Blog Authors:
Tom Curry, Senior Security Consultant, Office of the CISO
Bob Mechler, Director, Office of the CISO
Telecommunication networks are the bedrock of our economy and society. They are not just complex; they are sprawling, ever-changing ecosystems of legacy and next-generation technologies. This complexity, combined with their status as critical national infrastructure, creates immense security challenges. The attack surface is vast, and the potential consequences of a breach or outage are severe.
For telecom operators, this creates a fundamental dilemma. How do you rigorously test your defenses, simulate sophisticated cyberattacks, and validate network resilience on a live network that cannot afford a single second of downtime? The answer is, you don’t. Disruptive testing in production is not an option when the live environment underpins emergency services, financial markets, and public utilities. Historically, telecom operators have relied on test networks - but they cannot reflect the scale, complexity or current state of live networks and are also expensive to maintain. A new paradigm is needed: one that allows for aggressive, continuous security validation in a perfectly replicated, safe-to-fail environment.
Meet the network digital twin
The solution to this dilemma lies in the concept of a network digital twin—a high-fidelity virtual replica of your entire telecoms network estate, that can be subjected to the most punishing scenarios without any risk to the live network. By continuously synchronizing with its real-world counterpart through real-time data feeds, the network digital twin mirrors the state, configuration, and behavior of the production environment.
Combining the network digital twin with agentic AI creates a good proving ground for security, as AI agents excel at reasoning within complex data environments. Security teams can finally move from theory to practice, enhancing their capabilities to keep pace with adversaries and evolving risks.
The following security use cases draw on Google’s experience of operating its own global network (one of the industry’s most advanced and resilient autonomous networks) as well as our learnings from deploying graph networks and AI within our security platforms.
- Continuously simulate attacks: Move beyond annual penetration tests by running automated "red team" exercises 24/7 to discover and validate attack paths before adversaries do. An “attack agent” can simulate thousands of realistic, multi-stage attacks in the network digital twin, emulating the tactics of sophisticated opponents, to find and prioritize security vulnerabilities within your network environment.
- Safely test security controls: Deploying or changing security controls (e.g. firewall changes) in the real network is vital for maintaining a strong security posture but can also introduce unintended consequences, including service outages. A “network change agent” can simulate these changes in the network digital twin to empirically measure their impact, reducing the risk of introducing new vulnerabilities or causing service disruptions.
- Evaluate BC/DR strategies: How will your production network cope if you lose power to a data center or a region, or if a storm takes out critical connectivity. With a network digital twin you can evaluate any number of scenarios to stress test your business continuity and disaster recovery plans and identify potential weaknesses - before a real disaster occurs.
- Enhance incident response: When a security threat or incident is detected in the real network, a rapid response is required, yet this can also have unknown or unintended consequences. A “response agent” can rapidly evaluate multiple remediation strategies within the network digital twin to find the most effective option with the least collateral damage—all before a single change is made to the production network.
The network digital twin fundamentally shifts the security posture from reactive to proactive, enabling telecom operators to answer the critical question, "How secure are we, really?" with empirical data rather than assumptions.
