CrowdStrike deprecated the Detects API on October 1, 2024 and this API will be decommissioned on September 30, 2025. This API has been superseded by the CrowdStrike Alerts API.
Please continue reading if…
- You have active SIEM data feeds on Google SecOps using the CrowdStrike Detection Monitoring (“CS Detects”) API connector (mapped to the CS_DETECTS logtype), and
- Your CrowdStrike API Client mapped to this feed does not have permission to read ‘Alerts’.
What action do I need to take?
You are advised to take one of the following actions:
- Option 1 (recommended): Update permissions for your existing CrowdStrike API clients that are using the CS Detects API.
- This is a straightforward and simple approach, requiring changes only on your Falcon Tenant.
- It also provides a way to verify whether your feeds are still using the DETECTS API (verification steps provided below).
- This has the lowest downstream impact on any active Detection Rules that refer to the CS_DETECTS logtype.
- Option 2: Update your existing feeds’ API credentials to include a new API client which has been granted suitable read permissions.
- This should be used if you face any trouble identifying your existing API client IDs using Option 1.
Please take these actions by September 30, 2025 to avoid any disruptions.
Option 1: Update permissions for your existing CrowdStrike API clients using the CS Detects API
First, confirm whether the Detects API is in use by your CrowdStrike tenant. CrowdStrike has developed a dashboard to help you identify API clients that are using the deprecated endpoints. Please refer to this CrowdStrike support article to access this dashboard.
API clients used by the Detection Monitoring feed will display a user agent string starting with Google-Chronicle-Security. If any such API clients are shown, please carry out the following steps.
Step 1: Navigate to the article (link)
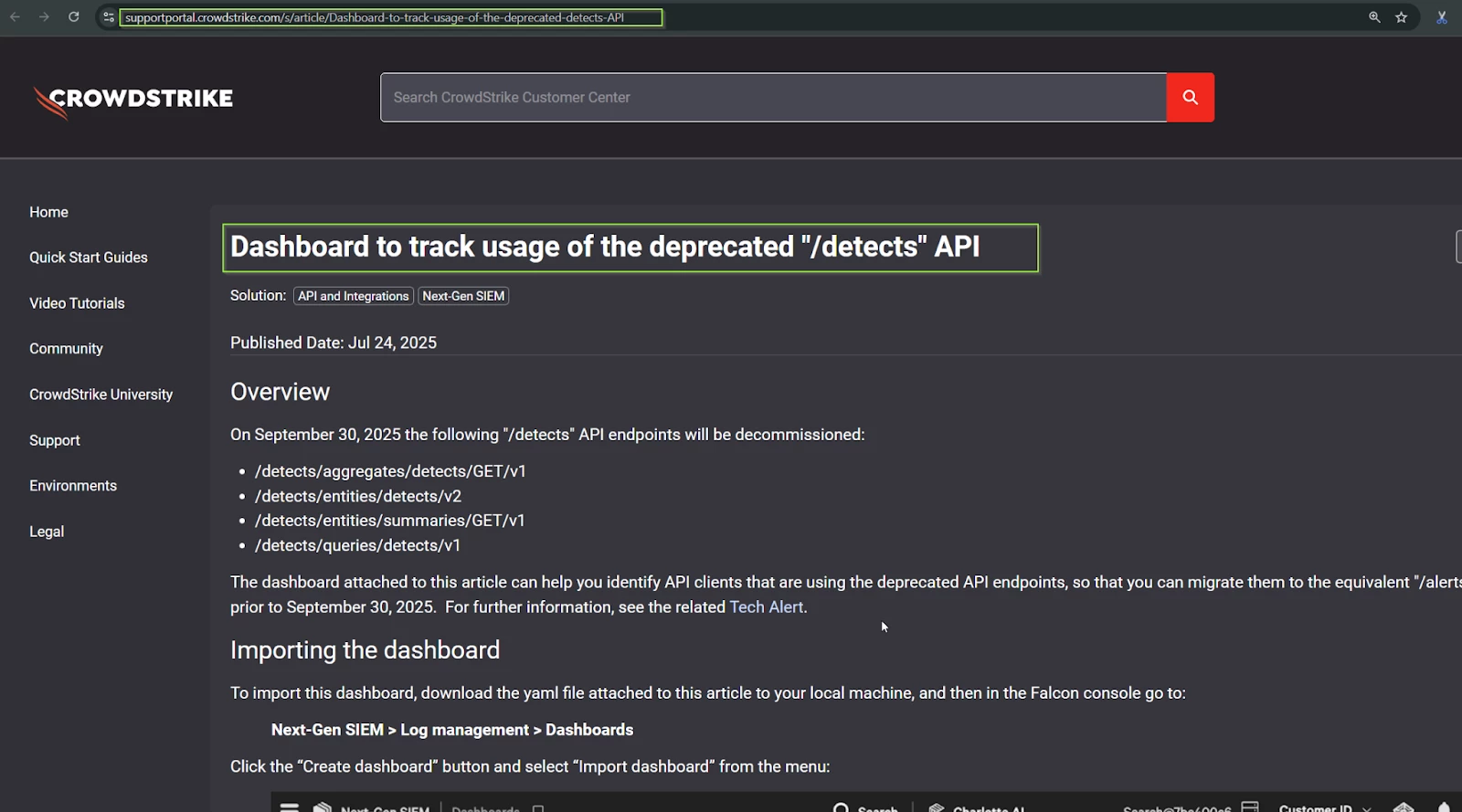
Step 2: Scroll down to the bottom of the article and download the YAML file
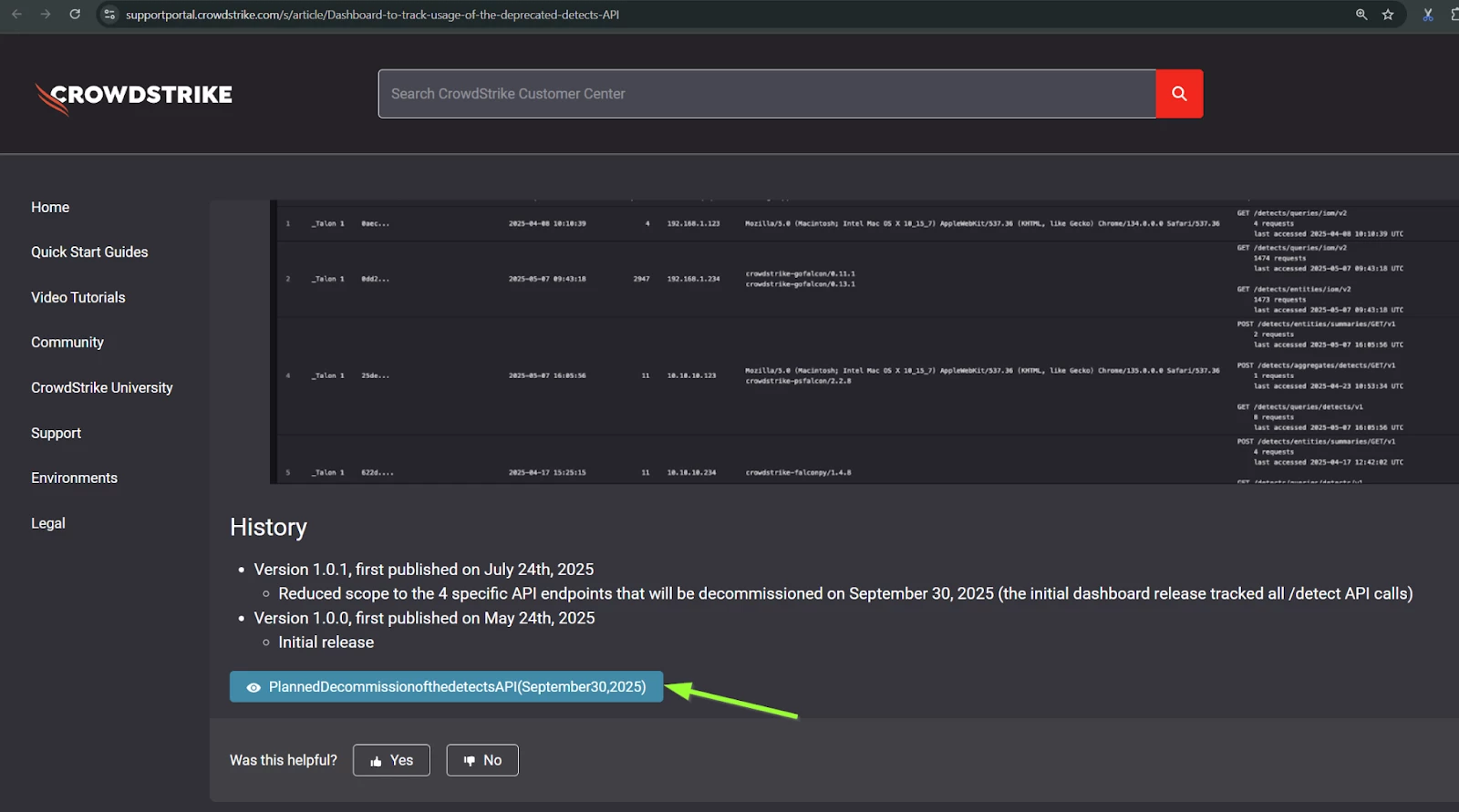
Step 3: In the Falcon console, go to Next-Gen SIEM > Log management > Dashboards, and create a new dashboard importing the YAML file downloaded in Step 2.
