On January 14, 2025, we had the pleasure of hosting a Strategic Threat Intelligence for Financial Institutions webinar, sharing insights obtained from Google Threat Intelligence. This blog post serves to answer possible questions that Google Threat Intelligence users may have had during the webinar. Please use the comment box below if you have any questions.
Campaigns impacting the financial sector
In early-to-mid November, Palo Alto Networks disclosed two vulnerabilities in PAN-OS, affecting numerous firewall products. Actors have used CVE-2024-0012 to gain administrator privileges on vulnerable appliances followed by CVE-2024-9474 to achieve privilege escalation and execute arbitrary code with root privileges. Both vulnerabilities were exploited as zero-days. This global event was carried out by suspicious China-nexus threat actors, where multiple sectors were affected, including the financial sector.
Mandiant discovered a global event where threat actors were using SNOWLIGHT downloader written in C and the affected regions of the campaign were South America, Southern Asia, Southern Europe, Eastern Asia, South-eastern Asia and Northern America.
The following figure displays the suspected origins of threat actors’ observed activity as well as locations of targeted victims in the Financial Services sector over the past two years. This is not limited to suspected state sponsored actors, but includes suspected locations of activity sets with various assessed motivations, for example, financially motivated groups. In some cases, countries may be both a Target and a Source of threat activity, as reflected in the legend.
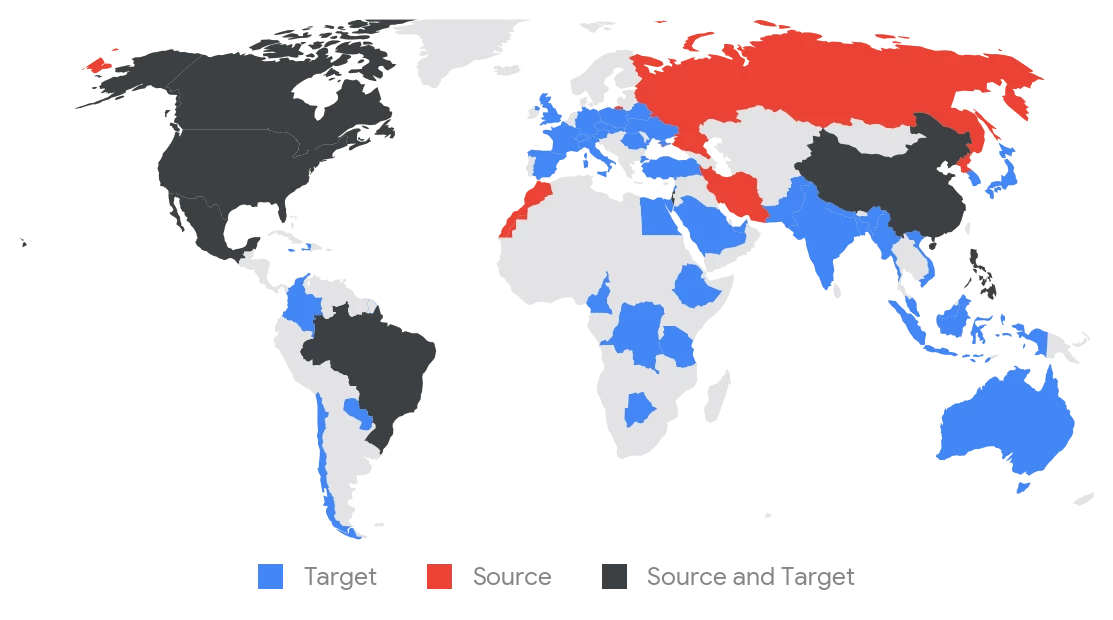 Figure 1: Target and source geography
Figure 1: Target and source geography
Malware Impacting the Financial Sector
The following figure highlights the most prevalent malware families identified in tracked campaigns impacting the financial sector during 2024. Most of these tools are backdoors, demonstrating the objective to establish and maintain remote connections to compromised systems.
