This is a question that has come up more than once, particularly when DTM Research Tools is being used. It can also occur when viewing Compromised Credential Monitor Alerts.
tl;dr this is by design, to protect any entity whose compromised credentials appear in DTM. There are steps you can take to view your own compromised credentials in a safe, controlled way.
First, a word on Research Tools:
Research Tools enables users to safely explore open-source, dark web, and raw data that Google Threat Intelligence has collected for Digital Threat Monitoring. Providing raw threat and related data in an easy interface, Research Tools helps you find what matters, see what is happening in the cyber realm, and thus better protect your business. We recommend you use Research Tools as a precursor to creating a Monitor. This will help you create Monitors focused on what matters and reduce false positives.
Safely explore means, among other things, we do not allow users to view plaintext compromised credentials via Research Tools. This ensures that every organisation and individual that has suffered a credential leak is protected from any malicious third-party that might seek to exploit this information, at least where we can control things, within our solution.
However, it is possible to view your own compromised credentials in full, but only via a Compromised Credential Monitor with a relevant alert. This allows a greater level of control and auditing, since there are also granular DTM User Roles. This means that creating, editing, and accessing Monitors can be restricted to trusted users or admins only. In addition to these Monitor User Roles, the following specific User Roles for a Custom DTM Admin and/or DTM User exist:
- View Cleartext Passwords for verified domains on Compromised Credentials alerts
- Download Credentials
- View account login details on Compromised Credentials alerts
Once you have configured your admins/users with appropriate User Roles, they can
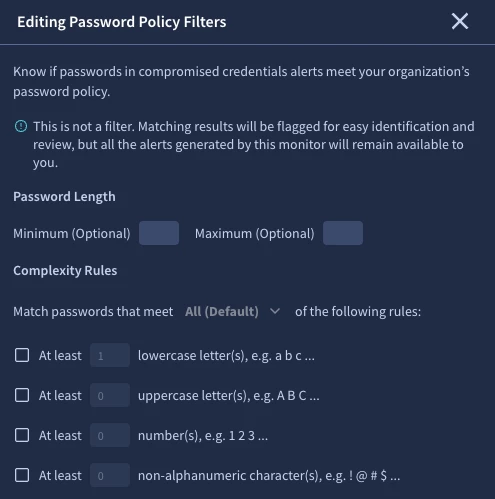
configure one or more Compromised Credential Monitors. When you create a Compromised Credential Monitor, there are a few specific menus that can be configured, one of the most important being Password Policy:
This is not actually a filter in the sense that it will not exclude alerts, but it does mean you can prioritise any alerts involving a password that meets your password policy, since they are likely to be a higher risk than a leak of a short, simple password that would never be allowed by your authentication systems complexity requirements. This is something you would see within the Monitor's Alert page, if configured, and is optional but recommended, particularly if you are seeing many hits from the monitor and would benefit from a way to prioritise them:
Finally, to view plaintext passwords, you will need to verify ownership of your domain (or domains) via this procedure. I
n summary:
Verify domain ownership with a TXT record.
Verifying ownership of a domain lets us enrich associated alerts with additional details such as PII that otherwise would not be displayed. This improved context typically results in more actionable alerts. For more information on verifying domains with a TXT record, including step-by-step instructions, see
Verify your domain with a TXT record.
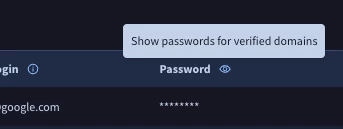
Once verification is complete, you will find that you can toggle this 'eyeball' icon next to relevant domains, and view plaintext passwords relating to your domain(s).
We hope that you do not find your own compromised credentials within our platform, since that means that they already exist somewhere else, such as the dark web. However, if you have correctly configured the above monitors and are alerted to a credential leak, you can efficiently resolve the compromise by following your normal procedures, such as forcing a reset of the password or blocking the account from logging in. You can use the wider Google Cloud Security product suite to investigate how the breach occurred to begin with, whether this is part of an ongoing incident, and address threats with AI-infused technology.
Postscript: If your organization suspects a cyber incident or are experiencing a security breach then contact us for breach response assistance. You can contact us in any one of the following ways: Complete the form in the link below, call us directly: US: +1 (844) 613-7588, International: +1 (703) 996-3012, or email our incident response team at investigations at mandiant dot com. https://cloud.google.com/security/report-incident