In today's complex threat landscape, having the right tools is essential. What if you could 'Google' for malware? With Google Threat Intelligence, you practically can!
Google Threat Intelligence is a comprehensive security solution that leverages Google's vast resources and expertise to help organisations detect, investigate, and respond to cyber threats. It combines the deep frontline knowledge of Mandiant, the global reach of the VirusTotal community, and the extensive visibility of Google's billions of signals across devices and emails.
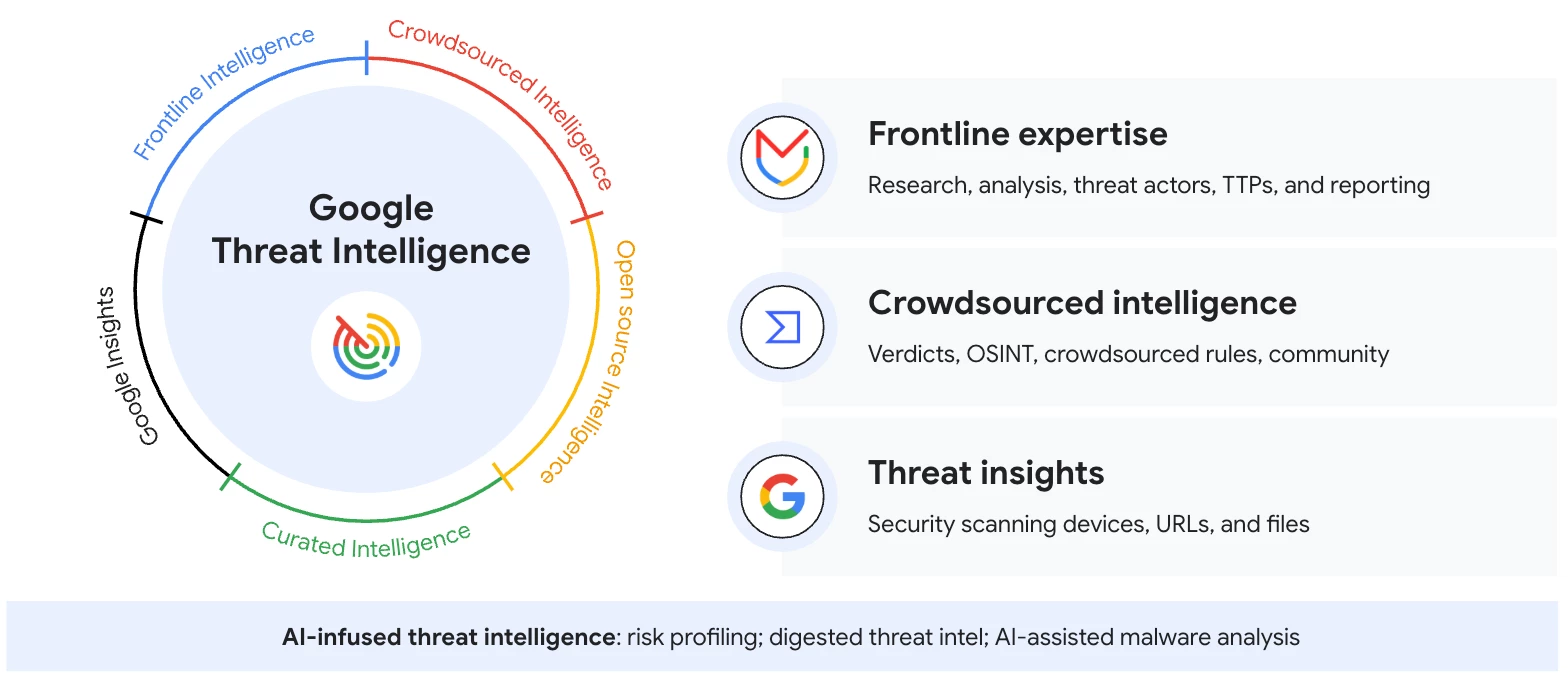
The Google Threat Intelligence Dataset:
The Google Threat Intelligence dataset, comprising over 50 billion files, 6 billion URLs, and 5 billion domains, serves as the foundational data repository for the Google Threat Intelligence platform.
