Author: Raimundo Alcazar
Co-Author: Alexandra Martin
Introduction
This guide is designed to empower you with the knowledge and practical steps necessary to fully adopt threat hunting activities in Google Threat Intelligence using advanced searches. Our goal is to ensure you understand the concepts and can confidently implement them within the product.
By following the detailed directions and best practices outlined here, you'll maximize your efficiency and achieve optimal results.
Google Threat Intelligence allows you to search through the dataset in order to identify Indicators of Compromise (IoCs) of several types (files, URLs, domains and IPs) that match certain criteria. For these search queries, we use entities and modifiers.
Entities are the objects we search for (file, url, domain or ip), and each of them can be combined with specific modifiers that help the user to search in a more precise manner. That is why Google Threat Intelligence is known as the Google of Malware.
This guide is designed to be a comprehensive resource for Cyber Threat Intelligence (CTI) and other cybersecurity analysts. It balances conceptual understanding with practical examples and instructions.
Conceptual Overview
To understand Threat Hunting within the context of Google Threat Intelligence’s advanced searches, it's crucial to first recognize that modern cybersecurity demands a shift from reactive to proactive defense. This is where threat hunting comes into play. It's a deliberate, iterative process where skilled analysts actively search for malicious activity, utilizing their expertise and intuition to uncover hidden threats that have evaded automated security systems.
Google Threat Intelligence significantly enhances the effectiveness of threat hunting by providing a centralized repository for diverse cyber threat data. Essentially, the advanced searches allow threat hunters to search using different criteria and anticipate potential attack vectors.
Exact detection vs Pattern detection approach
Modern cybersecurity strategies recognize the importance of both approaches. Exact detection provides a rapid response to known threats, while pattern detection allows for the identification of potentially unknown attacks.
Pattern detection takes a broader, more analytical approach. Instead of focusing on exact matches, it seeks to identify anomalies, variations or deviations through methods such as:
