Author: Raimundo Alcazar
This guide details how practitioners can leverage Google Threat Intelligence to gain insights into phishing campaigns targeting their organization and to investigate broader phishing trends.
Phishing attacks against organizations are becoming increasingly sophisticated, exploiting both technical vulnerabilities and human psychology. Here are two common examples of phishing techniques, along with how Google Threat Intelligence (Google TI) can help identify them:
- Typosquatting: Attackers register domain names that closely resemble legitimate ones, but with slight misspellings or variations (e.g., "offlice365[.]com" instead of "office365[.]com")".
In the following image, we can see how Google Threat Intelligence identifies the offlice365[.]com domain as malicious, and with a more attentive look, we can distinguish an extra “l” letter in the domain name. Additional detailed information can be found across the different report tabs.
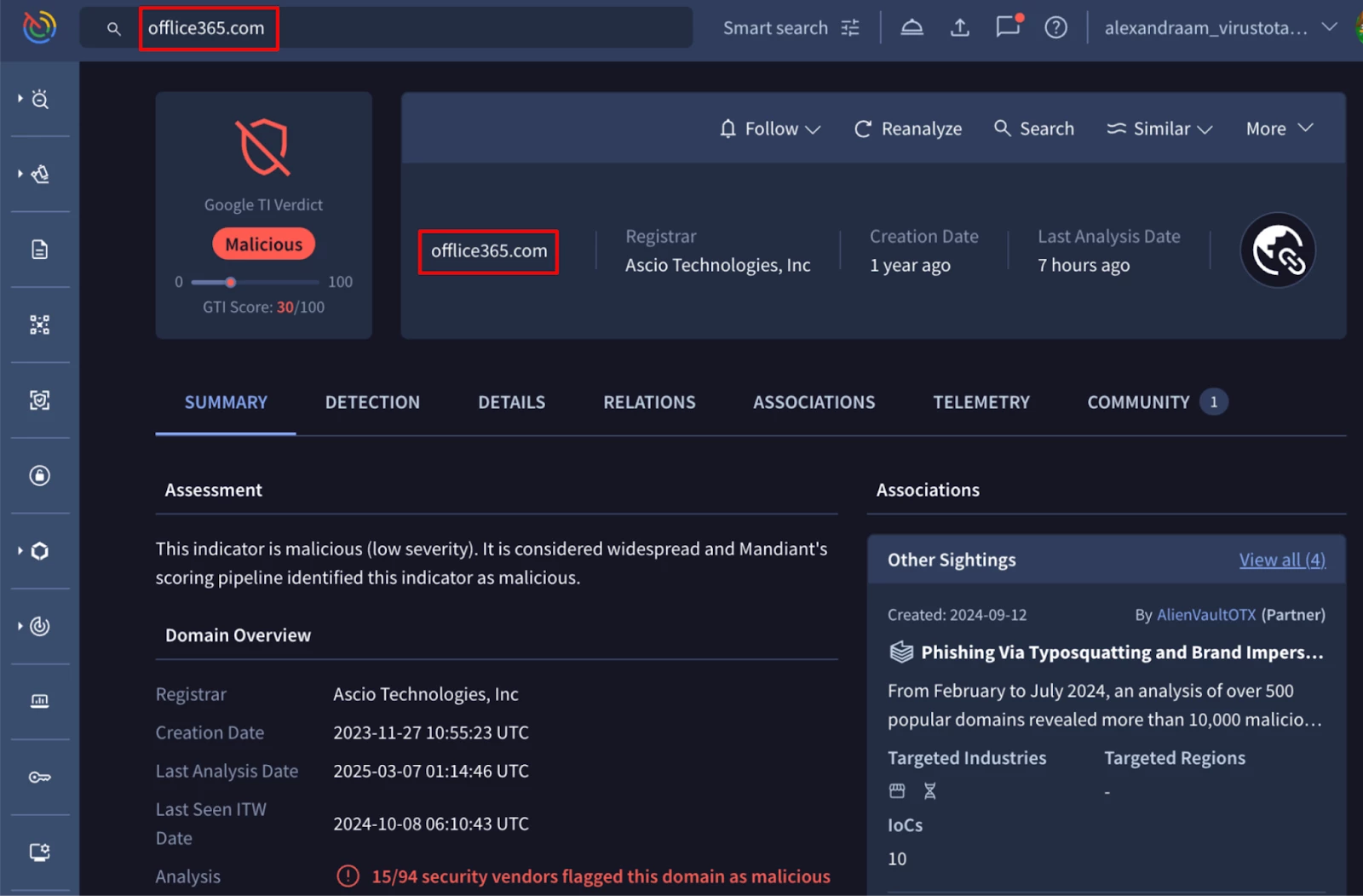 Figure 1:Typosquatting example related to office365[.]com
Figure 1:Typosquatting example related to office365[.]com
- Brand Impersonation: Attackers create websites that mimic the branding of well-known companies or organizations. This can include using similar logos, color schemes, and even website layouts.
