Google Threat Intelligence is part of Google Cloud Security’s comprehensive security portfolio.
Google Threat Intelligence helps protect your organization in a variety of ways, including external threat monitoring, attack surface management, digital risk protection, indicators of compromise (IOC) analysis, and expertise.
Google Threat Intelligence boasts a diverse set of sources that provide a panoramic view of the global threat landscape and the granular details needed to make informed decisions.
The following Onboarding Journey will guide you through the basic and fundamental tasks needed for you to set up, navigate, gain familiarity, and conduct essential tasks within the Google Threat Intelligence Platform.
Your journey begins now.
Journey
How Google Threat Intelligence Approaches the Intel Cycle
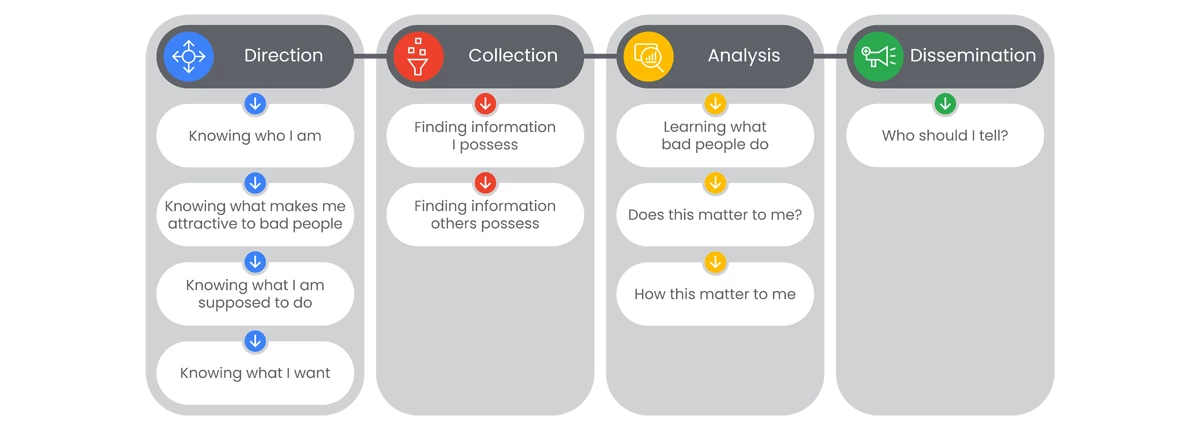
Google Threat Intelligence Journey
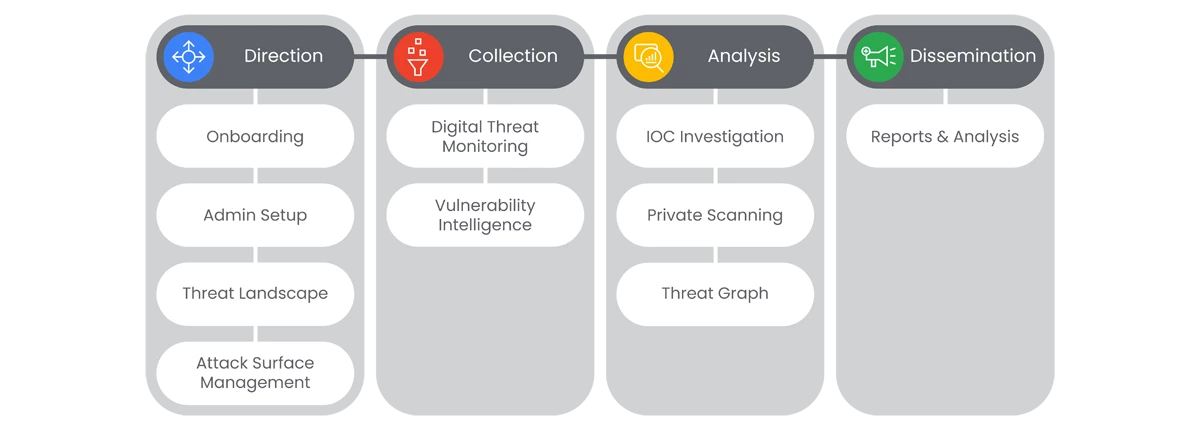 Actions
Actions
In the Google Threat Intelligence Journey, you will navigate through four main tasks of implementation:
1. Direction
1.1. Onboarding
1.2. Admin Setup
1.3. Threat Landscape
1.4. Attack Surface Management
2. Collection
2.1. Digital Threat Monitoring
2.2. Vulnerability Intelligence
3. Analysis
3.1. IOC Investigation
3.2. Private Scanning
3.3. Threat Graph
4.1. Reports & Analysis
Next Step: Google Threat Intelligence: Step 1: Direction


