

Day 4: Hunting Gamaredon-Related Document Activity
This Google Threat Intelligence search query is designed to find files that match a specific set of characteristics, generally indicative of a particular type of malware or activity.
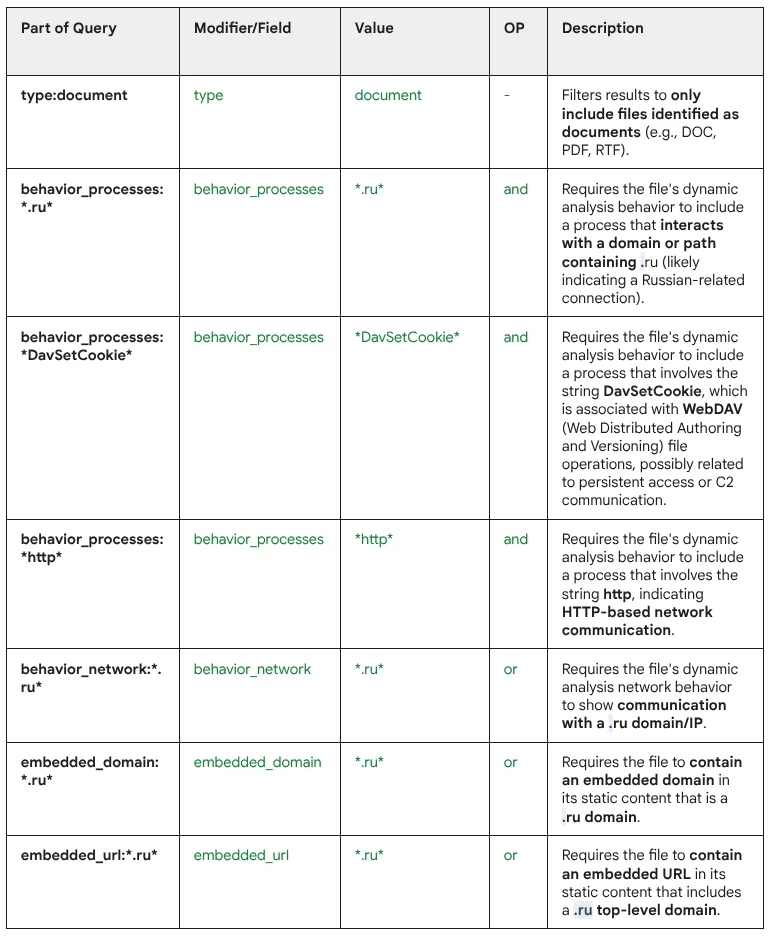
(type:document) and (behavior_processes:*.ru* and behavior_processes:*DavSetCookie* and behavior_processes:*http*) and (behavior_network:*.ru* or embedded_domain:*.ru* or embedded_url:*.ru*)

Query Breakdown: The query uses Boolean operators (and, or) and specific search modifiers (fields) to narrow down the results.
Summary of Intent: The overall goal of this search is to detect potentially malicious emails hiding behind privacy services.
The search looks for:
- File Type: The target must be an email file (type:email).
- Anonymity Service: It must utilize Onionmail.org (embedded_domain:onionmail.org), a service that can be abused for its anonymity.
- High-Risk Indicator: It must contain an attachment (have:email_attachment), distinguishing it from simple text-based spam and focusing on potential malware delivery attempts.
Day 5: Don't let a simple shortcut lead to a major breach…
This Google Threat Intelligence search query is designed to find files that exhibit specific obfuscated command lines during execution, often indicative of malicious shortcut (LNK) files disguised as documents.
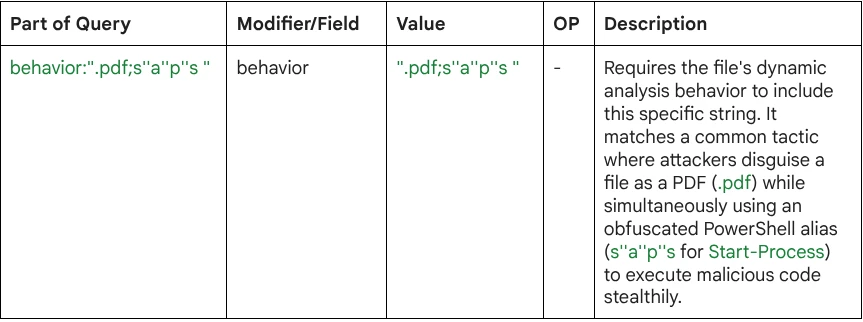
behavior:".pdf;s''a''p''s "
Query Breakdown: The query uses a specific search modifier (field) to identify a unique, obfuscated string within behavioral reports.
Summary of Intent: The overall goal of this search is to hunt for malicious LNK files that are trying to evade detection through masquerading and obfuscation.
The search looks for:
- Masquerading: The inclusion of .pdf in the command string suggests the file is attempting to appear as a legitimate PDF document to the user.
- Obfuscated Execution: The presence of s''a''p''s specifically targets a known obfuscation technique for the PowerShell Start-Process command, used to trigger hidden payloads without being immediately obvious to basic static analysis.
- Behavioral Confirmation: By using the behavior: field, this query relies on observed activity during sandbox execution, catching files that might look benign statically but reveal their true nature when run.
Author’s Note & Citation: The above Info-graphics are provided by both the VirusTotal team along with the use of NotebookLM for the summary graphics. Additional analysis and details of this search query written by the amazing