At the time of the previously mentioned offlice365[.]com domain detection, it pointed to the following website, which mimicked the original site in an attempt to steal credentials from the service’s users.
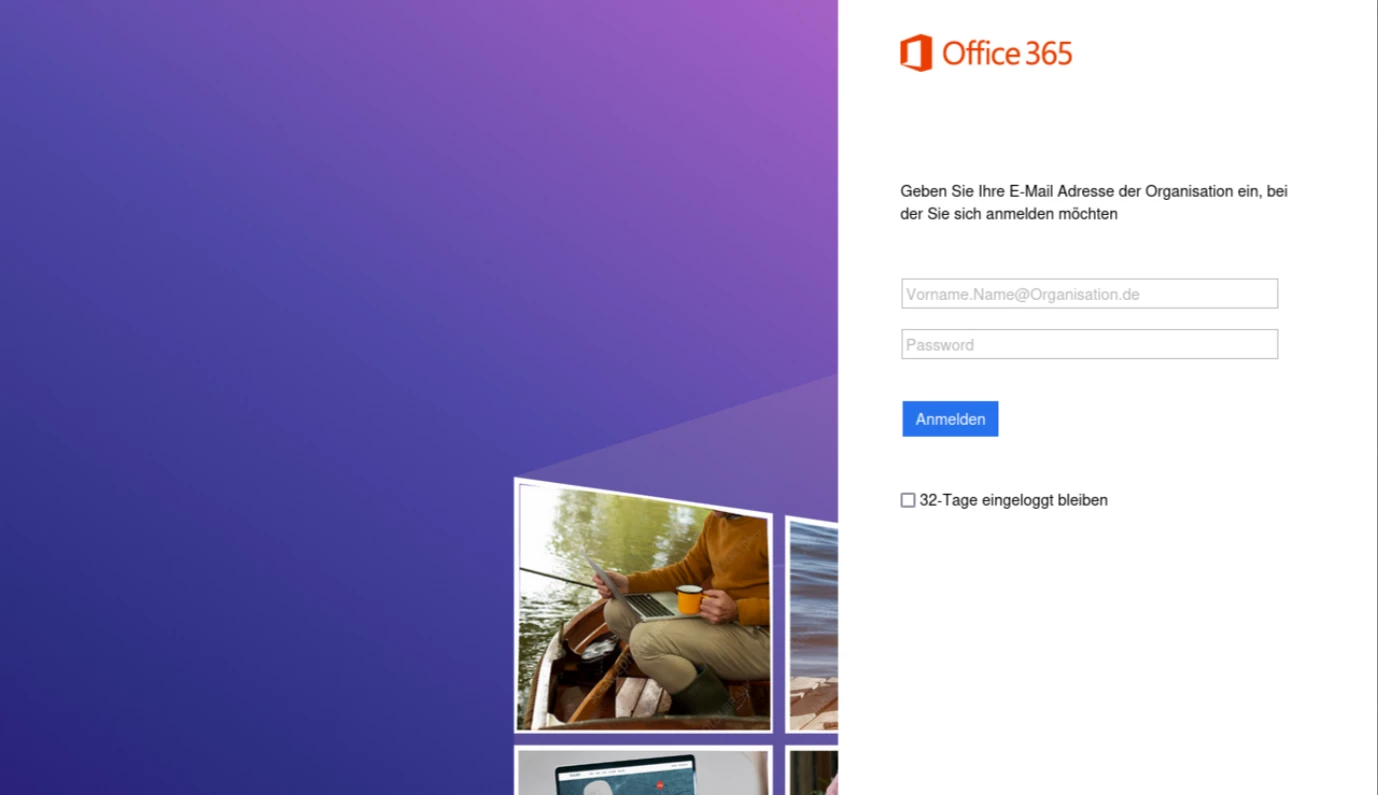 Figure 2: Website pointed by the previous domain mimicking office365[.]com
Figure 2: Website pointed by the previous domain mimicking office365[.]com
The following section details methods for identifying and tracking phishing campaigns with Google Threat Intelligence. We will explore:
- Searching our existing dataset of Indicators of Compromise (IoCs).
- Automating these searches through our API.
- Setting up automatic notifications or alerts for newly identified phishing-related IoCs using YARA Livehunt rules.
Proactive Phishing Detection with Google TI searches
A key element for querying our IoC dataset is the 'entity' search keyword to specify the type of output you want to search for:
- `entity:domain`
- `entity:url`
- `entity:ip`
- `entity:file`
In this guide we are going to focus mainly on domains and URLs, although Google TI allows us to search also for files and IP addresses as shown in the previous entities list. Each entity works in combination with specific search modifiers that can be combined through boolean operators (AND, OR, NOT, or none of them which is equivalent to AND) as well as parentheses:
Please, note that in all the use cases we are showing on this guide, we specify the IoC type since by default, you'll only get files.
Identifying Phishing campaigns targeting organizations
The following instructions and examples demonstrate how to search for domains or URLs that may be used to impersonate your organization, or even a third party. To make these examples work, replace [yourcorporatedomain] with your company's domain name.
