Blog Authors:
Bhavana Bhinder - Google Cloud, Office of CISO HCLS Europe Lead
RK Neelakandan - Google Health Quality and Safety Engineering Lead
Odun Fadahunsi - Office of CISO Senior Security Risk and Compliance Advisor
GxP Resilience for Patient Safety and Business Continuity
In the Healthcare and Life sciences industries, speed saves lives, every decision, every data point, and every batch record can literally be the difference between life and death. For our life sciences customers from startups accelerating drug discovery to global pharmaceutical manufacturers - GxP resilience is the bedrock of their mission. It’s not just a feature; it's a regulatory necessity that also happens to be a massive competitive advantage.
The promise of the cloud, AI, and data analytics is to accelerate this journey at every step. GxP resilience is fundamentally important because it directly connects regulatory compliance with patient safety, business continuity and outcomes, and data stability. GxP resilience is not just a technological luxury; it is a foundational quality management principle that protects public health and secures the long-term viability of the business.
Historically, a powerful brake is often applied to this acceleration: the GxP validation process. For decades, it has been a manual, document-heavy ritual, serving as a critical guardrail to ensure only proven safe and effective changes are applied. While this diligence is paramount for patient safety, a single change to an application or underlying infrastructure can trigger weeks of re-validation, risk assessments, and a mountain of paperwork—all while innovation waits. The real challenge lies not in circumventing safety, instead in preserving and elevating it without impeding the agility essential for competition and innovation - all underpinned by resiliency.
Resilience—the ability to withstand, recover from, and adapt to disruption; is the core defense against costly fines, warning letters, facility shutdowns, product recalls, and, most importantly, patient harm resulting from compromised data or processes. This isn't just inefficient; it's a critical business risk. What if you could flip the script? What if your GxP compliance wasn't a manual process to be completed, rather an automated and resilient process, with verifiable outcome for the development lifecycle? A process that is inherently focused on ensuring the safe and effective production of drugs, accelerating insights, and maintaining patient safety, without the innovation-numbing bottlenecks of manual compliance.
The Solution: "Low-Code" Compliance Through Automation
On Google Cloud, we see customers embrace a new paradigm we call "low-code, high compliance." This isn't about drag-and-drop interfaces; it's about minimizing the error-prone, manual effort required to achieve and maintain a validated state. By codifying compliance requirements into automated, repeatable processes, you can build GxP systems that are resilient, auditable, and secure by design.
