Example 2: Process Enrichment
For the next example we will look at the resultant Process Enrichment that Process Aliasing provides.
Referring back to the Google SecOps documentation, beyond the mentioned target.product_specific_process_id there is also reference that the “Whole process; not just the indicator” is indexed for the target.process. Let’s explore in more detail what this means.
EDR indexed fields for process aliasing
When a process is launched, metadata such as command lines, file hashes, and parent process details are collected. The EDR software running on the machine assigns a vendor-specific process UUID.
The following table lists the fields that are indexed during a process launch event:
| UDM field | Indicator type |
| target.product_specific_process_id | PROCESS_ID |
| target.process | Whole process; not just the indicator |
I
In addition to the target.process field from the normalized event, Google SecOps also collects and indexes parent process information.
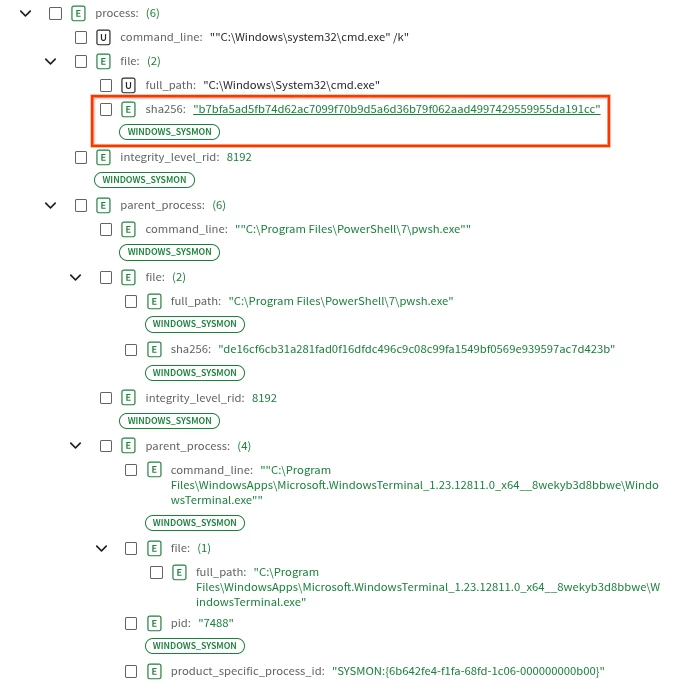
Following on from the prior timeout.exe process tree, there are several E(nriched) fields in the table, and this is Process Enrichment, adding all the original event’s target.process fields into associated process events.
| Enriched | UDM Key | UDM Value | Enrichment Source |
|----------|--------------------------------------------------------------|------------------------------------------------------------------|-------------------|
| U | principal.process.pid | 7524 | |
| E | principal.process.file.sha256 | b7bfa5ad5fb74d62ac7099f70b9d5a6d36b79f062aad4997429559955da191cc | WINDOWS_SYSMON |
| U | principal.process.file.full_path | C:\\Windows\\System32\\cmd.exe | |
| U | principal.process.command_line | \C:\\Windows\\system32\\cmd.exe\" /k" | |
| U | principal.process.product_specific_process_id | SYSMON:{6b642fe4-0598-68fe-f208-000000000b00} | |
| E | principal.process.parent_process.pid | 7084 | WINDOWS_SYSMON |
| E | principal.process.parent_process.file.full_path | C:\\Program Files\\PowerShell\\7\\pwsh.exe | WINDOWS_SYSMON |
| E | principal.process.parent_process.command_line | \C:\\Program Files\\PowerShell\\7\\pwsh.exe\"" | WINDOWS_SYSMON |
| E | principal.process.parent_process.product_specific_process_id | SYSMON:{6b642fe4-0594-68fe-f108-000000000b00} | WINDOWS_SYSMON |
| E | principal.process.integrity_level_rid | 8192 | WINDOWS_SYSMON |
| U | src.process.file.full_path | timeout.exe | |
| U | target.process.pid | 9184 | |
| U | target.process.file.sha256 | 106490870753d87d0c5a1b4fe83045a06518d415ec595bd1d0c30fe3ed4149c1 | |
| U | target.process.file.full_path | C:\\Windows\\System32\\timeout.exe | |
| U | target.process.command_line | timeout.exe /t 10 | |
| U | target.process.product_specific_process_id | SYSMON:{6b642fe4-059e-68fe-f308-000000000b00} | |
| U | target.process.integrity_level_rid | 8192 | |
| U | observer.process.pid | 9952 | |
Process Enrichment fields are usable in UDM Search and YARA-L Detection rules, which is a powerful and important feature to understand, as it means you can utilize consistent values that would not otherwise be in the original UDM event itself, e.g., you can run a UDM Search as follows, and it will match the UDM Event with the Process Enriched sha256 value
