Hi everyone,
Yesterday I noticed that there could be a problem with our SIEM. I'll give you an example:
In curated detections, there is a rule to catch the command
cmd /c "echo hello_chronicle_world!"I've activated this rule to make some tests and noticed something weird.
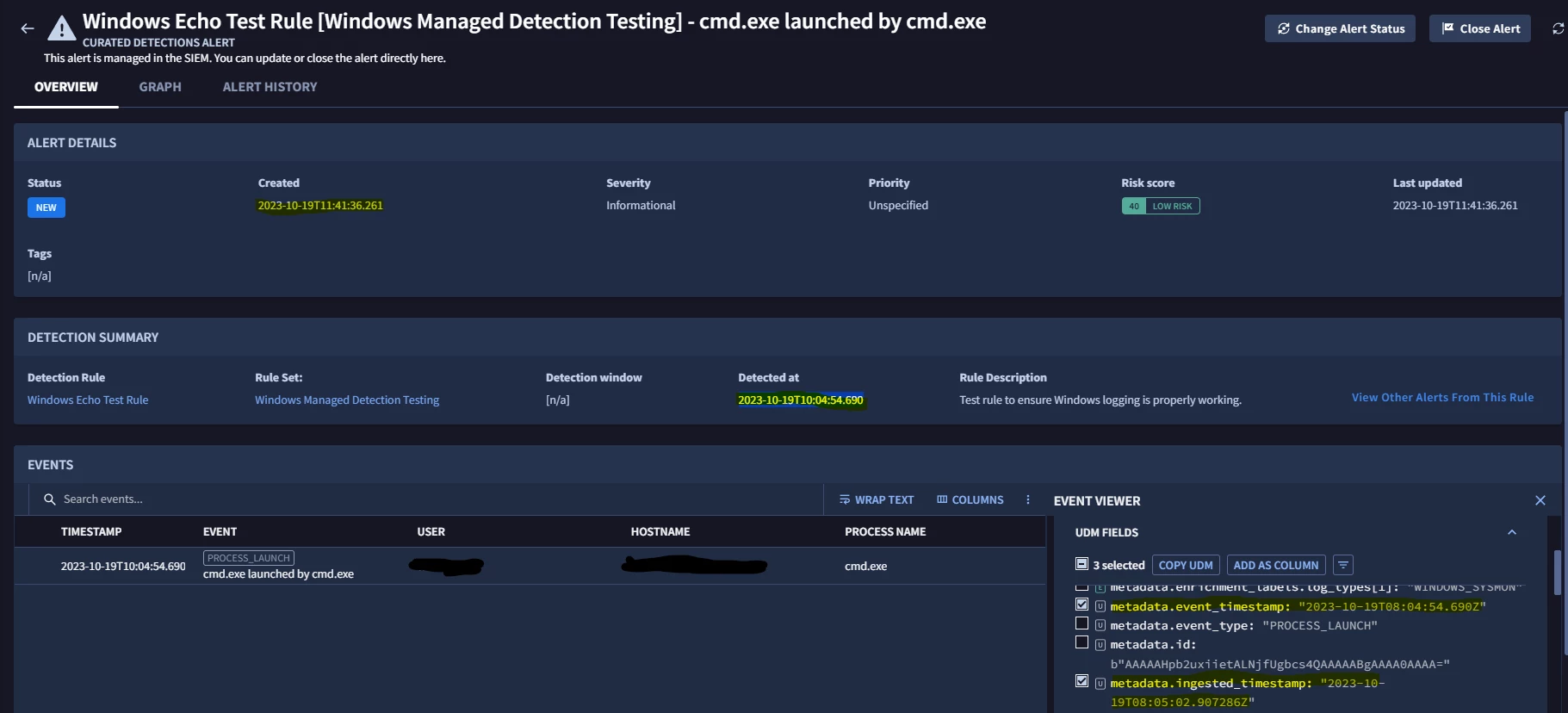
As you can see in the picture above there are four different timestamps:
metadata.event_timestamp THIS SHOULD BE THE TIMESTAMP AT WHICH THE EVENT IT'S BEEN GENERATED ON THE HOST
metadata.ingested_timestamp THIS SHOULD BE THE TIMESTAMP AT WHICH THE EVENT IT'S BEEN INGESTED IN CHRONICLE
Detected at THIS SHOULD BE THE TIMESTAMP AT WHICH THE DETECTION RULE DETECTED THE EVENT
Created FINALLY THIS SHOULD BE THE TIMESTAMP AT WHICH THE ALERT IT'S BEEN CREATED
If I'm right, why is there so much delay? The time between event creation and ingestion is minimal but there is 1 hour delay between ingestion and detection and then another hour from detection to alert generation.
I don't know if it could be related, the log type Is WINDOWS_SYSMON and all the logs of this type reach chronicle through chronicle forwarder for Linux.
I want also to specify that to be sure that the problem was not related to curated detections I've created a custom rule that matches the same things. The result is the same.
Thank you in advance.
A



