Authors: Raimundo Alcazar and Vik Singh
This guide introduces you to Google Threat Intelligence's Threat Profile, that provides a composite picture of the most relevant and potent cyber threats to your organization. It moves beyond generic threat intelligence by focusing on the specific adversaries, their motivations, their capabilities such as tactics, techniques, and procedures (TTPs) they are likely to employ against your unique environment, all while tracking how they change over time.
This guide is designed to be a comprehensive resource for Cyber Threat Intelligence (CTI) and other cybersecurity analysts. It balances conceptual understanding with practical examples and instructions.
Conceptual Overview: Developing a Cyber Threat Profile
A Cyber Threat Profile is a tailored, high-level summary of the potential cyber threats that are most relevant to a specific organization. It moves beyond a generic understanding of the global threat landscape to provide a focused view on the adversaries, their motivations, and their likely methods of attack against that particular entity.
To remain effective, the Threat profile must be actively maintained, requiring continuous updates to reflect the constant evolution of adversary tactics and changes within your own organization.
Main key uses for organizations are:
- Threat Model:
The threat profile is your security program’s source of truth for the threats that matter most to your organization.
Use Case Example: Focus on financially motivated threats, such as ransomware campaigns targeting the U.S. financial sector, and ensure continuous updates to reflect evolving trends.
- Research:
The threat profile is a place for CTI functions to tailor and curate emerging threats they are analysing.
Use Case Example: Focus on ingress nightmare threats, tracking associated vulnerabilities, and the campaigns and actors leveraging them, ensuring continuous updates over time.
The Threat Profile helps an organization to:
- Understand RelevantAdversaries: Identify the specific threat actors that are most likely to target the organization based on its industry, geography, and other criteria.
- Anticipate Attacker Behavior: Gain insight into the tactics, techniques, and procedures (TTPs) that these adversaries are known to employ. This includes understanding their motivations, capabilities, and the types of assets they typically target.
- Prioritize Defensive Efforts: Focus the organization security resources on mitigating the most probable and impactful threats, rather than attempting to defend against every conceivable attack vector.
By developing and maintaining a Threat Profile, an organization can realize several key benefits:
- Make strategic decisions: about security investments, risk management, and overall business strategy.
- Tailor defenses: to enhance the organization security controls, monitoring, and incident response plans.
- Proactive Defense: It shifts the organization's security posture from reactive to proactive approach.
In essence, a Cyber Threat Profile is a foundational element of modern cybersecurity, enabling a more focused, efficient, and effective defense against the ever-evolving landscape of digital threats.
Next image introduces you to the components of Google TI’s Threat Profile. Let’s explore how to use it in the next section.
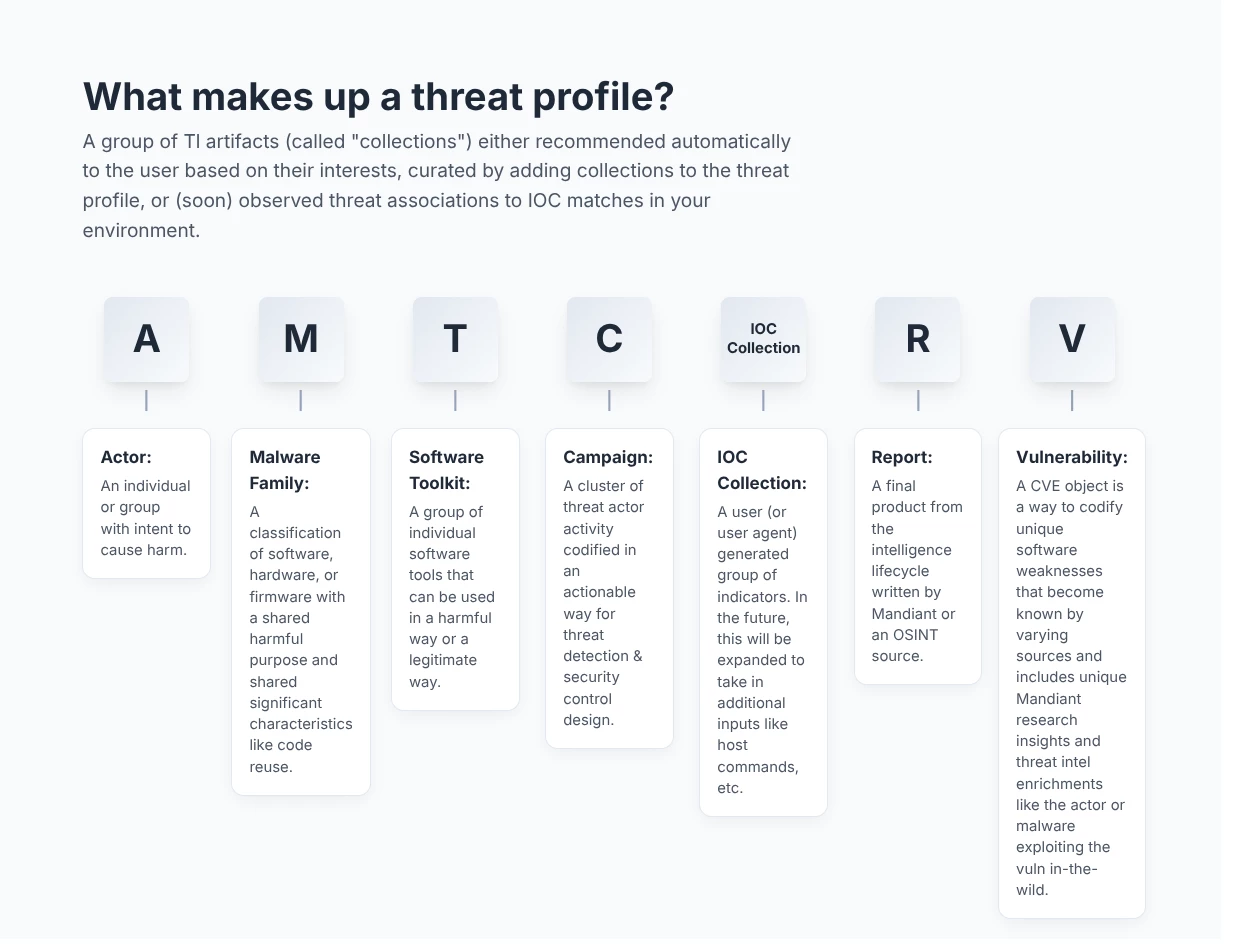
A GUIDED TOUR
Our Threat Profiles module in Google TI provides a customized view of Google's vast threat intelligence data. You define a profile by setting specific criteria, such as targeted industries, regions, malware roles, and actor motivations.
There are two key ways to populate your threat profile:
- Automatic threat profile creation. Our relevance algorithm uses these criteria to identify and recommend the most relevant threats—including Threat Actors, Malware & Tools, Campaigns, IOC collections, Vulnerabilities and Reports. This process creates a personalized profile tailored to your organization's unique risks, allowing you to focus on the threats that matter most.
- Manual research additions. The threat profile functionality is flexible and allows users to add additional threat objects such as actors, malware, campaigns, vulnerabilities and even reports for research projects or specific investigations you may be conducting where you need to supplement the automatic method.
To illustrate how to use a Cyber Threat Profile in Google TI, this guide will present a case study of a global innovative medicines company that operates in Europe (manufacturing division) and the United States (BioMedical research division).
As you can imagine the company's most critical assets are its vast portfolio of intellectual property related to pharmaceutical research and development, and its technologically advanced manufacturing and supply chain operations. Threat actors could be motivated by corporate espionage, intellectual property theft, and service disruption for financial or strategic gain.
