Hello everyone,
I'm reaching out to see if anyone has encountered similar challenges or has insights to share regarding monitoring and alerting on the health of log ingestion in Google SecOps.
Here's a bit of context: We've set up a Cloud Function that queries our BigQuery table for information related to Google SecOps ingestion. We then import this data using the event import API : https://cloud.google.com/chronicle/docs/reference/rest/v1alpha/projects.locations.instances.events/import
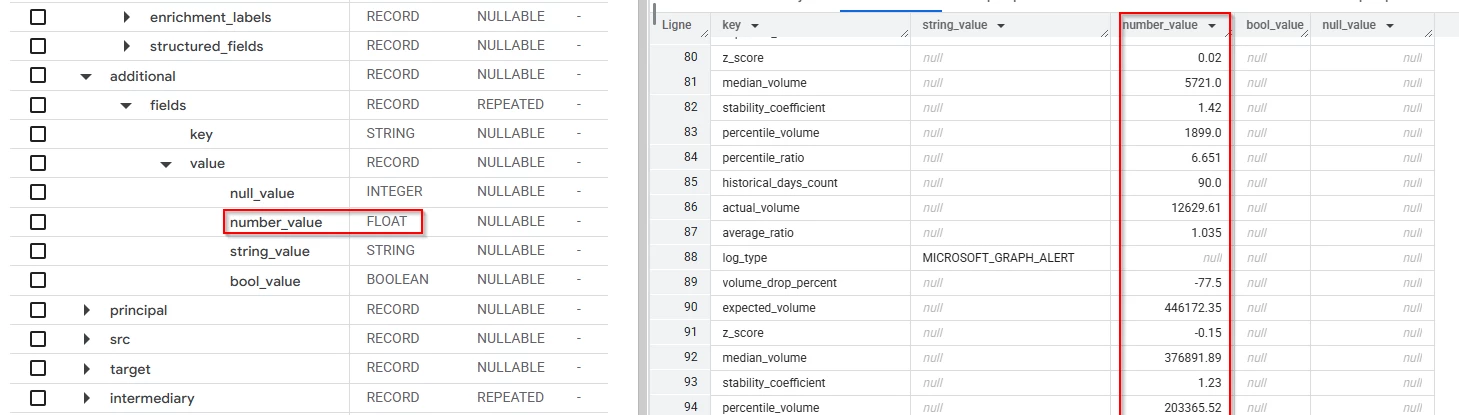
So far, everything works smoothly until we try to implement alerting rules on this data. The UDM events we are dealing with look like this :
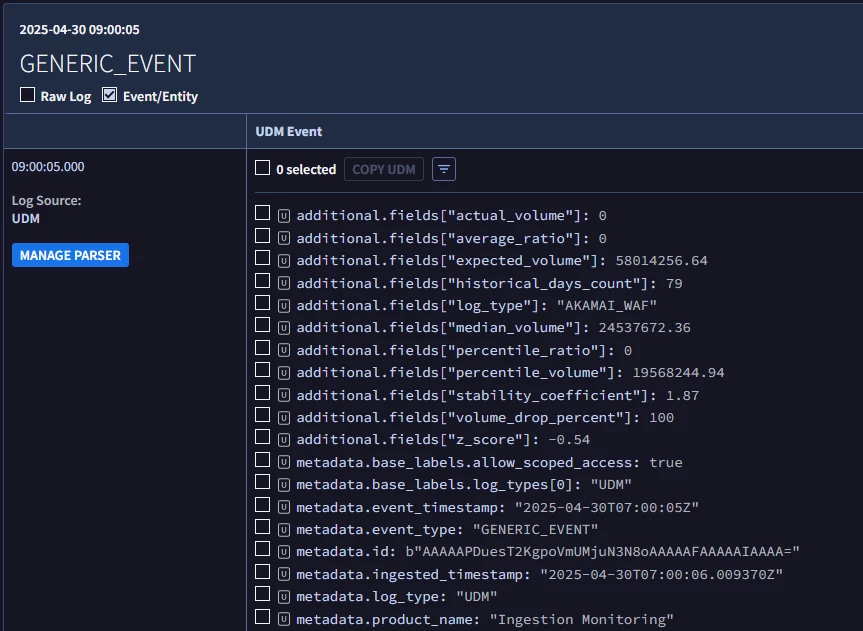
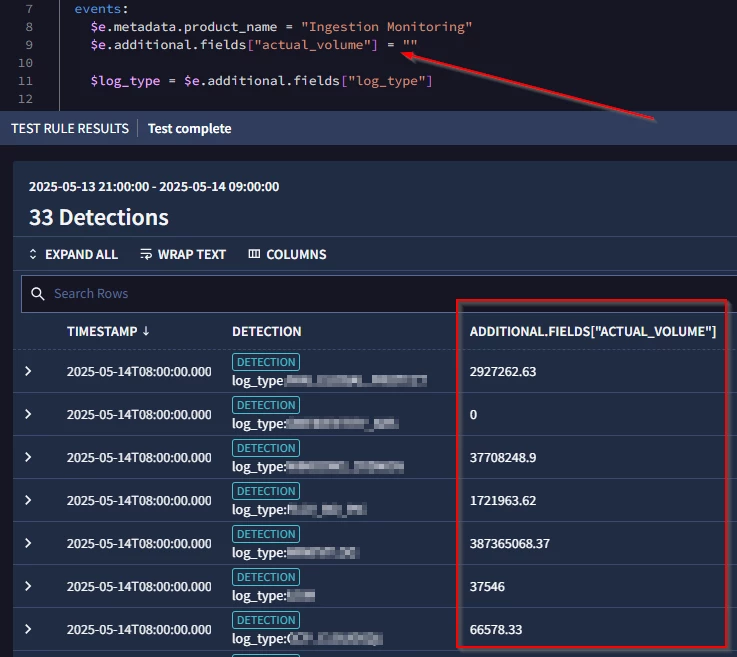
