In our previous blog post, we discussed how to integrate Chrome Enterprise with Google Chronicle to enhance your security visibility. In this blog, we will leverage the configuration we applied last time to provide some examples of how Chrome event data can be used to create rules and investigate security incidents.
Helping Users Who Can't Help Themselves
Have you ever seen this red warning page pop up when you try to visit a website? That's Google Safe Browsing. It helps protect over five billion devices every day by warning users when they attempt to navigate to dangerous sites or download dangerous files.
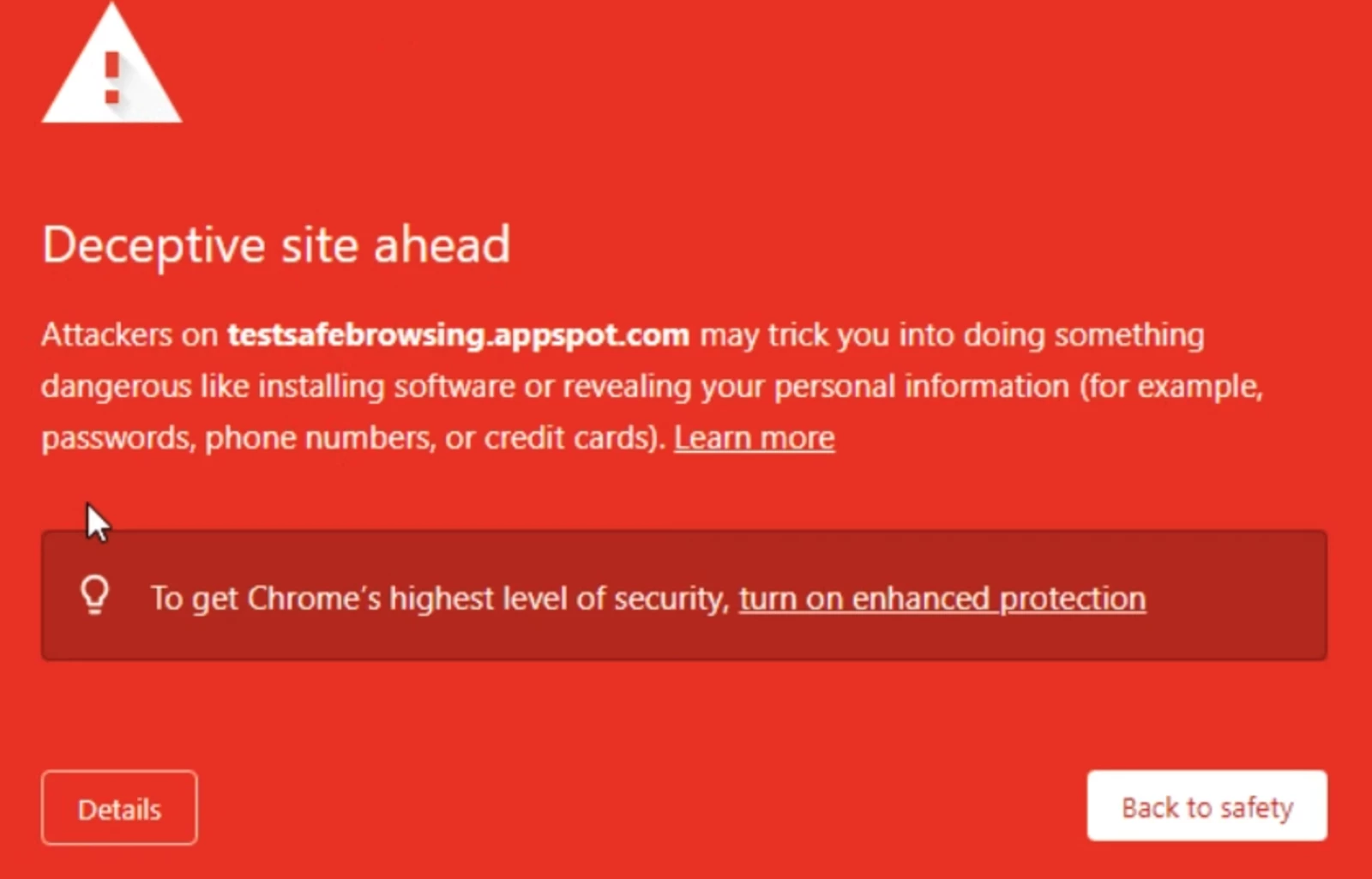
While it doesn't actually stop people from visiting these sites, organizations that use Chrome Enterprise Management can enforce Safe Browsing for their users and organizational units (OUs). This is a great way to protect employees from malware, phishing, unwanted software, and other assorted badness. I highly recommend checking it out!
One common use case for Chrome event data is to identify users who are bypassing Safe Browsing warnings. Let's say an employee who doesn't have Safe Browsing enforcement sees the warning about social engineering but they still go to the site anyway. If a user bypasses a Safe Browsing warning, it is important to investigate the incident to determine why the user bypassed the warning and whether the user is aware of the risks. Chrome event data can be used to investigate these incidents.