In this case, we will create separate Threat Profiles in Google TI for each business branch and region:
| Threat Profile name | Target industries | Target regions |
| TP1: Innovative medicines company | Manufacturing operations | Switzerland and Germany (Europe) |
| TP2: Innovative medicines company | Pharmaceutical Research and development | New Jersey (United States) |
1.1: Threat Profile creation:
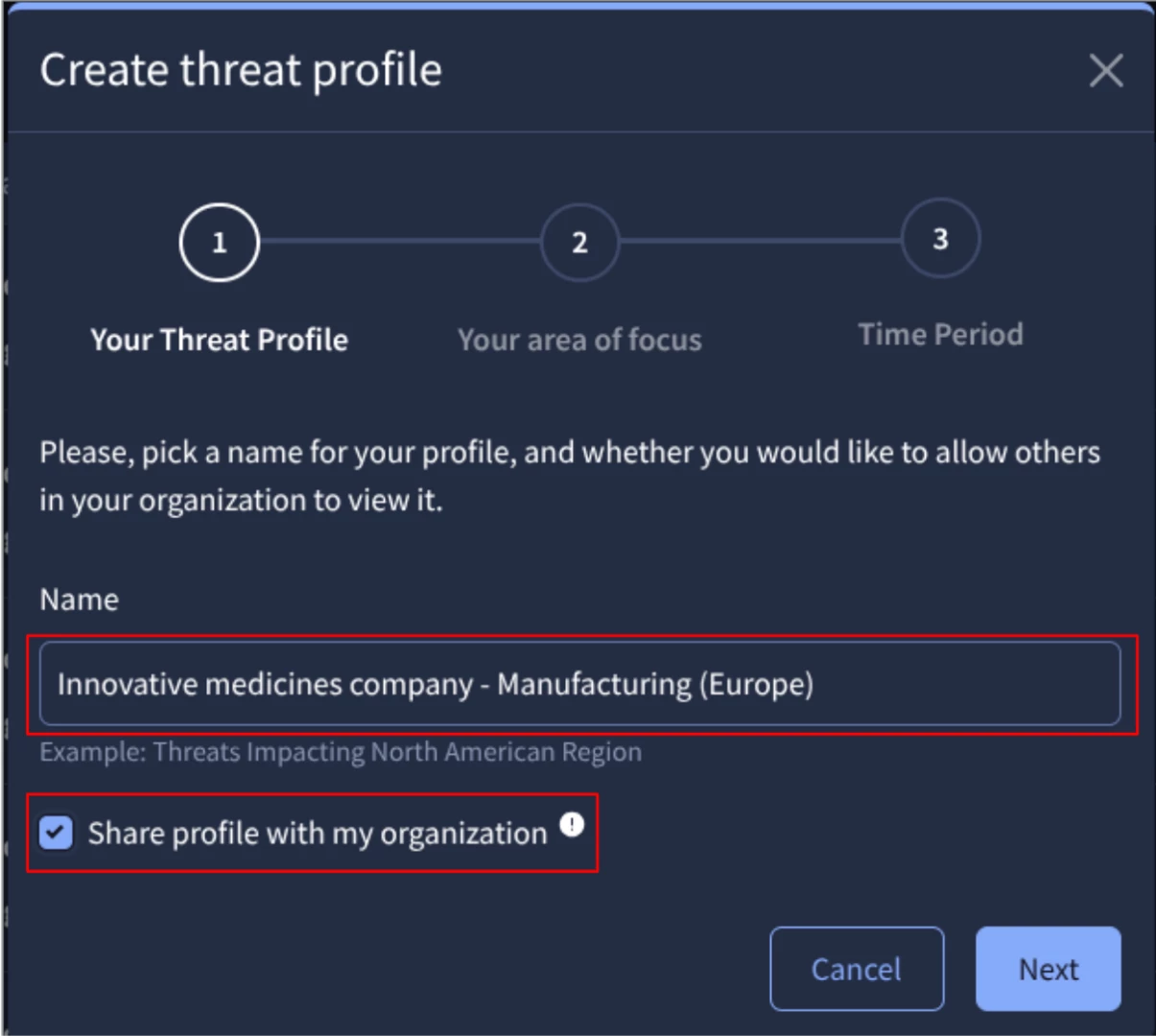
To create these threat profiles navigate to Threat Profiles in Google TI and click on the “Create Threat Profile” button. In the form that appears, enter the following details for TP1:
STEP 1: Name your Threat Profile and decide if you want to share it with your organization.
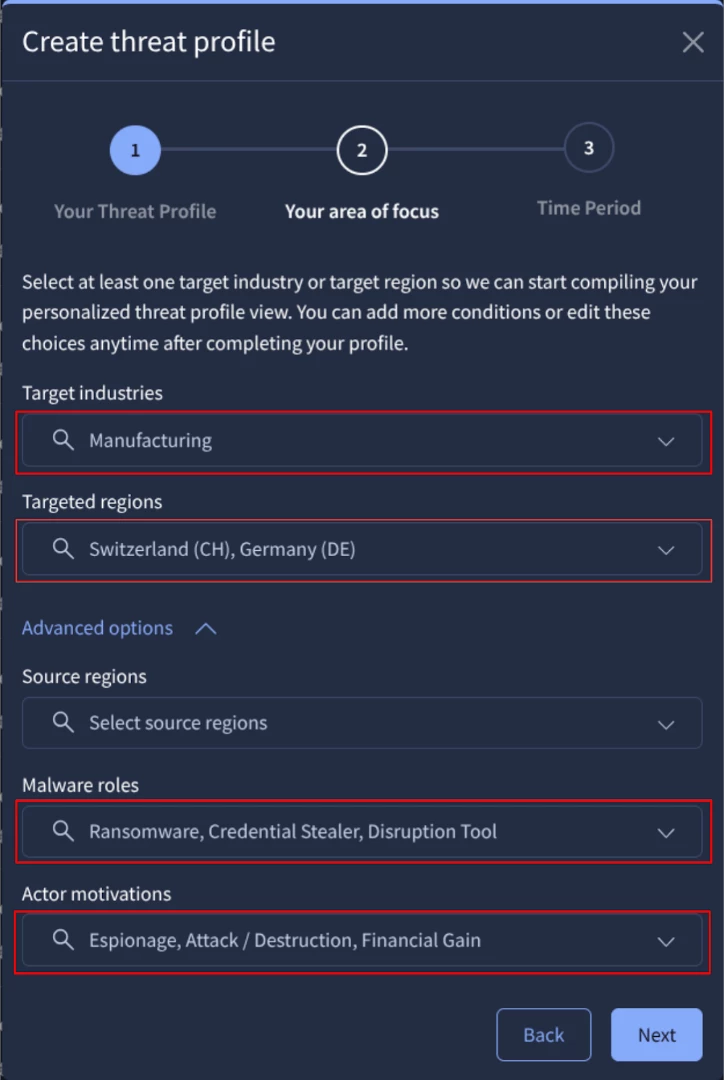
STEP 2: Select the area of focus to customize your profile:
At least you have to provide the Target industries and Targeted regions. In this case, there will be manufacturing operations with presence in Switzerland and Germany.
Based on your information you can select other Advanced options, such as Source regions, Malware roles, and Actor motivations that you could be interested in. For this example, we have considered these information:
| Source regions | Malware roles | Actor motivations |
| -- | Ransomware, Credential Stealer, Disruption Tool. | Espionage, Attack / Destruction, Financial Gain. |
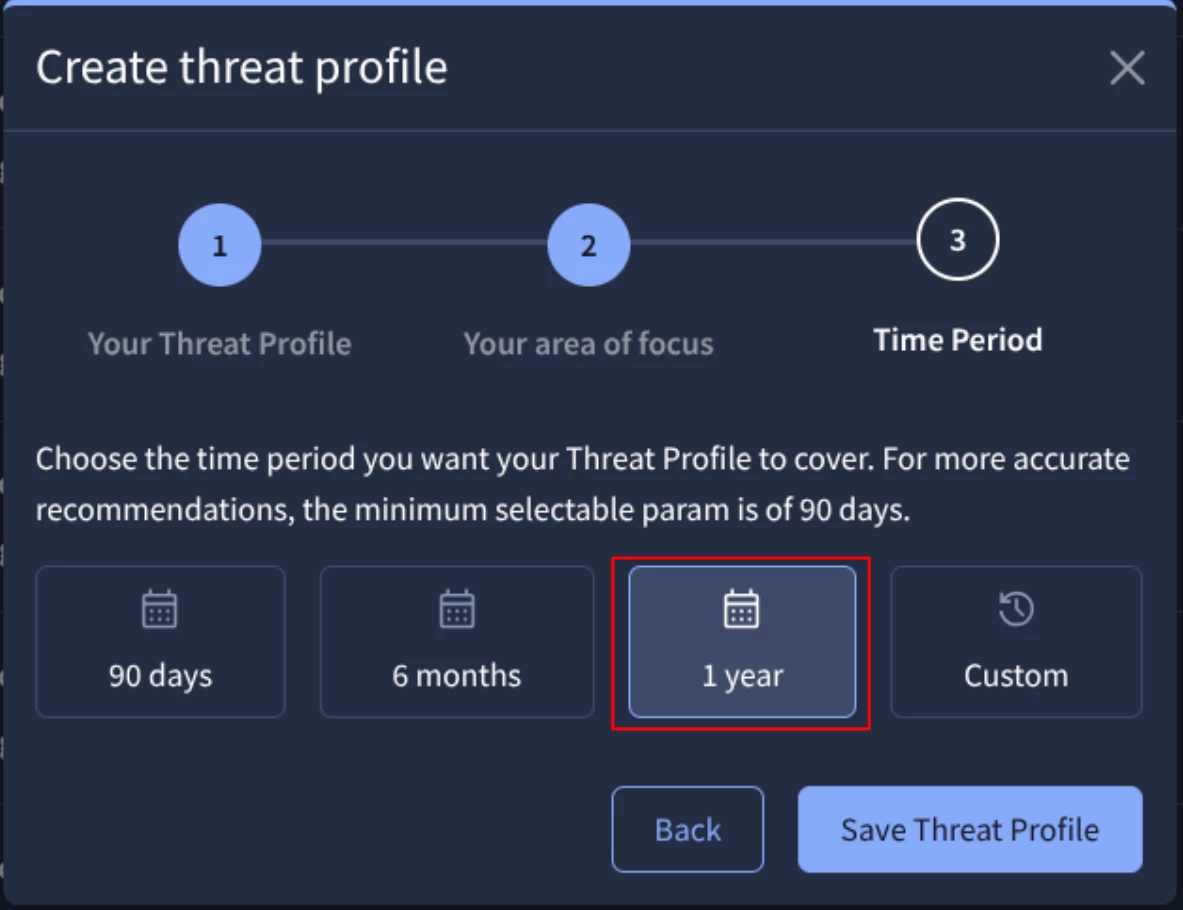
STEP 3: Select the time period for the threat profile.
As you can know the Threat Landscape is always evolving and your threat profile is also a living framework used to identify a baseline of significant threats to an organization, so you can define if needed a specific time period to be covered.
It is recommended to repeat these steps to create the second threat profile referred to the ‘Research and development (United States)’ branch of the organization.
