Your Red Team engagement found a vulnerability. Here’s how you can use Mandiant Security Validation to ensure it gets fixed.

The Mandiant Security Validation(MSV) platform is distinctly different from attack simulation technologies. Security validation includes vast integrations with defensive technologies and attack execution across the entire enterprise security environment. It is not limited to endpoint security controls. It uses real, active attack binaries to test the effectiveness of security controls.
MSV has the ability to create scheduled jobs and monitors. This provides a way to repeatedly test a vulnerability until it has been fixed and verify it stays fixed. The platform is open and allows users to create custom actions needed in their environment. The action types include: Host command line, port scan, DNS query, email, socket, network (PCAP based), web and cloud.
Here are a few examples that might be useful.

An open port in a firewall
The Red Team reports that a firewall port is open that should not be open.
Solution: Create a port scan action and schedule it to run between the affected network segments.
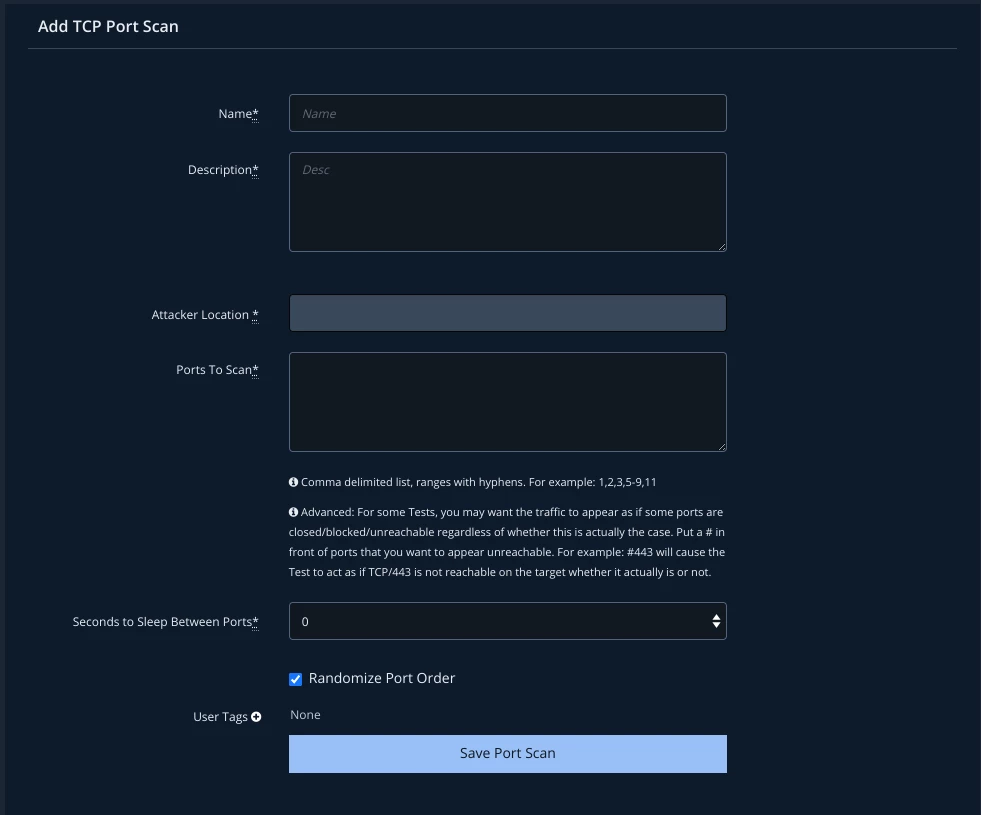
Simply fill out the form and a new action will be available to scan the ports. No need for a system with nmap or other networking tools.

Reverse shell or command and control traffic was not detected
The Red Team reports that they were able to establish command and control traffic out of a protected network.
Solution: Ask the Red Team for a PCAP of the network traffic that was generated. Then simply create and schedule a network action using the PCAP.