- Behavioral patterns, where the actions of files, processes, network connections and more are scrutinized for unusual activity, such as different ways of attempts to delete shadow copy, files dropping another file that executes an obfuscated payload, creating a specific service or mutex, connections to TOR nodes, etc.
- Metadata patterns for examining basic file characteristics (names, size, version, timestamp, type,… ), data coming from Exiftool, and internal structure of files to uncover malicious traits.
However, pattern detection also presents challenges, such as a higher rate of false positives and the need for more sophisticated analytical tools and expertise.
A robust security posture requires a balanced approach, leveraging both the precision of IoC exact matching and the analytical depth of pattern recognition.
Directions
-
Learning the basics about searches
One of the basics for searching through our dataset is using the “entity” search keyword to directly specify the type of output you want to get. Each entity works in combination with specific modifiers:
- File search modifiers
- URL search modifiers
- IP addresses search modifiers
- Domain search modifiers
- Collection search modifiers
Search modifiers can be combined via Boolean operators (AND, OR, NOT, or none of them which is equivalent to AND ) as well as parentheses, for more complex searches.
Please note that by default, if you don't add the entity at the beginning of the query, you'll only get results related to files.
1.1. Exact detection
Let’s see how to lookup for a file, URL, domain or IP address analysis report by placing the entity identifier on the search bar.
In this example we are checking a file report by its MD5 hash value
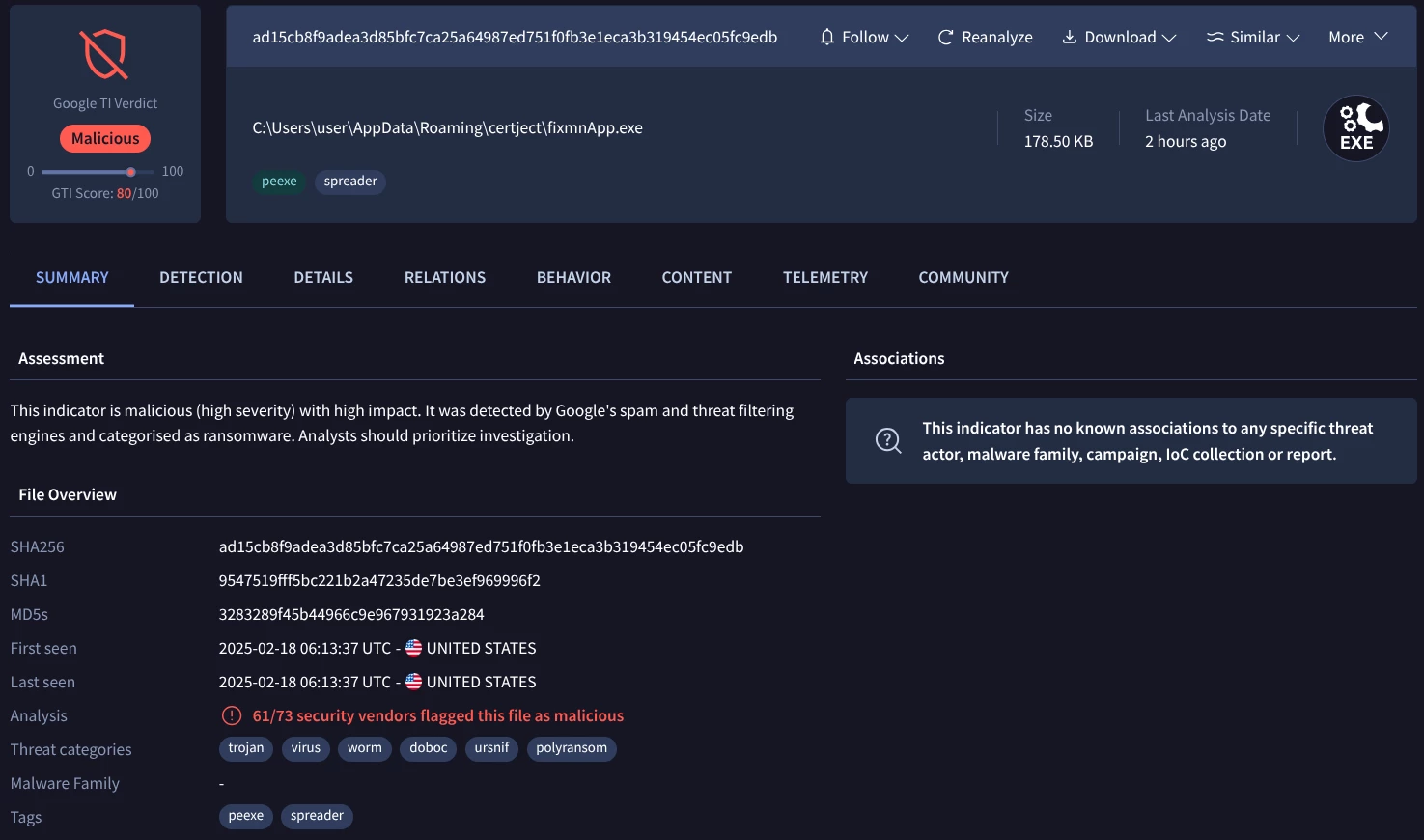
Figure 1: Report associated with this md5 hash file
1.2. Pattern detection - Content search and similarities
To search for ascii / hexadecimal files patterns you can use the content modifier. In these examples we are searching for patterns seen on Lumma stealer samples:
- content:{c70000000000 85c9 7406 c70100000000 c7466cfefffff}
- content:"rundll32.exe shell32.dll,Control_RunDLL MMSys.cpl"
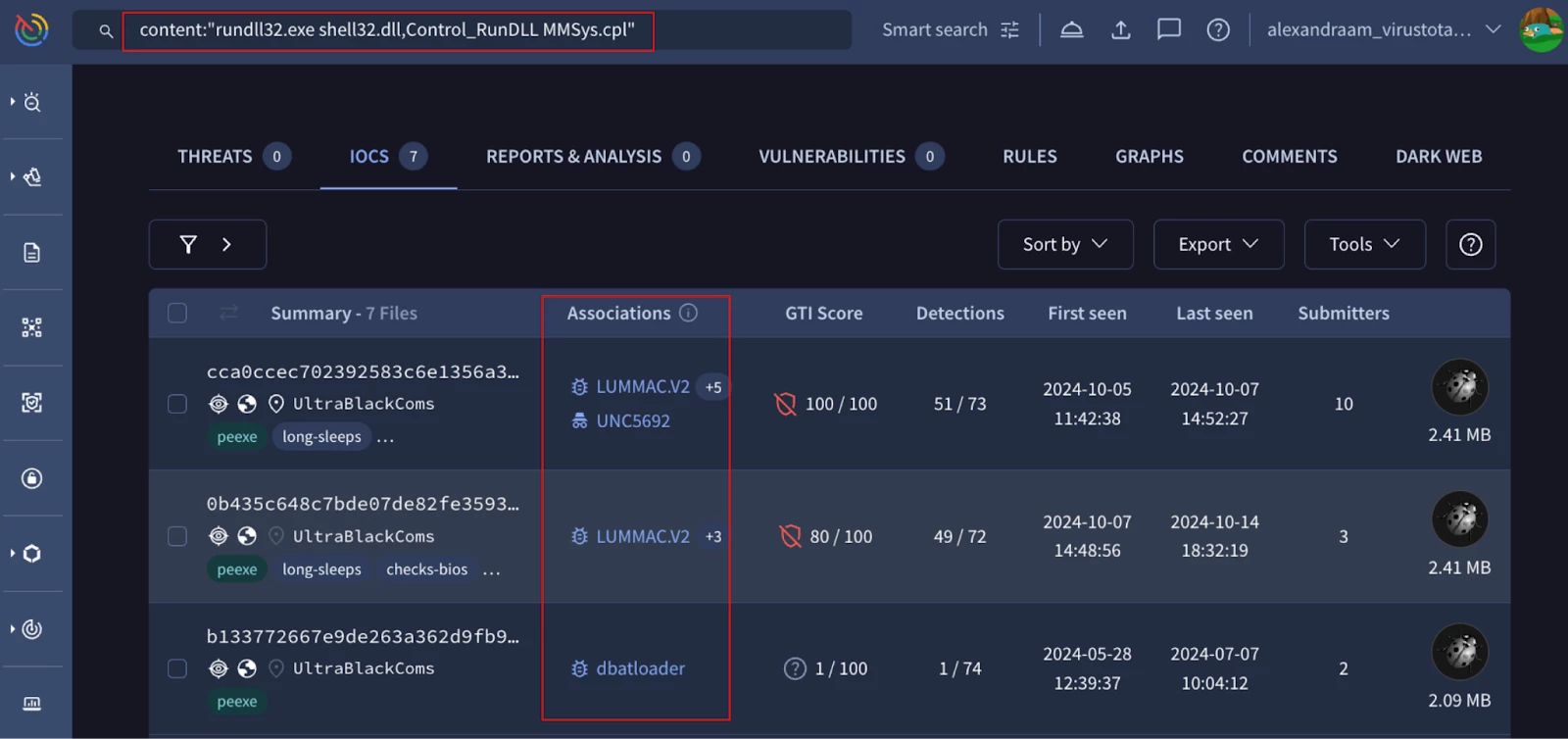
Figure 2: ASCII Content search results
It is also possible to search by some modifiers to pivot to other similar files (Vhash, Authentihash, SSDEEP, Imphash, … etc)
1.3. Pattern searches by entity
Let’s see some basic search examples for each entity type: files, URLs domains and IP addresses.