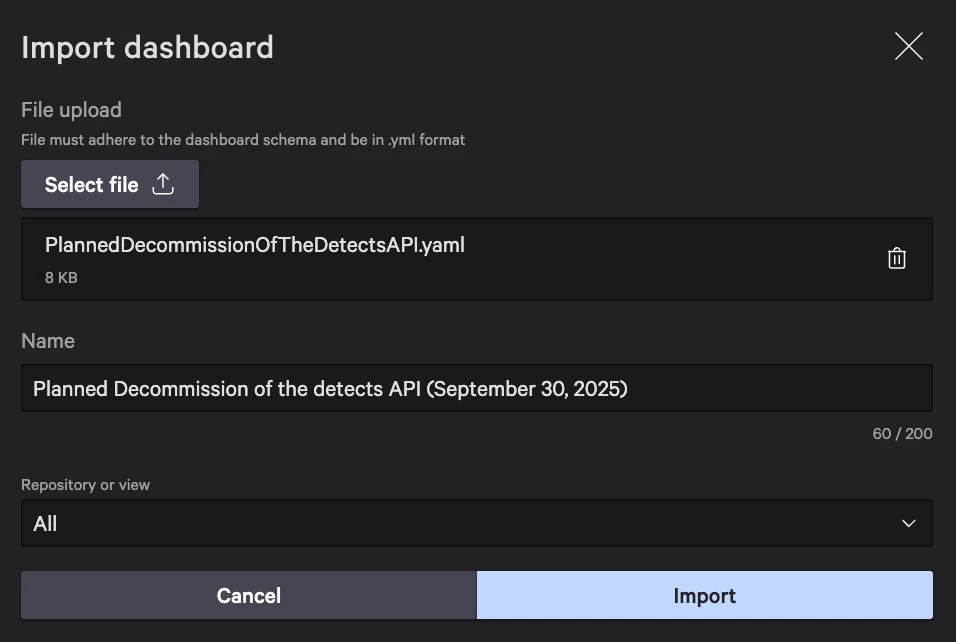
Step 4: Scroll down to Calls to the deprecated "/detects" API endpoints section and for every API client id found there - please add Alerts-Read permission as shown below (shown only for one API client ID 462e006dec**********)
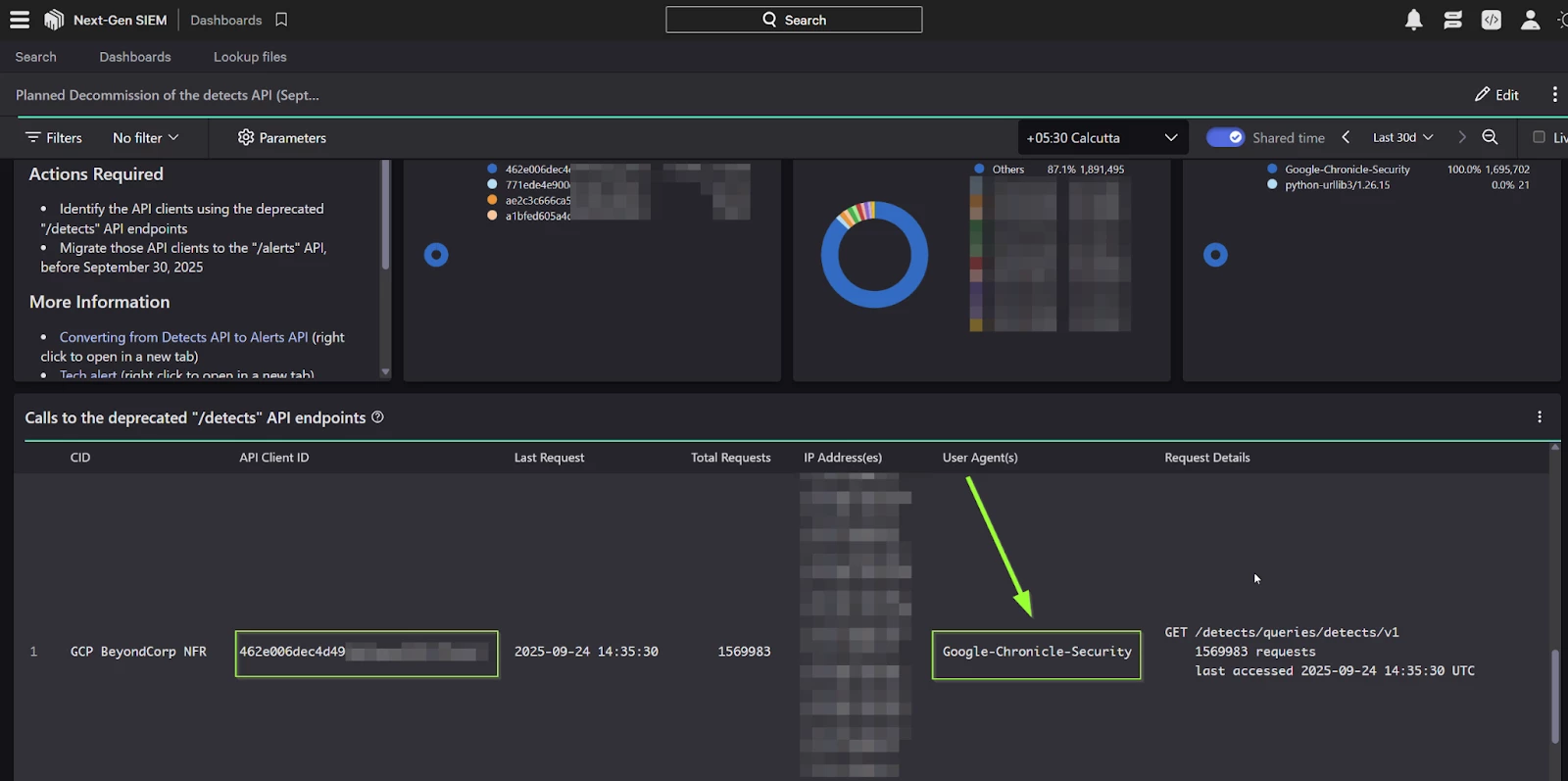
Step 5: You may have to cycle through the pages of “API clients and keys” screen on Falcon to find the API Client Ids
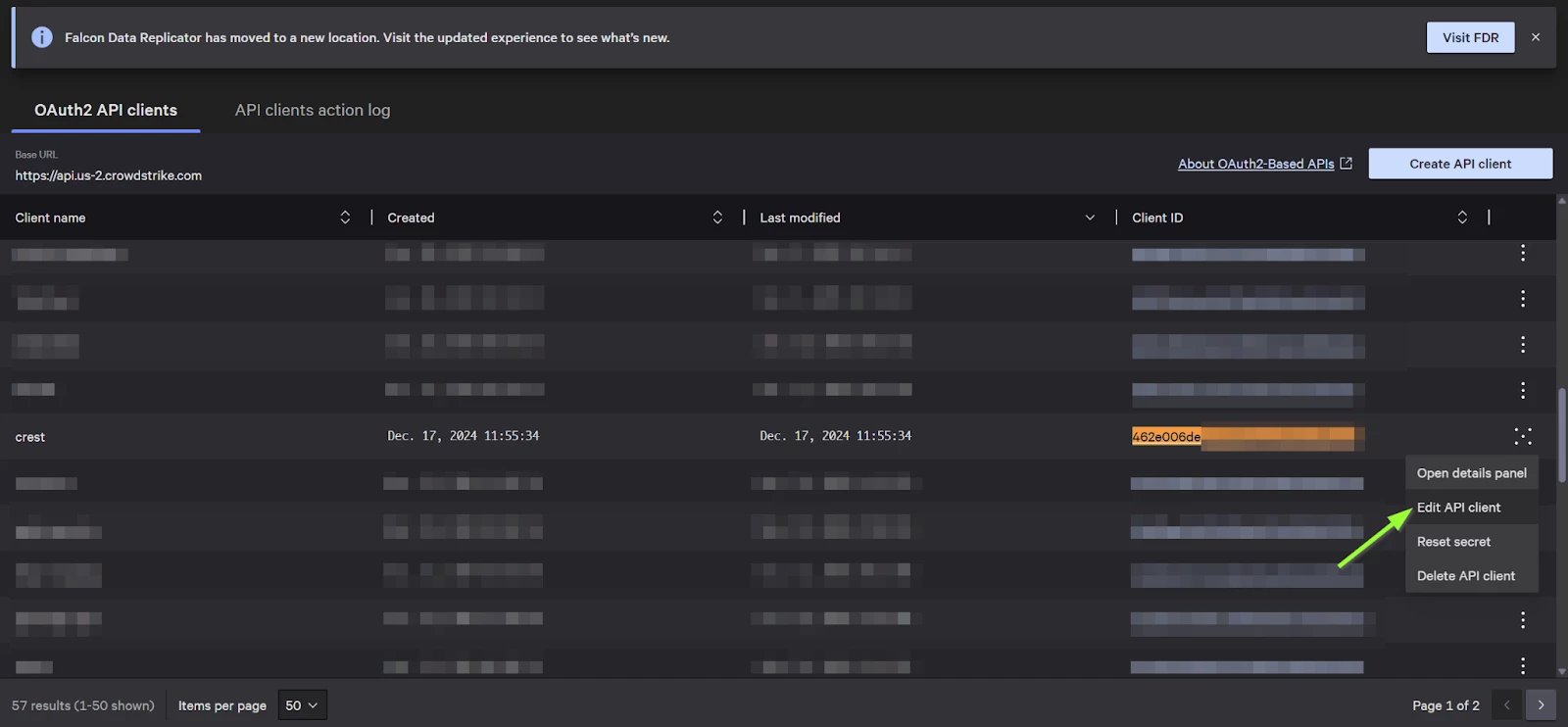
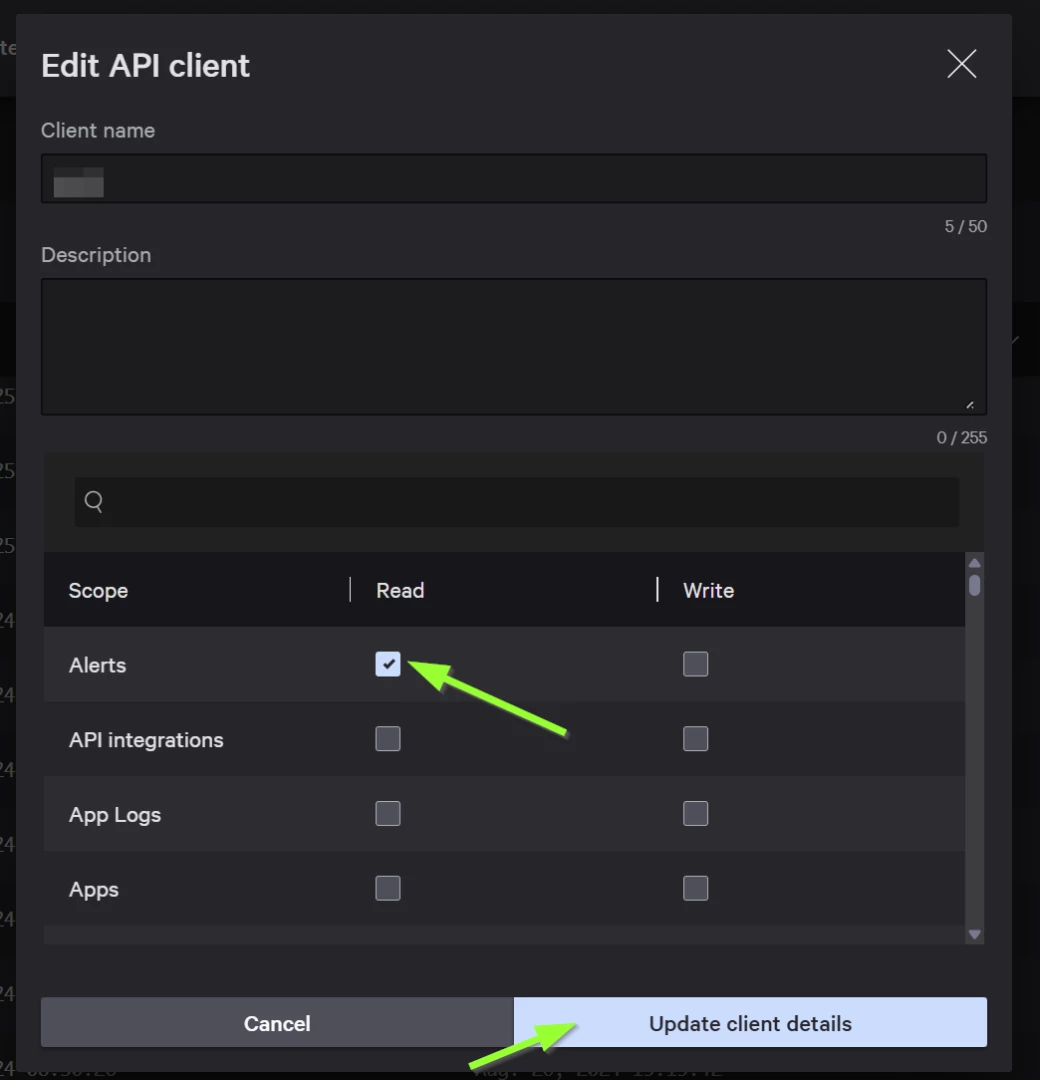
Step 6: Add the “Alerts - Read” permission as shown below and click “Update client details”
Step 7: Verify whether the changes have taken effect
- Check your SecOps tenant to confirm whether your feeds are still receiving data after the change.