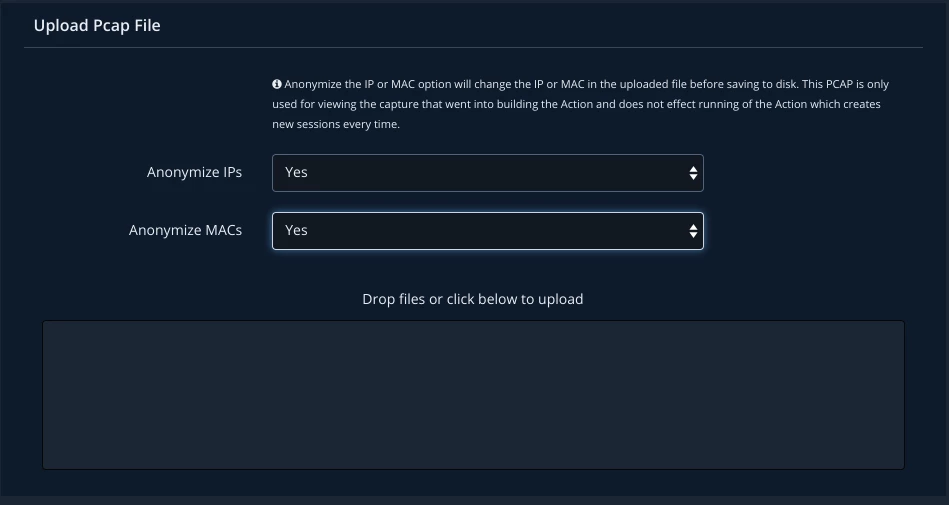
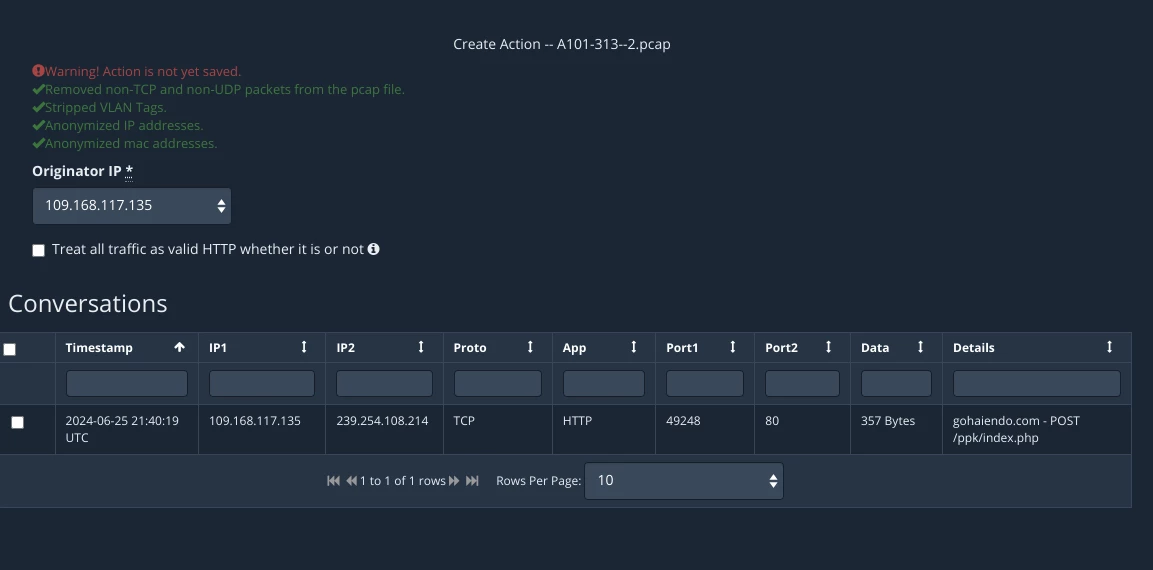
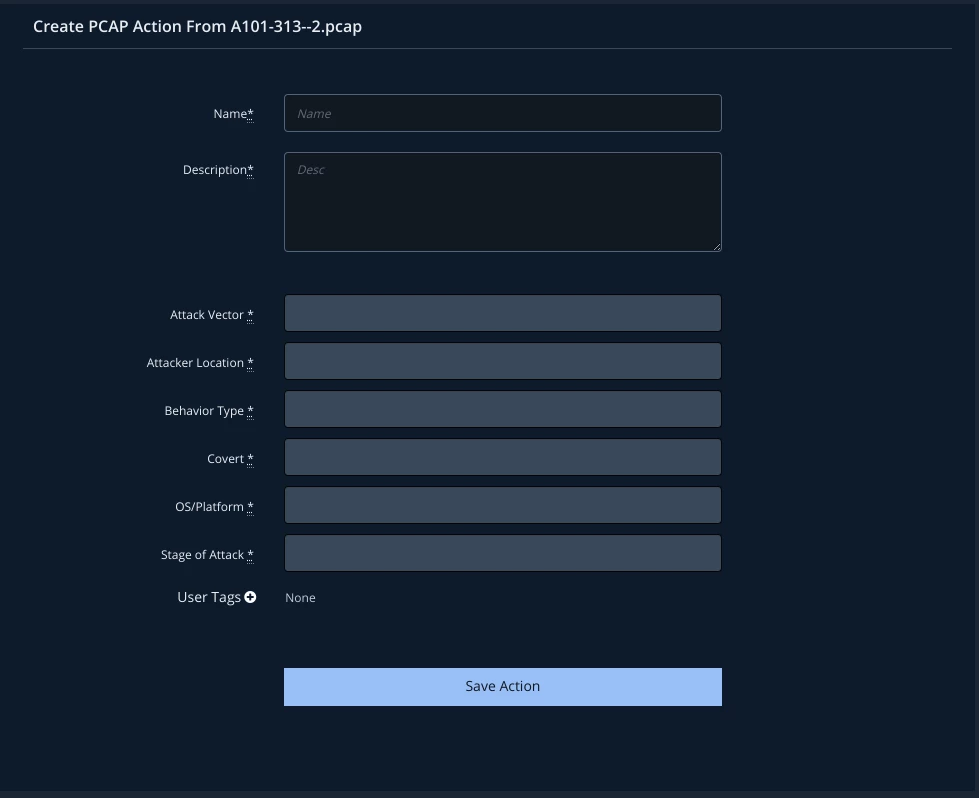

A document with embedded macros is not detected by the proxy
The Red Team reports that a PDF with embedded macros