The data itself revolves around 3 key concepts - objects, entities, relationships.
Objects are a key concept in Google Threat Intelligence. Each object has an identifier and a type. Identifiers are unique among objects of the same type, which means that a (type, identifier) pair uniquely identifies any object.
Entities are the plural form of the object type - for example, URL is the entity type containing all the objects of the type URL.
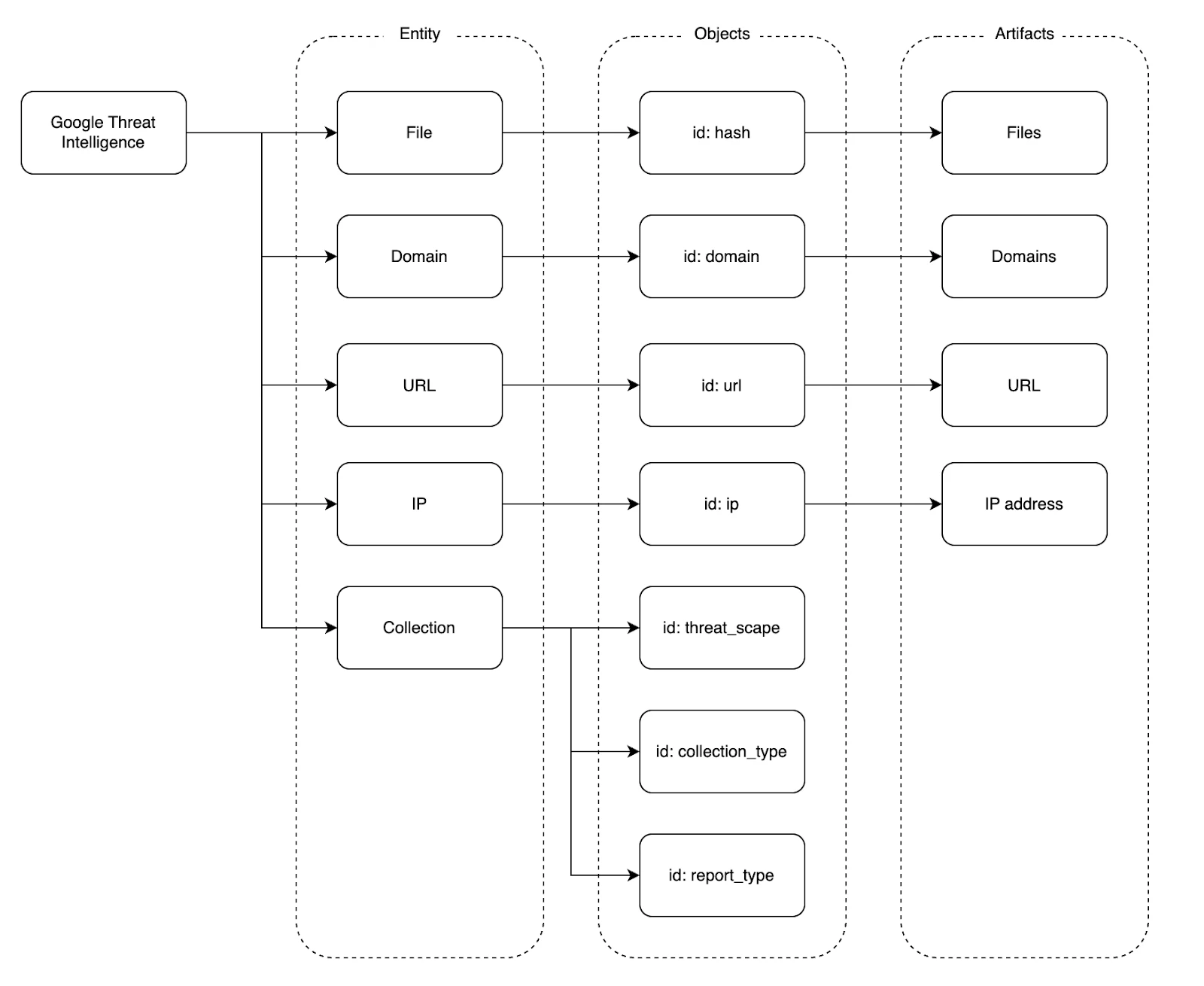
Each object may optionally have one or more relationships.
