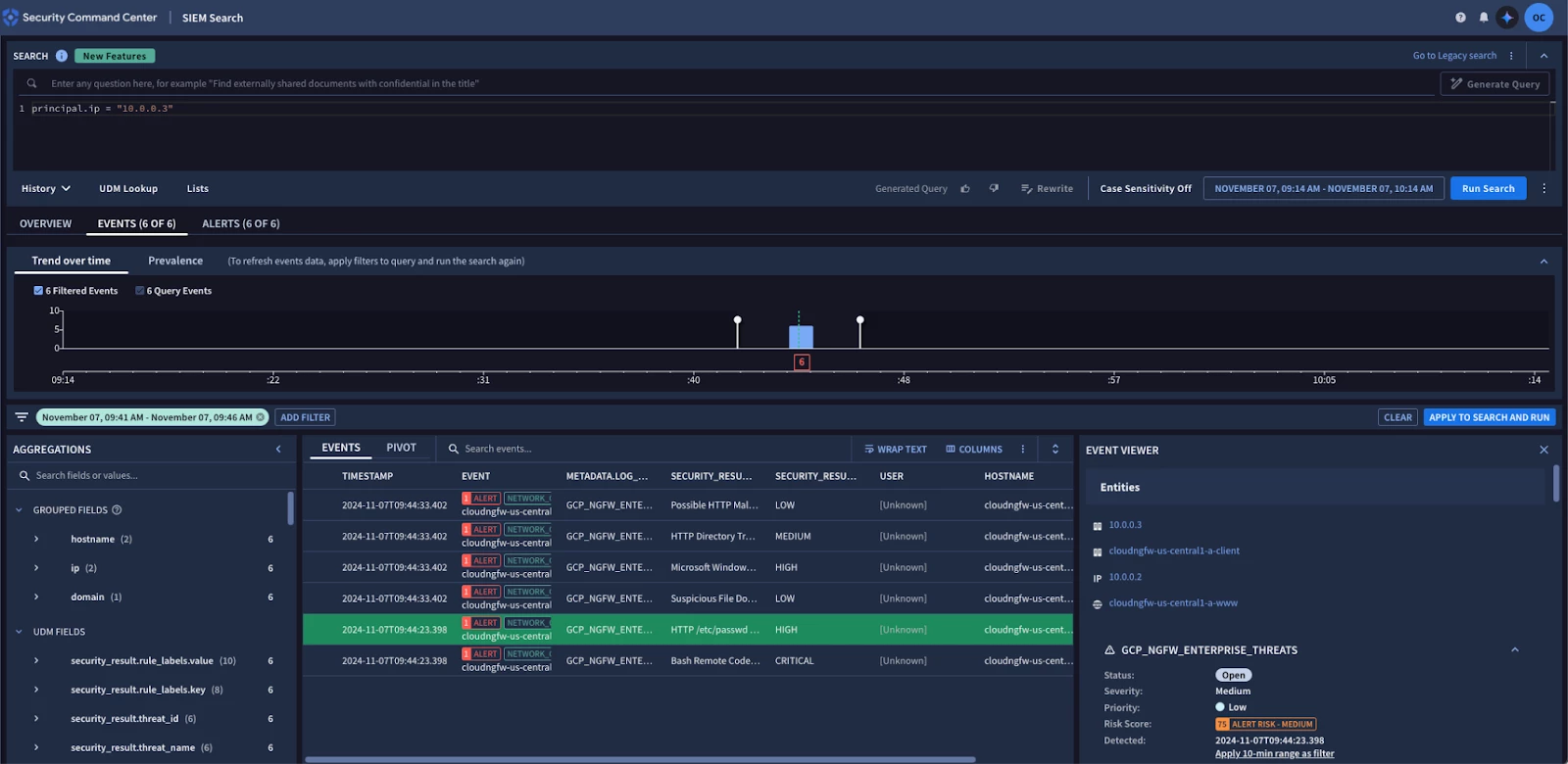 Figure: Security Command Center Events
Figure: Security Command Center Events
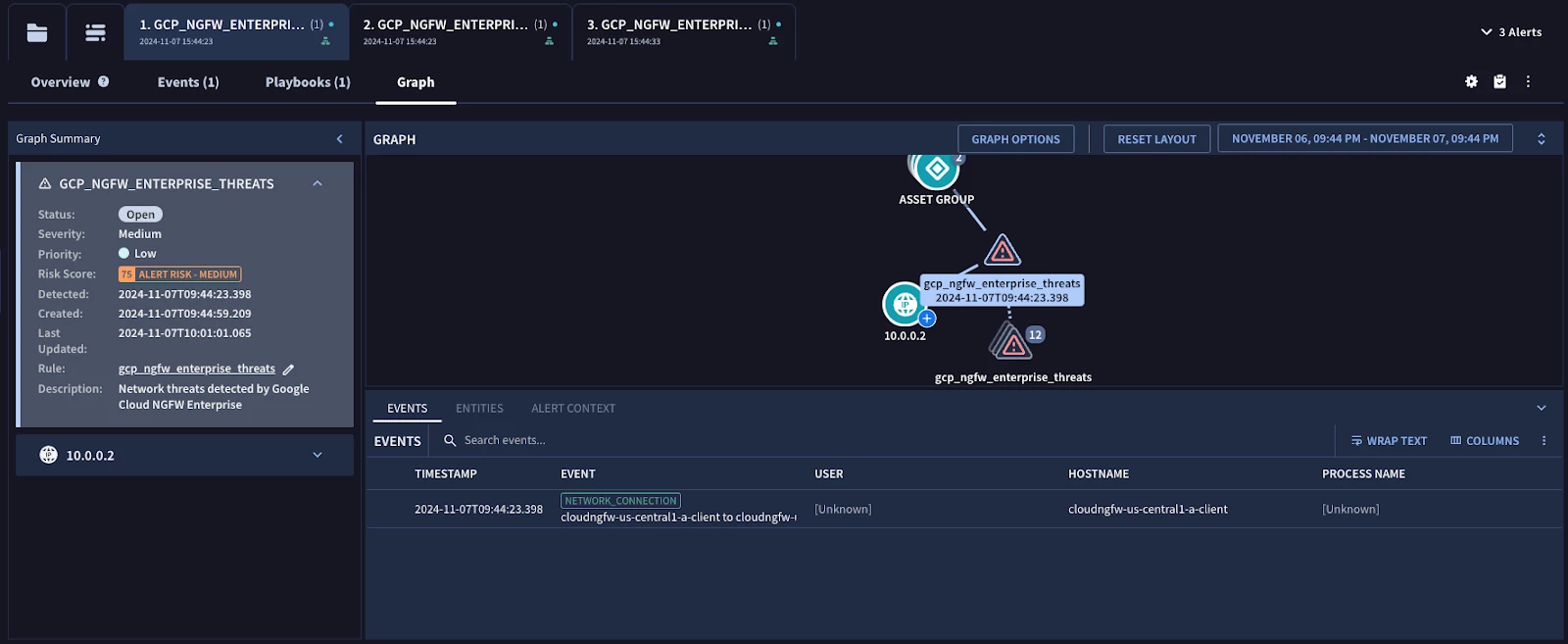 Figure: Security Command Center Case Event Graph
Figure: Security Command Center Case Event Graph
Playbooks
Playbooks provide a framework for automated responses to security incidents, allowing for predefined actions to be triggered when specific conditions are met. The integration with the Google Cloud API further extends these capabilities, enabling playbooks to interact with various Google Cloud services programmatically. This combination empowers security teams to automate routine tasks, accelerate incident response, and improve overall operational efficiency.