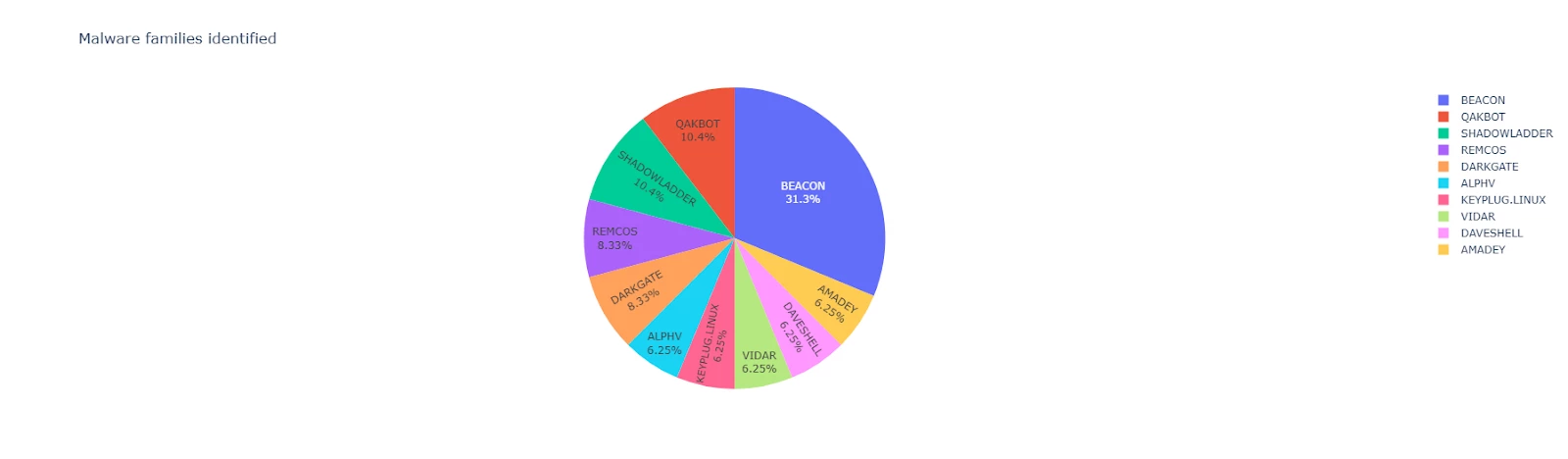
Figure 2: Malware families observed in campaigns tracked by Google Threat Intelligence
Threat Actors targeting the financial sector
Ransomware significantly impacts various sectors. Google Threat Intelligence analysts provide a monthly overview of ransomware and data theft extortion groups targeting the financial sector, identifying the most active groups. Data from public data leak sites reveals the extortion brands that impacted the financial sector in December 2024.
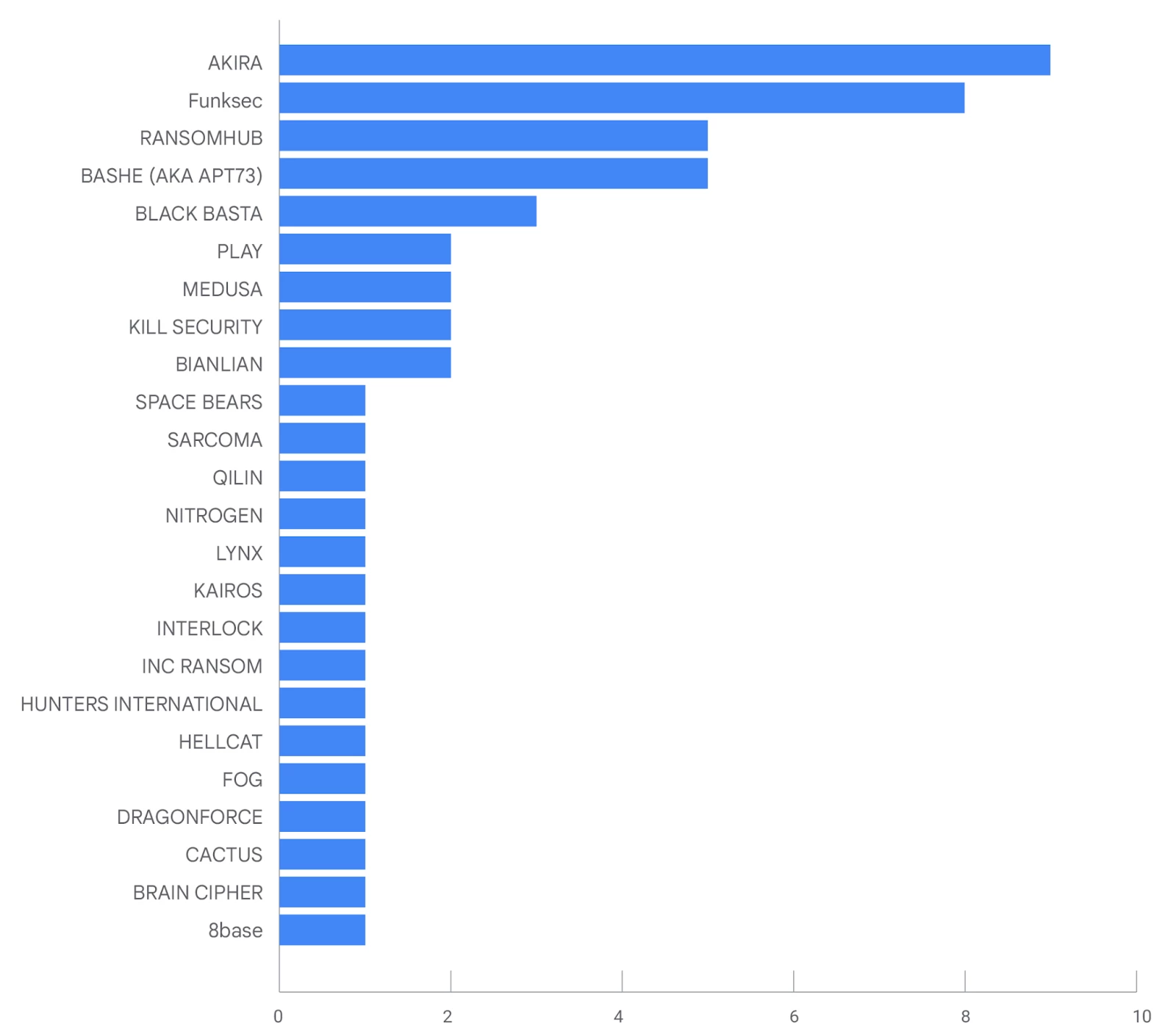 Figure 3: Financial sector extortion incident announcements on data leak sites in December 2024
Figure 3: Financial sector extortion incident announcements on data leak sites in December 2024
Mandiant constantly tracks many intrusion sets to understand the motivations and capabilities of cybercrime and nation-state groups frequently observed targeting the Financial Services sector. Our platform provides information on these actors, including identified campaigns, malware used, and affected sectors, which is valuable for financial companies. The following figure shows the most frequently observed threat actors impacting financial institutions over the past two years.
