Hi Team,
I have a project in that I need to run automated IP/URLs/Hash block to firewalls but due to some compliance issues I can not integrate SOAR directly with Firewalls and IOC feed can be implemented at firewalls.
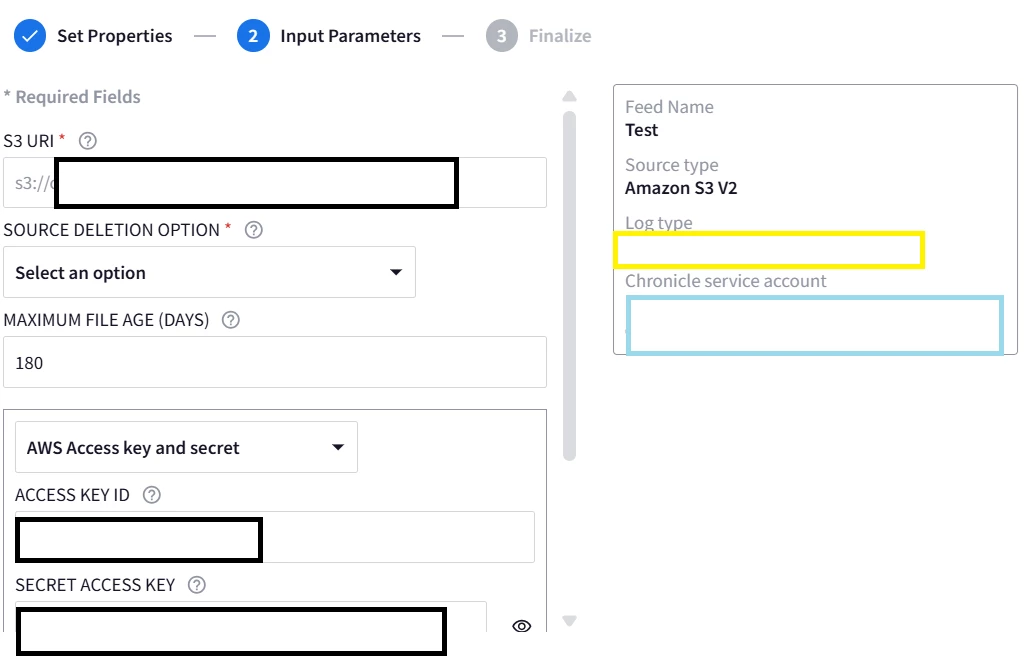
So I decided to have IOC feeds in S3 bucket and want to integrate this S3 bucket with chronicle SOAR to block the IP/URL/Hash automatically basis in SOAR actions.
Please help me how it can be achieved and share the reference article/MOP/video link.
Regards,
Brijesh Kumar