This approach leverages cloud-native tools to automate historically manual tasks, treating your GxP environment's configuration, deployment, and validation as code. This directly translates to faster deployments, lower risk of human error, and a state of continuous compliance that is transparent to auditors.
How-To: The Three Pillars of Automated GxP Compliance and Resilience
Here’s how you can implement this strategy on Google Cloud, focusing on the technical steps that underpin automated GxP resilience:
1. Build a Secure and Compliant Foundation with Infrastructure as Code (IaC)
The foundation of automated compliance is defining your entire GxP environment in code. This makes it repeatable, version-controlled, and auditable.
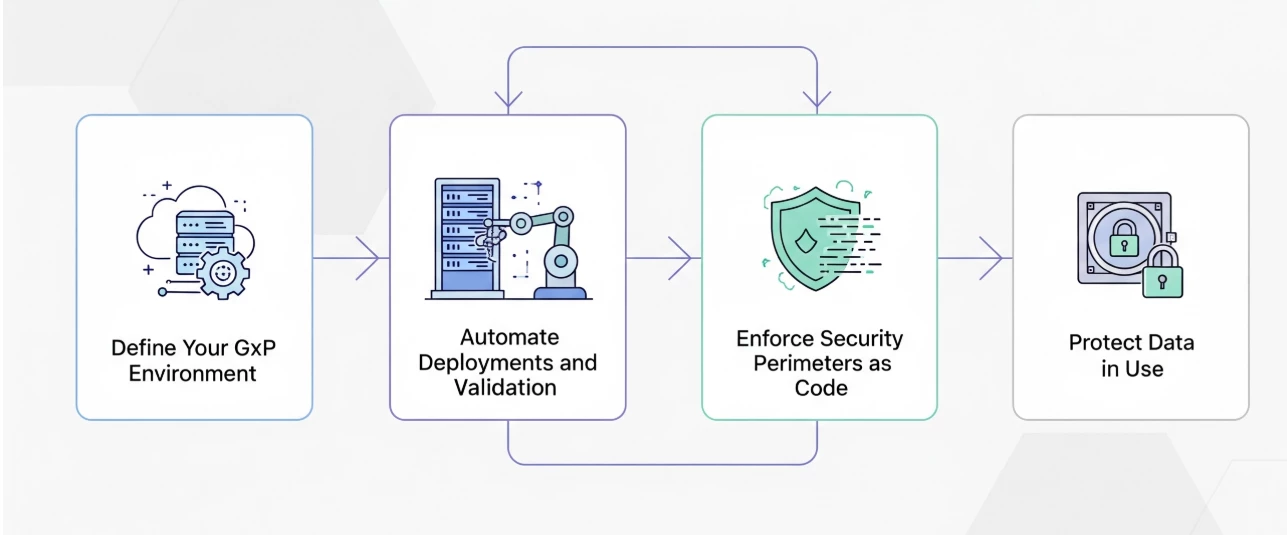
- Define Your GxP Environment: Use Infrastructure as Code (IaC) tools like Terraform to create verifiable configuration files for your GxP environment. Define your VPCs, subnets, firewall rules, and IAM policies in code. IaC (Terraform) templates should define not just what is built, but who can access it, using granular IAM policies. This directly supports the "Attributable" part of ALCOA++. It replaces manual setup guides with a single source of truth that can be peer-reviewed and stored in a version control system. By feeding Cloud Audit Logs, VPC Flow Logs, and other signals into a platform like Google Security Operations, you can automatically detect anomalous activity, such as unauthorized access attempts or data exfiltration patterns, that could signify a GxP non-conformance or a security breach. This transforms your audit log into active defense, enabling you to respond before a deviation becomes a critical incident.
- Automate Deployments and Validation: Use Cloud Build to automate IaC testing and deployment, making CI/CD pipeline a core part of your GxP change control. This ensures automated documentation and prevents unvalidated configurations from reaching production through integrated compliance checks. Additionally, secure your supply chain by using Artifact Registry and Binary Authorization. For example:
| Manual Patch Management (Before) A critical OS patch is required. This triggers a manual change control, weeks of revalidation, and a scheduled downtime window, all while the system remains vulnerable with potential GxP deviations. 
| Automated Patch Management (After) An automated new, patched VM image is released. The IaC pipeline automatically deploys it to a test environment, runs a pre-validated suite of automated tests (OQ/PQ), and, upon approval, performs a rolling update in production with zero downtime. The entire action is logged, auditable, and repeatable. 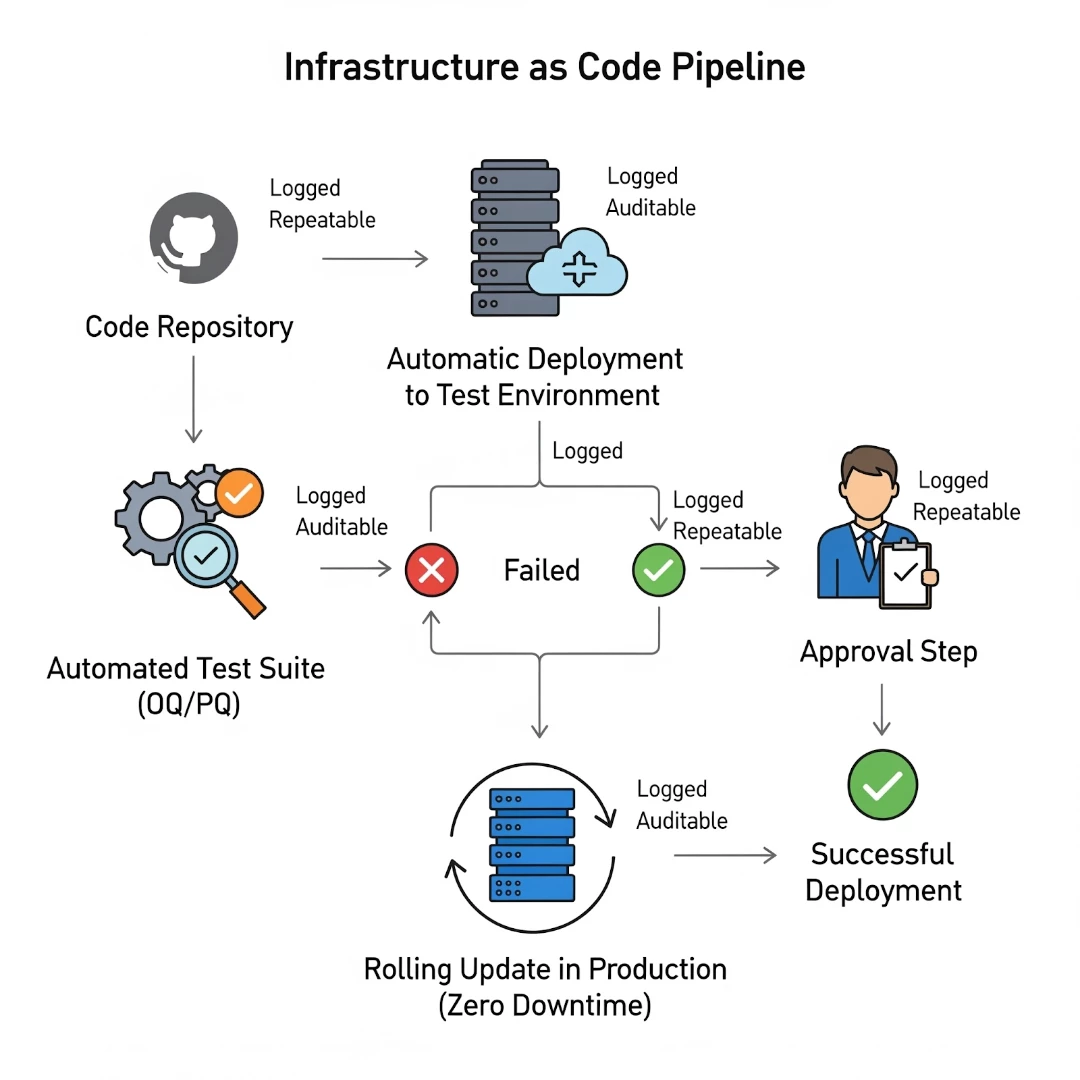
|
- Enforce Security Perimeters as Code: Go beyond traditional firewalls with VPC Service Controls. This feature can be configured via your IaC to create a cryptographic security perimeter around your sensitive GxP projects and data. It helps prevent data exfiltration by ensuring that services and data can only be accessed from within your trusted network boundary—a critical control for data integrity.