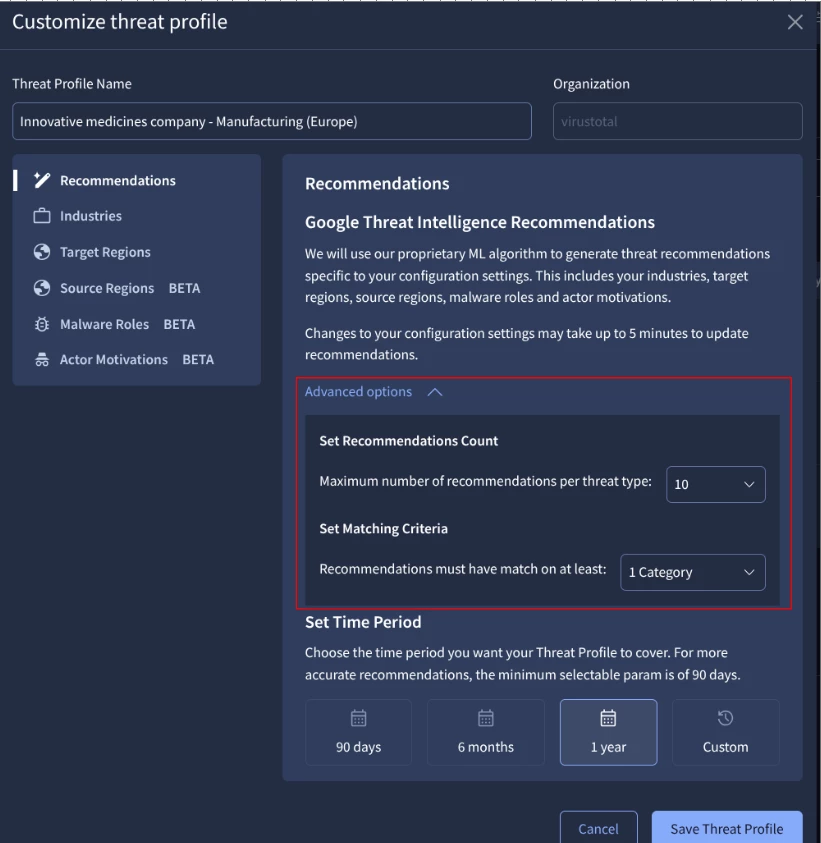
Once your Threat Profiles are created, you can edit them to fine-tune recommendations, such as setting:
- Maximum number of recommendations per threat type:
For example, let’s select 15 recommendations per each threat type (actor, malware family, campaigns and more).
- Number of categories on matching criteria that the recommendations must have matched on at least:
For instance, select at least 2 category criteria, that means 2 of the following categories: Industries, Target Regions, Source Regions, Malware Roles, and Actor Motivations.
1.2: Managing your Threat Profiles:
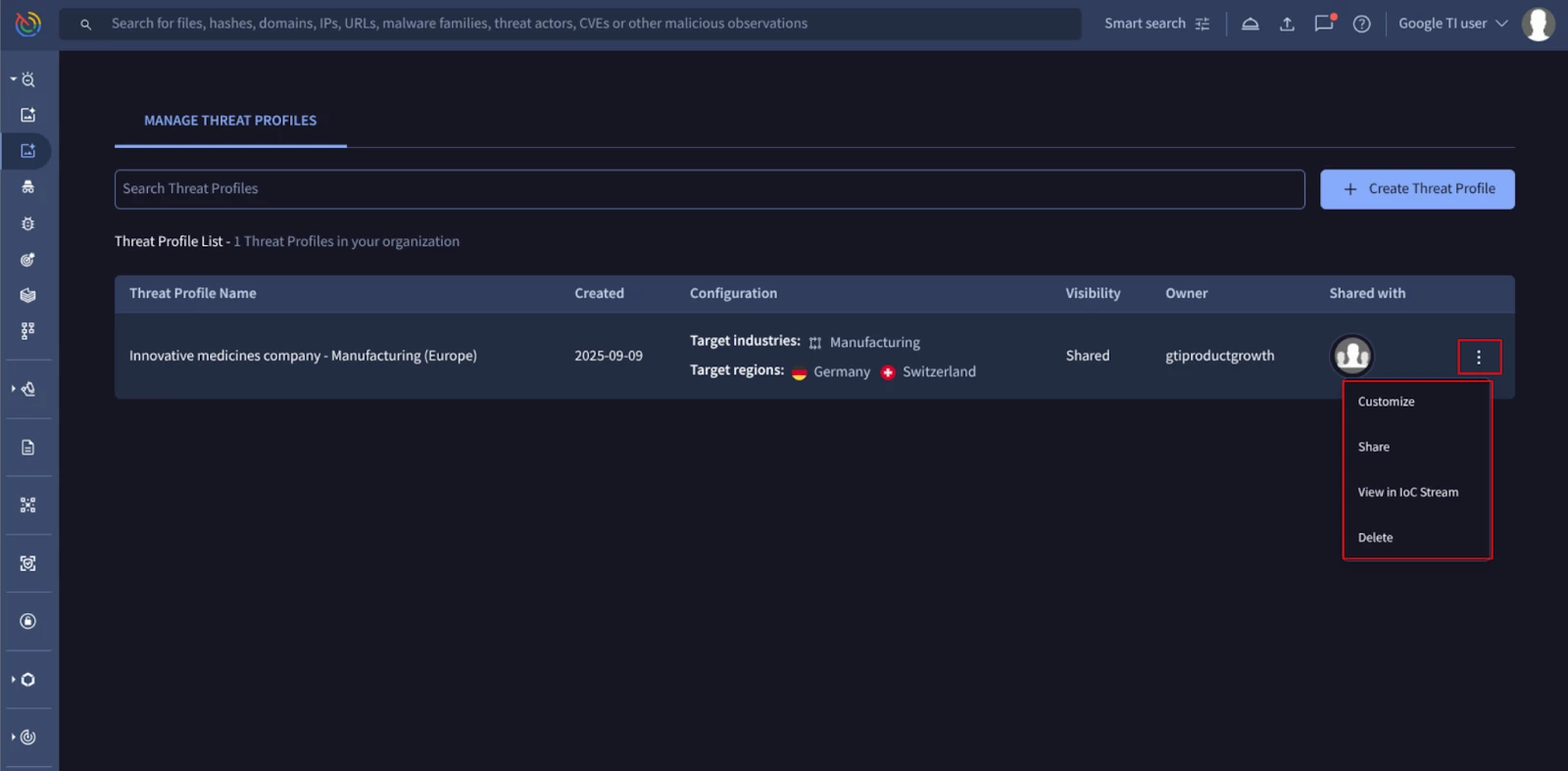
Once the Threat Profile has been created, you can manage it to share, delete, or customize it (if you did not do so previously), as shown in the next image:
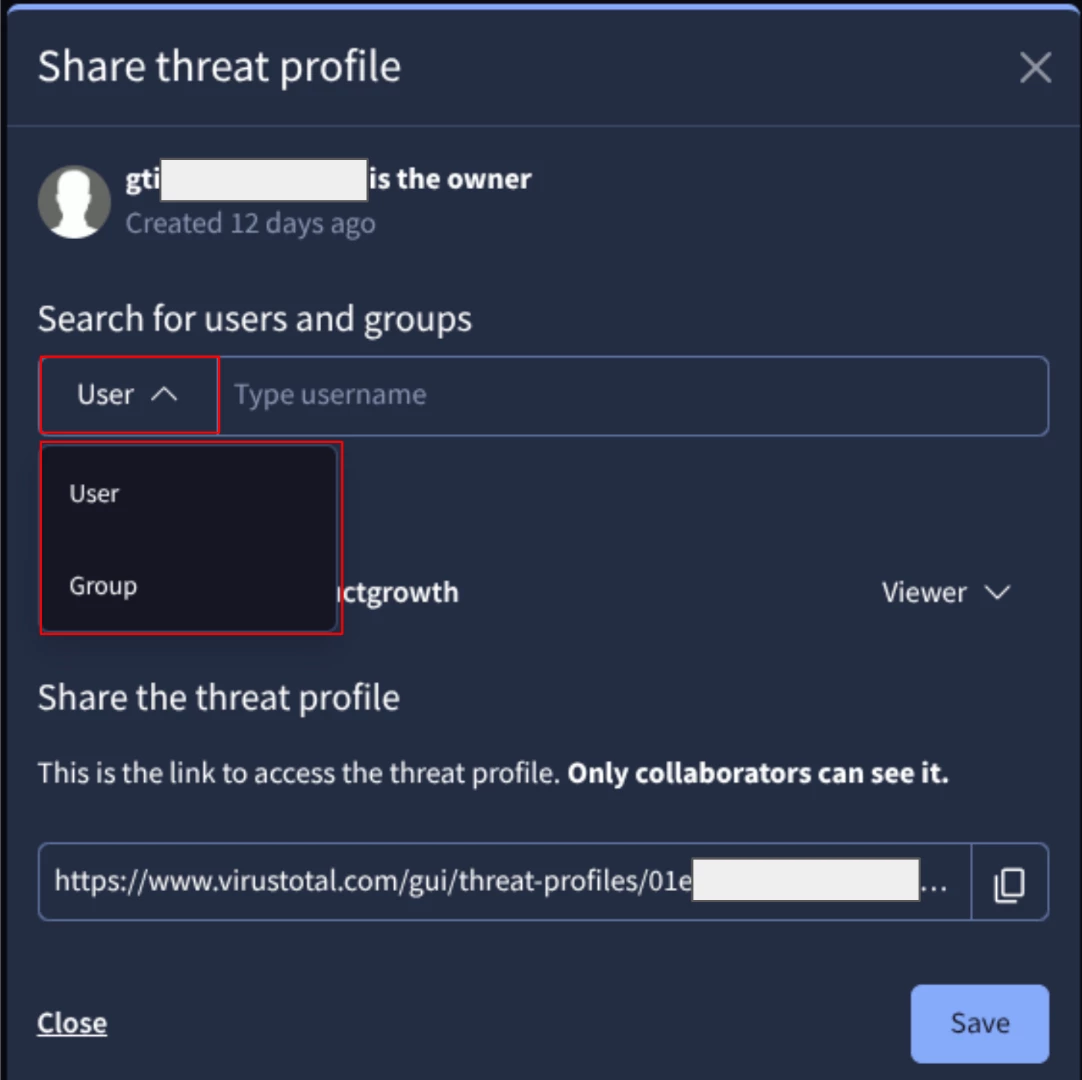
We will now focus on the 'Share' option. You can use this option to share your Threat Profile with a teammate as an 'editor' or 'viewer,' or share it with your entire organization in either role as you can see in the next image. This makes it easy to collaborate on your source of truth for relevant threats.