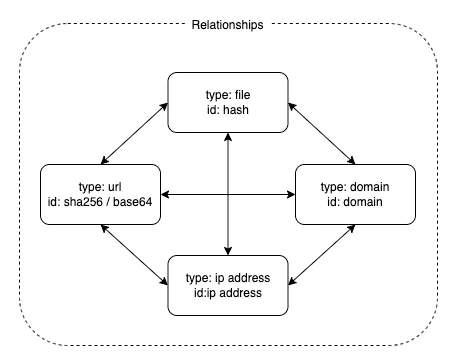
To sum it up, think of objects as individual files, URLs, Domains, or IP addresses. Entities are like folders containing those objects, and relationships show how these objects are connected.
With Google Threat Intelligence, you can search through its vast dataset to identify files (or any other IOCs) based on various criteria, such as their hash, antivirus detections, metadata, and even their file size. It's like having a specialized 'Google' search engine, but specifically for malware and cyber threats.
A simple search on Google Threat Intelligence will allow you to get relevant insights on the indicator you’ve put into the search bar. The example below shows a WannaCry ransomware sample.
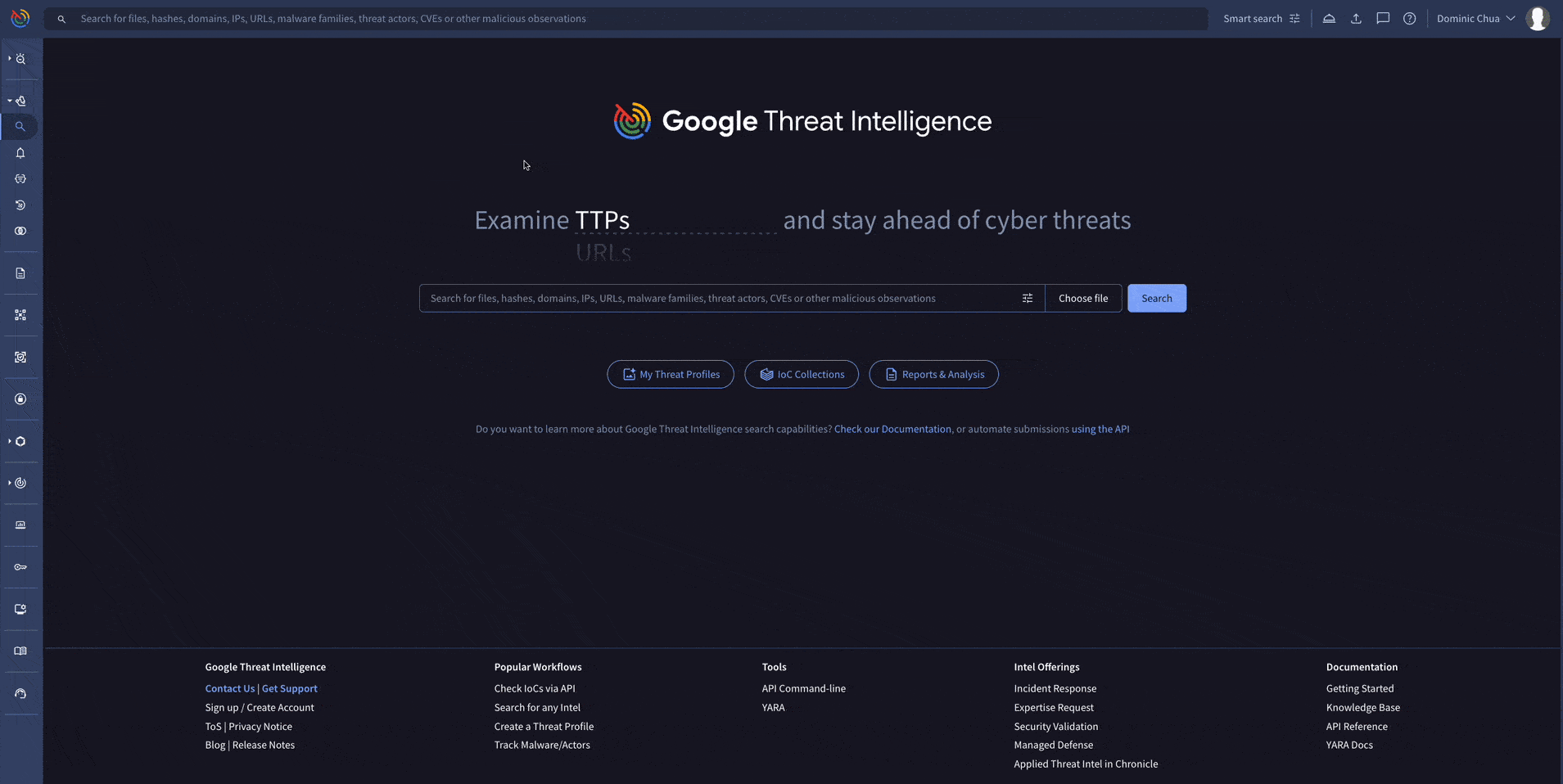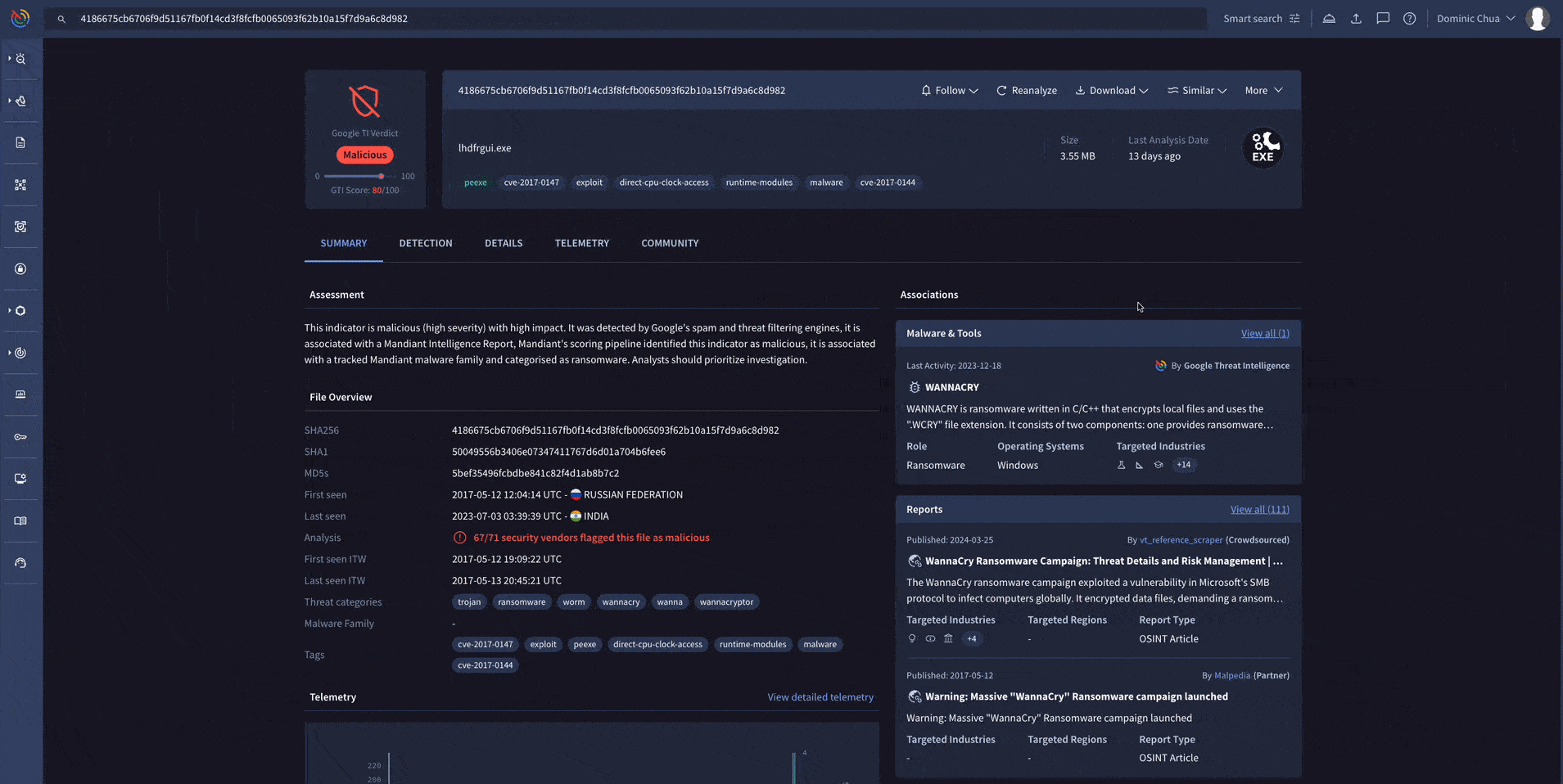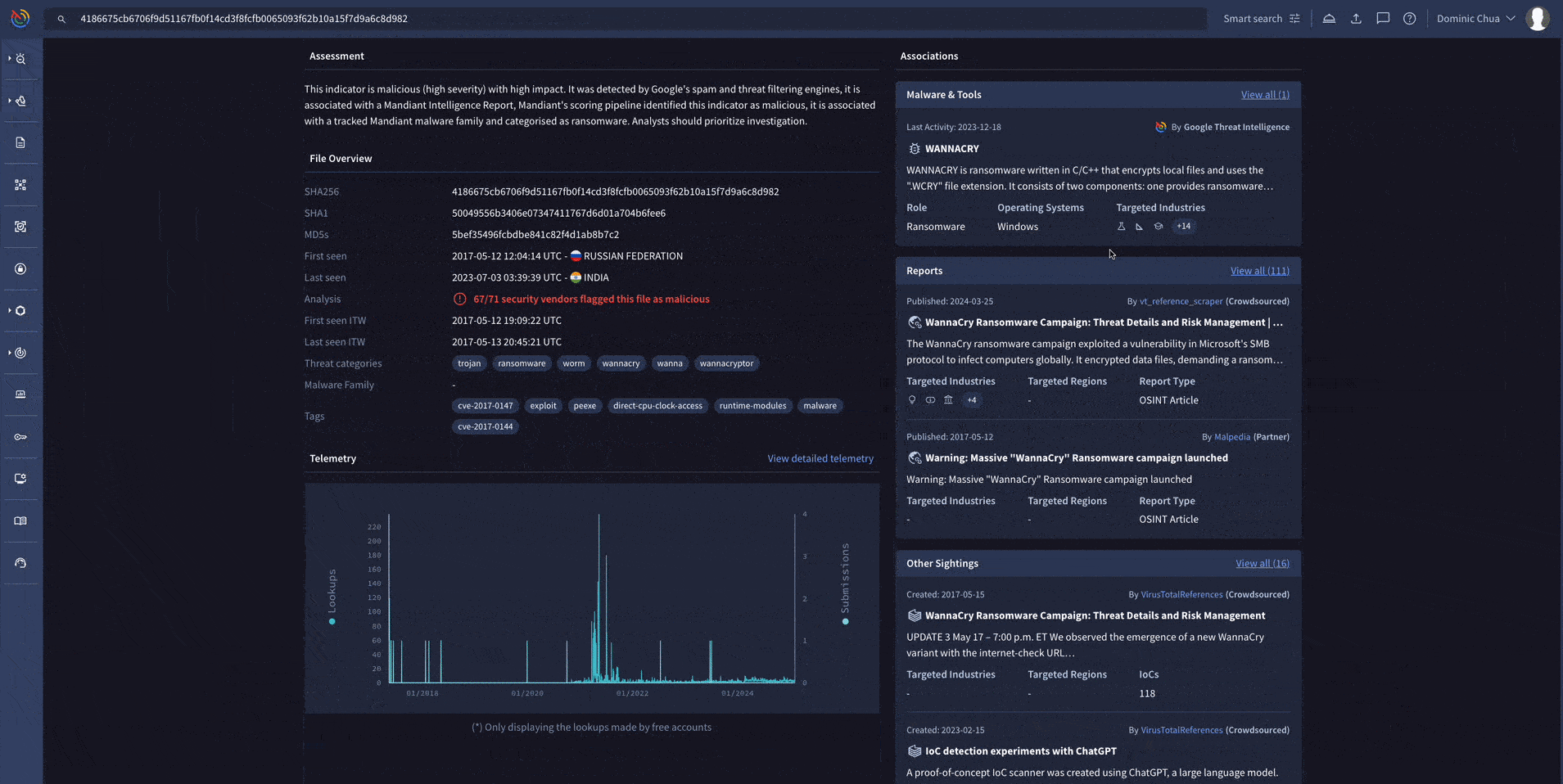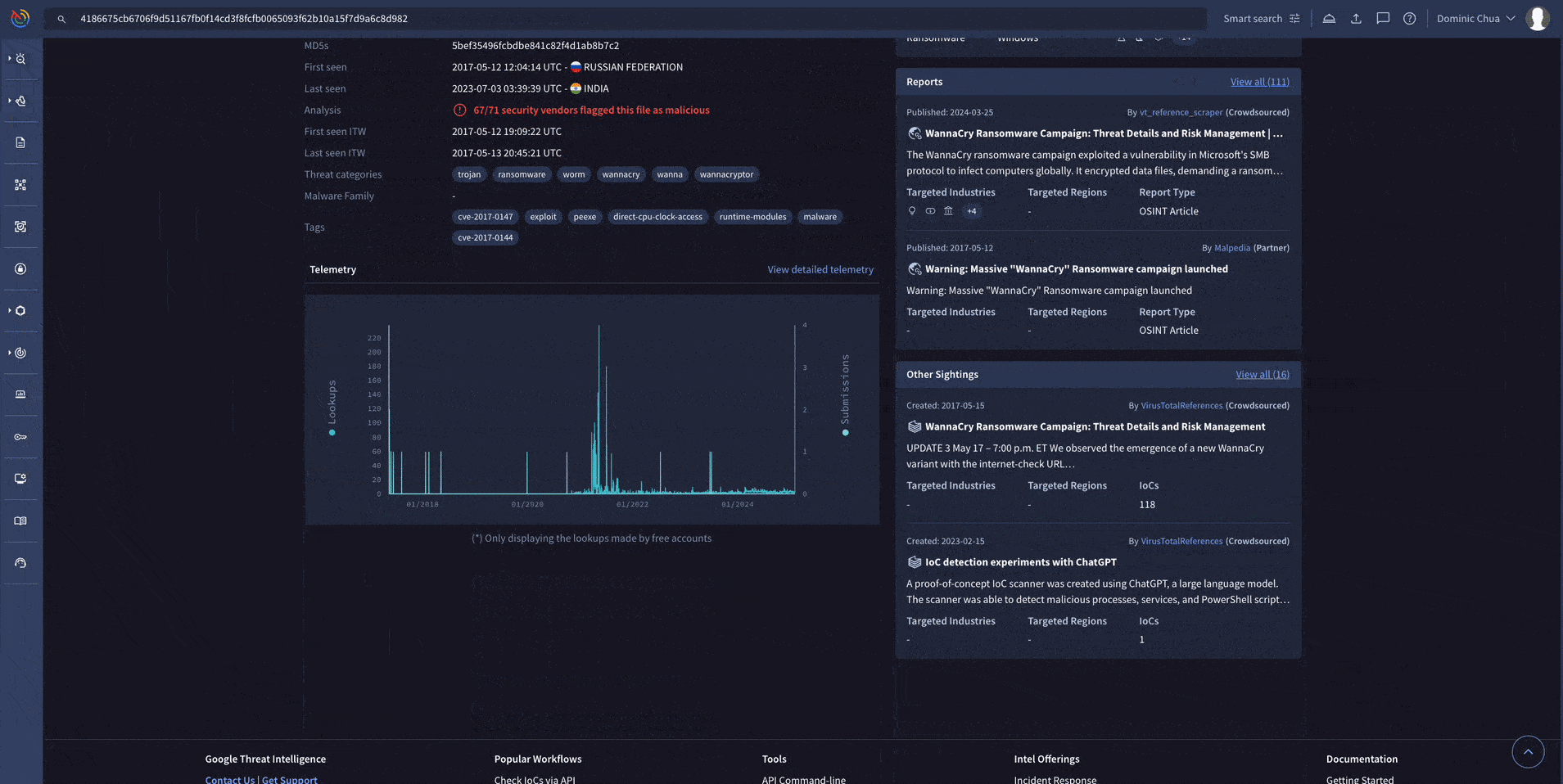