Cryptocurrency related IPs based on Google Cloud Platform abuse service verdict.
Search for potentially malicious domains with ".xyz" tld and “Let's Encrypt SSL” certificates.
Find URLs categorized as phishing that have "account/login.php" in the path.
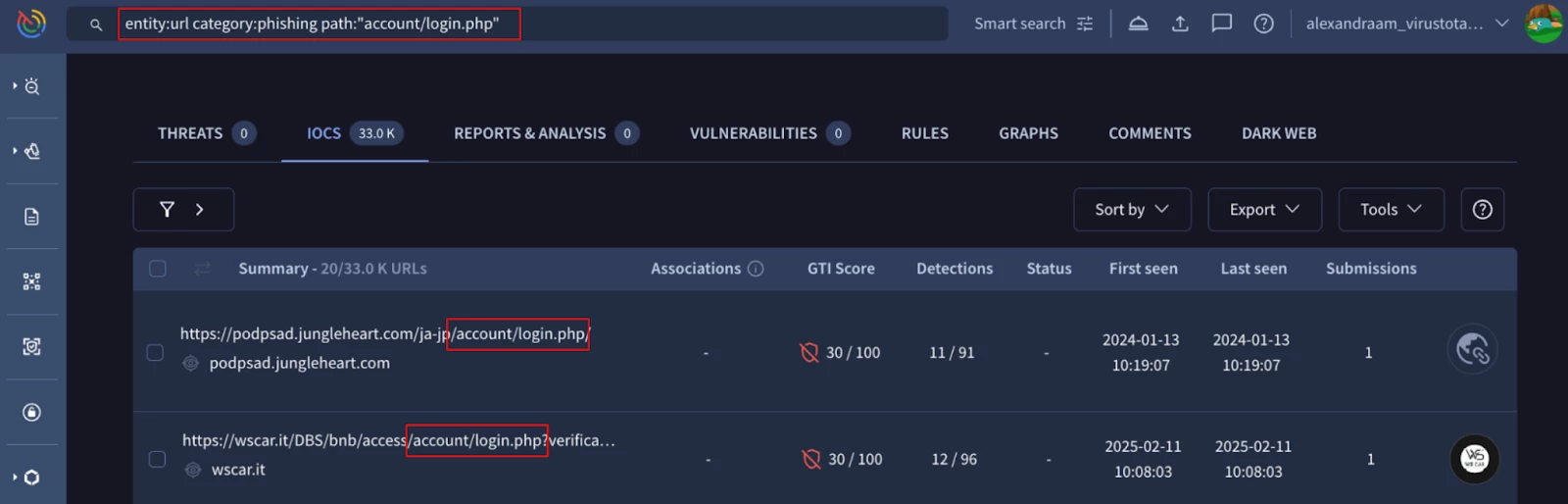
Figure 3: Phishing URLs with ”account/login.php” path results
Find files that antivirus engines classify as keyloggers and that are 100 KB or smaller in size.
Obtain Collections that have "Kimsuky" in their names or have been tagged with “Kimsuky” label.
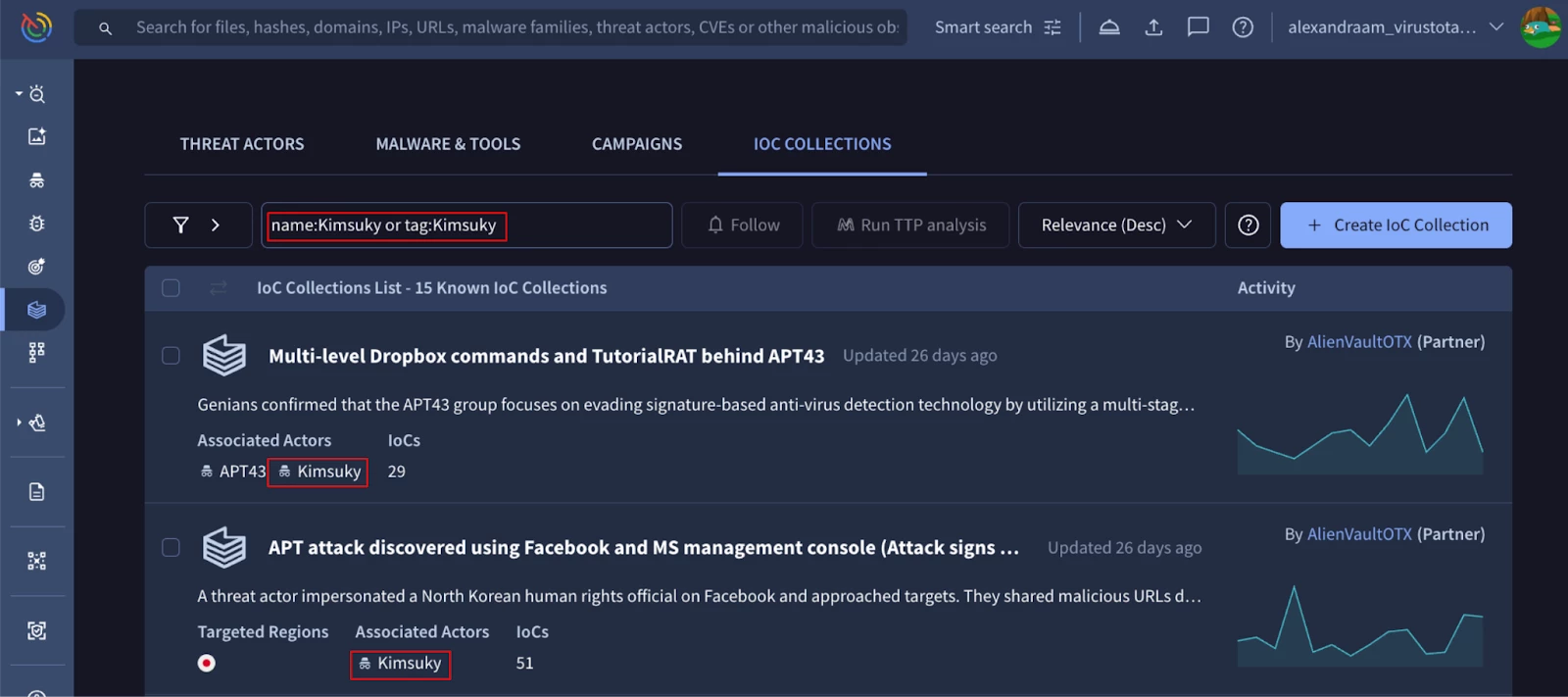
Figure 4: IOC collections with Kimsuky in name or tags
2. Combining modifiers for refining your searches
In this section we will combine different modifiers to create new advanced searches, grouped in different use cases according to their usefulness.
2.1. Documents and emails related searches
Documents or emails mentioning your brand used as the first stage in the Cyber kill chain.
This search identifies emails or documents containing "Acme corp" in their filename or metadata that have either displayed network activity or have been downloaded from a URL.