1.1. Typosquatting and look-alike for domains/subdomains
The following query searches for domains that are visually similar to your corporate domain name, excluding your actual domain, to identify potential phishing or scam attempts:
entity:domain (fuzzy_domain:[yourcorporatedomain] AND NOT parent_domain:[yourcorporatedomain])
Note that we are reducing the number ofS false positives by filtering out the legitimate domains through the `parent_domain` search modifier, while the fuzzy_domain search modifier is triggering slightly similar domains from our database based on Levenshtein distance.
We can further refine these results using other domain search modifiers, such as:
- `creation_date:30d+` to retrieve new domains that were created in the last 30 days.
- `gti_verdict:malicious` to detect only those domains that Google TI has identified as malicious.
- `positives`: Filter domains according to the number of engines/blocklists that detect them.
To learn more about domain search modifiers, please visit our documentation here.
1.2. Favicon reuse for domains/subdomains
In this example, we will search for domains that utilize your corporate website's favicon, or a visually similar favicon, to detect potential phishing campaigns impersonating your brand.
First, we need to get the fingerprint of the corporate domain’s favicon. This allows us to identify other domains using the same favicon, even with slight alterations.
To do so, let’s search for your legitimate domain on Google TI and once we locate this favicon, displayed on the right side of the screen, we will click on it to obtain its hash value.
