Author: Robert Parker
Collaborator: Chris Ralph
Introduction
The Digital Threat Monitoring (DTM) Module in Google Threat Intelligence is a powerful tool for monitoring against your brand, domains, and IPs that may be targeted by threat actors within the dark net and other underground forums. Within this advanced capability we provide several templates for customers to use which makes it easy to start using the platform and seeing value quickly. In today’s guide, we will cover some additional use cases which can be achieved using DTM, and how they can be set up. Please note that the guidance in this document is applicable to customers who subscribe to either an Enterprise or Enterprise+ Google Threat Intelligence package, where custom monitors can be implemented.
VIP User Monitoring
When building a VIP monitor, start by creating a custom monitor, add a condition using the Person and Identity type, select the must equal operator and enter as many identifiers as you can for the individual(s) (e.g. name, email, etc). At this point use the test monitor function to check the volume (also referred to as density) and quality of alerts. If this provides the desired information, select create monitor and you are done.
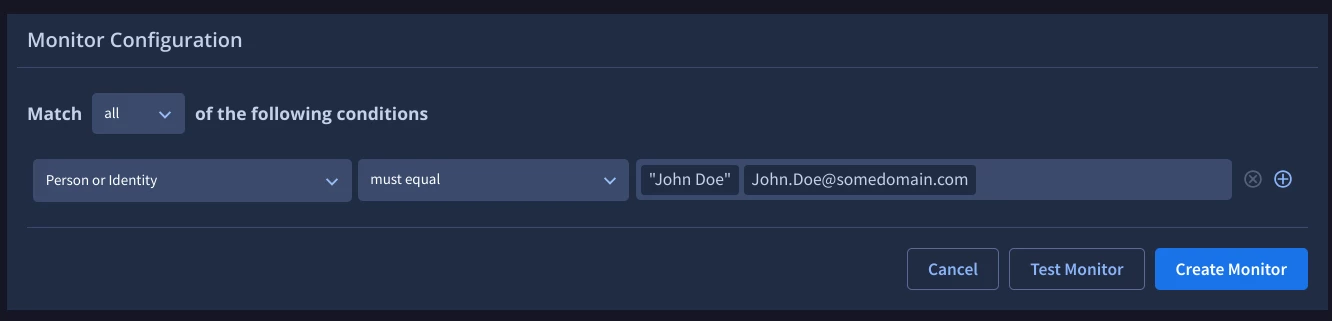
Now you have two options, narrow your search focus to target specific sources or add a condition that links the name to your organization or some other unique characteristic.
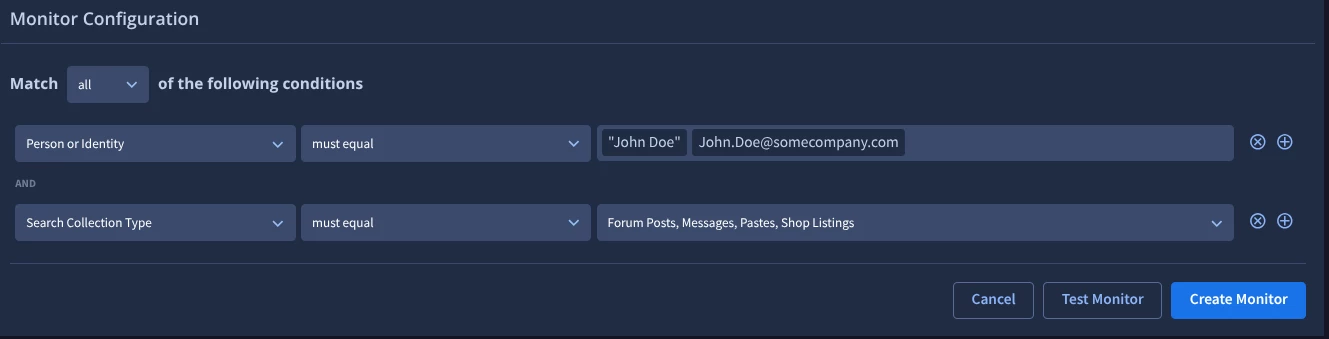
To focus your search on a specific source(s) add a second condition, select Search Collection Type, and choose the sources you want to target. In this example, we suggest starting with Forum Posts, Messages, Pastes, and Shop Listings for now. Test the monitor and review the results for volume and quantity, if this fulfills your requirements, then select create monitor.