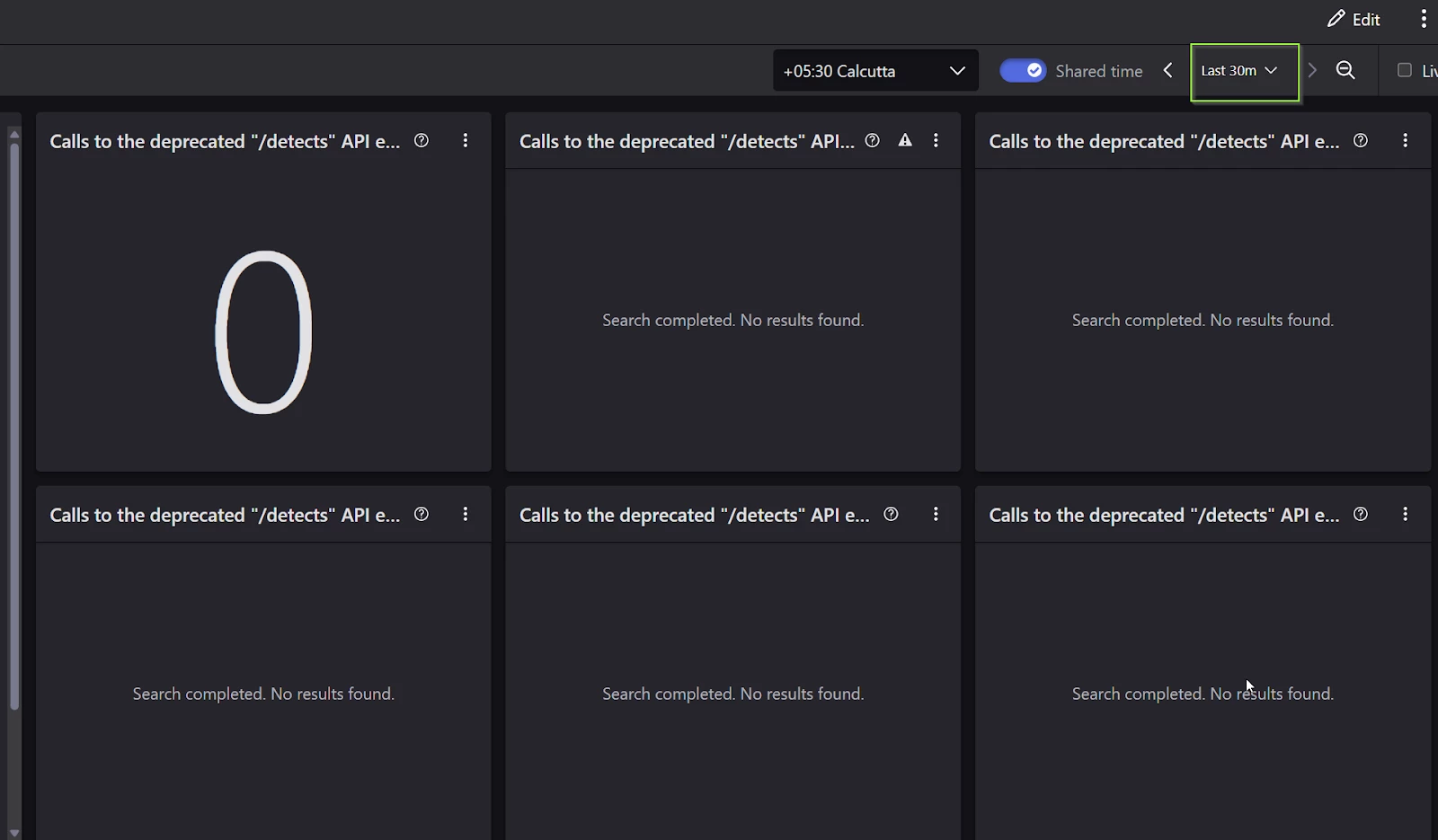
- Check the “before” and “after” scenarios in the dashboard as shown below
Before Update: the 30d period has several client IDs which we enabled for Alerts using the steps described above.
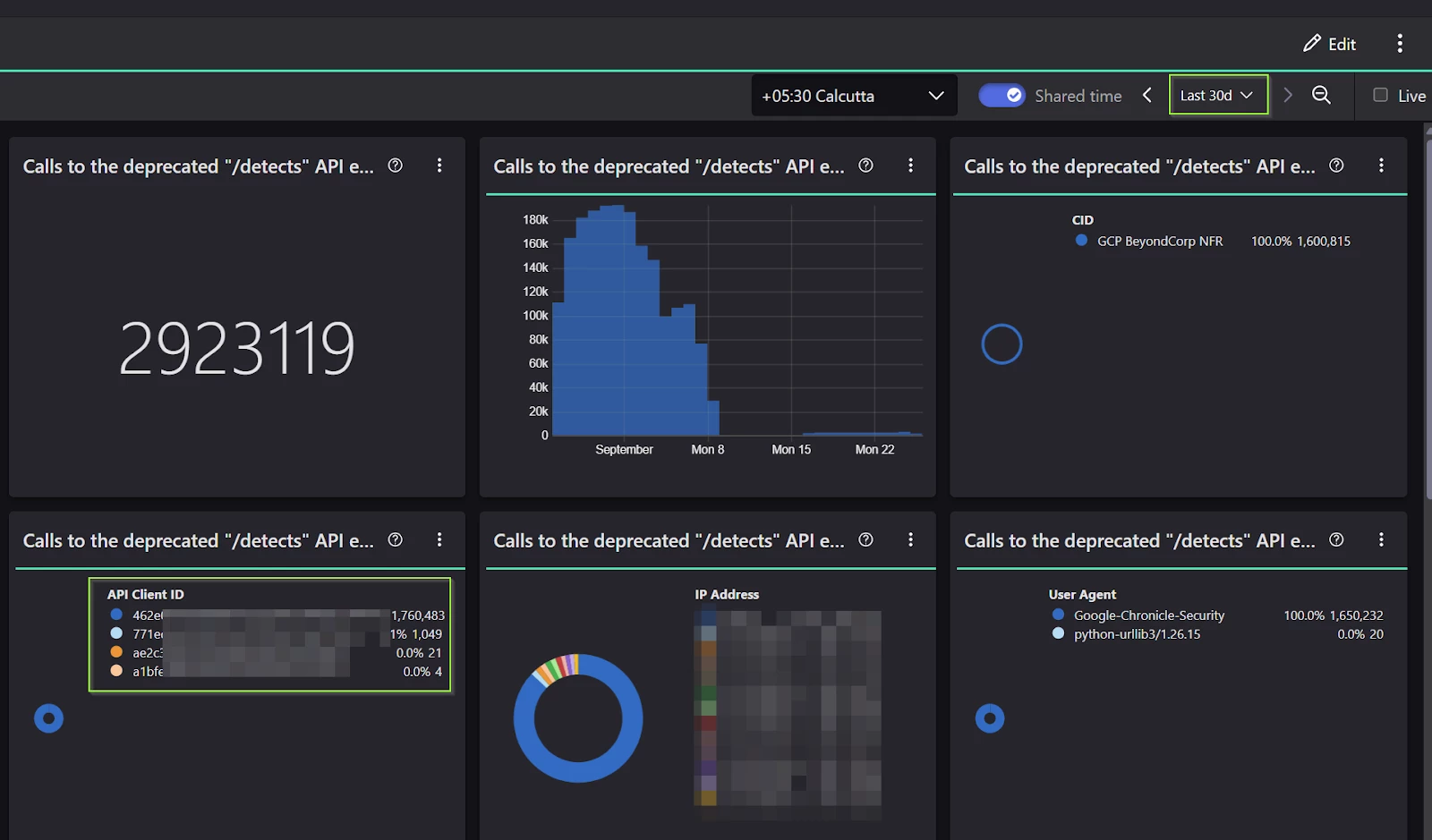
After Update: 30 minutes after the change, you should find that no detects API calls are being registered by the Crowdstrike dashboard
Option 2 - Update your existing feeds’ API credentials to include a new API client which has been granted suitable read permissions
The CS Detects API connector in Google SecOps automatically tries to call the new CS Alerts API first for your feed, before falling back to Detects API if the necessary permissions are missing (i.e., Alerts - Read).