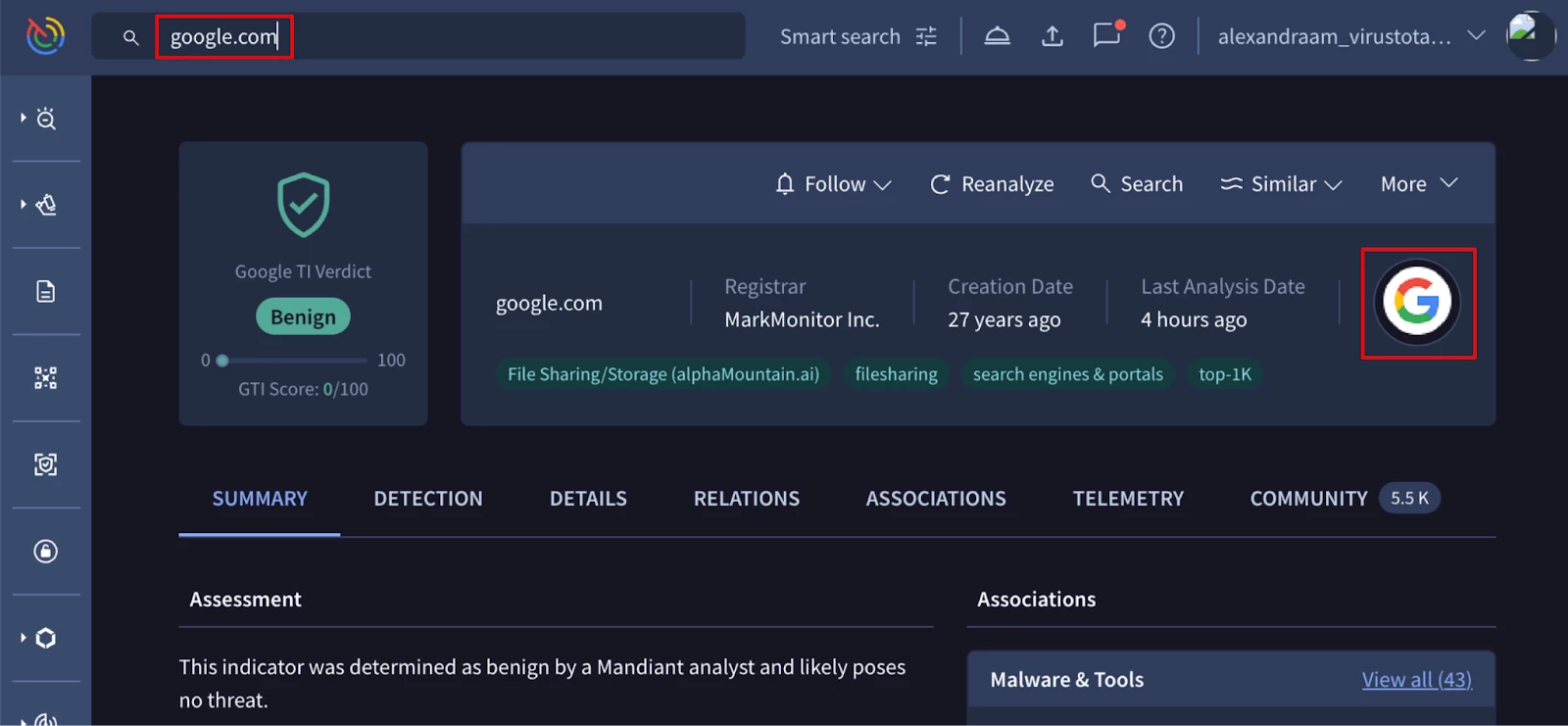 Figure 3: Example of google[.]com domain lookup to show the favicon
Figure 3: Example of google[.]com domain lookup to show the favicon
The favicon fingerprint value we get is a similarity `dhash` and it is automatically placed on the search bar to check other domains with similar favicons.