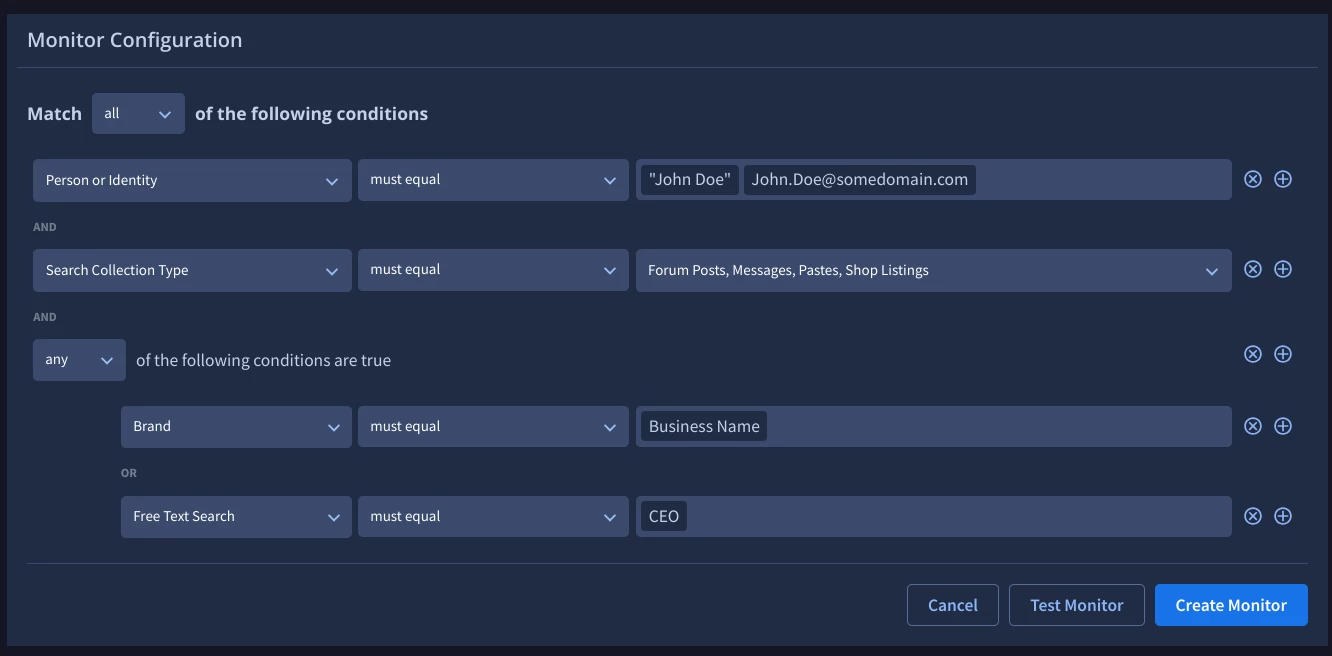
If you wish to further refine your search add a third condition, typically Brand, and enter in your organization name(s). This combination will require the VIP’s name and the organization to both be present in the document.
A second strategy here is to use the VIP’s title(s) (e.g. CEO, CIO, VP, etc). Test the monitor and review the results.
If you continue to get an inordinate amount of noise and low quality alerts associated with one or more of the names, the final option is to build a Lucene text query that leverages a proximity filter. The first thing you must do is build a list of “problem terms”, which are words that answer the question:
If John Doe's name shows up on the internet, it is a problem when (fill in the blank).
Terms like compromise, phishing, target, etc are all good choices, but the terms should be built around a specific intelligence requirement.
Add a new condition, select Lucene Text Query. Build your proximity filter by placing the VIP’s first or last name in quotations and one of your problem terms (e.g. “hacked doe”~5 OR “compromise doe”~5 OR “doe phishing doe”~5 etc). In each case the monitor will only alert if the VIP’s last name and the problem term is within the number of words defined in the filter; in this case it is 5 words. The number of words is user defined.
We advise to not use more than two words in the individual queries; if you add the VIP’s full name “John Doe hacked”~5 the search becomes: John and Doe within 5; or John and hacked within 5; or Doe and hacked within 5.