The data includes :
- The time the event happened
- The type of event
- Information about the browser (e.g., version, platform)
- Information about the operating system (e.g., version, architecture)
- Whether the device is managed or not
- Details about the action, such as whether the warning was bypassed
- The malicious site address
- The category of the malicious site
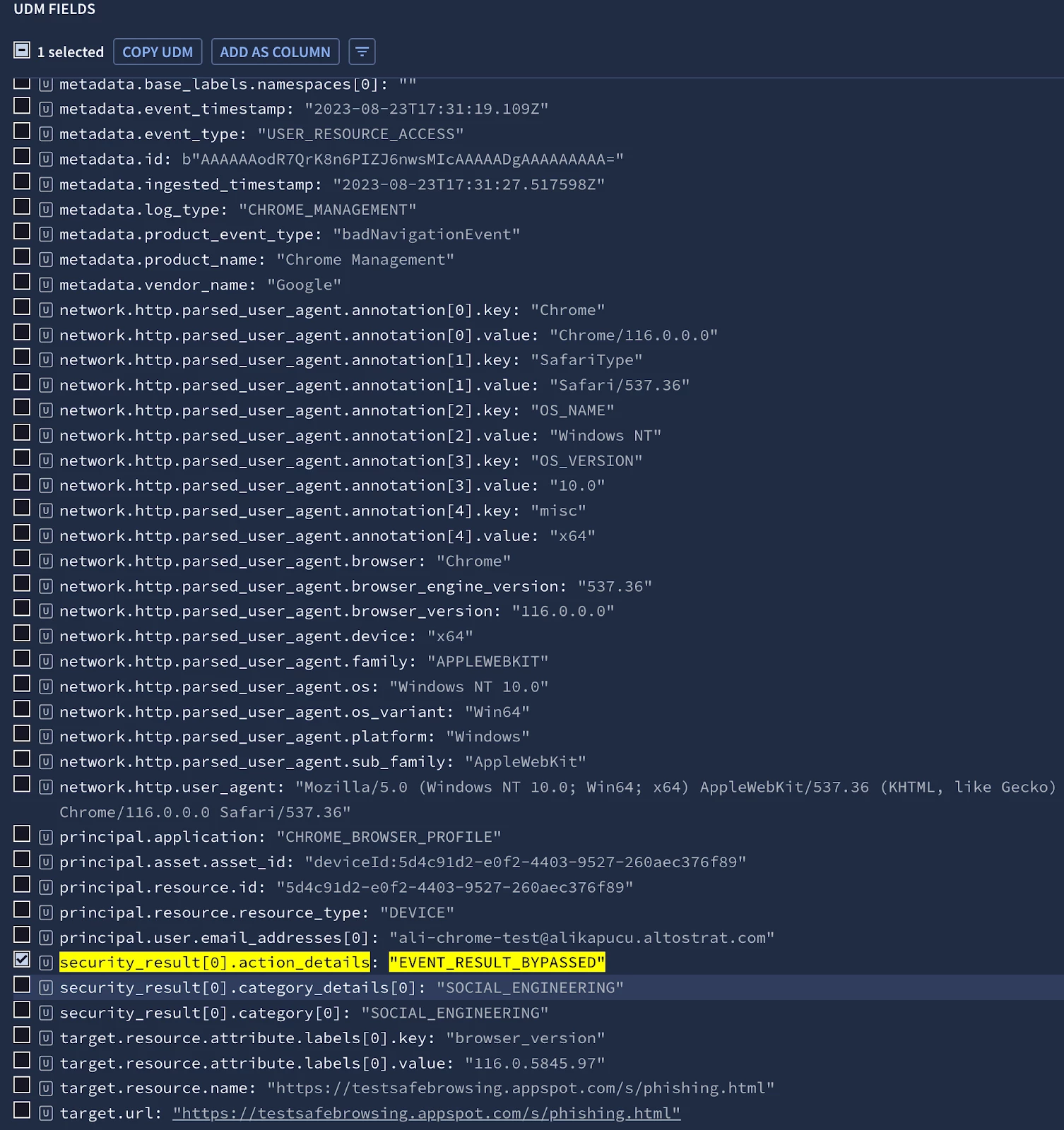
Security analysts can use the data to investigate security incidents and identify potential threats to the organization. To gather more sample data, you can use the Google Safe Browsing testbed (https://testsafebrowsing.appspot.com/) to trigger events and analyze them in your Chronicle instance. You can also refer to the Google Chronicle parser documentation Parser syntax reference | Chronicle Security to understand all the events provided by Chrome Enterprise Management and how they are aligned with the UDM events.
Chronicle's integration with Chrome enterprise telemetry provides granular visibility for specific use cases. Even if you don't have this setup, you should still leverage Safe Browsing data in your environment, why wouldn't you? Chronicle automatically ingests Safe Browsing data and gives you a way to enrich your UDM events and rules. For more information, check out my colleague John Stoner's New to Chronicle: Safe Browsing Integration blog post.