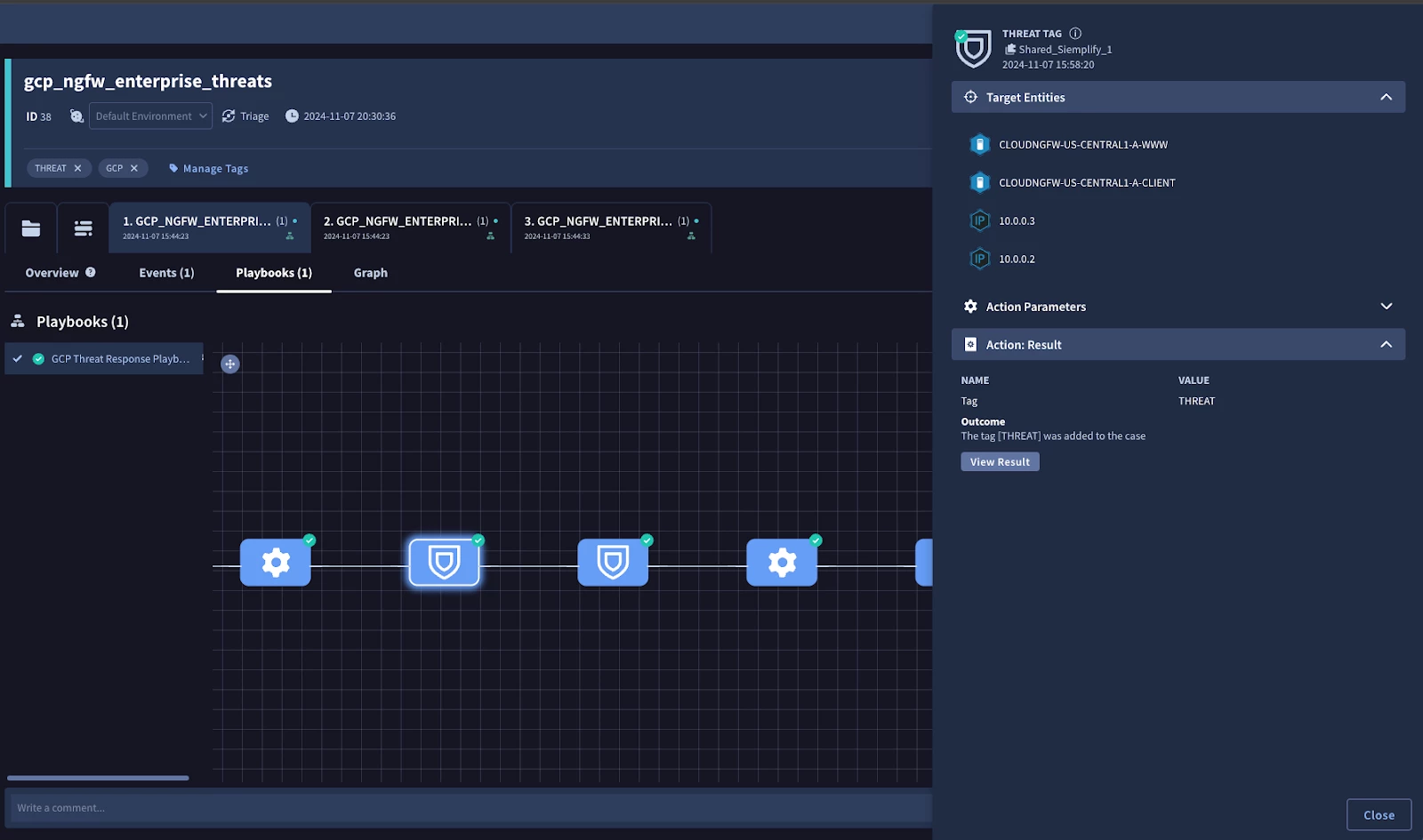 Figure: Security Command Center Case Alert Playbook
Figure: Security Command Center Case Alert Playbook
For instance, a playbook could be created and customized to use the Google Cloud API integration to automatically add a tag to a compromised instance and isolate it or block malicious IP addresses.