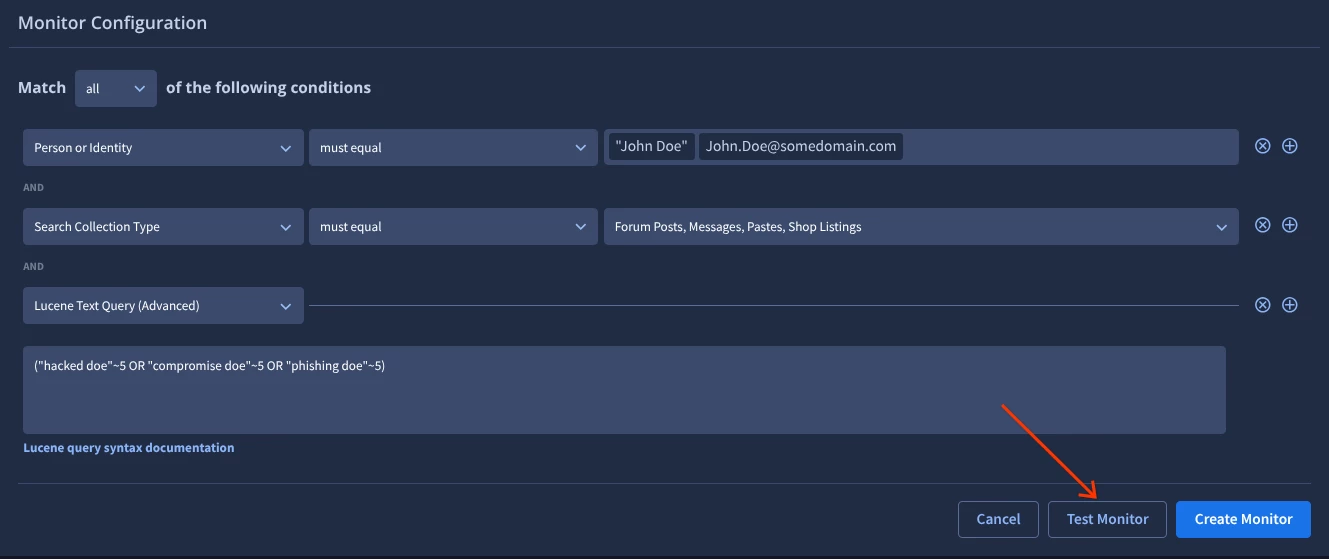
("hacked doe"~5 OR "compromise doe"~5 OR "phishing doe"~5)
Test the monitor and add problem terms as needed to address your requirements.
The flexibility within custom monitors allows for many different ways to set up VIP User monitoring, but we hope that this example here will help you narrow your results and remove noise from the results.
VirusTotal Document Searching Tuning
The Data Leaks template is a powerful monitor to use for when you want to detect exposure of your sensitive information such as financial data, trade secrets, or customer information. However there are times where this template may generate more noise than desired, and a custom monitor could be used to narrow the search results.
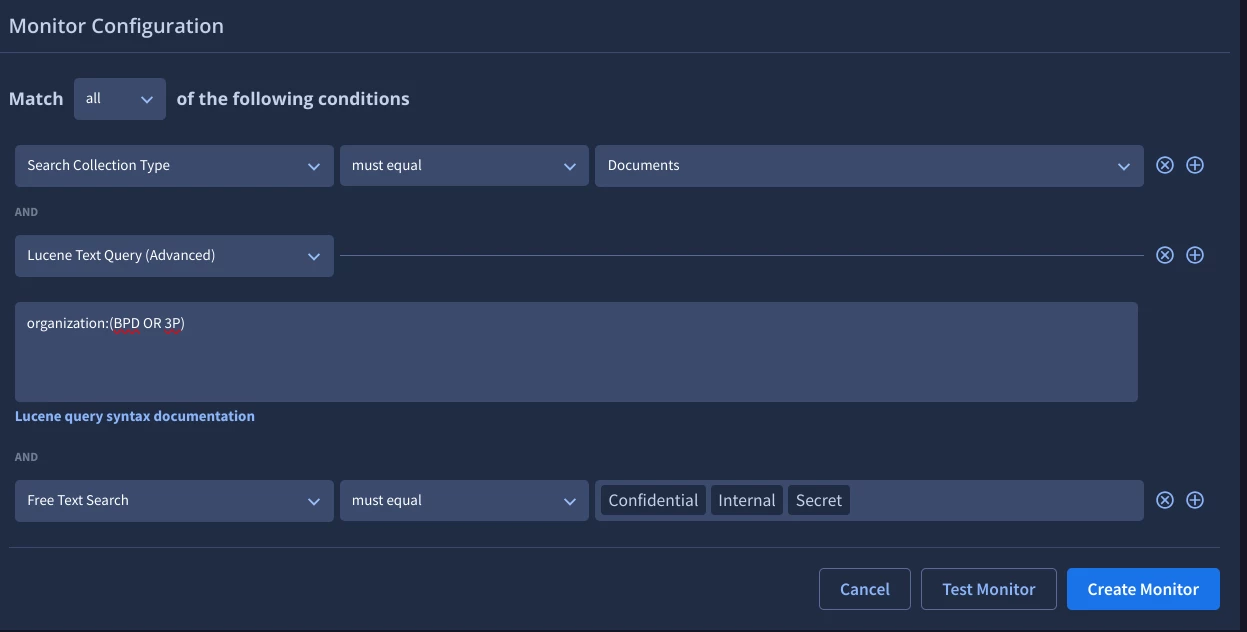
In the below example, you can use a custom monitor with Lucene Text Queries and Free Text Search to find instances of internal documentation being publicly uploaded to VirusTotal. Oftentimes, we see instances of organizations where their name is either an Acromyn, (such as BPD) or a very short string of characters (such as 3P) may generate a lot of false positives.
