We're bringing to you another Community challenge and this time it's about Model Context Protocol. MCP is a hot topic in the security world right now. For those just hearing about MCP, it allows AI models to communicate with and leverage the capabilities of diverse security tools. This helps enhance security workflows by ensuring models are contextually aware across multiple downstream services. With the ability to interact with security data in natural language, security teams can produce insights faster and scale their security operations. If you’re just getting started with the SecOps MCP server, check out our SecOps MCPserver content to learn more.
We're excited to launch this new challenge and can't wait to see all the different ways you are using the Google SecOps MCP server to boost your security operations. Knowing our expert Community users, we bet you're doing incredible things. And we want to see what you're up to! This is your chance to contribute to the Community, show off your skills, inspire others and win some awesome Google swag!
Here's How to Participate:
- Tell us how you're using the SecOps MCP server. In the comments below, share how you're using the SecOps MCP server in your workflow. Are you using it for automation, data analysis, or something completely new? We want to hear all about it!
- Show us a screenshot or video (YouTube videos only please). Post a screenshot or a short video (you can blur out any sensitive info) that shows your SecOps MCP server in action.
- Get likes! The posts with the most likes from the Community will win! Make sure to like your favorite responses to help us find our winners.
Duration: Jul 22, 2025 - Aug 29, 2025
Winner Announcement date: Winners will be announced Early-September 2025
Prizes: The top three participants with the most likes will win some cool Google SecOps swag! The contest ends on August 29, 2025, and we'll announce the winners shortly after.
Get Inspired: SecOps MCP Ideas and Examples
Stuck for ideas? The SecOps MCP server is incredibly versatile! Here are some ideas and examples from our engineers to spark your creativity for a winning entry:
Ideas
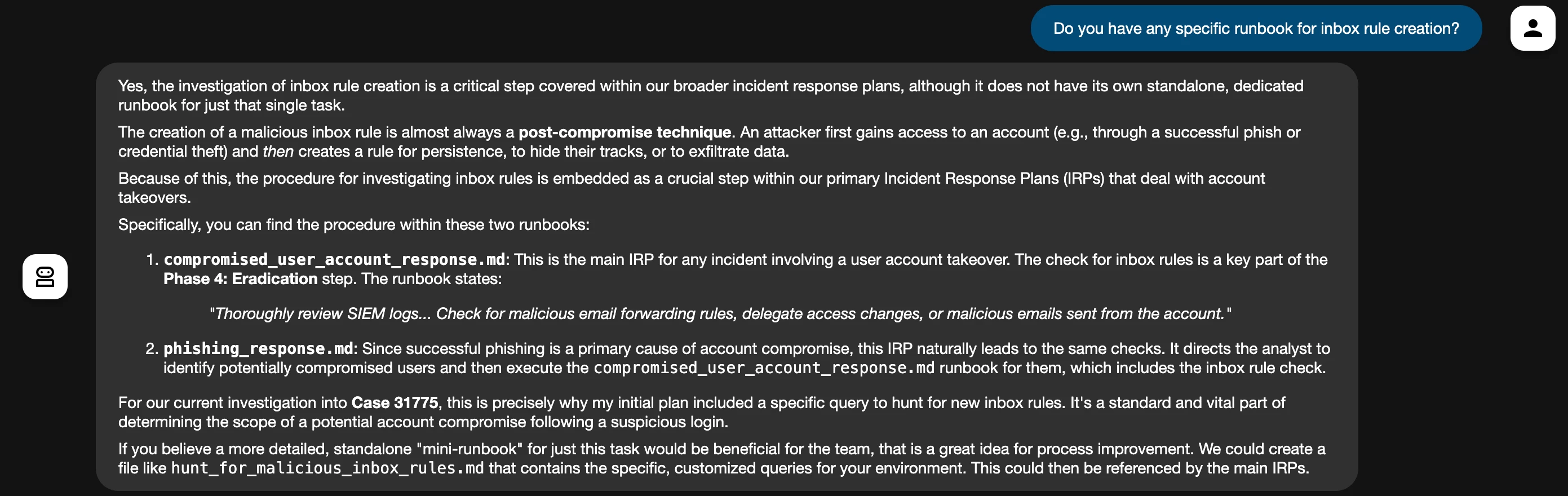
- Automation Master: Show your custom scripts, playbooks, or automated workflows that save time on tasks, incident response, or alert enrichment.