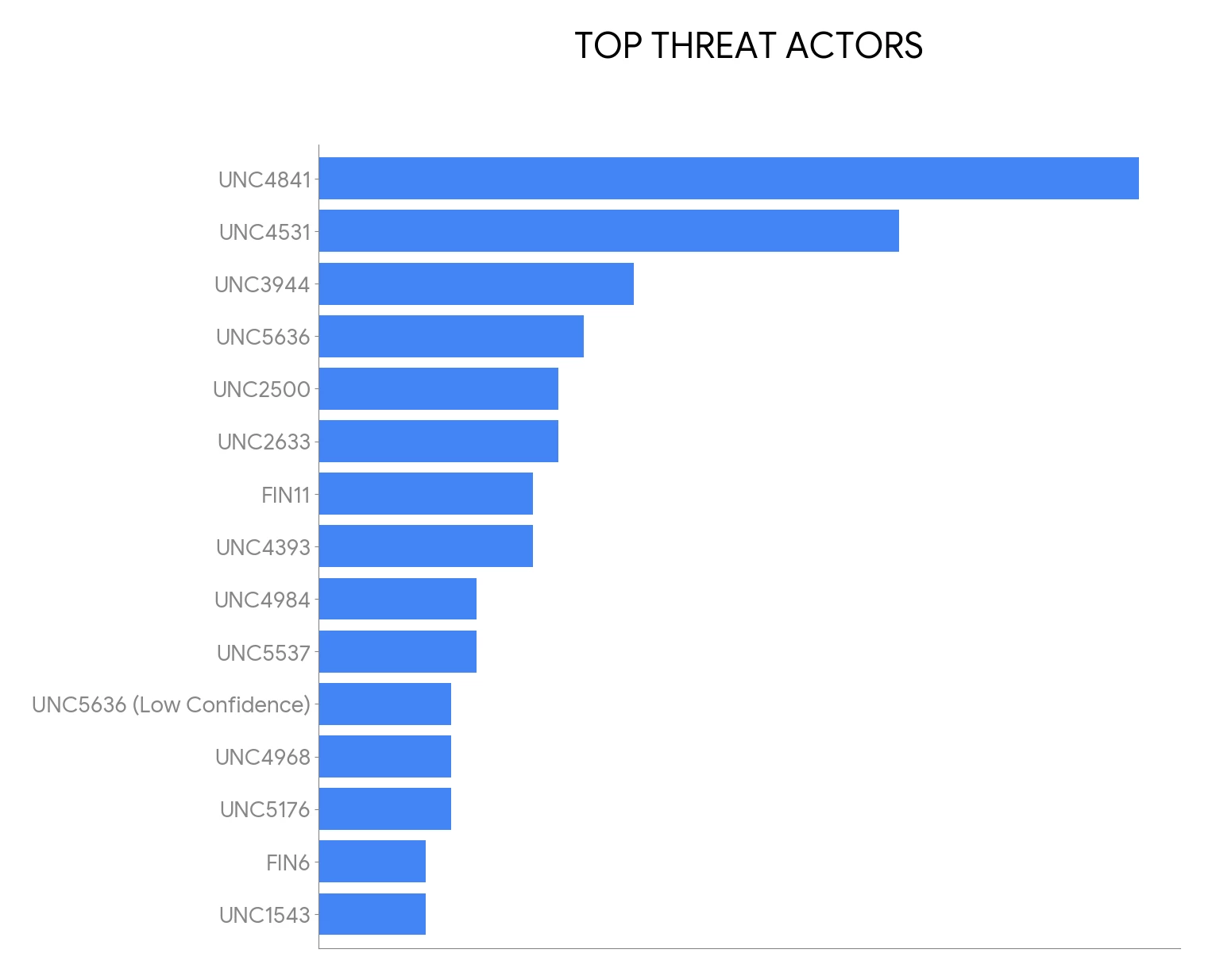 Figure 4: Threat actors most frequently observed impacting financial institutions
Figure 4: Threat actors most frequently observed impacting financial institutions
CVEs exploited in intrusions impacting the financial sector
Analyzing the vulnerabilities exploited against financial services, some of them started with the exploitation of specific vulnerabilities as a primary tactic for gaining unauthorized access to systems. Among the myriad of potential weaknesses, a particular favorite for threat actors has been targeting network edge devices and virtualization software to evade detection. These products have been repeatedly targeted and exploited in various campaigns, serving as initial access points for a range of malicious activities.
The widespread exploitation of vulnerabilities underscores the critical importance of robust patch management and vulnerability remediation practices. Financial institutions must remain vigilant in identifying and addressing potential weaknesses in their systems, particularly those associated with commonly exploited products. Additionally, the adoption of advanced threat detection and response solutions can help organizations identify and mitigate attacks that leverage these vulnerabilities, thereby safeguarding sensitive financial data and ensuring the continuity of critical operations.
Conclusions
The financial sector faces a persistent and multifaceted threat environment. Ransomware and financial cybercrime groups remain the most prevalent threat actors, but the landscape is evolving. Attackers are increasingly using complex techniques, such as supply chain compromises or leveraging AI-powered malware, to breach systems and evade detection. Traditional security measures are proving insufficient against increasingly sophisticated campaigns, particularly those with ties to China.
The speed at which vulnerabilities are exploited is increasing. The exploitation of the Palo Alto Networks vulnerabilities CVE-2024-0012 and CVE-2024-9474 as zero-days highlights the critical need for proactive security measures like threat hunting, vulnerability scanning, and intrusion detection systems to mitigate risks even before patches are available.
If you want to know more about Google Threat Intelligence, you can visit our website!
We hope you found this blog interesting and useful, and as always we are happy to hear your feedback on the Comment section below.
