Hello Security Community Members,
I hope you’re all doing well!
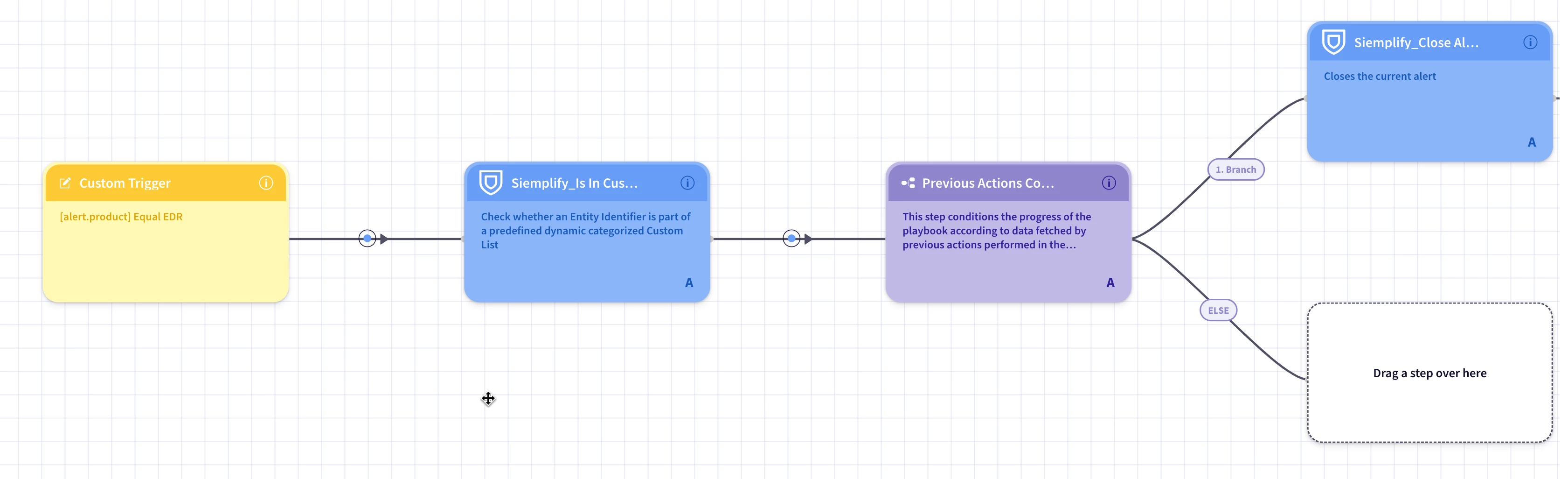
We are currently working on improving our Endpoint Detection and Response process. We want to use manual analysis for some events or alerts and add summaries of false positive hash values to a custom list for future reference.
The idea is that if we encounter the same event with the same hash value in the future, we’d like to pull that analysis from our custom list instead of doing the manual work all over again.
I’m looking for some guidance on how to set this up in our SOAR playbook. Specifically:
- How can we configure the playbook to first check the custom list when an alert is triggered?
- What’s the best way to implement the logic that allows us to either reference the analysis from the custom list or continue with our normal incident response process? (but first look into custom list)
- Are there specific conditions we should use to make this work smoothly?
I’d appreciate any tips or examples from anyone who has done something similar.
Thanks so much for your help!
Thanks,