Find malicious ".docx" attachments that contain the word "invoice" in the filename, have more than 5 AV detections, and were first seen within the past two weeks.
You can narrow these results to detect those malicious attachments submitted massively and not detected by your corporate antivirus (for example, bitdefender) adding these modifiers options at the end as follows:
Find ".xlsx" files that were first detected in 2025 and have a Google Threat Intelligence score above 60. The files should exhibit suspicious behavior, such as executing a file or using PowerShell.
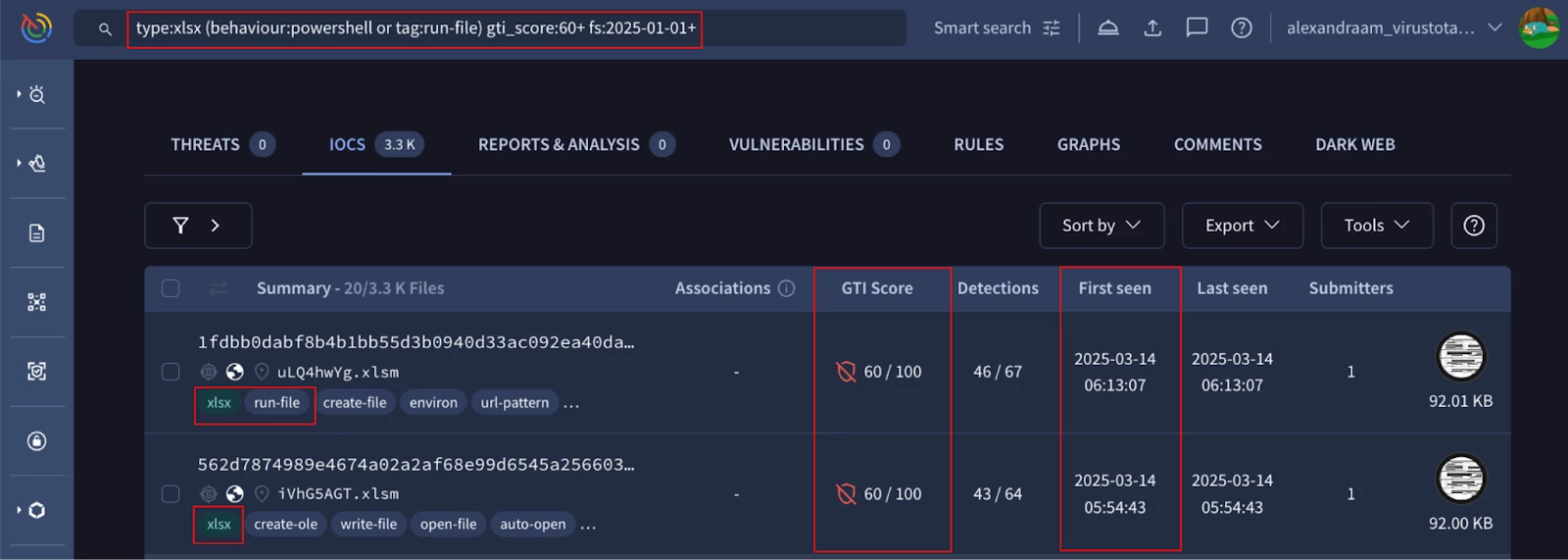
Figure 5: xlsx files with suspicious behaviours first seen in 2025 and gti_score greater than 60
2.2. Windows executables related searches
Hunt for Windows executable files that connect to port 445 and use an exploit.
Get new Windows executable files that were uploaded from Germany between January 1st 2025 and today, and categorized as ransomware by antivirus engines.