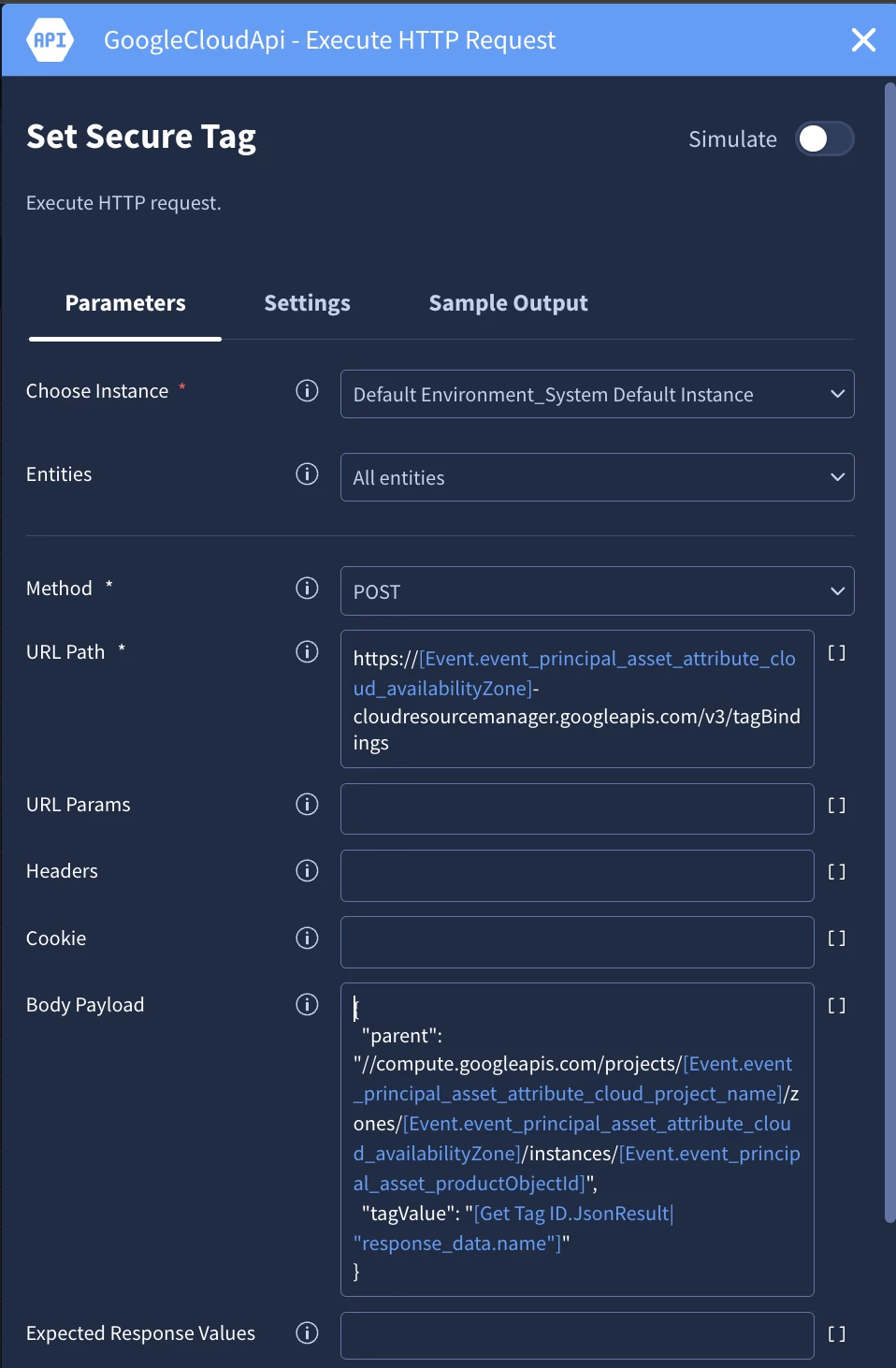 Figure: Security Command Center Google API Action
Figure: Security Command Center Google API Action
Note that when you change the enforcement state of a firewall rule, or when you create a new rule that is enforced, the change applies to new connections only. Existing connections are not affected by the change.
Dashboards
Custom dashboards allow security teams to tailor their view of security data by selecting specific metrics, logs, and charts relevant to their needs, and provide a centralized and personalized overview of security insights, enabling efficient monitoring, analysis, and reporting.