By using Lucene Text Queries, we can specify that we are looking for organization:<NAME> and in combination with Free Text Search of using specific terms that would generally accompany internal sensitive document labels, this can help to reduce noise in the alerts.
Monitoring Mentions of Cryptocurrency Wallets Addresses
Using a custom monitor, you are able to set up a monitor for mentioning a specific cryptocurrency wallet. This does not monitor for any traffic or transactions to that wallet, just the mentioning of the wallet address.
To set this up, select the Search collection type to the appropriate areas as shown in the below screenshot, and set the topic to be ‘Crypto’
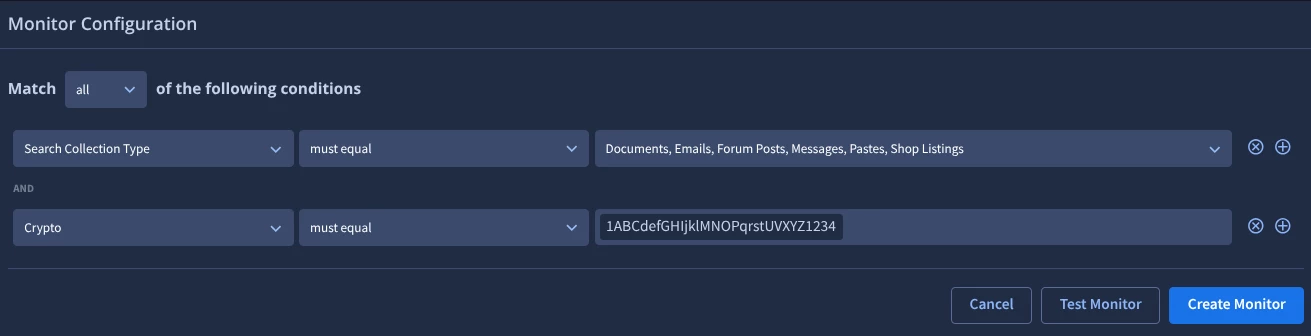
The ‘Crypto’ Topic will search for the following wallet addresses of cryptocurrency:
Atom, BCH, Bitcoin, Dash, Doge, Litecoin, Stellar, Monero, and Zcash, as outlined in this page from our documentation: https://gtidocs.virustotal.com/docs/monitor-fields
Advanced Lucene Text Queries
This section provides a use-case driven guide to building Digital Threat Monitoring Research Tools searches. These searches can then be turned into custom monitors using the Lucene Text Queries search operators.
Identifying and Investigating Credit Card Shop Listings
This use case demonstrates how Mandiant Digital Threat Monitoring (DTM) searches can be employed to detect and analyze illicit credit card shop listings across various online platforms. By targeting specific attributes of credit card listings, such as card type, brand, issuer, product, and shop name, investigators can efficiently pinpoint relevant listings and gather evidence for further analysis.
Key Objectives
- Identify credit card shop listings: The primary goal is to locate listings offering stolen or compromised credit card information for sale.
- Filter listings by specific criteria: Searches can be refined to focus on particular card brands (e.g., Mastercard, Visa), issuers, products (e.g., Gold), or even specific shops.
- Investigate suspicious listings: By identifying relevant listings, investigators can gather intelligence about the sellers, card details, pricing, and other relevant information.
- Support fraud investigations: Data collected from these searches can aid in identifying compromised accounts, tracing fraudulent transactions, and potentially apprehending the perpetrators.