Find samples exploiting a recent 2025 vulnerability barely detected by antiviruses.
Note the use of the asterisk to include all the tags starting with “cve-2025” substring and also how this search it’s narrowed down setting thresholds for the number of positives.
Identify malicious files that are detected as "vidar" malware by AV engines and that, when executed, create processes that attempt to enable remote debugging on port 9223.
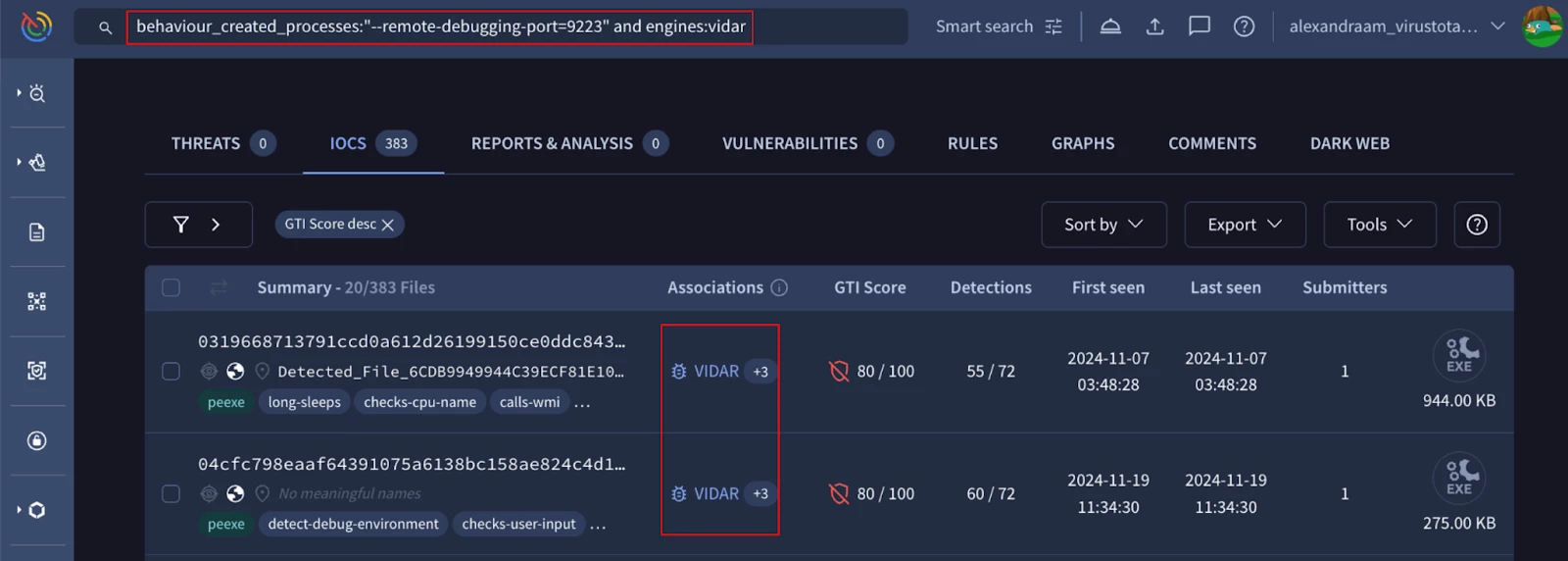
Figure 6: Files creating a specific process and detected by AV engines as vidar
Identify files that exhibit a specific JA4 fingerprint.
Track malware using the malware configuration extractor.
This search detects malware based on AVs engines snake_keylogger verdict and belonging to Campaign id: 7618581100 that was extracted from the malware configuration.
You can search by other different fields coming from the malware_config modifier as shown on this image:
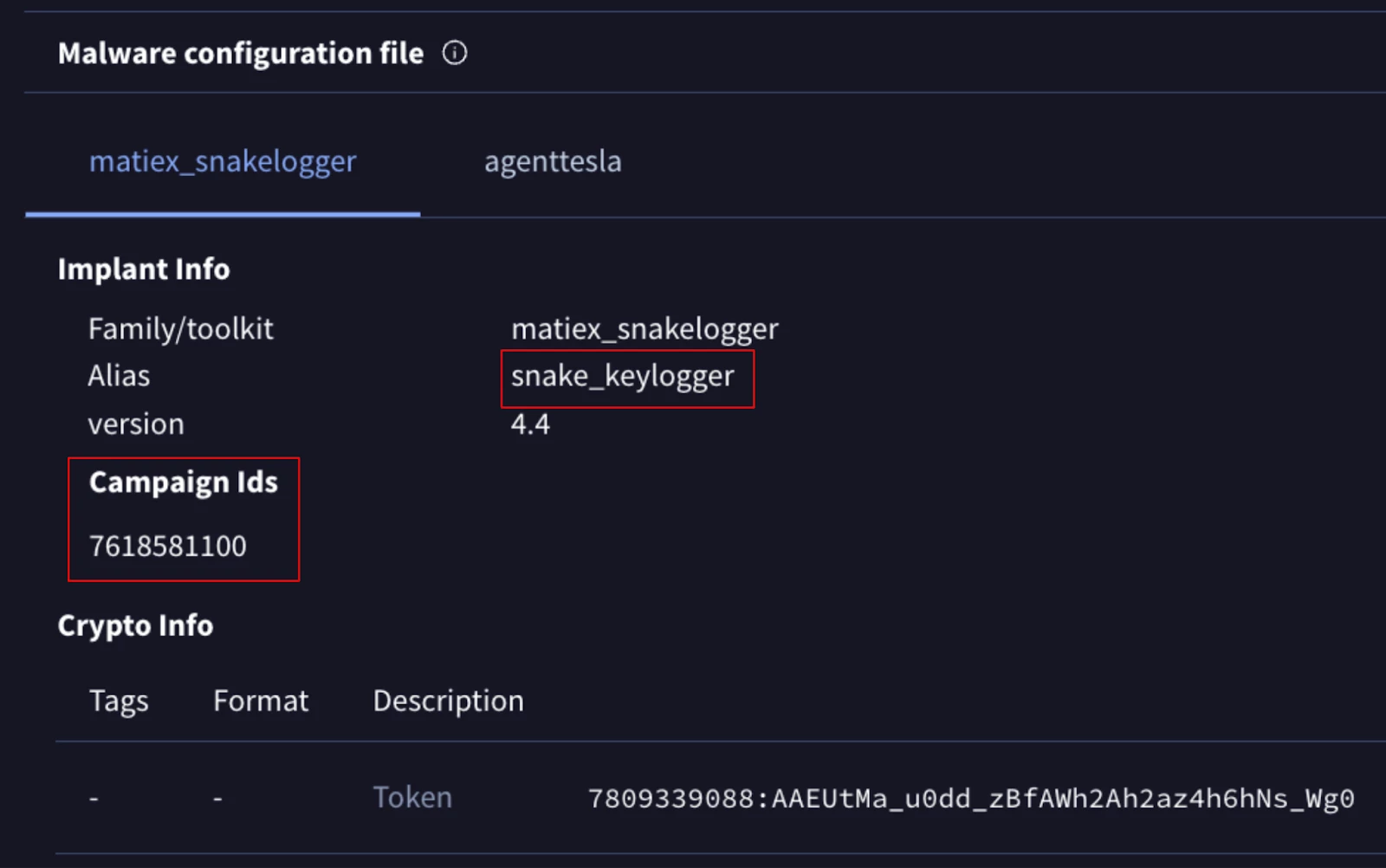
Figure 7: snake_keylogger files belonging to a specific campaign
Hunt for files served in the wild related to a specific domain.
Hunt for malware exploiting the CVE-2025-21298 vulnerability firstly submitted to Google TI in the last month.
2.3. Other files types related searches
This section is focusing specifically on other operating systems binaries and files, such as Linux, Mac OS X and Android.
Uncover files that create or modify shell scripts (".sh" files) within the "/etc/profile.d/" directory on Linux systems.
This directory is often used to host scripts that are automatically executed during user login, making it a common target for malware seeking persistence or automatic execution.
Detects DMG or MAC files with activity in the bash_sessions folder and matches a specific Sigma rule that detects AppleScript execution.
Search for “.apk” files with specific package name and permissions.
Search for “.apk” files containing a specific resource file path and using an icon matching a specific “dhash” value.