1.3: Exploring your Threat Profile List:
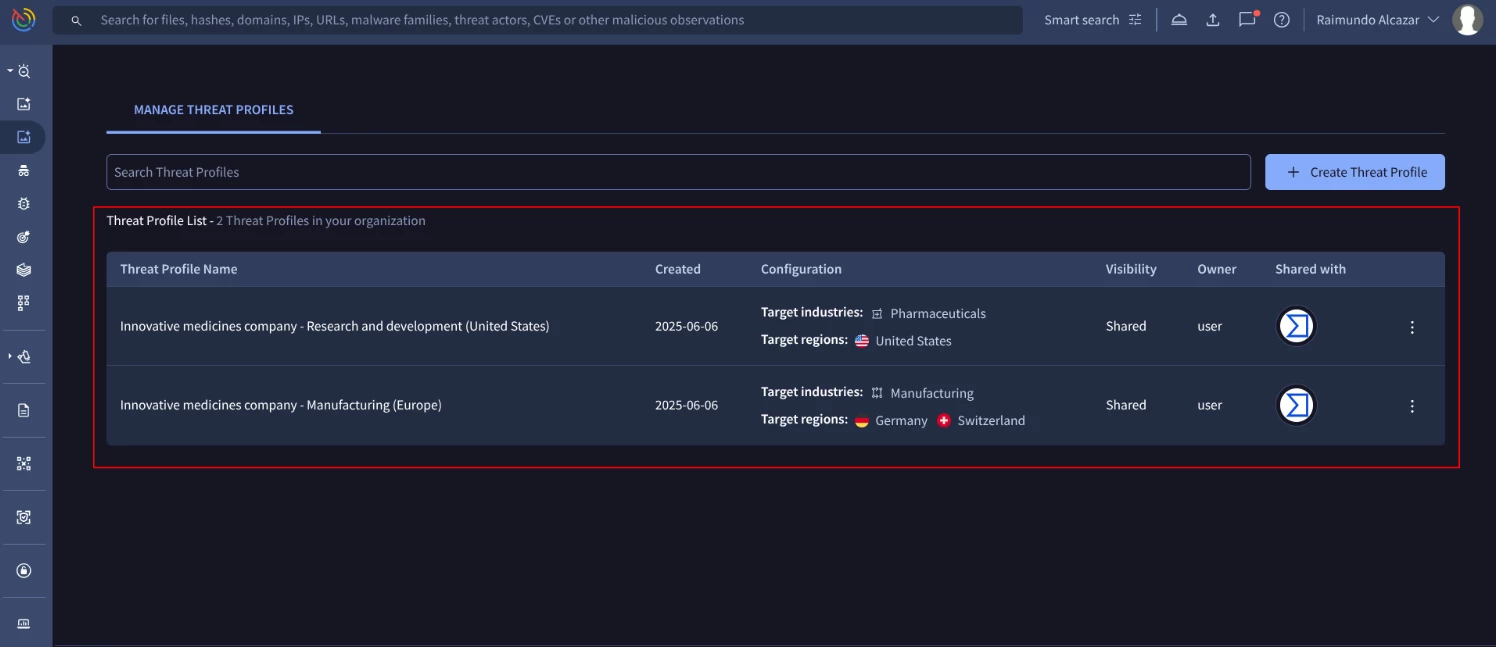
To access your created threat profiles, click on Threat Profiles in the left-hand menu:
Select the desired Threat Profile from the list to open the Threat List panel:
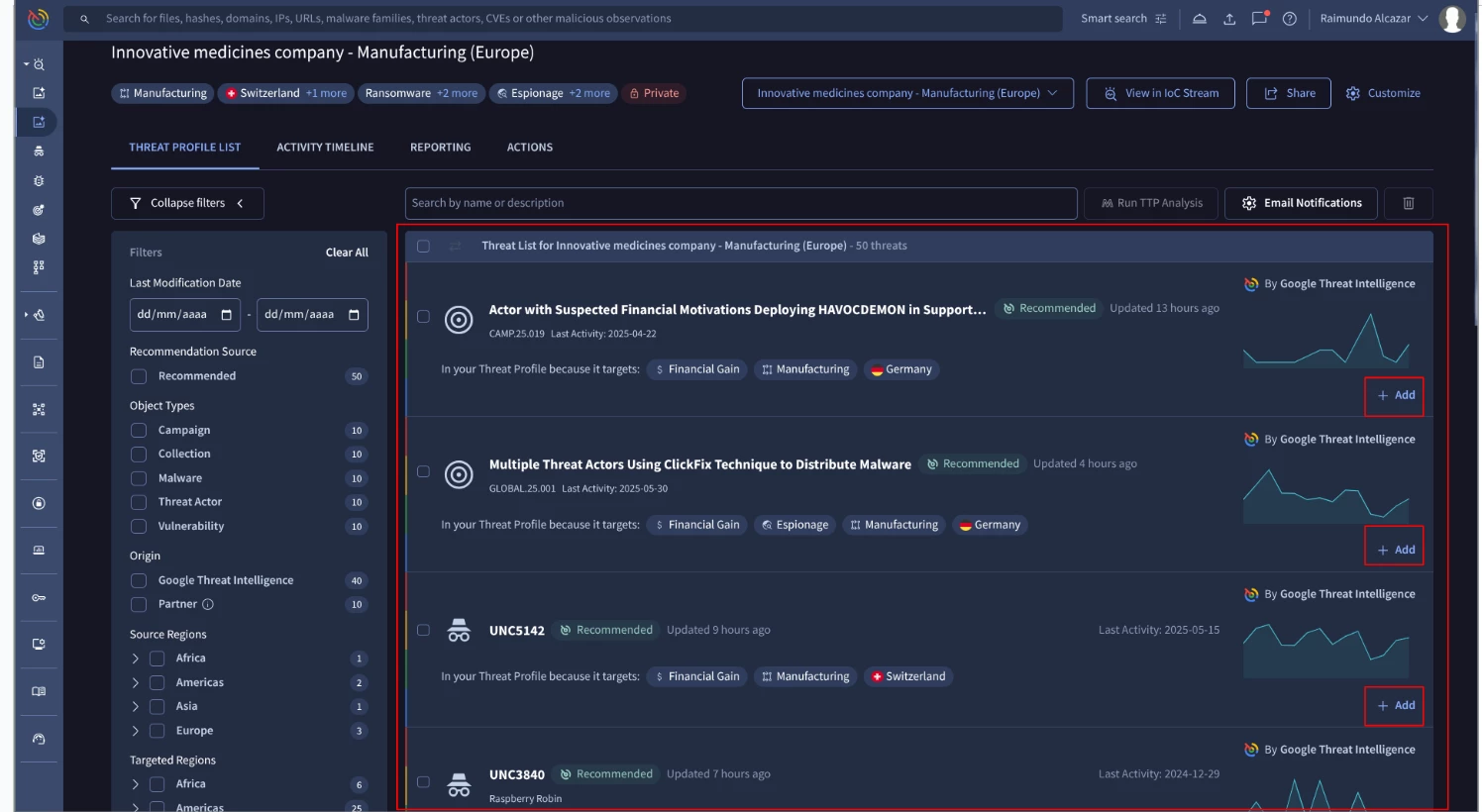
To add a threat from this list to your profile, click its ‘Add’ button. Each threat includes the matching criteria explaining why it was recommended, as shown in the image below:
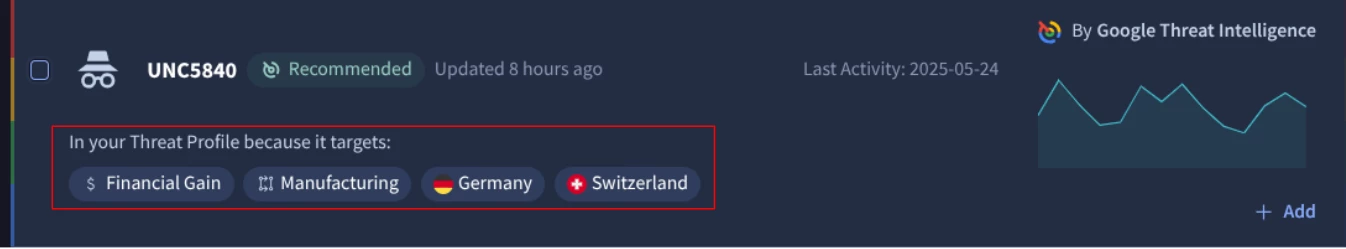
To get more relevant suggestions, use the filters on the left to narrow the results.