Card Data Tracking
I want to search for shop listings of credit cards
type:"shop_listing"
AND item_type:"CC"
I want to filter the results by brand such as mastercard or visa
__type:"shop_listing"
AND item_type:"CC"
AND (payment_card.brand:"mc" OR payment_card.brand:"visa")
I only want a specific issuer
__type:"shop_listing"
AND item_type:"CC"
AND (payment_card.brand:"mc" OR payment_card.brand:"visa")
AND payment_card.issuer:"ISSUER_NAME*"
I only want a specific product
__type:"shop_listing"
AND item_type:"CC"
AND (payment_card.brand:"mc" OR payment_card.brand:"visa")
AND payment_card.issuer:"ISSUER_NAME*"
AND payment_card.product:"GOLD"
I only want a specific shop
__type:"shop_listing"
AND item_type:"CC"
AND (payment_card.brand:"mc" OR payment_card.brand:"visa")
AND payment_card.issuer:"ISSUER_NAME*"
AND payment_card.product:"GOLD"
AND shop.name:"ACME CARD SHOP"
Alternatively or in combination, search by bin codes.
__type:"shop_listing"
AND item_type:"CC"
AND payment_card.partial_number_prefix:("555555" OR "123456")
NOTE: payment_card.partial_number_prefix does not accept wildcards and is a literal search option.
Customer names are not typically identified using this search methodology but can sometimes be found within forum posts so consider also searching for these using the known bin codes identified above or through customer supplied details noting that these can be very verbose,.
__type":"forum_post" and body:("BIN1" OR "BIN2" OR "BIN3")
Threat Actor Message Tracking
I saw a threat actor named Freebandz in the telegram channel SaneMarket. I want to check if they were previously using a different handle, so I need to grab their user_id first. I can perform a search based on this information and look for their user_id in the JSON structure of a message they sent.
__type:message
AND messenger.name:telegram
AND sender.identity.name:"SampleName"
AND channel.name:"1337Market"
Now I know their user_id is “6273******” (This can be found in the field of sender.telegram.user_id from RAW_JSON view of message) so I can look for all messages they sent on telegram channels.
__type:message
AND messenger.name:telegram
AND sender.telegram.user_id:6273******
When an telegram user_id or a channel_id: contains a hyphen at the beginning of the value, the hyphen will need to be “escaped” as demonstrated below:
sender.telegram.user_id:\\-123456789
channel.channel_id:\\-987654321
OS Specific Shop Listings
I want to search for host_access shop listings published this month for Microsoft Server 2019
__type:shop_listing
AND item_type:host_access
AND host_access.host_info.operating_system:"Windows 2019"
Active Accounts from a specified shop
I want to search for listings from the 1337Hack Market shop that contain the description Active accounts.
shop.name:"1337Hack Market"
AND description:"Active accounts"
Country and shop specific credit card listings
I want to search for japanese credit cards from the Robot market shop. The credit cards should have a price starting from 10 USD.
item_type:CC
AND shop.name:"Robot market"
AND price:[10 TO *]
AND (payment_card.owner.contact.geo_location.country_code:"JP"
OR payment_card.owner.contact.geo_location.country:"japan")
Forum messages initial access broker offers
I want to fetch forum posts from the Ramp forum, in the thread Access for sale.
__type:forum_post
AND forum.name:hackzorzExample.onion
AND subject:"Access for sale"
Forum specific subject query across multiple boards
I want to fetch forum posts sent by Robotmarket in the Robot.co forum. I don't know the full path to the board, but it contains the text Marketplace. I want posts only from the Robot Shop thread
__type:forum_post
AND author.identity.name:"Robotmarket"
AND forum.name:Robot.co
AND board:*arketplace*
AND subject.raw:"Robot Shop"
Domain specific email search
I want to look for emails that contain Microsoft as a header value sent to a specific domain. The email should have a filename property, the content type should be text/plain or text/html.
__type:email_analysis
AND email.headers.value:"Microsoft Outlook 16.0"
AND email.headers.value:"@os-kh.de"
AND (email.body_multipart.content_type:"text/plain"
OR email.body_multipart.content_type:"text/html")
Conclusion
DTM is a very powerful tool for searching the surface and dark web, which allows organizations to stay ahead of digital risks. While DTM provides robust templates to help ease the configuration of the monitors, using custom monitors and in combination with Lucene Text Query capabilities also enables customers to do even more powerful searches, to look for very specific needles in a very large haystack known as the internet. We hope this adoption guide provides you with some additional examples of how powerful the tool can be, and how to narrow down specific searches to help ensure the alerts returned are both relevant, and actionable by your threat intelligence teams.
Dont forget to utilize our Google Cloud Customer Community to post questions if you ever need help with a specific use case, or want to see what kind of monitors other customers are coming up with.