Step 1 - Navigate to the “API clients and keys” section on your CrowdStrike Falcon console
- Navigate to {BASE_URL}/api-clients-and-keys/clients
- e.g. https://falcon.us-2.crowdstrike.com/api-clients-and-keys/clients
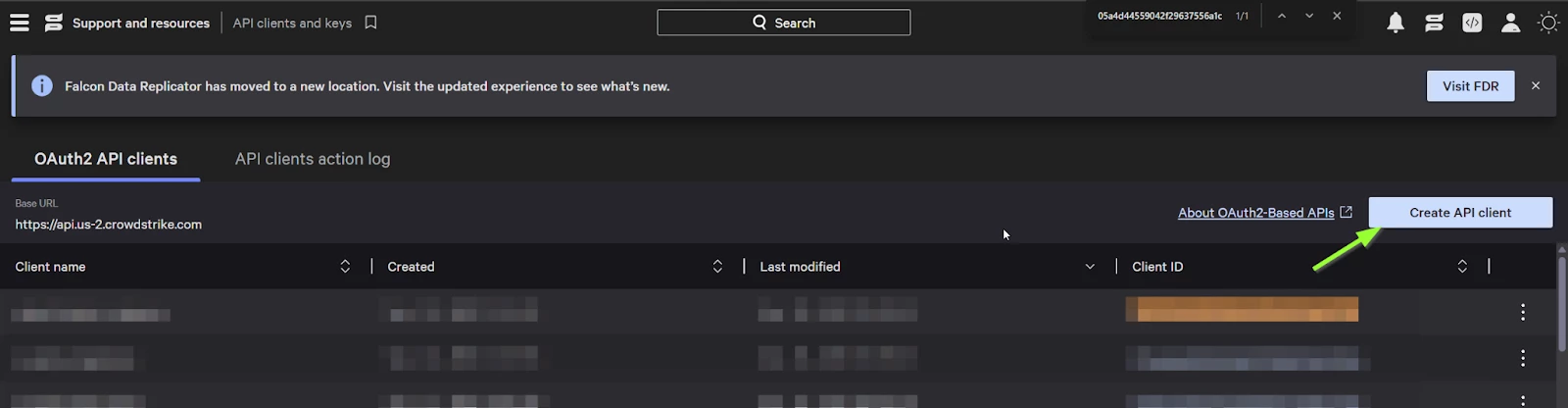
Step 2 - Create a new API client
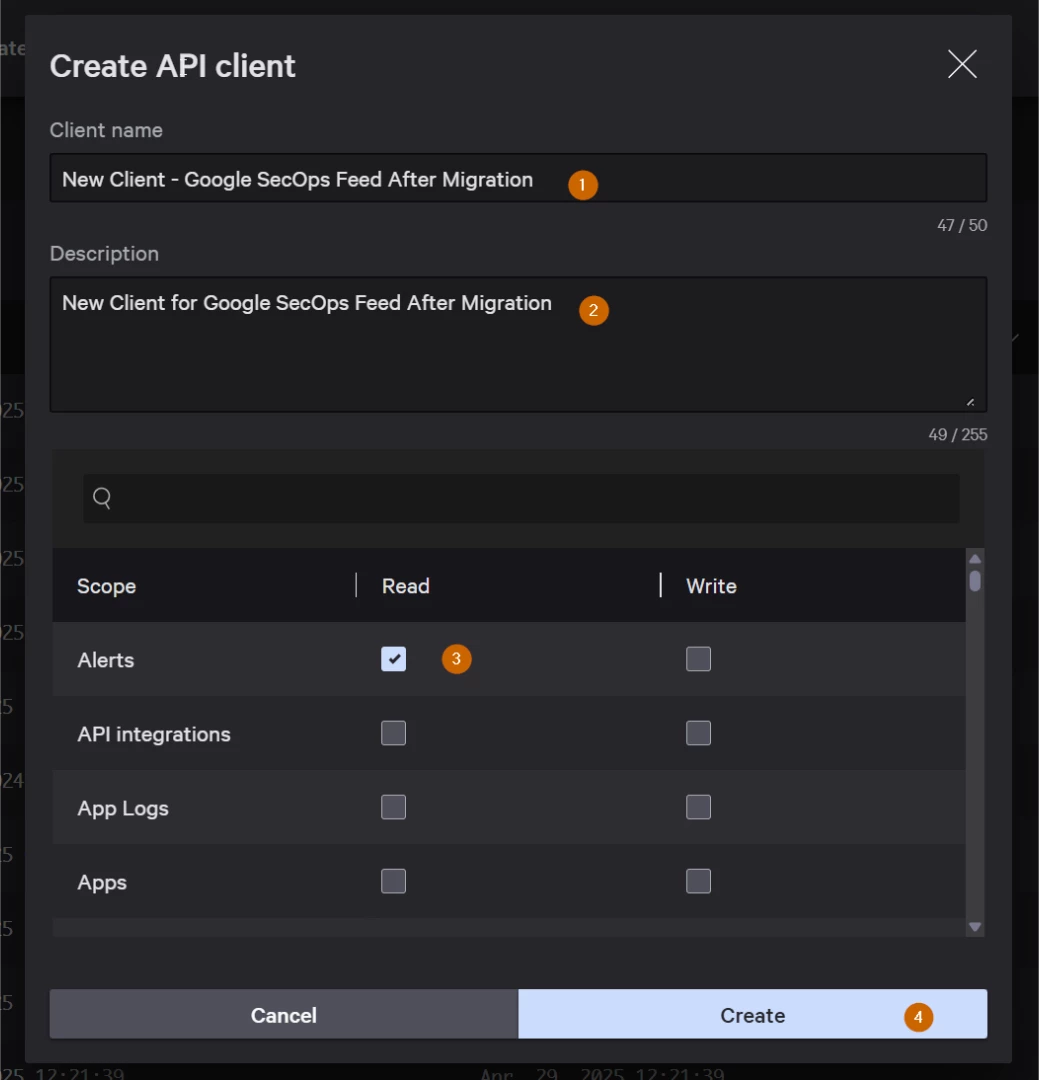
Step 3 - Provide the new API Client with Alerts - Read permission
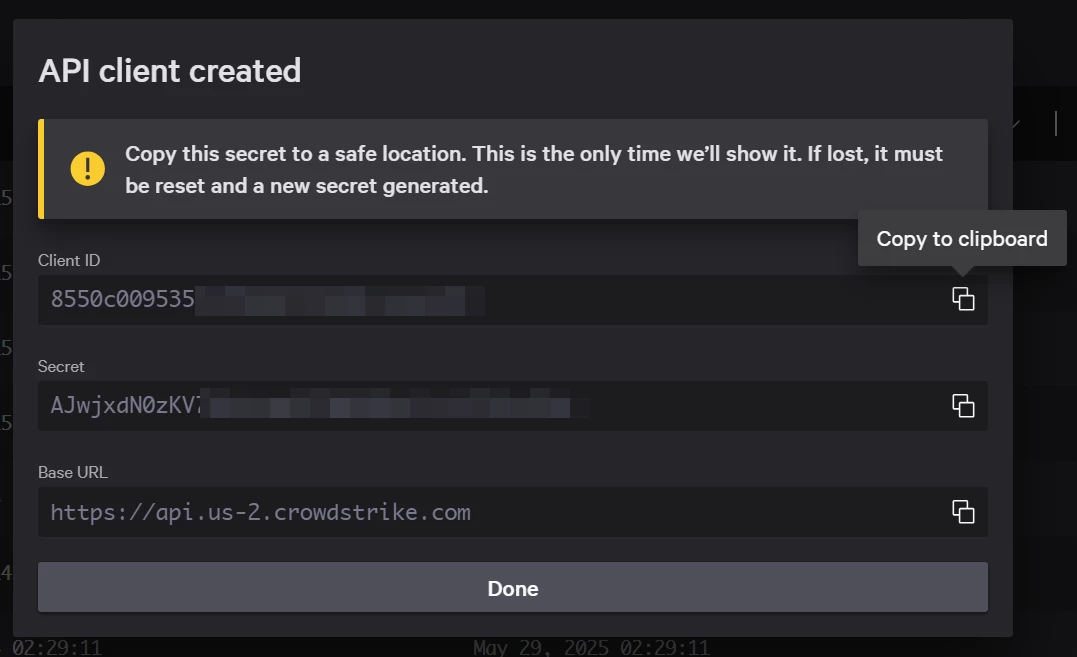
Step 4- Copy the Client ID, Client Secret, and Base URL from the console
