

This Google Threat Intelligence search query uses a high-fidelity byte signature to instantly identify LockBit 3.0 ELF ransomware samples.
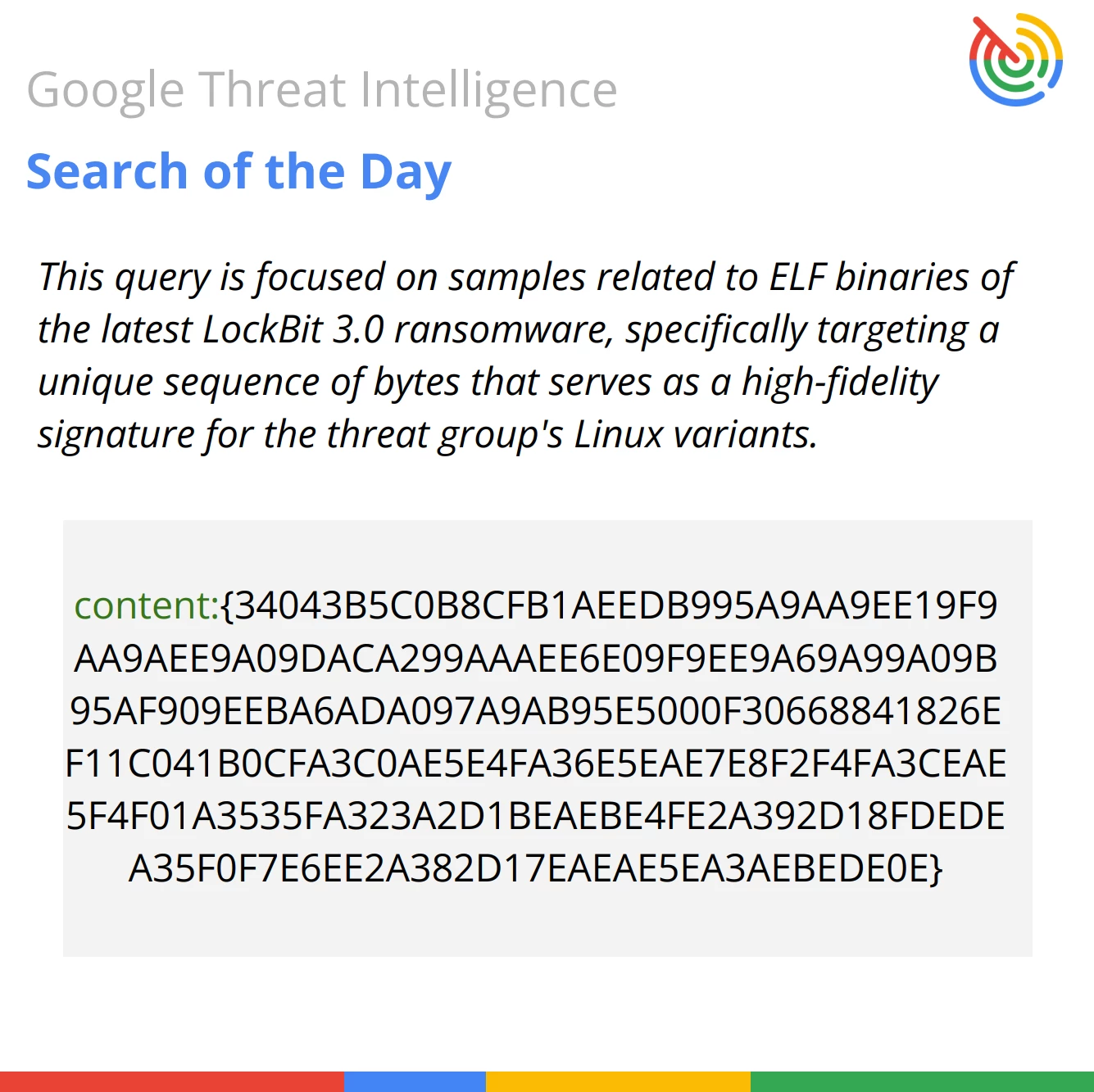
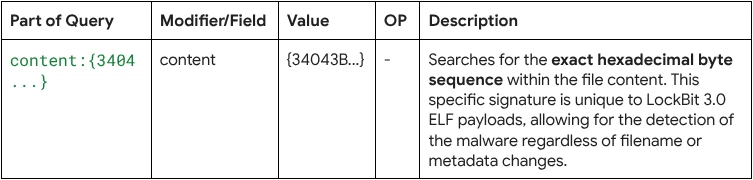
content:{34043B5C0B8CFB1AEEDB995A9AA9EE19F9AA9AEE9A09DACA299AAAEE6E09F9EE9A69A99A09B95AF909EEBA6ADA097A9AB95E5000F30668841826EF11C041B0CFA3C0AE5E4FA36E5EAE7E8F2F4FA3CEAE5F4F01A3535FA323A2D1BEAEBE4FE2A392D18FDEDEA35F0F7E6EE2A382D17EAEAE5EA3AEBEDE0E}
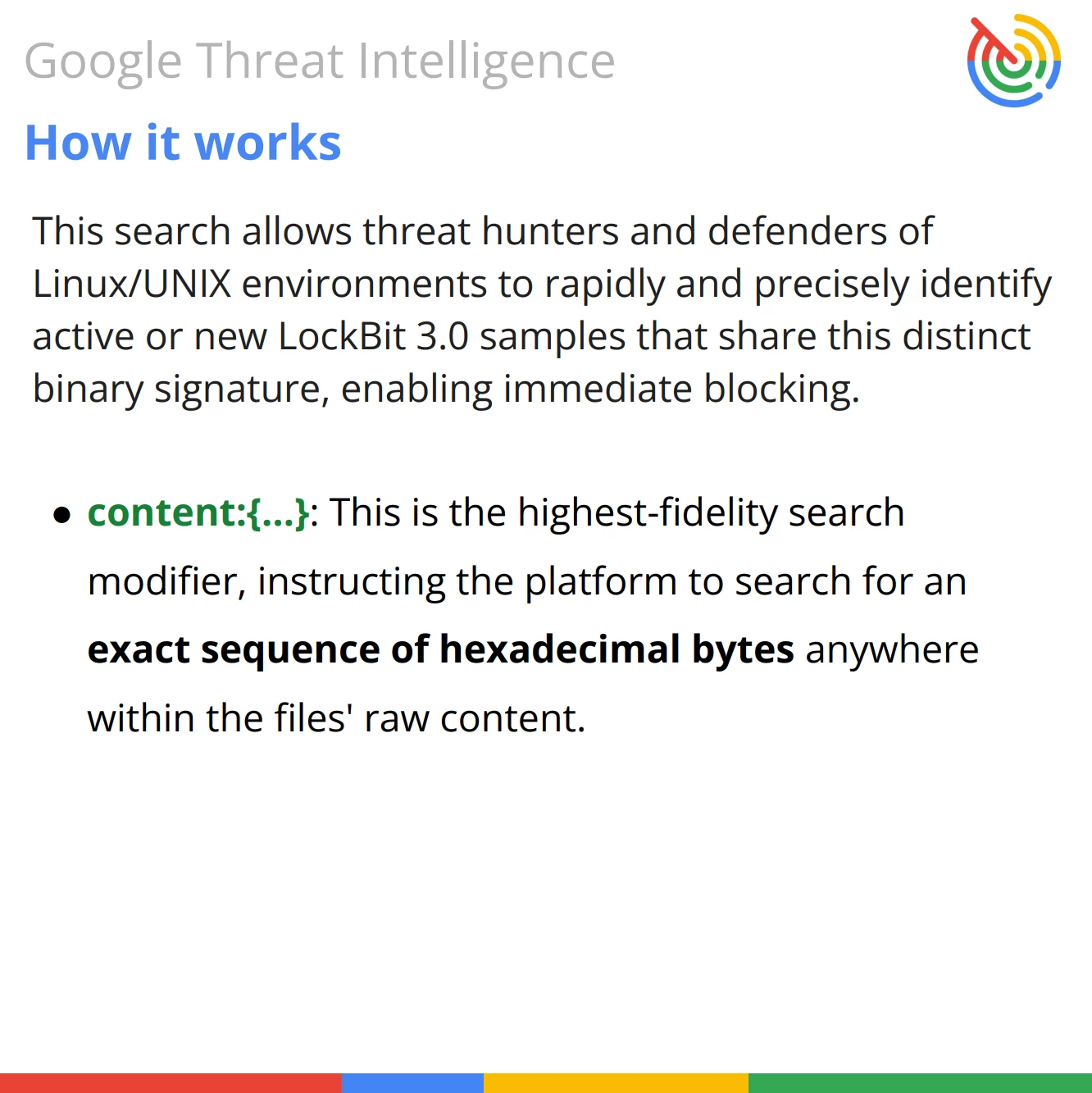
Query Breakdown: The query uses the content modifier to search for a specific hexadecimal string within the file's binary data, acting as a precise digital fingerprint for this specific malware strain.
Summary of Intent: The overall goal of this search is to rapidly and precisely identify active LockBit 3.0 samples targeting Linux/UNIX environments.
The search looks for:
- Target: LockBit 3.0 ELF ransomware (often used against ESXi servers and Linux infrastructure).
- Mechanism: It relies on content matching rather than metadata or behavioral reports.
- Precision: By using a long, distinct byte signature, it enables high-confidence detection for immediate blocking of new or active samples.
Author’s Note & Citation: The above Info-graphics are provided by both the VirusTotal team along with the use of NotebookLM for the summary graphic. Additional analysis and details of this search query written by the amazing