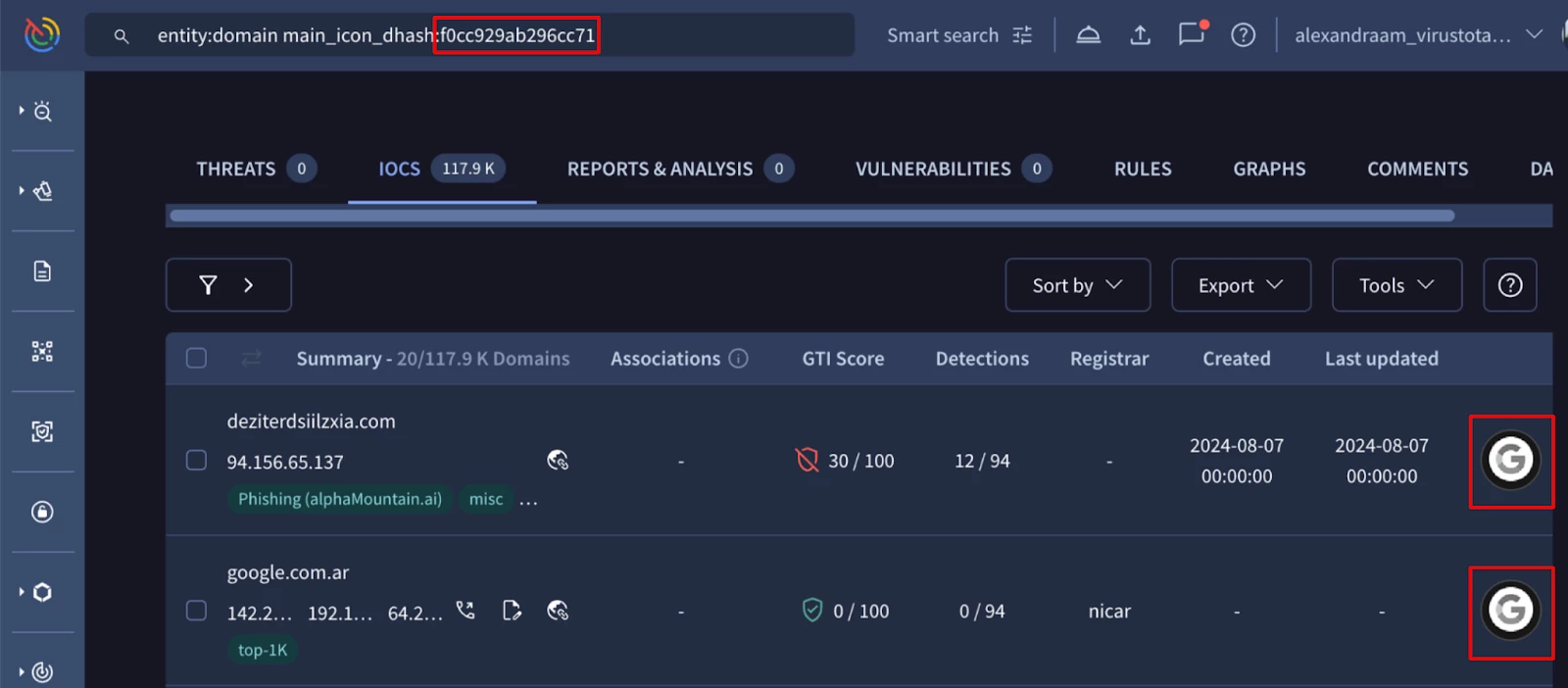 Figure 4: main_icon_dhash associated to google[.]com favicon
Figure 4: main_icon_dhash associated to google[.]com favicon
As we can see on the previous image, the `dhash` value is used with the `main_icon_dhash` search modifier.
Once we have this value, we can create another open query to search for potentially malicious domains utilising in this case a similar favicon `dhash` instead of a similar domain name.
entity:domain main_icon_dhash:[youricondhash] AND NOT parent_domain:[yourcorporatedomain]
We can refine our domain search by adding modifiers. For example:
- `tag:dga ` allows you to filter for domains generated through Domain Deneration Algorithms (DGA) through its associated tags.
To learn more about domain search modifiers, please visit our documentation here.
1.3. Brand impersonation for URLs
Beyond domain searches, we can also identify URLs impersonating your brand for credential theft, malware distribution or other fraudulent activities.