- Protect Data in Use: For collaborative research involving sensitive patient data, leverage Confidential Computing. This allows you to process data within a hardened, encrypted memory space, ensuring that even while in use, the data remains protected and inaccessible, even to cloud administrators. Utilise Isolator, a purpose built, secure collaboration solution on Google Cloud built with Chrome Enterprise Premium, Cloud Identity and a Terraform blueprint. It enables organizations to work with sensitive data in a controlled environment within Google Cloud. Isolator helps solve the problem of needing to give your cloud engineers, researchers, product teams, and anyone involved in a multi-party collaboration access to restricted data and tools when they are building solutions that involve sensitive information.
2. Ensure Data Integrity and Auditability (ALCOA++)
As process data is critical to making quality determinations on produced product, GxP’s prime directive is data integrity, often summarized by the ALCOA++ principles (Attributable, Legible, Contemporaneous, Original, Accurate, plus Complete, Consistent, Enduring, and Available). Google Cloud’s data services are built with foundational capabilities that directly support these requirements.
- Immutable and Enduring Records: Configure Google Cloud Storage buckets with retention policies and object versioning. This ensures that once data (like raw clinical trial results or lab instrument outputs) is written, it cannot be altered or deleted for a defined period, directly satisfying GxP requirements for original, unchangeable records.
- Complete and Attributable Audit Trails: Enable Cloud Audit Logs across your GxP projects. This service automatically records administrative activities and data access events across the vast majority of Google Cloud services (for a comprehensive list of services covered, refer to the Cloud Audit Logs documentation). These logs are immutable and provide the exhaustive, traceable "who, what, where, and when" audit trail required by regulators, without any manual setup.
- Governed AI/ML for Scientific Discovery: When using AI for scientific advancements like drug discovery or clinical trial optimization, GxP principles remain paramount. The entire lifecycle: training data, model development pipeline, and model outputs must be strictly governed and auditable. While services like BigQuery and Cloud Audit Logs provide the necessary data lineage to meet emerging regulations like the EU AI Act, organizations also need a definitive system of record for the model themselves. To achieve this, utilize Vertex AI Model Registry as your GxP-compliant ‘single source of truth’ for governance and compliance. Mirroring established IaC governance patterns, Vertex AI Model Registry allows you to version-control validated models, manage their lifecycle promotion (e.g. from ‘dev’ to ‘prod’), and maintain an audit trail. Crucially, it enables you to inextricably link each model version to its specific training data in BigQuery and its validation results, supporting rigorous quality management and documentation requirements.