Review the suggested threats, select the ones you want to track, and your profile will be ready to use.
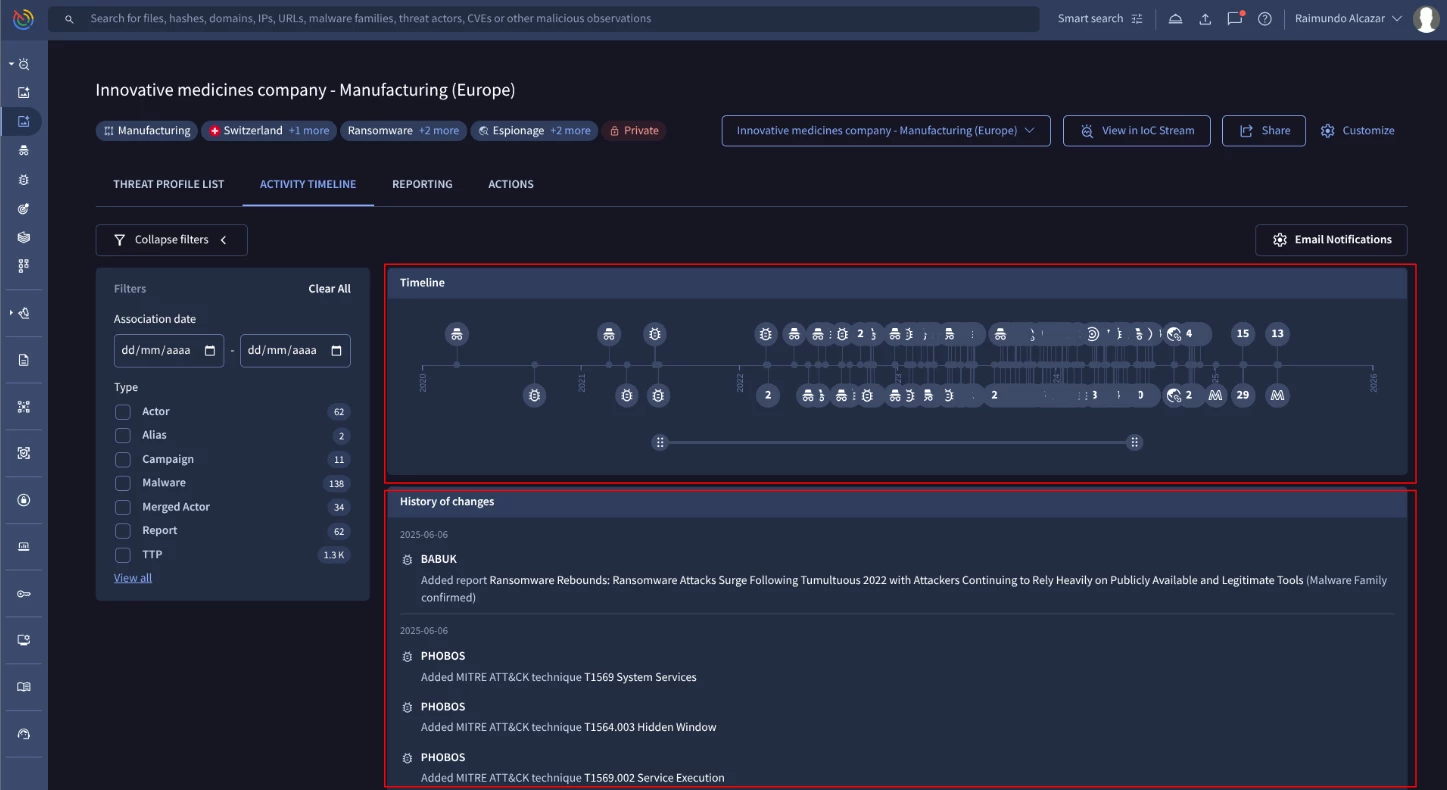
The threat profile also contains other valuable sections, including the ‘Activity timeline’, ‘Reporting’ and ‘Actions’:
The ‘Activity timeline’ displays how these threats have evolved over time, including all historical changes.
The ‘Reporting’ provides you with different reports created by the Google Threat Intelligence experts and related to your current threat profile.
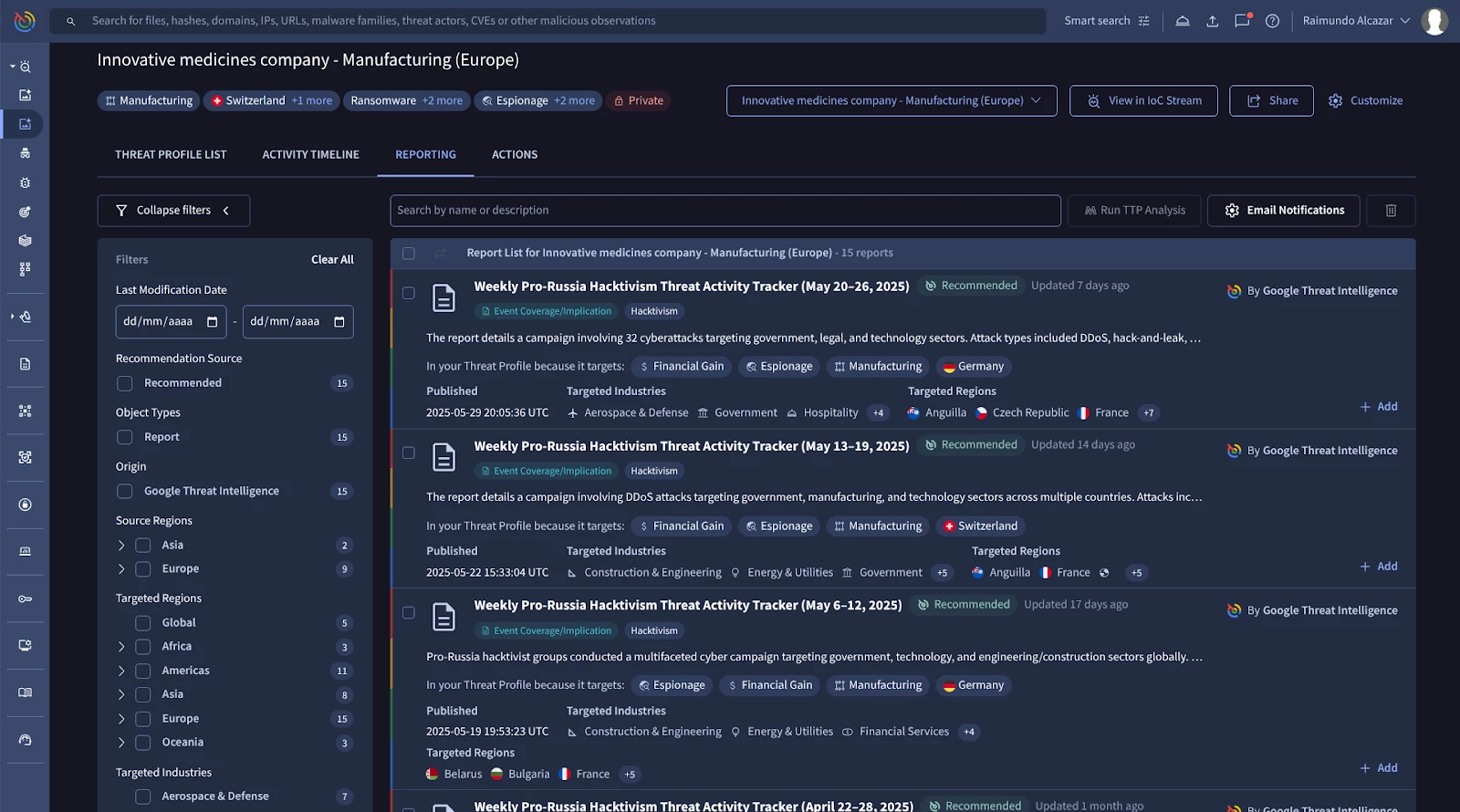
Next, ‘Actions’ offers the user the way to operationalize this threat intelligence from the threat profile. You can do that in these ways:
- Integrating the IOC stream
- Analyzing attacker TTPs
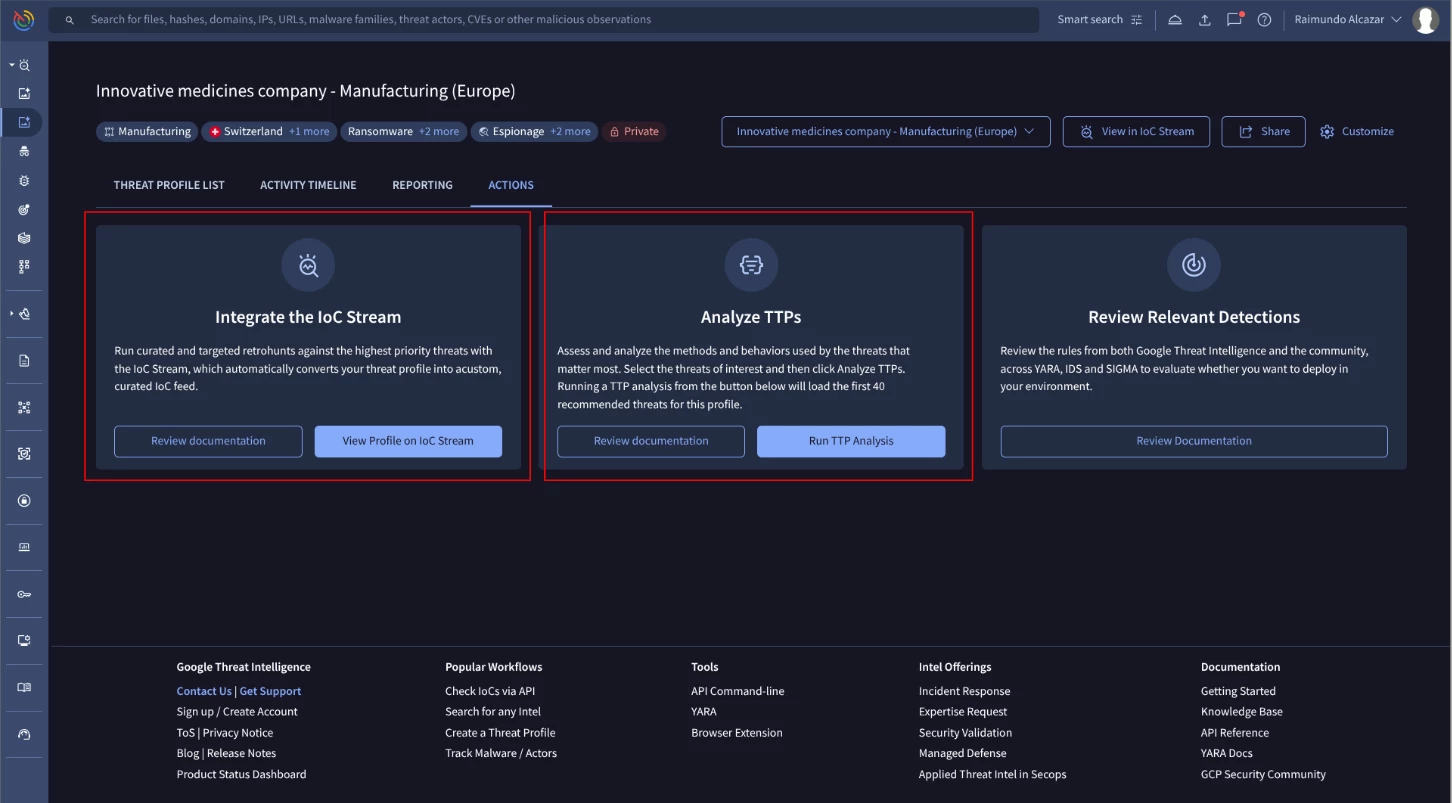
Integrate to the IOC stream:
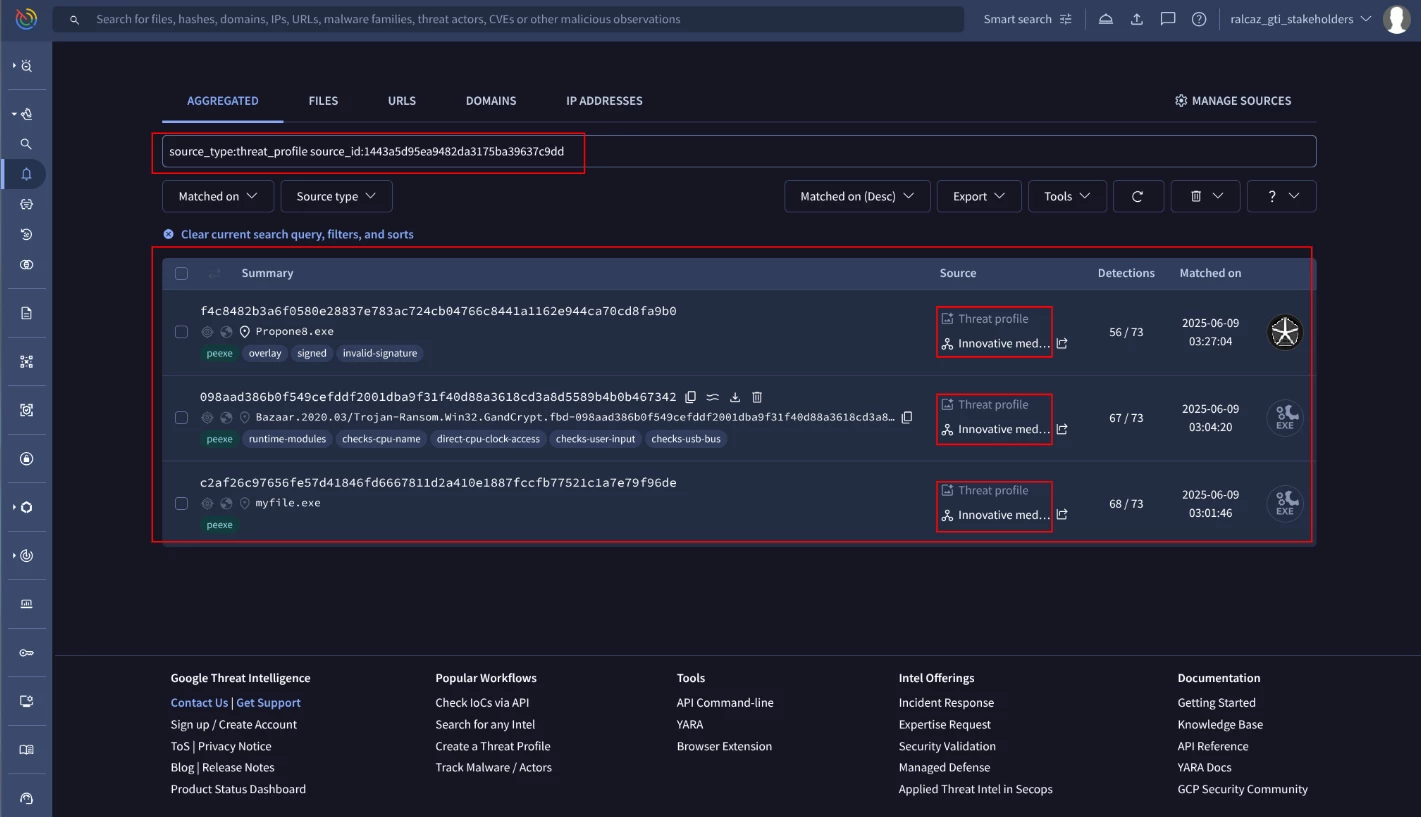
