As a Splunk user I got used to the _index and being able to search on user activity and other events in Splunk.
I don’t see as a clear a path to search for Chronicle activity in Chronicle
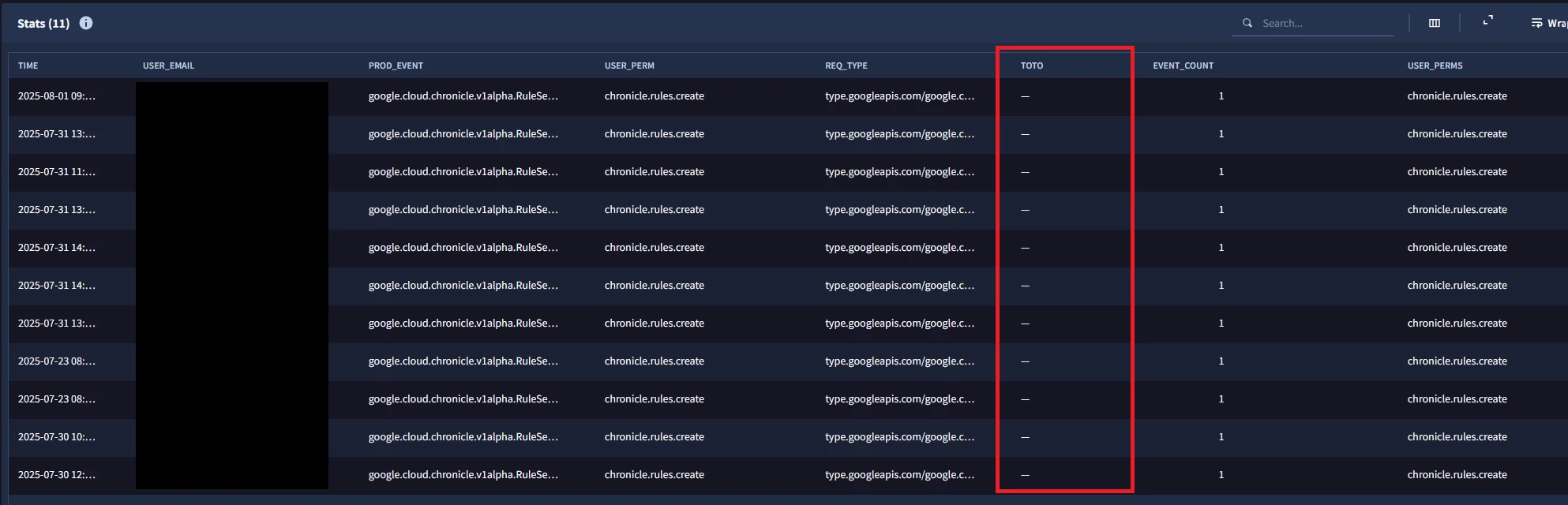
The following search is for a user creating a rule, but including the match fields shows no results even tho commenting them out does.
metadata.log_type = "GCP_CLOUDAUDIT"
target.application = "chronicle.googleapis.com"
principal.user.attribute.permissions.name = "chronicle.rules.create"
$time = timestamp.get_timestamp(metadata.event_timestamp.seconds)
$user_email = principal.user.email_addresses
$prod_event = metadata.product_event_type
$user_perm = principal.user.attribute.permissions.name
$req_type = target.resource.attribute.labels["request_type"]
// match:
// $time , $user_email , $prod_event , $user_perm , $req_type
//outcome:
// $event_count = count_distinct(metadata.id)
// $user_perms = array_distinct($user_perm)
I’m curious if other users monitor rule creation, edits using searches for managing and reporting rule creation.
...or manage their MSSP analysts using searches to see how the analysts are using searches.
thanks