Hi Lee,
For the GKE Security Bulletin vulnerabilities we would normally look for vulnerabilities related to Security Bulletins related to GKE. Some more details on these can be found here:
https://cloud.google.com/kubernetes-engine/security-bulletins
If you have any associated Active Findings then it’s worth checking for any actions which could be required per the associated bulletin.
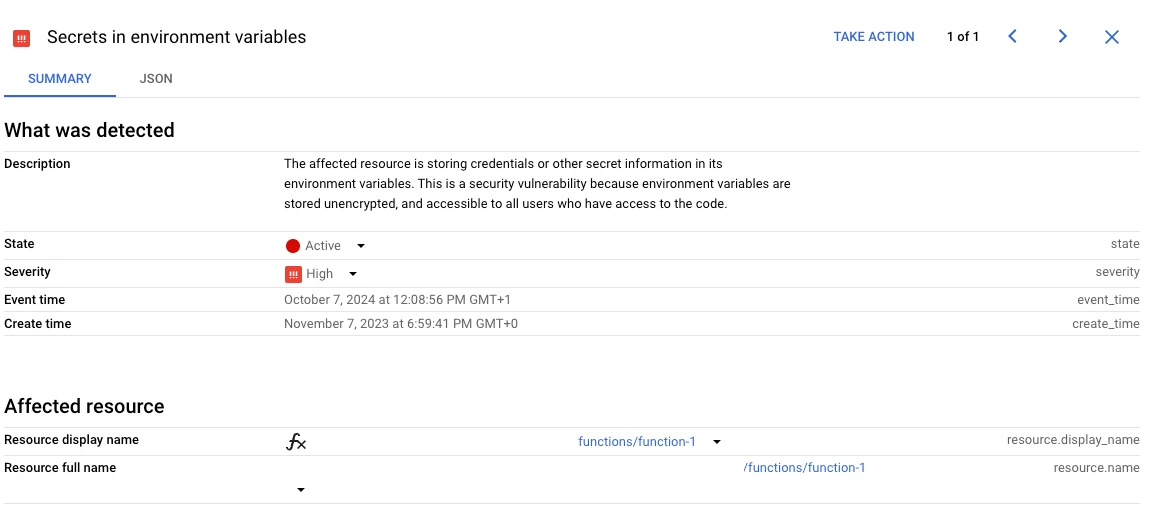
For Secrets in environment variables is looking for affected resource storing credentials or other secret information in its environment variables. This is a security vulnerability because environment variables are stored unencrypted, and accessible to all users who have access to the code. Any associate Findings should list the affected resource in question
For Block All Ingress these are items associated with the Policy Controller and the creation of Ingress Objects based on the BlockAllIngress policy template
https://cloud.google.com/kubernetes-engine/enterprise/policy-controller/docs/latest/reference/constraint-template-library#k8sblockallingress