hash = "b7bfa5ad5fb74d62ac7099f70b9d5a6d36b79f062aad4997429559955da191cc"
Example of Process Aliasing & Enrichment
Let’s pivot to show another example of Process Enrichment but this time using Crowdstrike’s EDR. Here is an example CrowdStrike EDR raw log:
{
"IntegrityLevel": "8192",
"ParentProcessId": "15427753895",
"SourceProcessId": "15427753895",
"aip": "34.6.28.149",
"SHA1HashData": "0000000000000000000000000000000000000000",
"UserSid": "S-1-5-21-3644437979-728855135-3149758677-1000",
"event_platform": "Win",
"TokenType": "2",
"ProcessEndTime": "",
"AuthenticodeHashData": "30c643a1c081fdeebbecf152d64ca7a6bd7d198433bd6ce47455683ef433bb86",
"ParentBaseFileName": "winlogon.exe",
"EventOrigin": "1",
"ImageSubsystem": "2",
"id": "586be9b2-d6cf-4d7e-b438-8517a8d33a48",
"EffectiveTransmissionClass": "3",
"SessionId": "2",
"Tags": "41, 862, 874, 924, 1225, 1313, 1990, 12094627905582, 12094627906234",
"timestamp": "1761472981234",
"LocalAddressIP4": "10.164.0.5",
"event_simpleName": "ProcessRollup2",
"RawProcessId": "5960",
"ConfigStateHash": "1834585670",
"UserName": "admin",
"MD5HashData": "854e144c28736dd9f888deded85810e4",
"SHA256HashData": "257cb75fa8b9fd740584d0580ee40597d20b6c190bbc2e80f903a1d19183dc7e",
"AuthenticationId": "18275706",
"ConfigBuild": "1007.3.0020108.15",
"CommandLine": "C:\\Windows\\system32\\userinit.exe",
"ParentAuthenticationId": "18275706",
"TargetProcessId": "15483458681",
"ImageFileName": "\\Device\\HarddiskVolume3\\Windows\\System32\\userinit.exe",
"SourceThreadId": "186772304093",
"Entitlements": "15",
"name": "ProcessRollup2V19",
"ProcessStartTime": "1761472980.763",
"ComputerName": "WIN-SRV-01",
"Attacks": [
{
"Tactic": "Execution",
"Technique": "User Execution"
}
],
"aid": "120092c7157c4b5e81c38fca2964f260",
"SignInfoFlags": "32768",
"cid": "7015a549d5a5464f894353a509408606"
}
And now to view the same raw log as seen as a UDM event:
| Enriched | UDM Key | UDM Value | Enrichment Source |
| U | metadata.product_log_id | 586be9b2-d6cf-4d7e-b438-8517a8d33a48 | |
| U | metadata.event_timestamp.seconds | 1761472981 | |
| U | metadata.event_timestamp.nanos | 234000000 | |
| U | metadata.event_type | PROCESS_LAUNCH | |
| U | metadata.vendor_name | Crowdstrike | |
| U | metadata.product_name | Falcon | |
| U | metadata.product_event_type | ProcessRollup2 | |
| U | metadata.description | ProcessRollup2V19 | |
| U | metadata.ingested_timestamp.seconds | 1761473707 | |
| U | metadata.ingested_timestamp.nanos | 655271000 | |
| U | metadata.product_deployment_id | 7015a549d5a5464f894353a509408606 | |
| U | metadata.id | b"AAAAAEiWvQWkihlz/y0VHOwh2ZEAAAAABgAAAG4CAAA | |
| U | metadata.log_type | CS_EDR | |
| U | metadata.base_labels.log_types | CS_EDR | |
| U | metadata.base_labels.allow_scoped_access | TRUE | |
| E | metadata.enrichment_labels.log_types | CS_EDR | Crowdstrike EDR |
| E | metadata.enrichment_labels.allow_scoped_access | TRUE | Crowdstrike EDR |
| U | metadata.parser_version | 19 | |
| U | principal.hostname | win-srv-01 | |
| U | principal.asset_id | CS:120092c7157c4b5e81c38fca2964f260 | |
| U | principal.user.userid | admin | |
| U | principal.user.windows_sid | S-1-5-21-3644437979-728855135-3149758677-1000 | |