3. Maintain Operational and Cyber Resilience
Google Cloud employs a comprehensive strategy to avoid service interruptions, prioritizing redundancy, automation, and continuous monitoring. We architect our infrastructure and services on the principle that failures are inevitable, designing systems that automatically recover and mitigate impact to users.
Resilience in a GxP context means more than just disaster recovery; it encompasses active cyber defense and service continuity, aligning with modern cybersecurity frameworks.
- Adhere to Global Resilience Mandates: Regulations like Europe's NIS2 Directive and frameworks like the NIST Cyber Security Framework (CSF) demand robust security and operational resilience for critical infrastructure. As a global, enterprise-grade cloud provider with a secure, geographically redundant network infrastructure, Google Cloud helps you meet these requirements.
- Architect for High Availability (HA) and Disaster Recovery (DR): Simply architecting for HA and DR is not enough; you must rigorously and continuously test it. Use Google Cloud's global footprint of regions and zones to design GxP workloads that can withstand regional outages. Architecting a multi-zone or multi-region deployment for a critical clinical or manufacturing system is vastly more accessible and cost-effective on the cloud than in traditional data centers, directly mitigating the risk of service disruption, data loss, or loss of operational control that could lead to GxP deviations and trigger extensive Corrective and Preventive Action (CAPA) processes. This ensures crucial services remain available to patients and researchers, and that data integrity is maintained even during adverse events.
True GxP resilience means proving your HA and DR design works as intended. Your automated CI/CD pipeline can be extended to periodically and safely conduct automated failure injection testing. By simulating a zonal or service failure in a validation environment, you can verifiably demonstrate, and document for an auditor, that your system fails over gracefully and maintains data integrity, transforming resilience from an architectural diagram into a tested, validated GxP control.
Regulatory compliance demands that any computerized system supporting GxP activities (such as batch release, clinical data management, or quality systems) must be backed by a robust Business Continuity Plan (BCP) and Disaster Recovery (DR) strategy. Services such as Google Cloud Backup and DR or automated snapshots for databases and Persistent Disks support the validation and systems ability to maintain a state of control during disruption. A GxP-compliant DR plan is only effective when validated and tested, This validation must be an automated, regularly tested, and auditable process that includes robust data backup and proven restoration procedures.
Conclusion: Your Next Steps to Automated Compliance
The fundamental core principles for modernizing GxP compliance:
- Treat Compliance as Code: Shift your mindset from writing static validation documents to defining your GxP environment using Infrastructure as Code (IaC). This makes your compliance posture version-controlled, auditable by default, and repeatable on demand.
- Automate Your Audit Trail: Integrate your IaC into a CI/CD pipeline using a tool like Cloud Build. This transforms GxP change control from a manual, multi-week process into a streamlined, verifiable workflow where every change is automatically tested and logged.
- Leverage Built-in Compliance Primitives: Google Cloud services like Cloud Audit Logs for traceability and Cloud Storage retention policies for data immutability are designed to meet core GxP data integrity (ALCOA++) requirements. Build on this foundation instead of reinventing the wheel.
- Focus on Science, Not Servers: By automating infrastructure validation, you free your most valuable resources—your scientists, engineers, and quality teams—to focus on accelerating research and improving patient outcomes, not on paperwork.
By embracing a "low-code, high compliance" approach on Google Cloud, life sciences organizations can transform GxP from a manual, time-consuming barrier into an automated, integrated part of their development lifecycle. This allows you to innovate faster, reduce compliance risk, and increase pace time-to-market all whilst resiliency becomes your catalyst.
Ready to start your journey?
- Check out our whitepaper on Google Cloud for GxP Systems.
- Read our AI GxP blogs: Achieve Validated AI, ALCOA++, Life Sciences Compliance for Your AI Model, Compliant Data Foundation for Life Sciences AI Demands. How Google Cloud Enables GxP Compliance in Life Sciences
- Explore how to get started with Infrastructure as Code on Google Cloud and Isolator.
Connect with a specialized Google Cloud life sciences partner to accelerate your GxP validation process.