The IOC stream is designed to provide a curated list of very recent IOCs from different sources from Google TI, one of which is the Threat Profile. The IOCs will only show up if they were recently added to a collection inside of your threat profile and age out after 7 days.
To access this information, click the “View Profile on IOC stream” button. You will see the curated list of IOCs coming from the Threat Profile as shown in the image below:
TTP analysis:
This option automatically runs a TTP analysis on the top 40 recommended threats. You can also customize the analysis by selecting specific threats first.
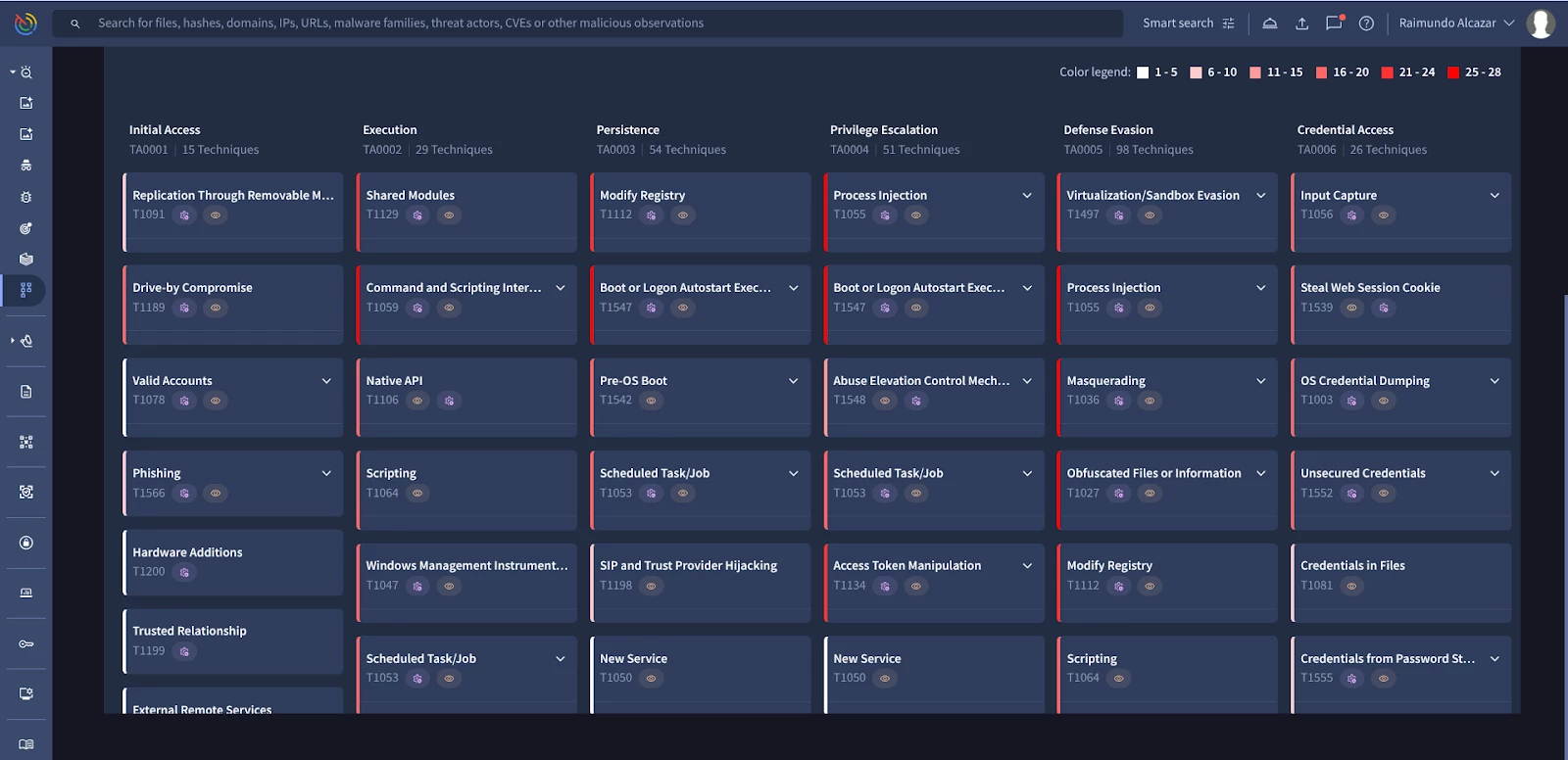
This heat map of adversary TTPs is a powerful tool for proactive defense. Cross-reference the highlighted techniques with your security controls to perform a gap analysis and identify your weakest areas.