2.4. Network indicators related searches
This section is focused on exploring some different cases and examples that are related to IP addresses, URLs and domains.
Identify your legitimate IP addresses (i.e: from range 191.158.128.0/20) contacted or referred by potential malware.
- entity:ip ip:"191.158.128.0/20" (detected_communicating_files_count:1+ or detected_referring_files_count:1+)
- “detected_communicating_files_count” modifier refers to the number of files that contact an IP address within the specified range during their sandbox detonation and have at least one AV detection.
- “detected_referring_files_count” modifier refers to the number of files that contain an IP address within the specified range and have at least one AV detection.
Instead of the “ip” modifier you can use the “asn” modifier to search for all IP addresses belonging to a specific Autonomous System number (ASN).
Identify URLs with the .ru top-level domain that could be used to distribute Android APK files:
- entity:url url:android tag:downloads-apk tld:ru
Find undetected URLs (according to Google TI verdict) using a specific tracker identifier:
- entity:url tracker:G-KVN8M54JBZ gti_verdict:undetected
Detect URLs related to specified parent domain/subdomain with a specific header in the response:
- entity:url header_value:"SimpleHTTPServer" parent_domain:domain.org
2.5. Tracking APTs activity related searches
This section is oriented to follow APTs activity through advanced searches.
Search for IoC Collections based on name terms and owner.
Search for Reports based on description keywords.
You can narrow down the search to receive the last month reports using the “lm” modifier as follows:
Search for “.pedll” files with gti_score higher than 30 and belonging to a specific IoC collection and filter the entities and other required modifiers:
You can get the IoC collection ID from the browser address bar when navigating a specific collection.