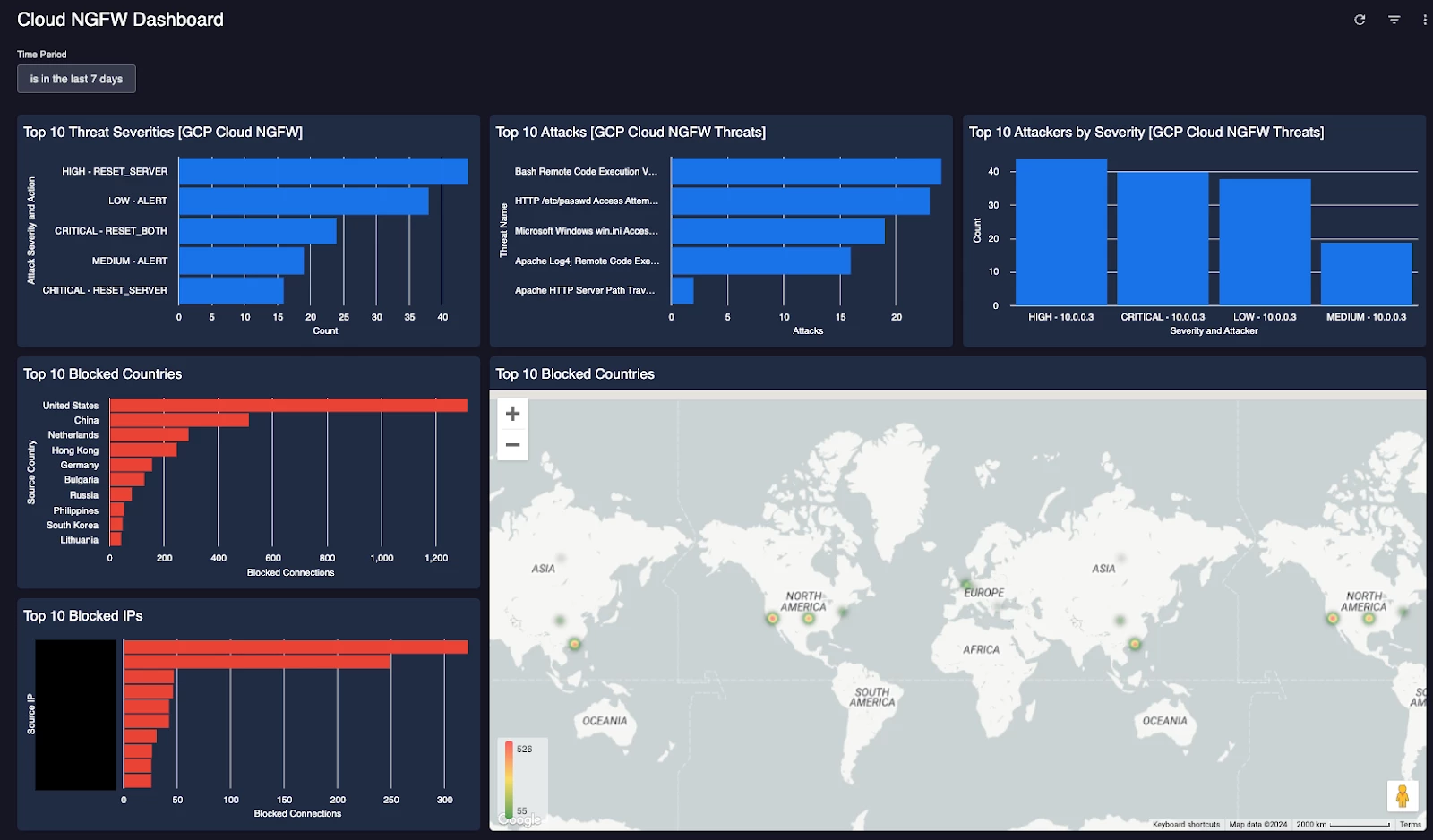 Figure: Security Command Center Custom Dashboard
Figure: Security Command Center Custom Dashboard
Conclusion
Integrating Cloud NGFW Enterprise with SCC Enterprise helps bolster your cloud security. This powerful combination offers advanced threat detection, streamlined response and enhanced visibility, enabling you to proactively protect your critical cloud assets, and get:
- Streamlined threat detection and response: The integration enables rapid identification and response to threats, minimizing potential damage.
- Enhanced visibility: SCC Enterprise provides a centralized view of security events, improving your ability to monitor and analyze your security posture.
- Automation: Playbooks enable automated responses, reducing manual effort and improving response times.
- Customization: Custom rules and dashboards allow you to tailor the integration to your specific security needs.
By leveraging these Google Cloud security solutions you can build a more resilient and secure cloud environment. And our recommendation is to regularly review and update your firewall rules and logs, detection rules, playbooks, and dashboards to adapt to evolving threats and maintain a robust security posture.
The step-by-step Cloud NGFW and Security Command Center Enterprise Integration Guide can be accessed through this link.


