I'm trying to parse ALIENVAULT_OTX I've used a python script that ingests the following log for each IOC:
id=4065110078|indicator=192.168.1.1|type=IPv4|description=|created=2025-05-02T20:25:08Z|content=and this is my custom parser:
filter {
mutate {
replace => {
"id" => "",
"indicator" => "",
"created" => "",
"description" => "",
"type" => "",
"content" => ""
}
}
kv {
source => "message"
field_split => "|"
value_split => "="
whitespace => "strict"
}
mutate {
replace => {
"event.idm.entity.metadata.vendor_name" => "AlienVault"
"event.idm.entity.metadata.product_name" => "ALIENVAULT_OTX"
}
}
date {
match => ["created", "ISO8601" ]
target => "event.idm.entity.metadata.interval.start_time"
on_error => "ts_not_found"
}
if [type] == "FileHash-SHA256" {
mutate {
replace => {
"event.idm.entity.metadata.entity_type" => "FILE"
"event.idm.entity.entity.file.sha256" => "%{indicator}"
}
}
} else if [type] == "FileHash-SHA1" {
mutate {
replace => {
"event.idm.entity.metadata.entity_type" => "FILE"
"event.idm.entity.entity.file.sha1" => "%{indicator}"
}
}
} else if [type] == "domain" {
mutate {
replace => {
"event.idm.entity.metadata.entity_type" => "DOMAIN_NAME"
"event.idm.entity.entity.hostname" => "%{indicator}"
}
}
} else if [type] == "FileHash-MD5" {
mutate {
replace => {
"event.idm.entity.metadata.entity_type" => "FILE"
"event.idm.entity.entity.file.md5" => "%{indicator}"
}
}
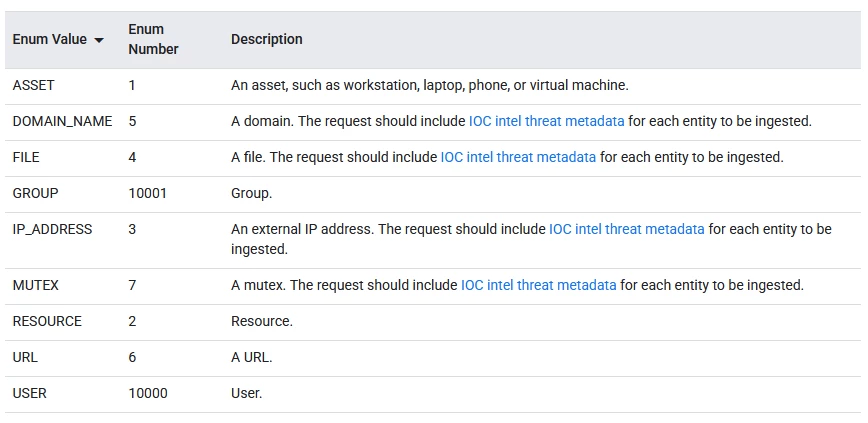
} else if [type] == "IPv4" and [indicator] != "" {
mutate {
replace => {
"event.idm.entity.metadata.entity_type" => "IP_ADDRESS"
}
}
if [event][idm][entity][metadata][entity_type] == "IP_ADDRESS" {
mutate {
merge => {
"event.idm.entity.entity.ip" => "indicator"
}
on_error => "indicator_empty"
}
mutate {
convert => {
"indicator" => "bytes"
}
on_error => "failed_to_convert_indicator"
}
mutate {
rename => {
"indicator" => "event.ioc.ip_and_ports.ip_address"
}
on_error => "indicator_not_found"
}
}
}
if [type] != "" {
mutate {
merge => {
"@output" => "event"
}
}
}
statedump{}
}And this is the error I'm receiving:
generic::unknown: invalid event 0: LOG_PARSING_GENERATED_INVALID_EVENT: "generic::invalid_argument: unknown or unset entity type"Can anyone please help me with this IP_ADDRESS mapping I'm assuming there is an unset value for my entity_type but I'm not sure what is it.