Now that we have investigated and identified the UDM fields that are important to us, a rule can be created to handle Safe Browsing alerts.
A copy of the rule can be found here in our chronicle/detection-rules repo.
rule chrome_browser_safe_browsing_user_bypass {
meta:
author = "Google Cloud Security"
description = "Detects and alerts on users bypassing Chrome Safe Browsing warnings and accessing potentially dangerous content or downloads"
mitre_attack_tactic = "Initial Access"
mitre_attack_technique = "Phishing: Spearphishing Link"
mitre_attack_url = "https://attack.mitre.org/techniques/T1566/002/"
mitre_attack_version = "v14.1"
type = "alert"
tags = "chrome enterprise"
data_source = "Chrome Management"
severity = "Low"
priority = "Low"
events:
$process.metadata.product_name = "Chrome Management"
(
$process.metadata.product_event_type = "badNavigationEvent" or
$process.metadata.product_event_type = "dangerousDownloadEvent" or
$process.metadata.product_event_type = "contentTransferEvent" or
$process.metadata.product_event_type = "unscannedFileEvent"
)
$process.security_result.action_details = "EVENT_RESULT_BYPASSED"
$process.security_result.category_details = $category
strings.coalesce($process.principal.user.email_addresses, $process.principal.hostname ) = $user
match:
$user over 5m
outcome:
$risk_score = max(
if ($category = "", 10) +
if ($category = "THREAT_TYPE_UNSPECIFIED", 20) +
if ($category = "SSL_ERROR", 30) +
if ($category = "UNWANTED_SOFTWARE", 50) +
if ($category = "DANGEROUS", 60) +
if ($category = "SOCIAL_ENGINEERING", 70) +
if ($category = "DANGEROUS_HOST", 80) +
if ($category = "MALWARE", 90)
)
$instances = count_distinct($user)
$suspicious_url = array_distinct($process.target.url)
$suspicious_file_sha256 = array_distinct($process.target.file.sha256)
$principal_user_userid = array_distinct($user)
condition:
// To reduce the number of alerts to just higher risk events, uncomment the value in the line below
$process // and $risk_score >= 50
}
The rule above identifies events where Chrome Safe Browsing has detected a threat, but the user has disregarded the warning. The rule assigns a risk score based on the type of threat. The rule is useful for identifying users who may be intentionally bypassing Safe Browsing warnings, or who may be unaware of the risks. You can see the alerts generated by this rule below.
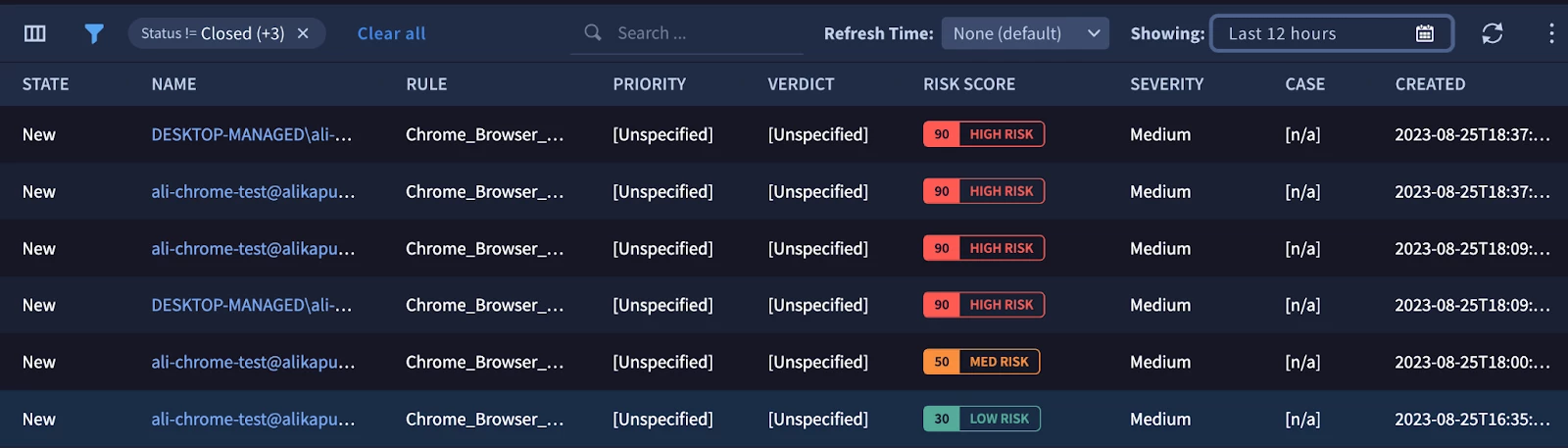
Above, we have provided an example of how Chrome event data can be used to create rules and investigate security incidents. In our next blog post, we will explore other use cases for supercharging your security visibility with Chrome Enterprise and Chronicle, and how leveraging other log sources can provide even greater visibility into your security posture. Stay tuned!