This is great when you need to quickly understand if an indicator you’ve encountered is malicious or not, and to retrieve relevant information to help with your investigation.
However, what happens when you don’t have the hash itself, or are trying to threat hunt based on a hypothesis?
This is where the concept of dorking comes in.
What is Dorking?
Dorking is a specific technique that leverages advanced search operators to find information on the internet that may not be immediately accessible through standard search queries.
While it shares a similar philosophy with traditional dorking, Google Threat Intelligence dorking utilizes a unique set of search modifiers specially designed to uncover specific indicators of compromise. This allows security professionals, malware analysts, and threat hunters to search for specific malware samples, identify emerging threats, and conduct in-depth investigations.
All search terms come in a <modifier:value> structure. Almost all metadata found within the indicator report can be used as a search modifier.
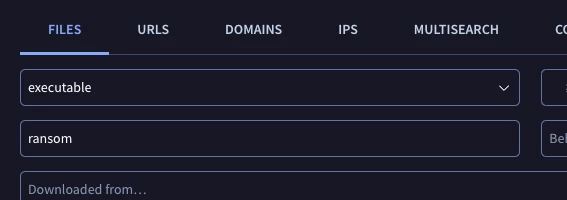
The first way to leverage advanced searches is via the “Smart Search” dropdown, where you have the option to select the file type, the when it was last seen, and if the file has been signed.