Let’s employ `entity:url` instead of `entity:domain` that we have seen in the previous examples, to search for URLs that mimic your organization.
The next query aims to find URLs by searching for your company name within a URL's meta tags, title, or the URL itself, while excluding your legitimate domains.
entity:url (meta:"[yourcompanyname]" OR title:"[yourcompanyname]" OR url:"[yourcompanyname]") AND NOT parent_domain:[yourcorporatedomain
We can refine your URL search by adding other modifiers. For example:
- `category:phishing ` that we can use to filter by what security vendors have already identified as phishing campaigns and reduce false positives, or other way around to filter out (`not category:phishing `) what’s already detected as such and focus only on new potential campaigns.
- `engine:phishing`: labeled as phishing by at least one blocklist/scanner.
- `path:[yourcompanyname]-login/home` to filter by path patterns, such as those typically used for login pages.
- `response_code:200` filter only by those alive URLs whose HTTP status code was 200 during the last analysis.
Another technique to detect phishing campaigns is based on a specific tracker ID, since sometimes, attackers can clone a website's look and feel (HTML/CSS code) for phishing campaigns including the same tracker of the original website.
Finding URLs that use this tracker can reveal additional URLs involved in the same campaign:
entity:url tracker:[detectedtrackerid] AND gti_score:30- AND NOT parent_domain:[yourcorporatedomain]
To identify your legitimate tracker IDs, access your Google Threat Intelligence report for your URL, and navigate to the 'DETAILS' tab → 'Trackers' section. If your organization's URL uses them, you will find some trackers there that you can use for your searches.
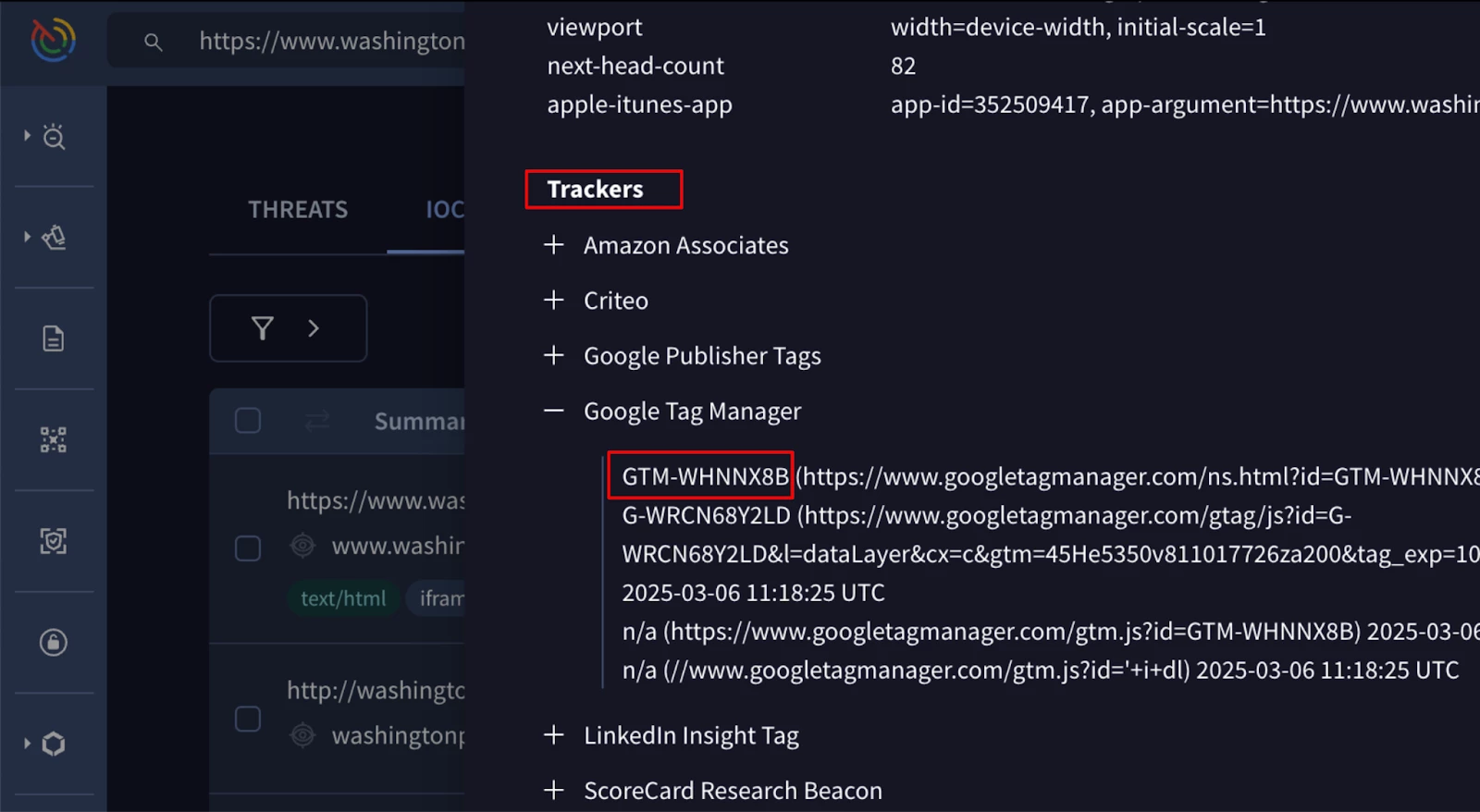 Figure 5: Breakdown of the site’s tracker information
Figure 5: Breakdown of the site’s tracker information
To learn more about URL modifiers, please visit our documentation here.
Analyzing generic phishing campaigns based on custom criteria
We can search for other URLs in Google TI through other popular criteria, like certificate issuers commonly used by attackers, domain registrars and suspicious TLDs or other reliable aspects for the investigation.
