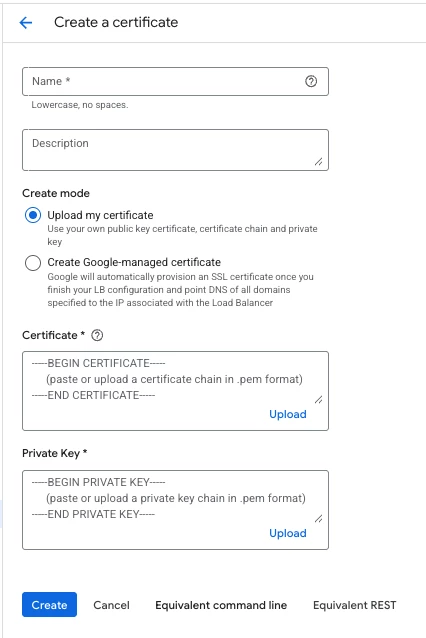
I am really surprised (rather appalled) to know GCP wants users to upload TLS Certificates and their private keys in to the Certificate Manager for being referenced by the services such as Application Load Balancers. Though its secured with encryption at rest, there are chances of unnecessary exposure by human error in handling the private keys at the first place and as a responsible CSP, I would expect GCP to do something about this.
At its face, it appeals to be a not-so-secure practice. I can understand even if the requirement is to upload PFX and password or even better an option to generate a CSR, that can be signed by an External CA and only the signed certificate need to be uploaded.
I want to hear the story on the side of GCP Engineering on their choice for users to upload private keys directly.
Though Certificate Manager is not a security product, I hope I can attract the attention of the Security Experts in contributing to this question.