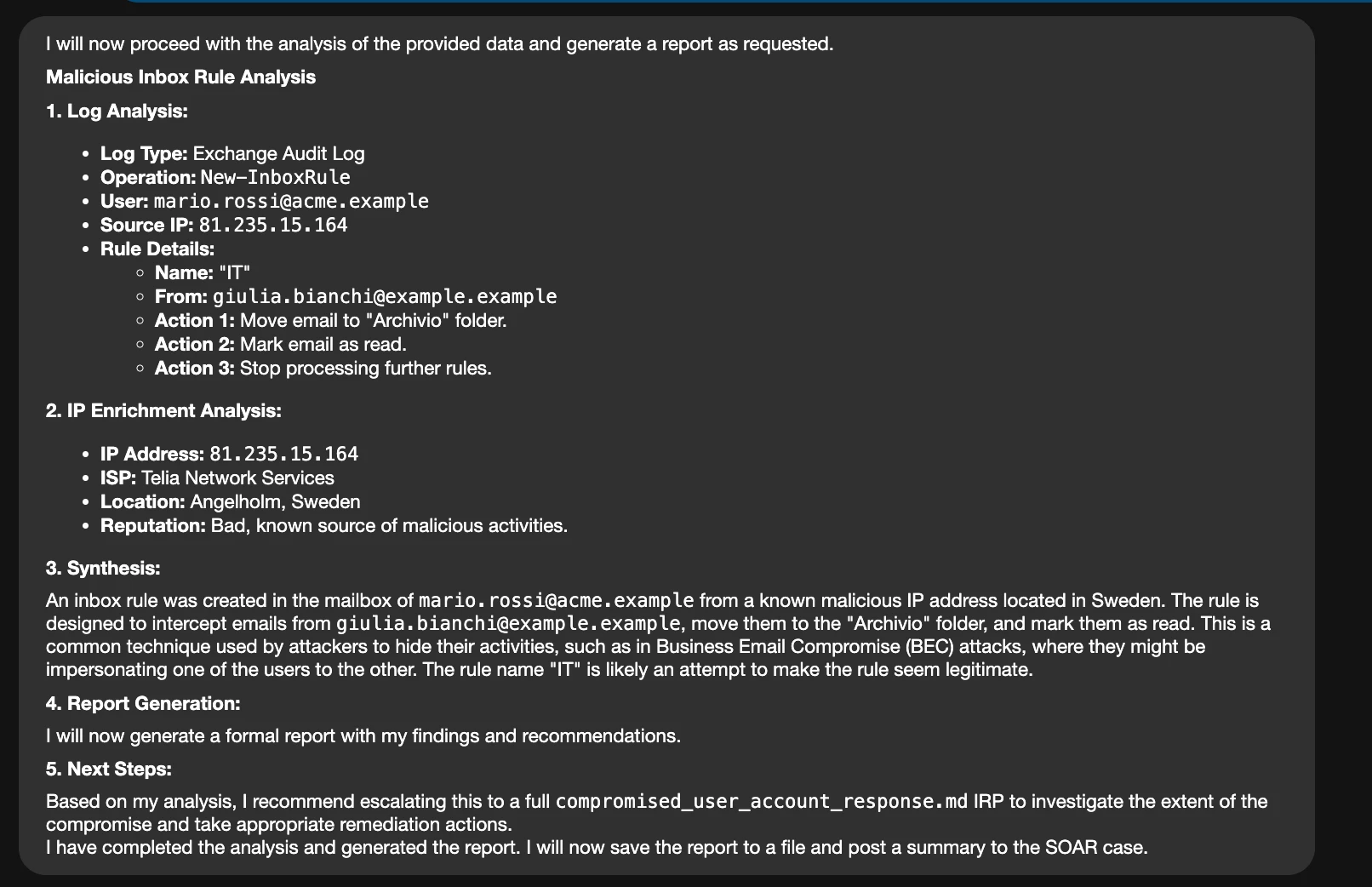
- Visibility Guru: Share unique dashboards or reports that provide deep insights, visualize data, identify trends, or track key metrics.
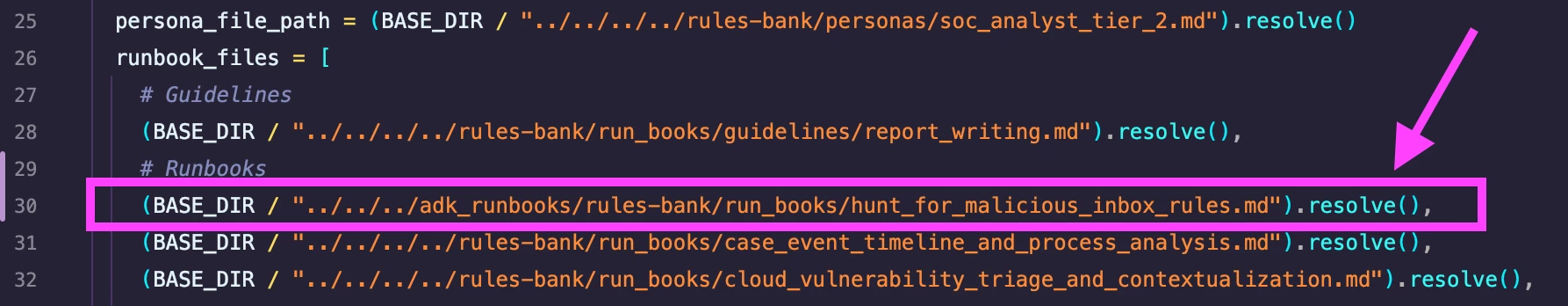
- Integration Wizard: Demonstrate how your MCP server connects seamlessly with other security tools, threat intelligence, or ticketing systems for a unified ecosystem.
- Efficiency Champion: Tell us how the MCP server has reduced false positives, sped up investigations, or improved overall operational efficiency (a "before and after" can be powerful!)
Examples and Resources
- See what’s new on our video AI Runbooks for Google Cloud Security MCP Server, where we demonstrate how AI runbooks can enhance your visibility and automate responses within Google Cloud Security.
- Here is how you can use MCP for proactive threat hunting, showcasing how the MCP server integrates with various tools to identify and mitigate threats before they escalate. Take a look at our video demonstrating using MCP Servers with ADK, highlighting how this integration can significantly improve the efficiency of your security operations.
- Check out our video on starting to use MCP for Google Cloud Security, which walks you through the initial setup and automation capabilities for your security services in Google Cloud environment.
We're looking for creativity, clarity, and most importantly, how you're making the SecOps MCP server work for you. Don't hold back – even small, clever use cases can make a big impact.
Ready to share? Drop your submission below in the comment section with a screenshot and description, or YouTube video.