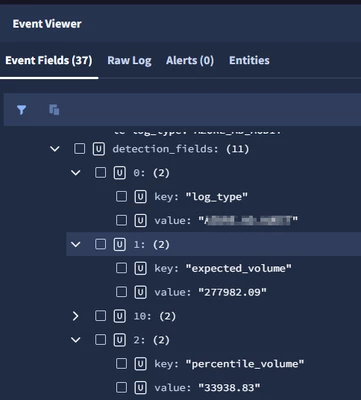
The useful information is placed in the additional fields of the UDM. However, it seems that the SIEM struggles to process these fields as strings or floats. For instance, I can't compare these numeric values, even if I cast them as floats beforehand :
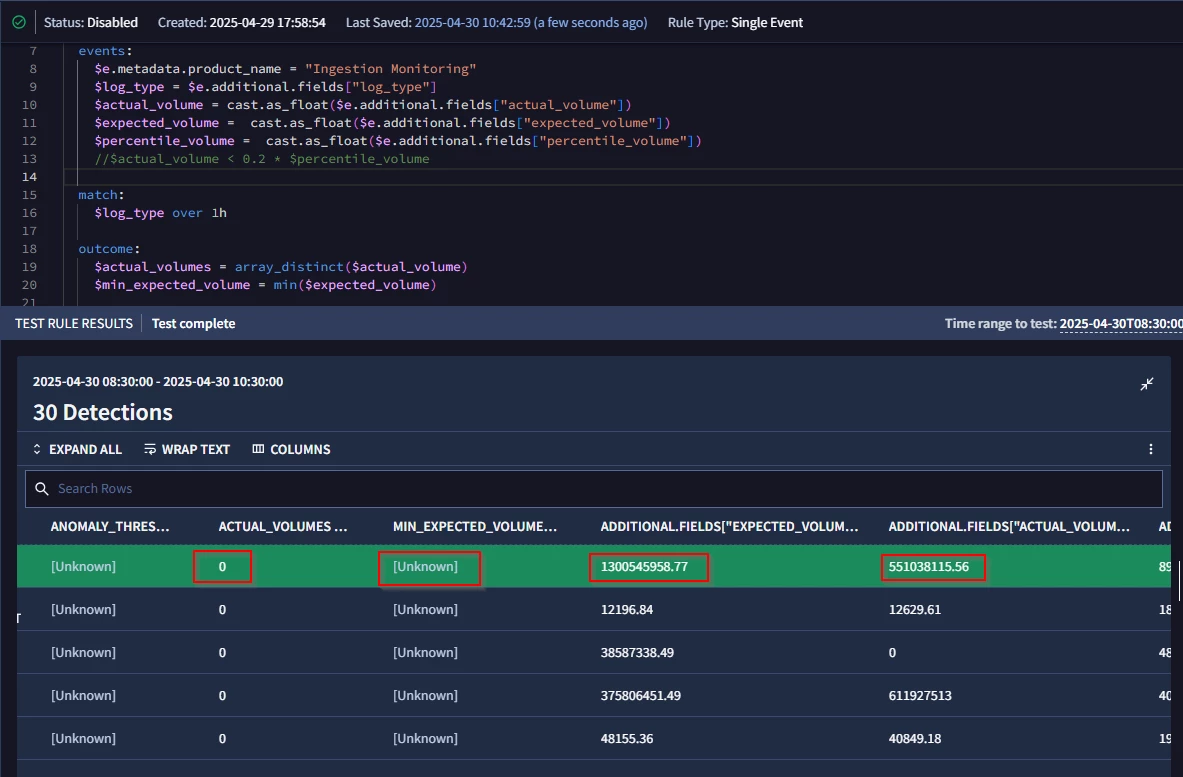
I suspect this issue might be due to the use of additional fields, which are the only ones without a specified type in the API documentation (type: object): https://cloud.google.com/chronicle/docs/reference/rest/Shared.Types/UDM
- Has anyone else faced this problem?
- How do you handle numeric comparisons from additional fields?
- Or could the issue be stemming from something else
Any advice would be greatly appreciated! Thank you!