For deeper analysis, you can download the MITRE ATT&CK heat map in CSV or JSON format.
Finally, it is possible to activate the email notifications. These notifications help you to track the changes in Threat Profile as things evolve. Follow these steps:
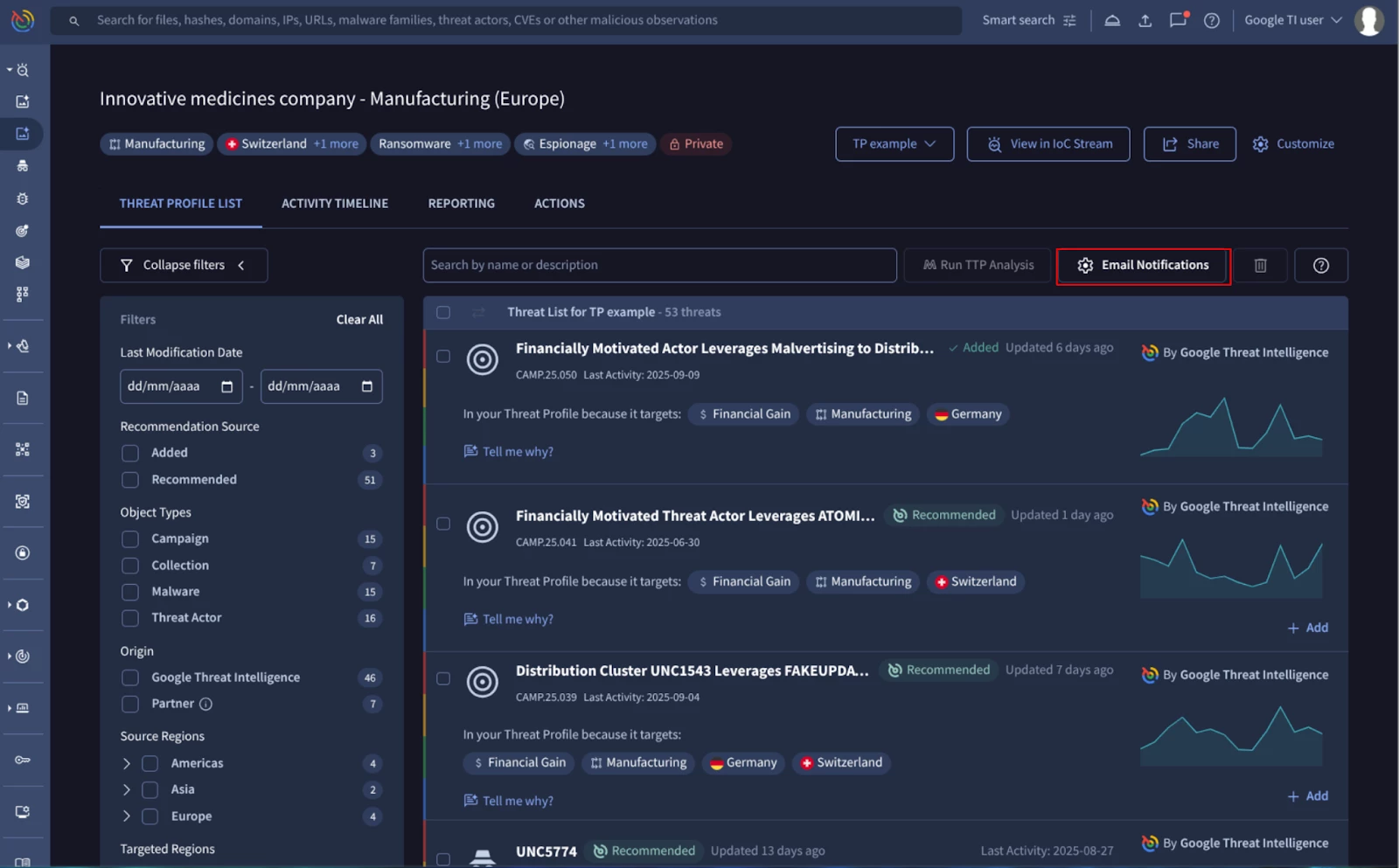
- Click on the “Email notifications” button.
- Scroll down to the “Email notifications” section.
- Click on the “+ New notification”.
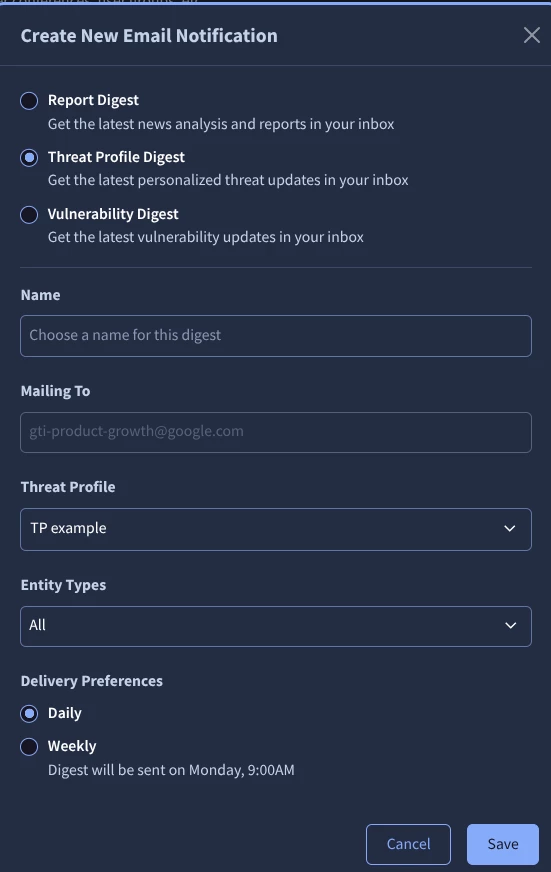
- Choose Threat Profile digest: Personalized threat updates in your inbox.
- Select a name for the notification.
- Select the threat profile you are interested in receiving updates.
- Select the 'Entity Types’ to choose what options you are interested in, including:
- Malware family
- Software toolkit
- Campaign
- Collection
- Threat actor
- Report
- Vulnerability
- TTP Deep Dive
- Weekly Vulnerability Exploitation Report
- Select the delivery preferences: Daily or weekly.
- Finally, save the changes.
1.4: Adding more value to your Threat Profile:
After adding the initial suggestions, you can further customize your Threat Profile with internal data from past incident response cases. For example, you can add threat actors or malware that weren't originally suggested.