| E | principal.process.pid | 1560 | Crowdstrike EDR |
| E | principal.process.file.sha256 | cacbb90adfc073fafc8e1036f39ebc5148b7bce1e97bc882211d53667de528e3 | Crowdstrike EDR |
| E | principal.process.file.md5 | 1494f9aa83791a4f588122a539702f7f | Crowdstrike EDR |
| E | principal.process.file.full_path | \\Device\\HarddiskVolume3\\Windows\\System32\\winlogon.exe | Crowdstrike EDR |
| U | principal.process.file.names | winlogon.exe | |
| E | principal.process.file.authentihash | 22c5fbf4bc9800533a95fee12b5109e3a9fca421 | Crowdstrike EDR |
| E | principal.process.command_line | winlogon.exe {F4205A0B-6E93-4E2D-A187-5C9597630000} | Crowdstrike EDR |
| U | principal.process.product_specific_process_id | CS:7015a549d5a5464f894353a509408606:120092c7157c4b5e81c38fca2964f260:15427753895 | |
| E | principal.process.parent_process.file.names | smss.exe | Crowdstrike EDR |
| E | principal.process.parent_process.product_specific_process_id | CS:7015a549d5a5464f894353a509408606:120092c7157c4b5e81c38fca2964f260:15424793163 | Crowdstrike EDR |
| U | principal.ip | 10.164.0.5 | |
| U | principal.nat_ip | 34.6.28.149 | |
| U | principal.asset.hostname | win-srv-01 | |
| U | principal.asset.asset_id | CS:120092c7157c4b5e81c38fca2964f260 | |
| U | principal.asset.ip | 10.164.0.5 | |
| U | principal.asset.hardware.manufacturer | | |
| U | src.process.product_specific_process_id | CS:15427753895 | |
| U | src.labels.key | source_thread_id | |
| U | src.labels.value | 186772304093 | |
| U | target.process.pid | 5960 | |
| U | target.process.file.sha256 | 257cb75fa8b9fd740584d0580ee40597d20b6c190bbc2e80f903a1d19183dc7e | |
| U | target.process.file.md5 | 854e144c28736dd9f888deded85810e4 | |
| U | target.process.file.full_path | \\Device\\HarddiskVolume3\\Windows\\System32\\userinit.exe | |
| U | target.process.file.authentihash | 30c643a1c081fdeebbecf152d64ca7a6bd7d198433bd6ce47455683ef433bb86 | |
| U | target.process.command_line | C:\\Windows\\system32\\userinit.exe | |
| U | target.process.product_specific_process_id | CS:7015a549d5a5464f894353a509408606:120092c7157c4b5e81c38fca2964f260:15483458681 | |
| E | target.process.parent_process.pid | 1560 | Crowdstrike EDR |
| E | target.process.parent_process.file.sha256 | cacbb90adfc073fafc8e1036f39ebc5148b7bce1e97bc882211d53667de528e3 | Crowdstrike EDR |
| E | target.process.parent_process.file.md5 | 1494f9aa83791a4f588122a539702f7f | Crowdstrike EDR |
| E | target.process.parent_process.file.full_path | \\Device\\HarddiskVolume3\\Windows\\System32\\winlogon.exe | Crowdstrike EDR |
| E | target.process.parent_process.file.authentihash | 22c5fbf4bc9800533a95fee12b5109e3a9fca421 | Crowdstrike EDR |
| E | target.process.parent_process.command_line | winlogon.exe {F4205A0B-6E93-4E2D-A187-5C9597630000} | Crowdstrike EDR |
| E | target.process.parent_process.product_specific_process_id | CS:7015a549d5a5464f894353a509408606:120092c7157c4b5e81c38fca2964f260:15427753895 | Crowdstrike EDR |
| E | target.process.parent_process.parent_process.file.names | smss.exe | Crowdstrike EDR |
| E | target.process.parent_process.parent_process.product_specific_process_id | CS:7015a549d5a5464f894353a509408606:120092c7157c4b5e81c38fca2964f260:15424793163 | Crowdstrike EDR |
| U | target.labels.key | sign_info_flags | |