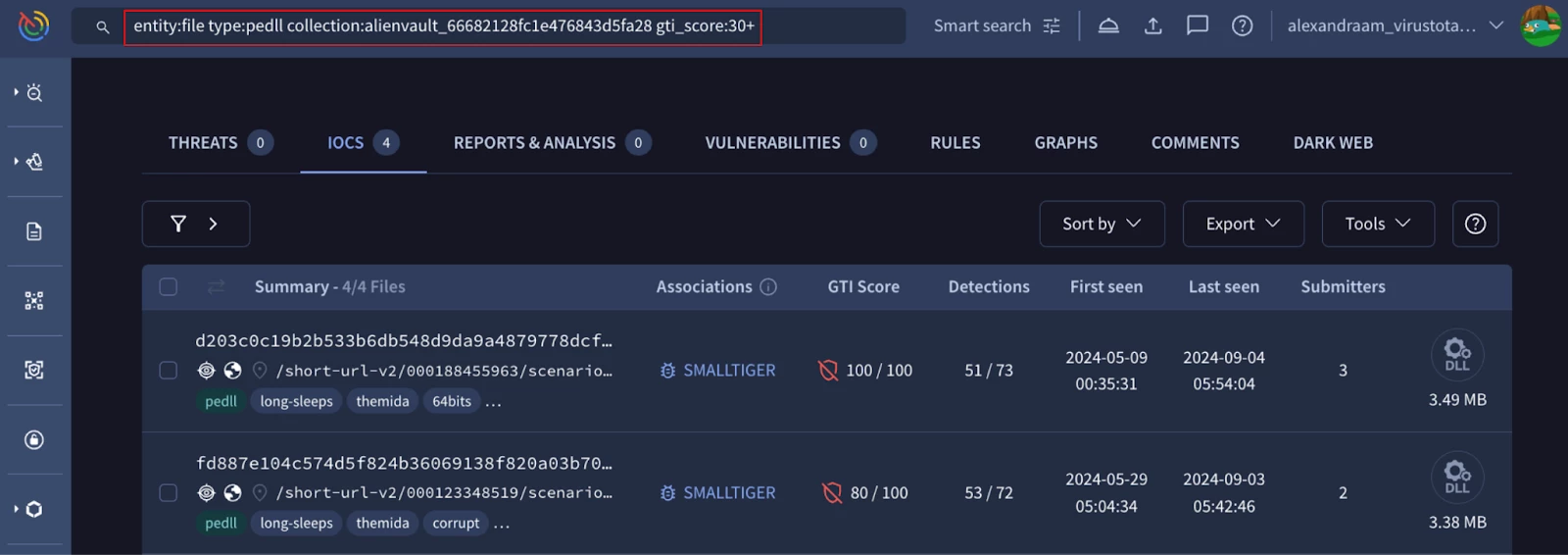
Figure 8: Filter files belonging to a specific collection
Get files related to a specific threat actor based on matches against crowdsourced rules detecting threat actor activity.
In this case we are searching for files matching Yara or IDS rules under the mentioned criteria.
Another way of searching for files potentially related to the same APT42 threat actor is by checking the community comments.
2.6. AI related searches - Code Insight
Code Insight is a feature that uses AI to analyze and interpret code snippets. It can read plain text code and generate human-readable summaries, allowing security professionals to quickly understand the code's functionality. This helps them find and fix security problems faster. For more information about file types supported by Codeinsight, please check this documentation.
Search for Powershell or bat files identified as keyloggers by CodeInsights.
The search identified a file that included an AI-generated description containing the word "keylogger."
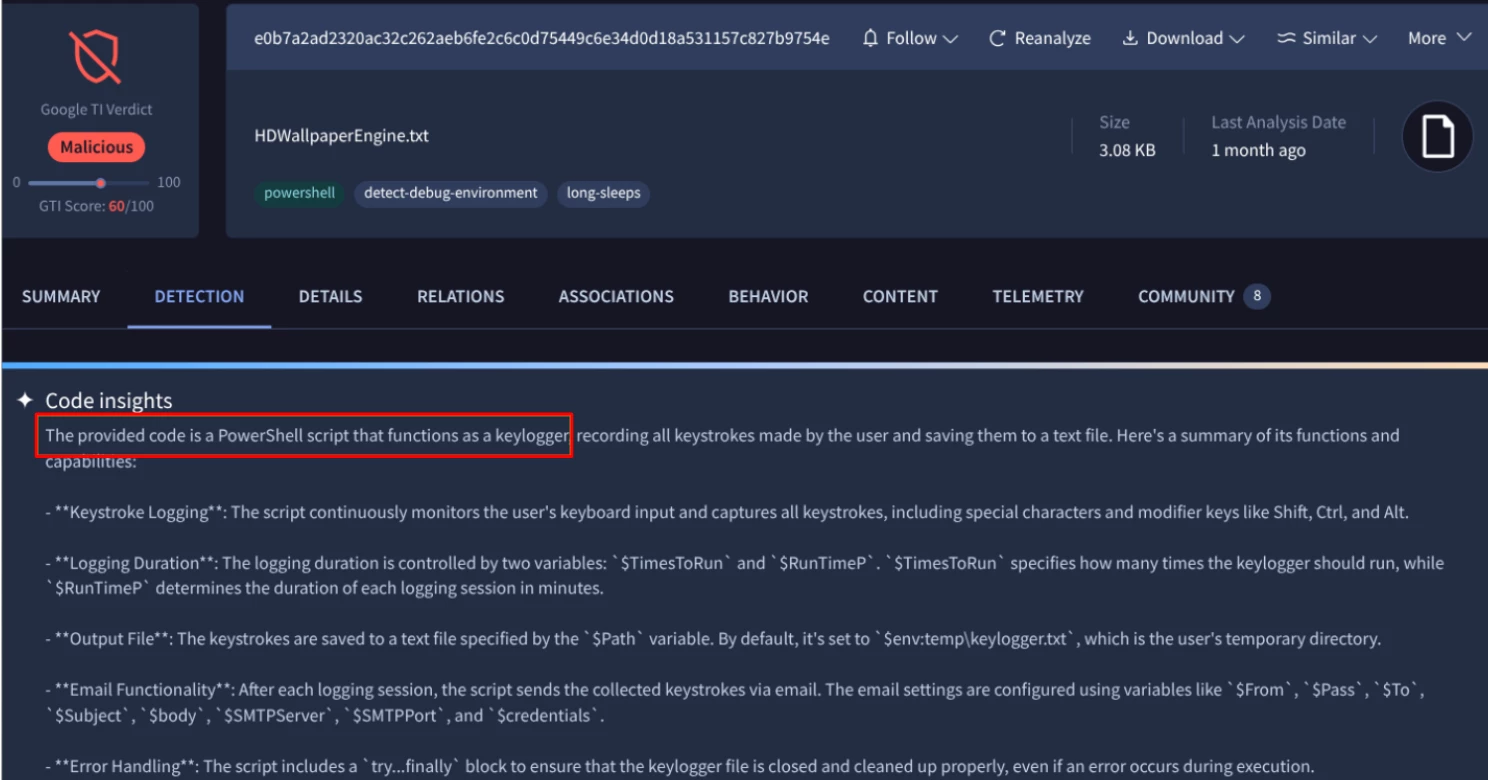
Figure 9: Powershell file that exhibits keylogger behaviour
Search for files identified as malicious by Code Insights with undetected Google TI verdict.