To add a new item, use the left-hand menu to find the object you want to include in your profile:
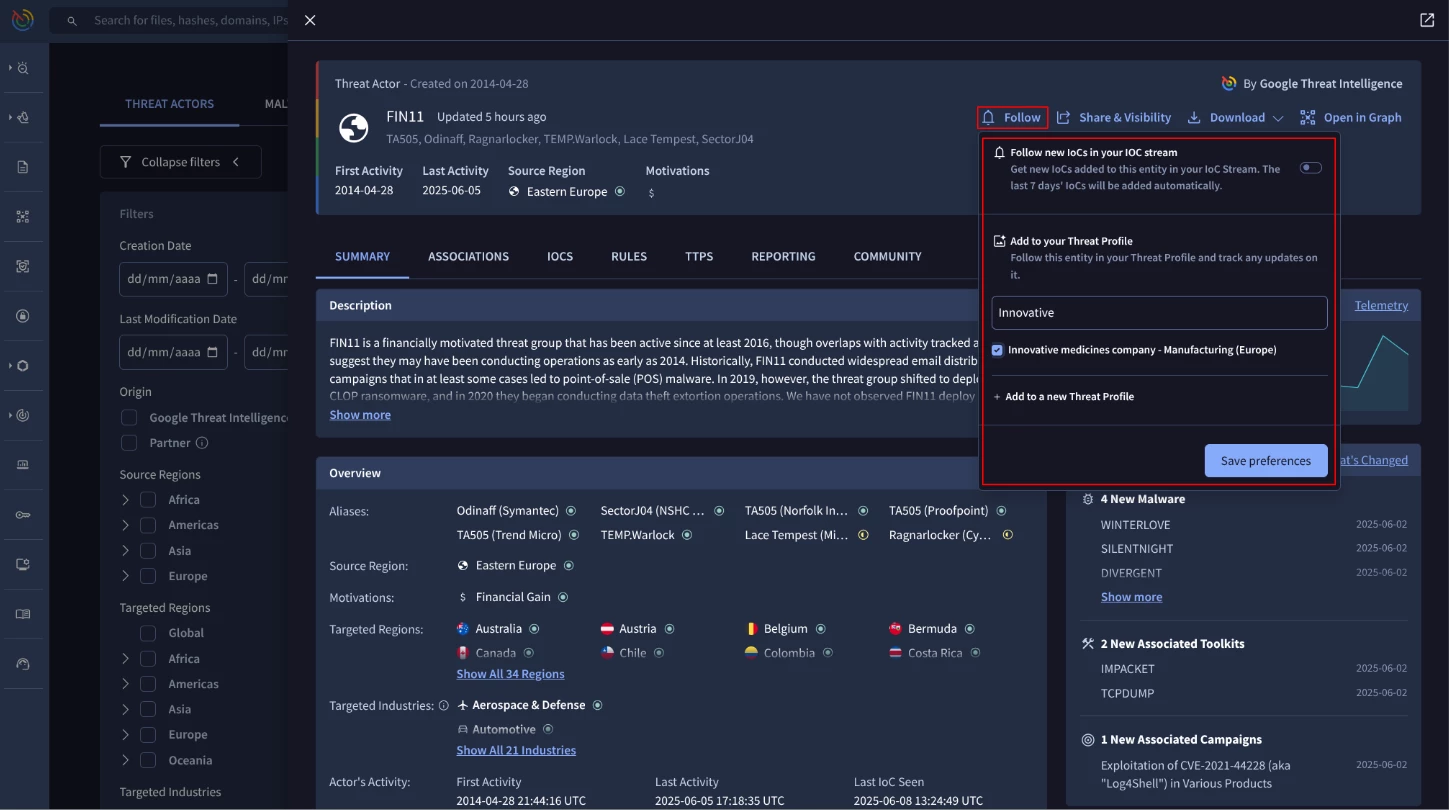
First, search for the FIN11 threat actor and open its profile card. Next, click the ‘Follow’ button. Then, find the ‘Add to your Threat Profile’ section and select the desired profile(s) to add it to.
The same process can be used again to add other objects to your profile, including Threat Actors, Malware and Tools, Campaigns, IOC Collections, and even Reports and Vulnerabilities.
1.5: Automatically generate or access a Threat Profile via API:
It is also possible to obtain the same information through the Google TI’s API. Here, you will find the official documentation on the current endpoints that can be used.
Below are some examples of how to use it. These Python code snippets provide basic examples of how to automate the Threat Profile data consumption.
Authorization can be achieved using your personal API key or a Service Account API key, which is not tied to a specific user.
In order to run this examples, you will need to find out your Threat Profile ID, that you can see in the browser’s URL bar:
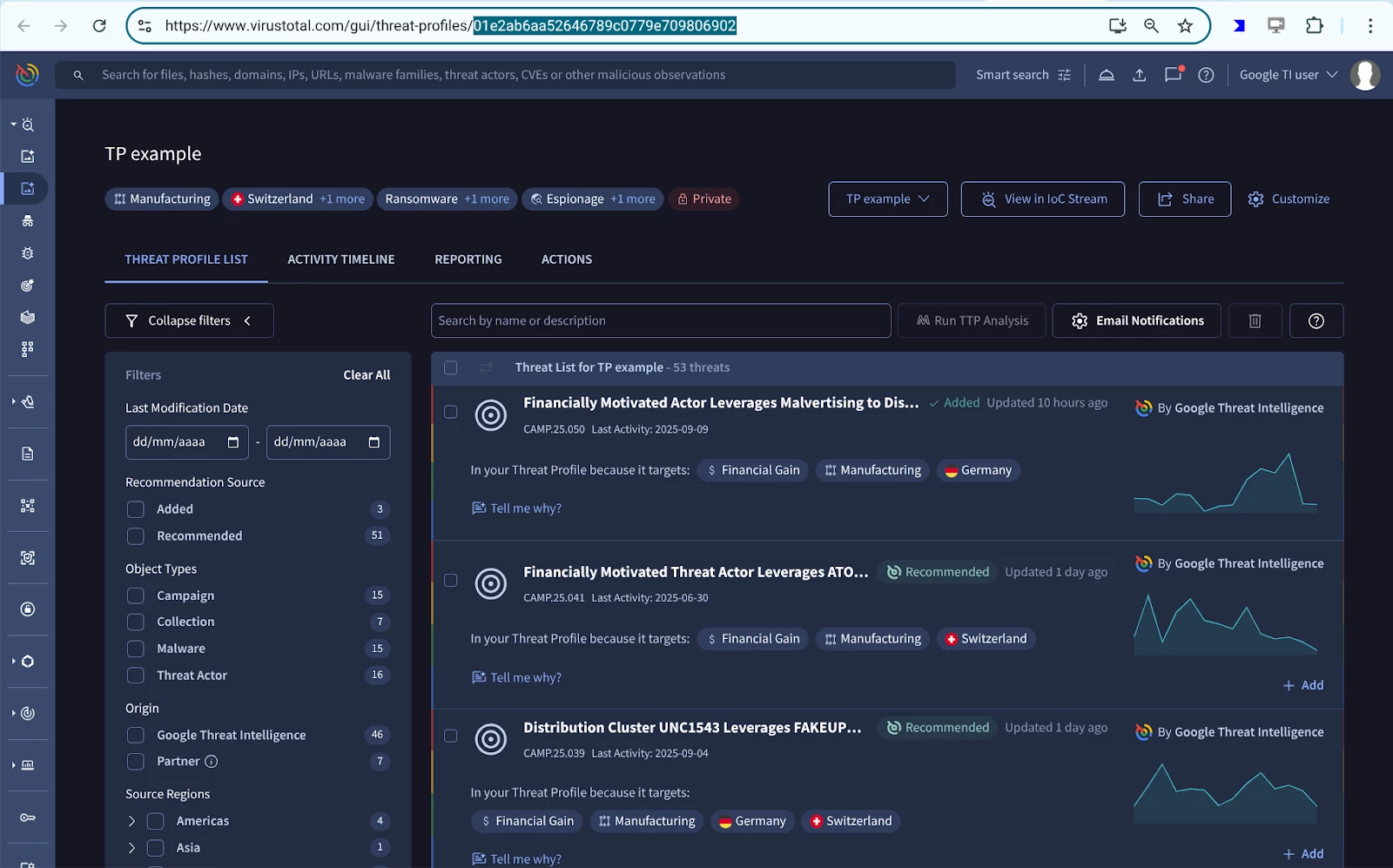
Some examples are:
- Get 10 objects associated with your Threat Profile:
| import requests profile_id = "INCLUDE_YOUR_PROFILE_ID" url = f"https://www.virustotal.com/api/v3/threat_profiles/{profile_id}/recommendations?limit=10" headers = {"accept": "application/json","x-apikey": "INCLUDE_YOUR_APIKEY"} response = requests.get(url, headers=headers) print(response.text) |
- Get only automatically generated recommendations associated with your Threat Profile.
| import requests profile_id = "INCLUDE_YOUR_PROFILE_ID" filter = "recommendation_source:SOURCE_RECOMMENDATION" url = f"https://www.virustotal.com/api/v3/threat_profiles/{profile_id}/recommendations?filter={filter}" headers = {"accept": "application/json","x-apikey": "INCLUDE_YOUR_APIKEY"} response = requests.get(url, headers=headers) print(response.text) |
- Get only reports and vulnerabilities associated with your Threat Profile.
| import requests
profile_id = "INCLUDE_YOUR_PROFILE_ID"
filter = "collection_type:report OR collection_type:vulnerability"
url = f"https://www.virustotal.com/api/v3/threat_profiles/{profile_id}/recommendations?filter={filter}"
headers = {"accept": "application/json","x-apikey": "INCLUDE_YOUR_APIKEY"}
response = requests.get(url, headers=headers)
print(response.text) |
Conclusion
In summary, the Google Threat Intelligence Threat Profile is a powerful and essential module designed to bring clarity and focus to your cybersecurity strategy. It moves beyond the vast, generic threat landscape to deliver a manageable, tailored, and actionable intelligence experience.
The true strength of the Threat Profile lies in its ability to act as a personalized lens on top of your threat intelligence, allowing your organization to downselect from Google’s extensive threat data based on specific area of focus that matters most to you. This automatic tailoring is powered by our proprietary relevance algorithm on top of a powerhouse of high quality threat intelligences.
Threat Profiles are a dynamic workspace that can be enriched with your own institutional knowledge alongside our expertise. By combining automated recommendations with deep customization and actionable outputs, the Threat Profile empowers your organization to shift from a reactive to a proactive defense.