| U | target.labels.value | SIGNATURE_FLAG_NO_EMBEDDED_CERT | |
| U | target.labels.key | tags | |
| U | target.labels.value | 41, 862, 874, 924, 1225, 1313, 1990, 12094627905582, 12094627906234 | |
| U | target.labels.key | process_start_time | |
| U | target.labels.value | 1761472981 | |
| U | about.resource.resource_type | CLOUD_ORGANIZATION | |
| U | about.resource.product_object_id | 7015a549d5a5464f894353a509408606 | |
| U | about.labels.key | entitlements | |
| U | about.labels.value | 15 | |
| U | about.labels.key | effective_transmission_class | |
| U | about.labels.value | 3 | |
| U | about.labels.key | config_build | |
| U | about.labels.value | 1007.3.0020108.15 | |
| U | about.labels.key | ConfigStateHash | |
| U | about.labels.value | 1834585670 | |
| U | about.labels.key | image_subsystem | |
| U | about.labels.value | 2 | |
| U | security_result.about.labels.key | AuthenticationId | |
| U | security_result.about.labels.value | 18275706 | |
| U | security_result.about.labels.key | token_type | |
| U | security_result.about.labels.value | IMPERSONATION_TOKEN | |
| U | security_result.about.labels.key | integrity_level | |
| U | security_result.about.labels.value | MEDIUM | |
| U | security_result.about.labels.key | parent_authentication_id | |
| U | security_result.about.labels.value | 18275706 | |
| U | network.session_id | 2 |
We can see in many cases a one to one mapping of original raw log fields into UDM; however, if we analyze the UDM version in more depth, we see the powerful results of Process Enrichment, which is enabled by aliasing.
Google SecOps was able to add additional key value data into the principal.process.file.* and target.process.parent_process.file.* by correlating the principal.process.parent_process.product_specific_process_id value (CS:7015a549d5a5464…) against the target.process.parent_process.product_specific_process_id.
It is also important to understand the Process Aliasing and Enrichment feature is not just applicable to UDM Event Types of PROCESS_LAUNCH, rather it will apply to any UDM Event Type with Process data, for example a NETWORK_CONNECTION or a REGISTRY_CREATED event.
For example, here is an original raw log for a CrowdStrike NetworkConnectIP4 event:
{
"ContextBaseFileName": "MpDefenderCoreService.exe",
"aip": "34.31.105.68",
"event_platform": "Win",
"EventOrigin": "1",
"id": "6e284d1b-2c2d-4baa-95ea-4a4c8f7909b7",
"Protocol": "6",
"EffectiveTransmissionClass": "3",
"InContext": "0",
"timestamp": "1761740838475",
"LocalAddressIP4": "10.0.10.3",
"event_simpleName": "NetworkConnectIP4",
"ContextTimeStamp": "1761740837.923",
"ConfigStateHash": "2379858933",
"ConnectionFlags": "0",
"ContextProcessId": "313614810682",
"RemotePort": "443",
"ConfigBuild": "1007.3.0019909.15",
"LocalPort": "51537",
"Entitlements": "15",
"name": "NetworkConnectIP4V13",
"ComputerName": "WINDOWS-KK",
"Attacks": [
{
"Tactic": "Command and Control",
"Technique": "Application Layer Protocol"
}
],
"aid": "36aa340a3674438090696e3e3906419a",
"RemoteAddressIP4": "20.50.80.214",
"RemoteAddressString": "20.50.80.214:443",
"ConnectionDirection": "0",
"cid": "7015a549d5a5464f894353a509408606"
}
Read more: Adoption Guide: Process Aliasing & Enrichment in Google SecOps - Part 3