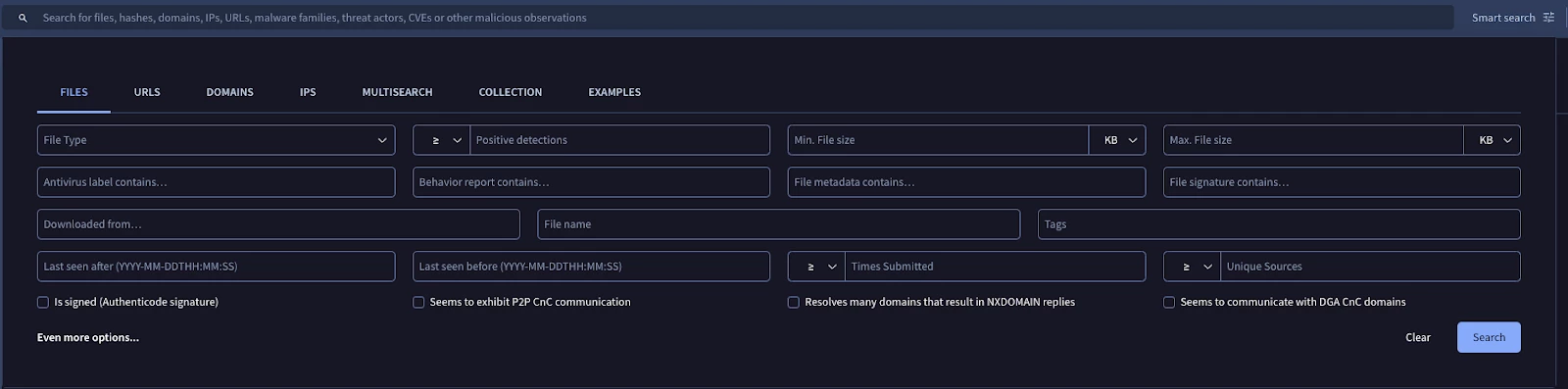
One use case is to search for new samples that have been detected as ransomware by the 3rd party antivirus vendors.
Example Google Threat Intelligence Queries:
- Searching for files with at least 10 detections
entity:file and p:10+ - Searching for files with at least 10 detections that have been detected as a malware (in this case, ransomware)
entity:file p:10+ engines:ransom - Searching for files with any filenames starting with the string “mimi”
name:mimi* - Show all lummac samples in the past 7 days
engines:lummac ls:7d+ - Find files hosted on a .gov site with a GTI scoring of at least 60
itw:”*.gov” gti_score:60+ - Searching for any URLs that have been categorised as phishing
entity:url (engines:phishing or category:phishing) - Search for typo-squatting domains that masquerade as Google
entity:domain fuzzy_domain:google.com NOT parent_domain:google.com - Search for all indicators that have been associated with APT43
entity:url threat_actor:apt43
Google Threat Intelligence Modifiers
Google Threat Intelligence has specific modifiers for each type of collection. Here are some of the most frequently used:
| Search Modifier | Description | Examples |
| fs | Filters results to be returned according to the first submission date/time | fs:2024-08-01T19:15:00+, fs:2024-12-25+, fs:30d- |
| ls | Filters results to be returned according to the last submission date/time | ls:2024-08-01T19:15:00+, ls:2024-12-25+, ls:30d- |
| positives / p | Filters the files to be returned according to the number of antivirus vendors that detected it upon scanning with Google Threat Intelligence | p:10+, p:30- |
| gti_score | Google Threat Intelligence assessment threat score | gti_score:60+ |
| tag | Behaviour of files are treated as tags. Returns results matching the exact string provided | tag:signed, tag:exploit, tag:macros |
| content | Searches for string or binary content within a file | content:”hello world!”, content:{53 ff767c ff7678 ff7644} |
| have | Filter the resources which report contains information from specific fields | have:behaviour, have:email_attachment, have:dropped_files |
| comment | Searches for strings in the comments section | comment:”fancy bear” |
You can combine multiple modifiers into more complex search queries using the logical operators AND, OR, and NOT. Parentheses can be used to group modifiers and logical operators, allowing for more precise queries by controlling the order of operations. All modifiers within a search query must be mapped to a single top-level entity.
Tips for Effective Searches:
- Start with broad searches and gradually refine your queries with more specific modifiers
- Combine multiple modifiers to narrow down your results
- Utilize the broad Google Threat Intelligence advanced search modifiers for more complex queries
This is just a glimpse into the power of Google Threat Intelligence searches. Start experimenting with these techniques today and see how they can enhance your threat hunting capabilities
For future articles, we will dive deeper into advanced search operators, explore practical use cases, and discuss how to leverage the different search modifiers for proactive threat hunting.