This search aims to find files flagged as malicious by Code Insight but not currently by Google TI.
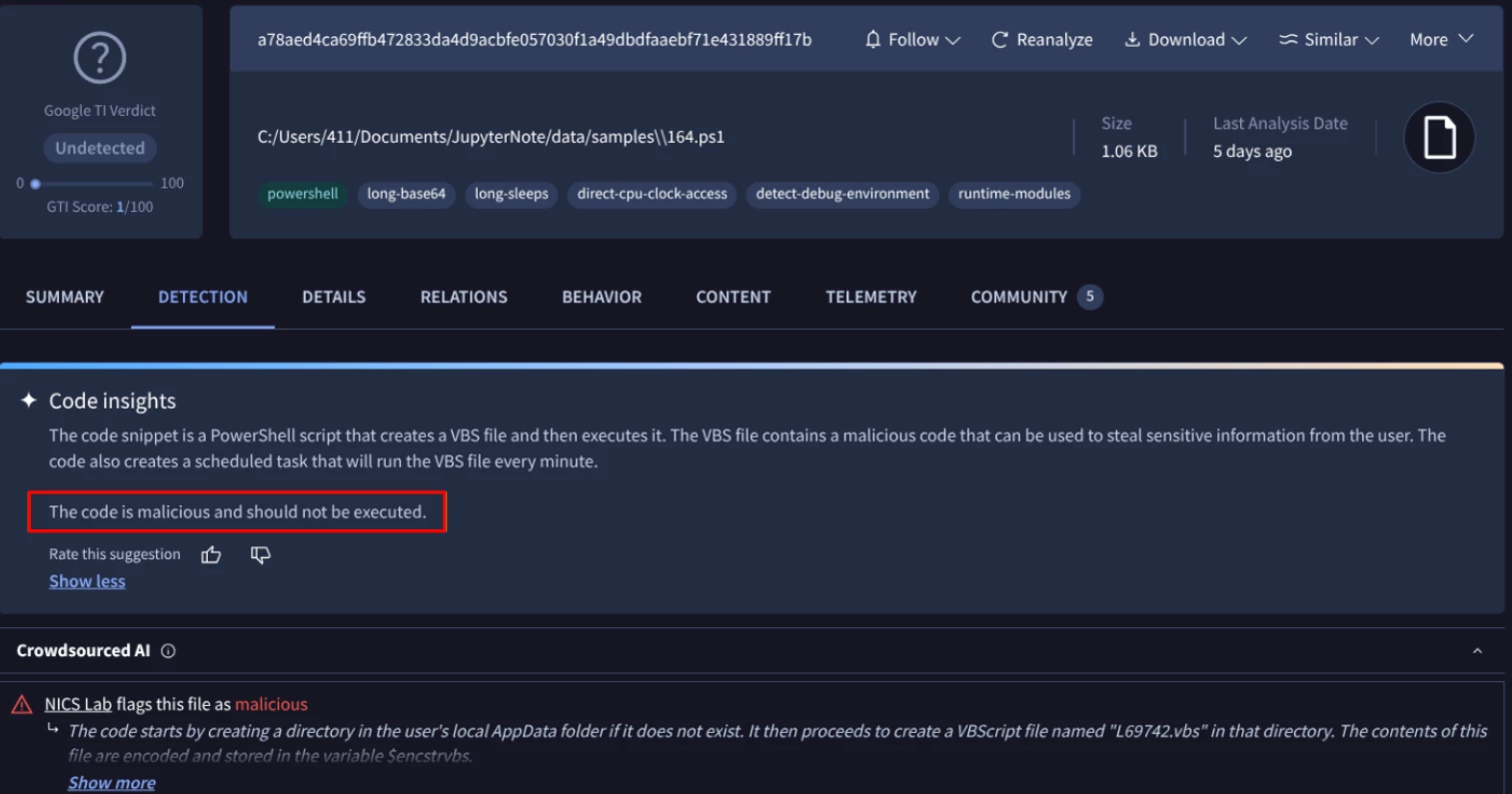
Figure 10: Malicious verdict from Code Insights but undetected at the moment
Final conclusions
Google Threat Intelligence is an actionable intelligence hub which allows users not only to gather individual items data but it provides very powerful search mechanisms to identify entities of their interest through a large list of search modifiers for each entity type.
This allows users to implement different tracking use cases and hunt for new campaigns and malicious activity, making Google Threat Intelligence much more than a powerful resource for threat analysis.For a more in-depth guide on using the entities and modifiers related to advanced searches, please see our documentation.
