Hi,
We've defined an AuditD Collector (10.0.0.47, UDP Port 517) in our Forwarder and send from our Linux (Ubuntu) servers the auth and authpriv logs to it:
auth,authpriv.* @10.0.0.47:517
Using Ngrep, we can see that the information is delivered to the Forwarder:
#
U 2024/11/11 11:17:01.332098 10.0.0.40:57666 -> 10.0.0.47:517 #46
<86>Nov 11 11:17:01 NUC CRON[32165]: pam_unix(cron:session): session opened for user root by (uid=0)
#
U 2024/11/11 11:17:01.335629 10.0.0.40:57666 -> 10.0.0.47:517 #47
<86>Nov 11 11:17:01 NUC CRON[32165]: pam_unix(cron:session): session closed for user root
#
U 2024/11/11 11:17:28.353498 10.0.0.40:57666 -> 10.0.0.47:517 #49
<38>Nov 11 11:17:28 NUC sshd[32546]: Connection from 10.0.10.4 port 50945 on 10.0.0.40 port 22
#
U 2024/11/11 11:17:28.502930 10.0.0.40:57666 -> 10.0.0.47:517 #50
<38>Nov 11 11:17:28 NUC sshd[32546]: Failed none for jlxx from 10.0.10.4 port 50945 ssh2
#
U 2024/11/11 11:17:35.633694 10.0.0.40:57666 -> 10.0.0.47:517 #52
<38>Nov 11 11:17:35 NUC sshd[32546]: Accepted password for jlxx from 10.0.10.4 port 50945 ssh2
#
U 2024/11/11 11:17:35.634912 10.0.0.40:57666 -> 10.0.0.47:517 #53
<86>Nov 11 11:17:35 NUC sshd[32546]: pam_unix(sshd:session): session opened for user jlxx by (uid=0)
#
U 2024/11/11 11:17:35.637395 10.0.0.40:57666 -> 10.0.0.47:517 #54
<38>Nov 11 11:17:35 NUC systemd-logind[923]: New session 21954 of user jlxx.
#
U 2024/11/11 11:17:35.695734 10.0.0.40:57666 -> 10.0.0.47:517 #55
<38>Nov 11 11:17:35 NUC sshd[32546]: User child is on pid 32624
#
U 2024/11/11 11:17:35.930106 10.0.0.40:57666 -> 10.0.0.47:517 #56
<38>Nov 11 11:17:35 NUC sshd[32624]: Starting session: shell on pts/3 for jlxx from 10.0.10.4 port 50945 id 0
#
U 2024/11/11 11:17:44.436399 10.0.0.40:57666 -> 10.0.0.47:517 #57
<85>Nov 11 11:17:44 NUC sudo: jlxx : TTY=pts/3 ; PWD=/home/jlxx ; USER=root ; COMMAND=/bin/bash
#
U 2024/11/11 11:17:44.436594 10.0.0.40:57666 -> 10.0.0.47:517 #58
<86>Nov 11 11:17:44 NUC sudo: pam_unix(sudo:session): session opened for user root by jlxx(uid=0)
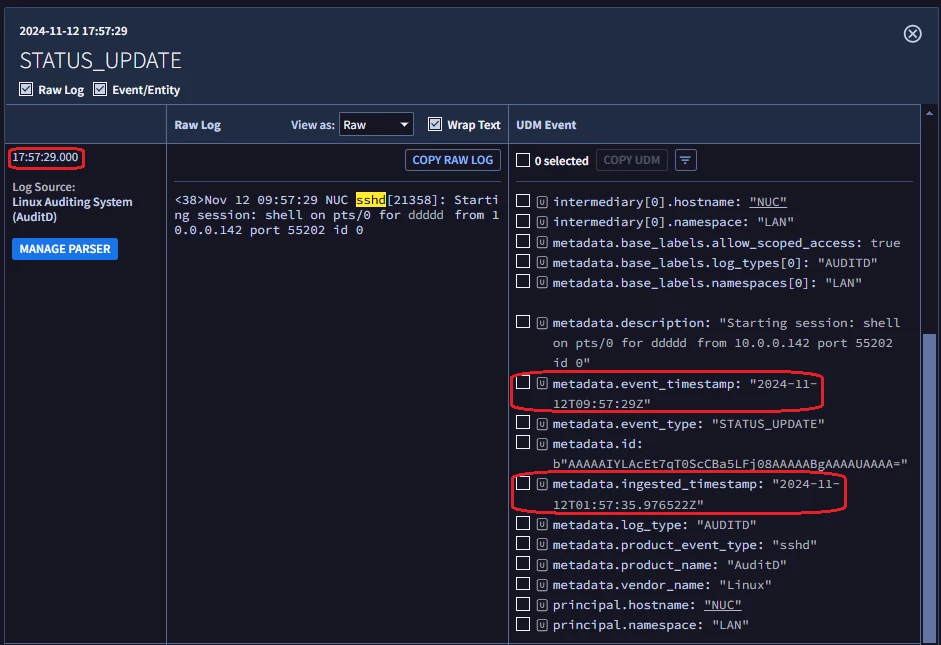
In the Raw Log Search, we only see those logins triggered by the CRON job (1st & 2nd entries in the Ngrep) and can't see all the other entries owned by sshd, sudo...
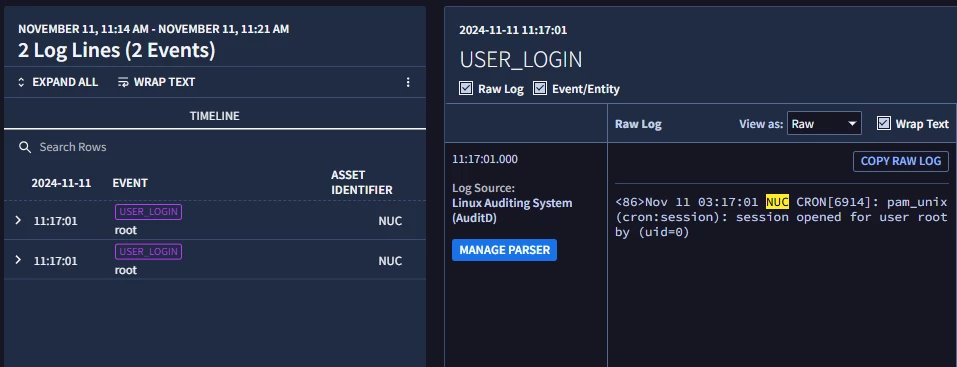
What's the reason we're not seeing the other entries?
Thanks