We could start with a query like the next one and adapt it to our convenience like for instance filtering by specific tags or the number of AV detected communicating files.
entity:domain creation_date:30d+ AND (tld:xyz OR tld:top OR tld:online) AND (registrar:namecheap OR registrar:GoDaddy) AND ssl_issuer:"Let's Encrypt" AND tag:”dga”
Automate your phishing queries using API
Another effective way to periodically run these intelligence searches is to create a script that makes use of the Google Threat Intelligence API. To automate intelligence searches, we need to use the following endpoint: 'www.virustotal.com/api/v3/intelligence/search'
This endpoint allows us to search for IoCs in the Google Threat Intelligence dataset, using the same query syntax that you would use in Google TI web interface.
You can check the endpoint official documentation here. Authorization can be achieved using your personal API key or a Service Account API key, which is not tied to a specific user
This Python code snippet provides a basic example of how to automate the following threat intelligence search.
- entity:domain creation_date:1d+ category:phishing
Link to Google TI query
import requests import json query = 'entity:domain creation_date:1d+ category:phishing' query = requests.utils.quote(query) url = f'https://www.virustotal.com/api/v3/intelligence/search?query={query}&limit=10&descriptors_only=false' headers = { "accept": "application/json", "x-apikey": YOUR_VT_APIKEY } response = requests.get(url.format(query), headers=headers) print(response.text)
Note that It is needed to transform the query to a URL Safe encoding value, in this case, we have used the `requests.utils.quote()` function.
Monitor phishing campaigns using Livehunt rules
Livehunt is a powerful feature based on YARA rules, which allows you to proactively monitor a real-time stream of analyzed URLs, IPs, domains, and files. Essentially, it's like setting up a custom alert system tailored to your specific threat intelligence needs. We will show next how to set up some basic rules to detect phishing.
You can find detailed information about the creation of YARA rules in the YARA documentation.