was downloaded successfully to a user endpoint.
Solution: Ask the Red Team for a copy of the file that was used. Upload the file to MSV. Then simply create and schedule a network action for a malicious file transfer. The transfer could be over any of numerous protocols: FTP, HTTP, HTTPS, etc.
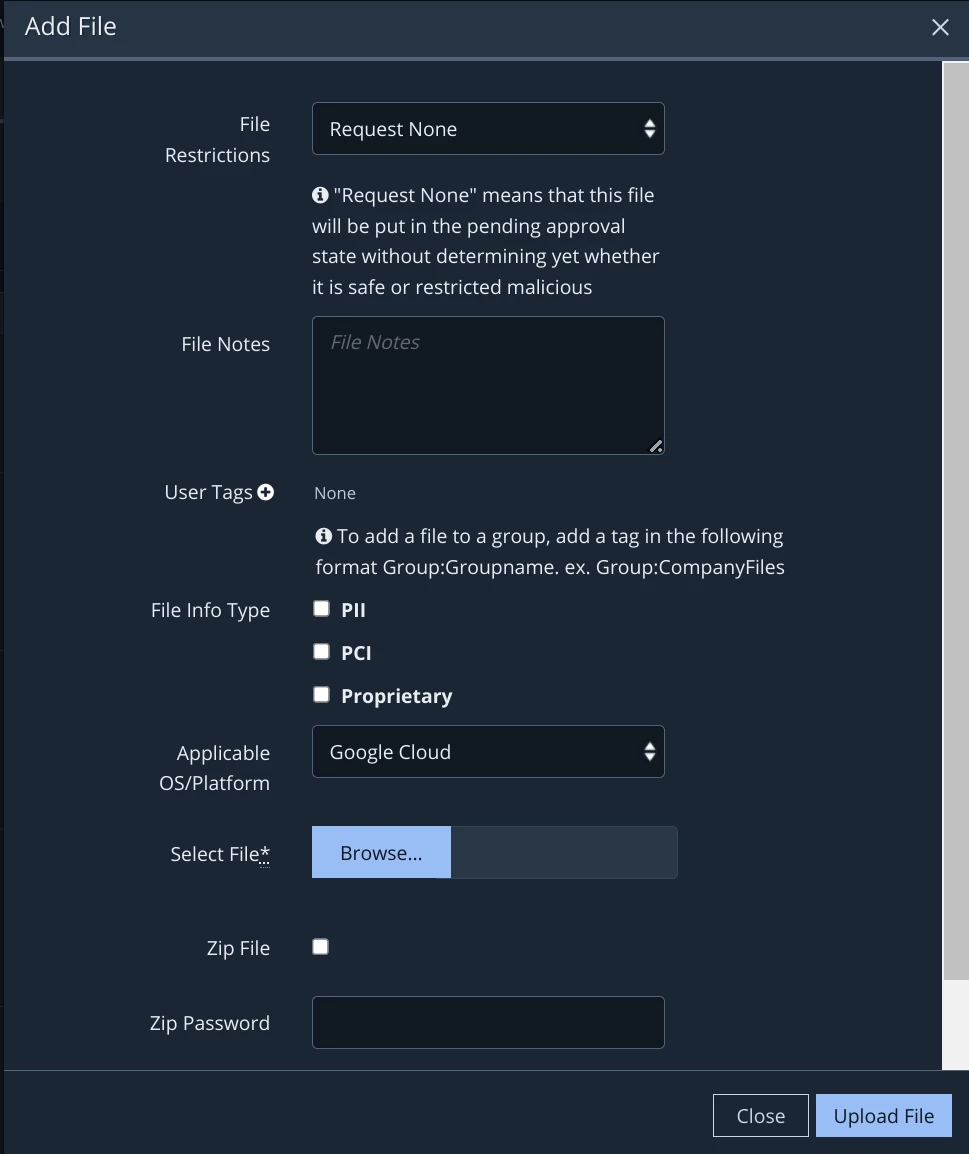
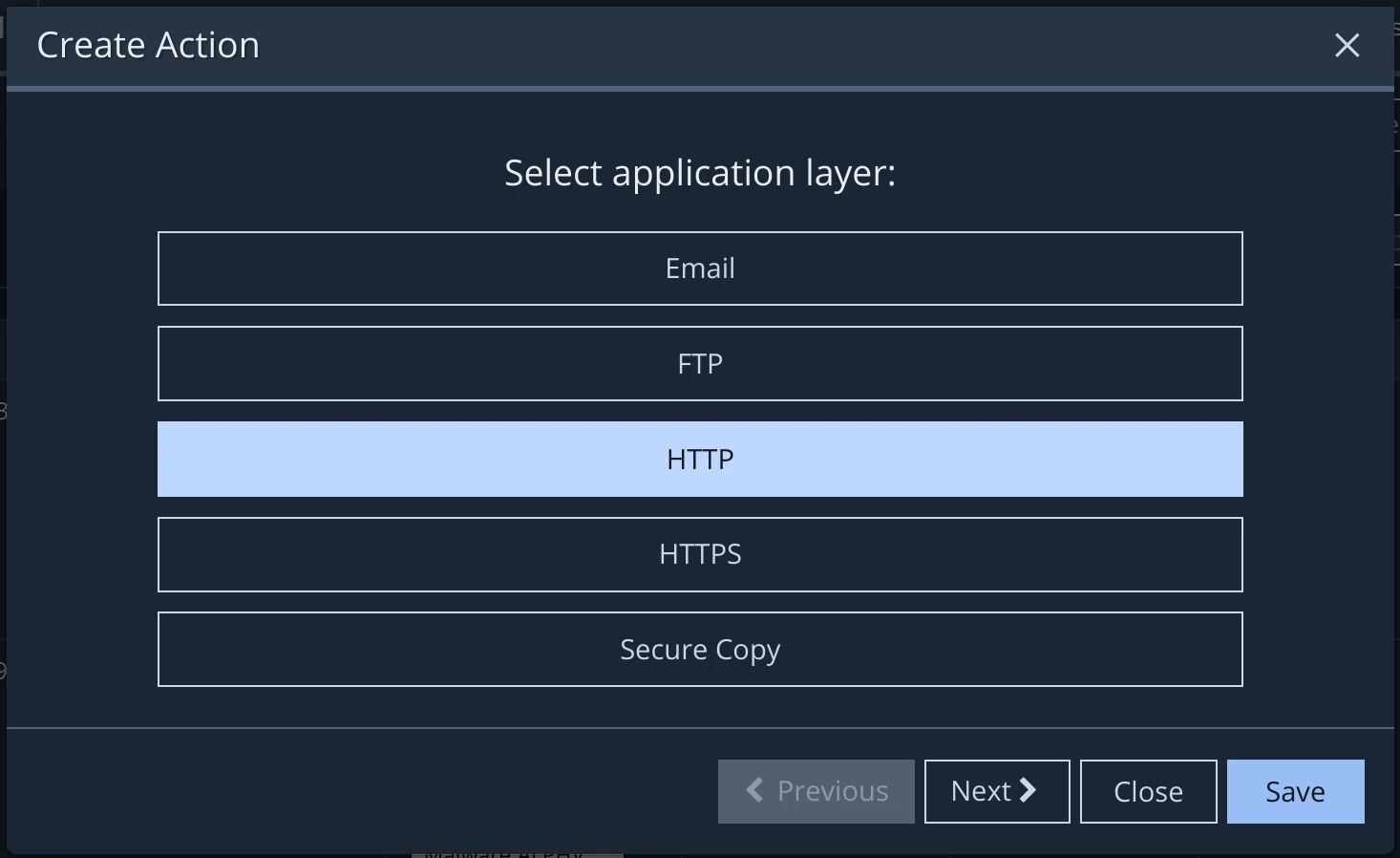
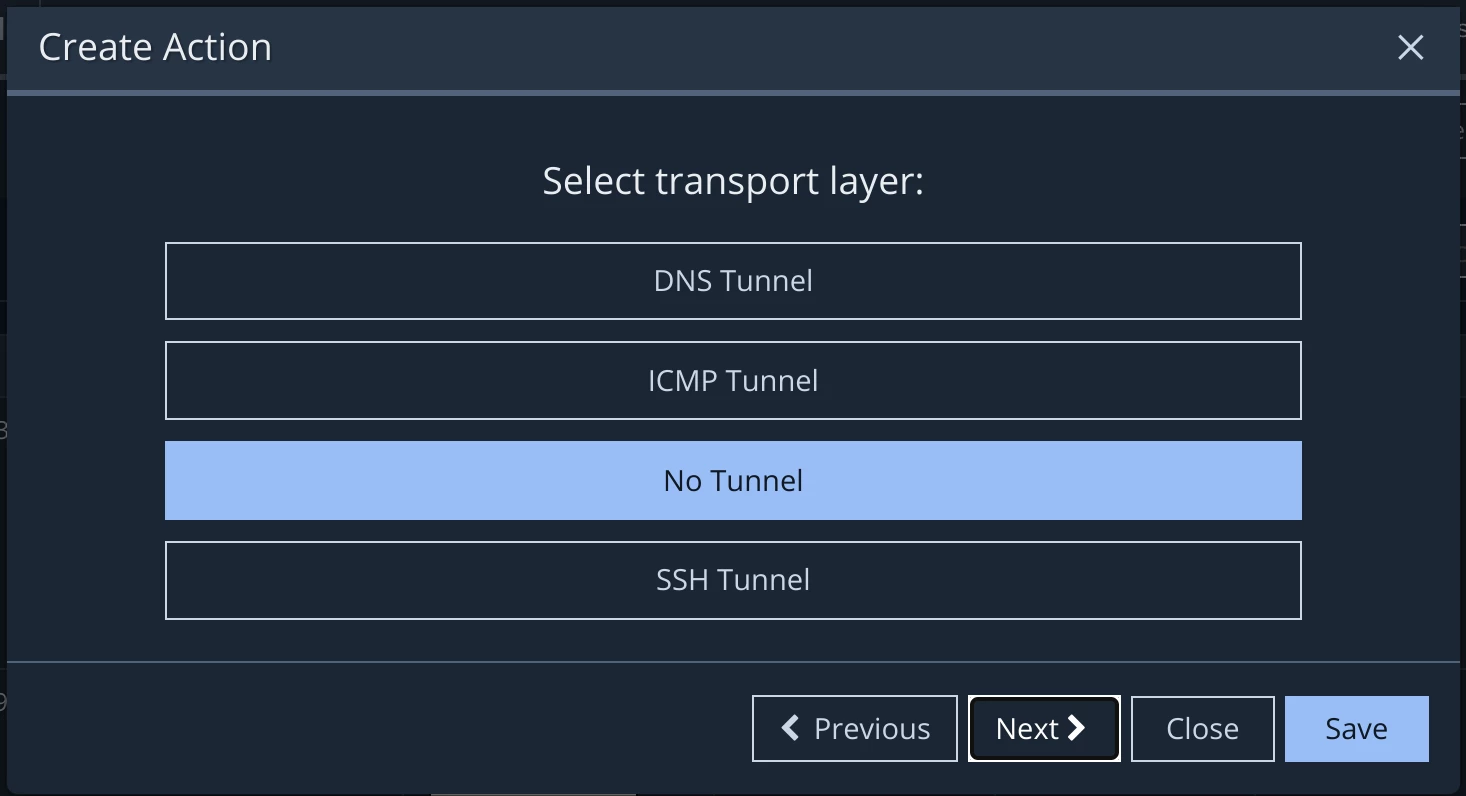
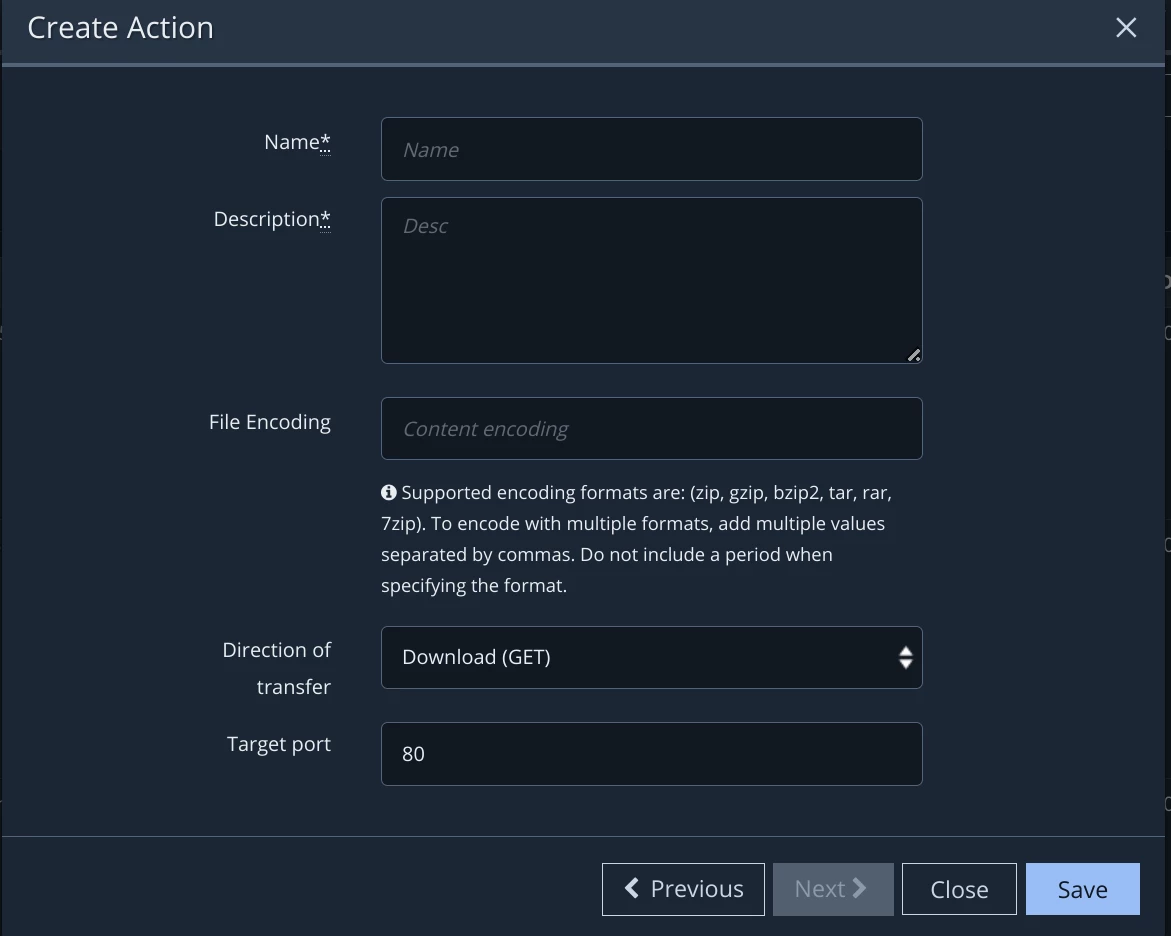
Scripts and executables can also be made into actions, see the blog post titled “Advanced Host CLI usage” for more information. Cloud configuration findings can also be made into actions, see the blog post titled, “Create your own Cloud Action” for more information.
In conclusion, the ability to test and retest Red Team findings is a great help to the overall security posture. Using Mandiant Security Validation, testing and retesting can be automated and ensure remediations are successful.