Step 5 - Go to your Google SecOps console, navigate to Settings>Feeds, and for your existing CS Detects feed, click on “Edit Feed”
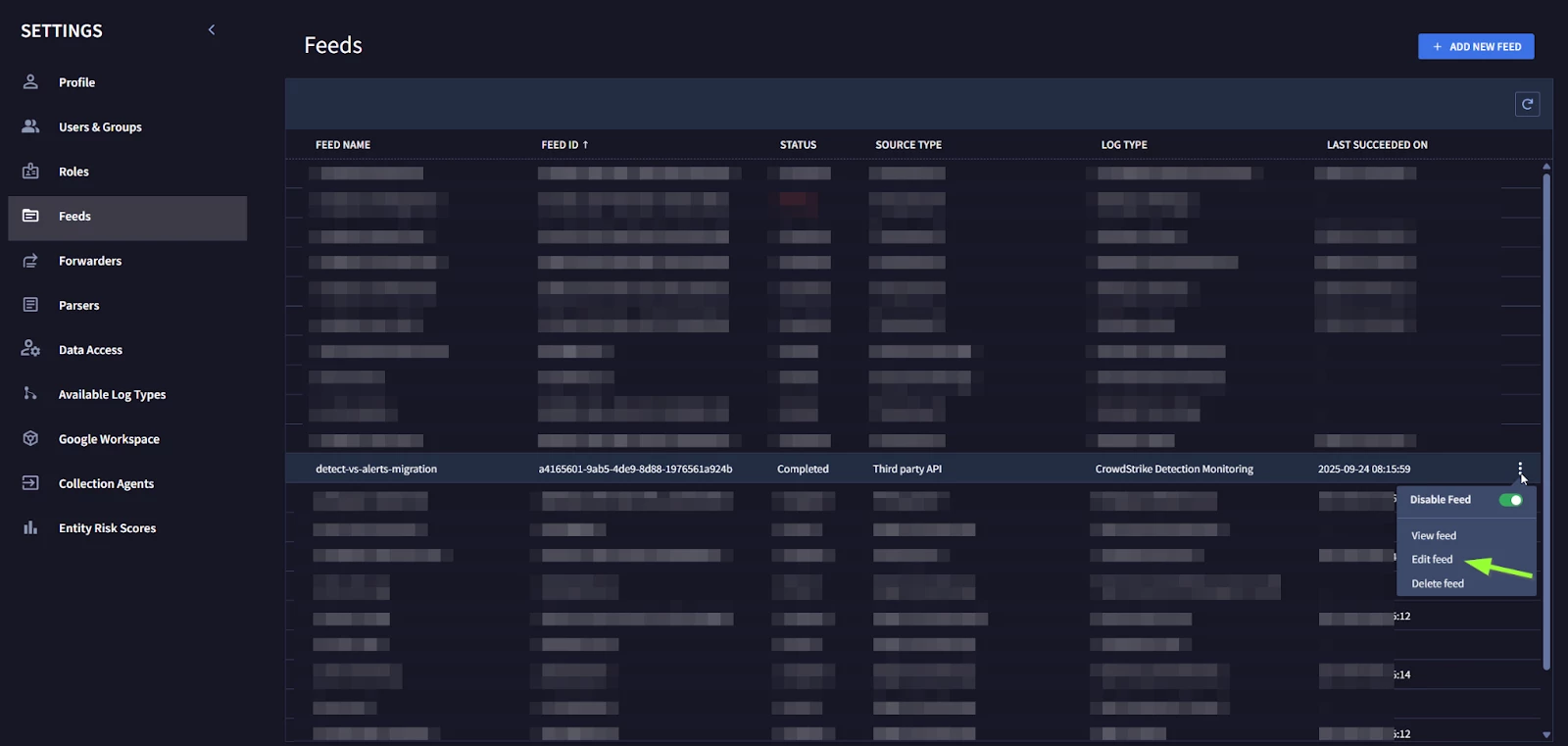
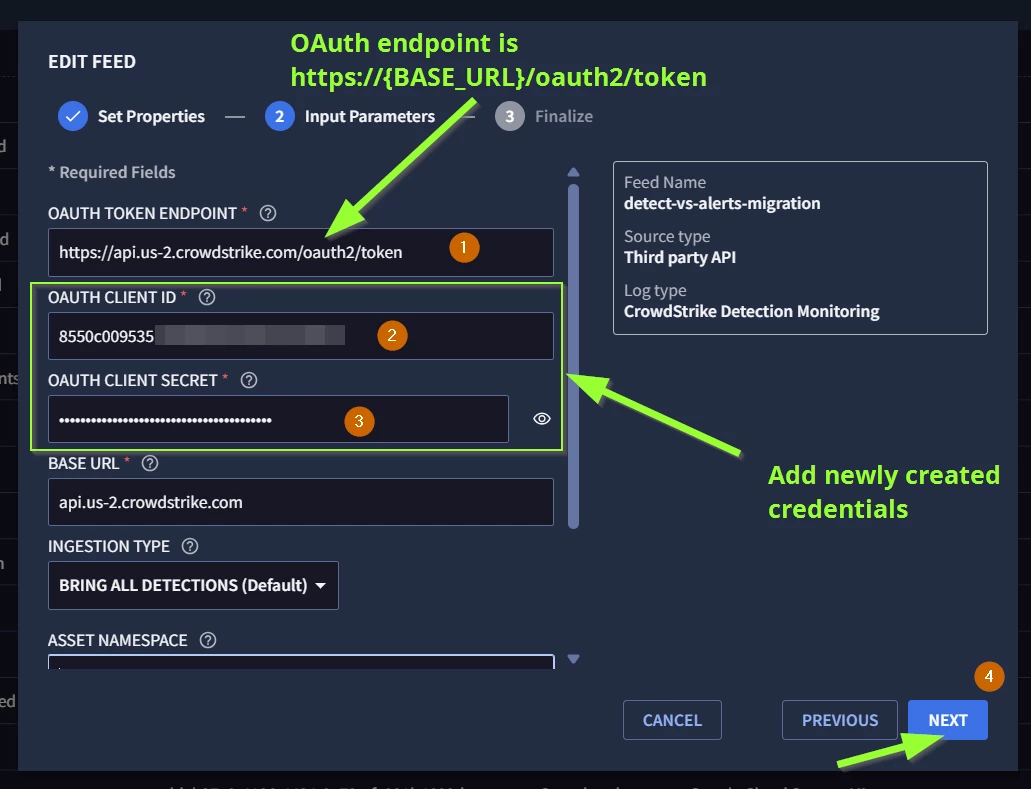
Step 6 - Update your feed with these new credentials that were copied from your CrowdStrike console
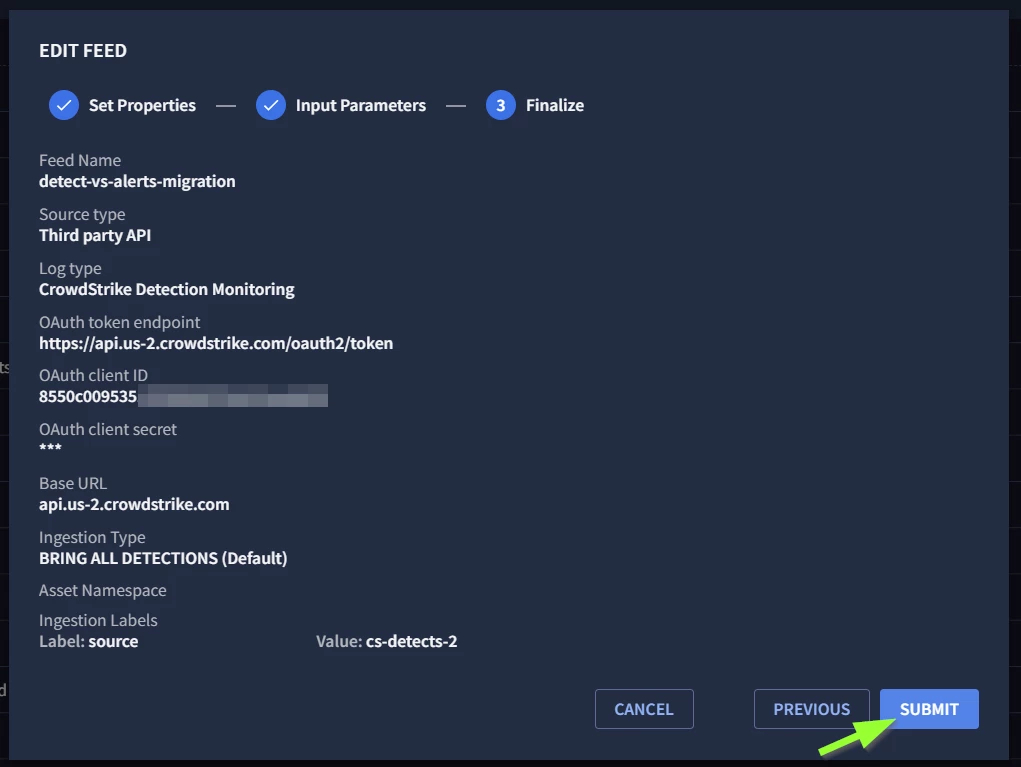
Step 7 - Review your feed configuration details, and click on submit to save these changes
Step 8: Verify whether the changes have taken effect
- Check your SecOps tenant to confirm whether your feeds are still receiving data after the change.
- Check the “before” and “after” scenarios in the dashboard as shown below
Note - In case you have multiple feeds for Crowdstrike Detection across multiple SecOps instances - repeat the steps 1-5 for each feed.
Timeline for decommission
As mentioned above the current final date for this transition is September 30, 2025. The detection monitoring feeds will fail to fetch the data after that date, unless you have taken one of the recommended action. For more information, click here to review CrowdStrike’s 30 day notice on the decommission using this link.