Implementing network digital twins in Google Cloud
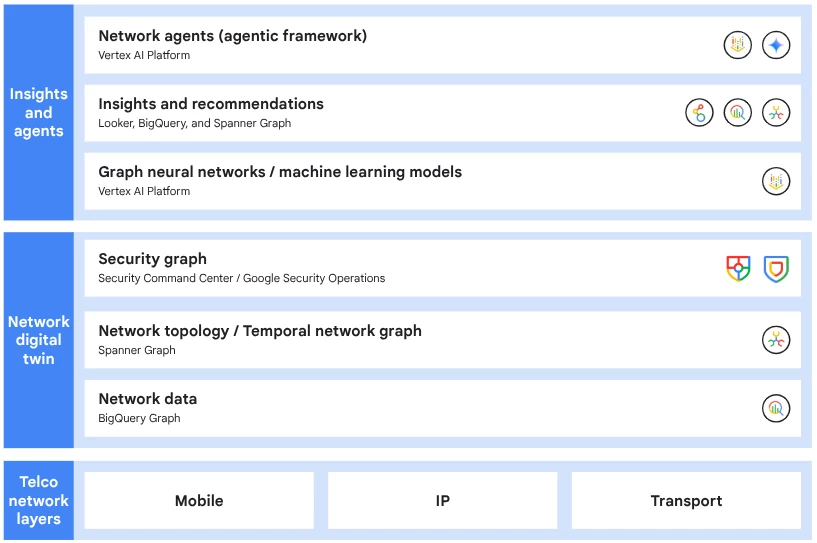
Realizing this vision of intelligent, autonomous security through network digital twins requires a platform that seamlessly integrates scalable infrastructure, data, and AI. Google Cloud provides a unique set of capabilities that enables customers to participate in this revolution.
- Digital twins are built upon graph networks. Cloud Spanner, with its native graph capabilities (Spanner Graph), offers a globally distributed database capable of modeling billions of relationships in a complex telecoms network at virtually unlimited scale, while maintaining strict consistency and high performance.
- The intelligence for network digital twins is provided by graph neural networks, a specialized and powerful class of deep learning models developed by Google DeepMind to work with graph networks. By processing the graph, AI can uncover hidden patterns, subtle behavioral anomalies and potential attack paths that are virtually invisible to conventional, rule-based security tools.
- This graph-based intelligence empowers agentic AI—autonomous AI systems capable of reasoning, planning and executing complex security tasks. These agents act as tireless security operators within the digital twin, performing high-value functions such as those described above.
- Vertex AI and Google's Gemini models provide the end-to-end platform for building, training, and deploying graph AI and autonomous AI agents, bringing the digital twin to life.
- Google’s Secure AI Framework provides guidance on security risks and controls that should be considered while deploying AI models, applications and agents.
This technology stack is already integrated within Google Cloud's Autonomous Network Operations framework, a telecoms-specific blueprint that leverages Google's decades of experience in running its own global network with AI-driven automation. The Autonomous Network Operations framework is already helping telcos achieve their goal of building autonomous network operations through network digital twins, graph AI and agentic workflows. The same framework could be extended to implement security-focussed use cases, by enriching the digital twin with security related data and developing new security agents.
This can be further complemented by Google Cloud’s unique security capabilities.
- Security Command Center uses its own security graph to identify risks and attack paths within a customer cloud environment. In addition to offering a proof of concept for use cases described here (for example, virtual red teaming and validating configuration changes), Security Command Center also includes a graph search feature.
- Google Security Operations, Google’s cloud-based SIEM and SOAR platform also leverages graph networks to correlate and enrich security alerts and related data including threat intelligence. Combining this with a network digital twin could unlock powerful threat hunting capabilities, including the potential to hunt for Advanced Persistent Threat (APT) adversaries using sophisticated techniques to operate “below the radar” of traditional security detection techniques.
- Google Threat Intelligence which provides unmatched visibility into the activities of threat actors, including tactics (TTPs), indicators (IoCs), campaigns, trends and much more. For any organization developing security agents, this is an invaluable resource.
Google has contributed MCP server implementations for Security Command Center, Google Security Operations and Google Threat Intelligence to the open-source community, opening up unlimited potential for innovation through customer-defined AI agents that can interact directly with these platforms as well as with the network digital twin.
Building the future of telecom security on Google Cloud
For telecom operators, the path to securing our most critical infrastructure is clear. By combining the risk-free simulation environment of a network digital twin with the deep relational insights of graph AI and the reasoning of AI agents, telcos can move beyond reactive defense and build the proactive, resilient, and autonomous networks of the future. Google Cloud provides the integrated and intelligent platform to make this future a reality.
To learn more, you can refer to this Autonomous Network Operations whitepaper, or contact your Google Cloud account team to start planning the implementation of your own network digital twin.