1. Malicious documents named invoice that use macros
This rule monitors a massive phishing campaign that employs malicious ‘.docx’ files that have "invoice" in the filename and are tagged with "macros".
import "vt" rule malicious_invoice_docx_macros { meta: description = "Malicious docx files using macros with ‘invoice’ name and submitted several times" target_entity = "file" condition: vt.metadata.file_name icontains "invoice" and vt.metadata.file_type == vt.FileType.DOCX and vt.metadata.analysis_stats.malicious > 5 and for any tag in vt.metadata.tags:(tag == "macros") and vt.metadata.first_submission_date > 1706486400 and vt.metadata.times_submitted > 10 }
Let's explain in detail the condition we have prepared so that the rule will alert us of any file that is uploaded to the platform and meets the detailed condition.
| Condition | Description |
| vt.metadata.file_name icontains "invoice" | Filters for files whose name contains the word “invoice”. |
| vt.metadata.file_type == vt.FileType.DOCX | Filter for only “docx” files. |
| vt.metadata.analysis_stats.malicious > 5 | Used to adjust the number of the detections coming from the AV vendors (> 5). |
| for any tag in vt.metadata.tags:(tag == “macros”) | Used to search the tag “macros” in the list of tags coming from the sandbox detonation. |
| vt.metadata.first_submission_date > 1706486400 | Narrow down the first submission date, it is used in epoch format. |
| vt.metadata.times_submitted > 10 | Select more than ten submissions since we are searching for a massive campaign. |
2. Potential URLs targeting an organization
This Livehunt YARA rule is designed to identify active phishing URLs targeting a particular company, with 'Acme' used for illustrative purposes.
import "vt" import "time" rule phishing_acme_urls{ meta: description = "Potentially active malicious phishing URLs targeting Acme company" target_entity = "url" condition: vt.net.url.favicon.dhash == "6190b6b8595c5523" and vt.net.domain.root != "acme.com" and vt.net.url.response_code == 200 and vt.net.url.first_submission_date > time.now() - (60*86400) and vt.net.url.analysis_stats.malicious >= 5 and ( for any engine, value in vt.net.url.signatures: ( value icontains "phishing" ) or for any engine, value in vt.net.url.categories: ( value icontains "phishing" )) }
Let's explain in detail all these conditions:
| Condition | Description |
| vt.net.url.favicon.dhash == "6190b6b8595c5523" | Filters for URLs reusing the same favicon dhash than Acme uses. |
| vt.net.domain.root != "acme.com" | Used to exclude results coming from the legit corporate domain. |
| vt.net.url.response_code == 200 | Filters for URLs that were active, in other words returned a 200 HTTP response code when they were scanned. |
| vt.net.url.first_submission_date > time.now() - (60*86400) | Verifies if the URL was first submitted to VirusTotal within the last 60 days. |
| vt.net.url.analysis_stats.malicious >= 5 | Verifying that the amount of engines returning malicious in the analysis (bigger or equal to 5). |
| for any engine,value in vt.net.url.signatures:(value icontains "phishing") | Check if one of the signatures returned by the engines will be phishing. |
| for any engine,value in vt.net.url.categories:(value icontains "phishing") | Check if one of the categories returned by the engines will be phishing. |
Conclusion
Google Threat Intelligence is a powerful tool for proactive phishing defense. It helps security teams identify and analyze phishing campaigns targeting specific organizations or broad phishing campaigns. This can accomplished using different methods:
- Detecting potential deceptive domains: Identifies typosquatting and look-alike domains/subdomains that could be used by attackers.
- Identifying favicon reuse: Detects favicon reuse across other non legitimate domains/subdomains.
- Recognizing impersonating URLs: Uncover URLs used to impersonate your brand.
These functions enable security teams to pinpoint targeted campaigns and analyze general phishing activity using custom criteria.
Moreover, Google Threat Intelligence provides API access for automated queries and Livehunt rules for real-time campaign monitoring. These capabilities empower security teams to proactively defend against phishing and mitigate its impact.
To know more about the full list of Google Threat Intelligence modifiers, please visit our official documentation here.


