Hi
I am trying to convert the below KQL query to yara L but it does not seem to be working , can someone suggest where i am going wrong
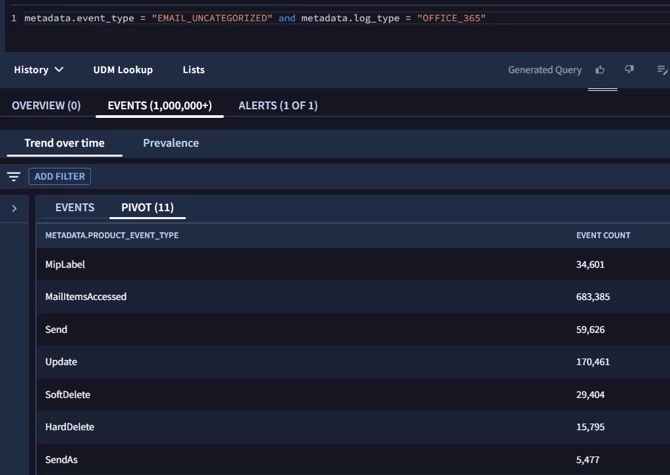
EmailEvents
| where TimeGenerated > ago(30d)
| where SenderFromDomain <> "XXXXX.com" or SenderFromDomain <> "XXXXXX.com"
| where LatestDeliveryLocation == "Inbox/folder"
| summarize EmailCount = count() by RecipientEmailAddress, bin(TimeGenerated, 180m)
| where EmailCount > 500
| project TimeGenerated, RecipientEmailAddress, EmailCount
YARA
rule WHS_High_Volume_of_Emails_from_Sender_Identifying_Potential_Spam_Activity
{
meta:
author = "ABC"
description = "Use-case detects when a user sends emails to an abnormally high amount of recipients."
severity = "Medium"
priority = "Medium"
mitre_tactic = "TA0042"
mitre_technique = "T1586.002"
events:
$event.metadata.log_type = "OFFICE_365"
$event.metadata.event_type = "EMAIL_UNCATEGORIZED"
$event.target.resource.name = "\\\\Inbox"
$event.network.email.mail_id != ""
re.capture ($event.network.email.from,"@(.*)") = $Domain
$sender = $event.network.email.from
$recipient= $event.network.email.to
//not $Domain in %Allowed_Domains
$threat_signature = strings.coalesce("High_Volume_of_Emails_from_Sender_Identifying_Potential_Spam_Activity", $event.security_result.threat_name, $event.additional.fields["signature"])
$targeted_host = strings.to_upper(strings.coalesce($event.target.hostname, $event.principal.hostname))
match:
$recipient over 3h
outcome:
$total_recipients = count($recipient)
$risk_score = max(60)
$threat_signature_list = array_distinct($threat_signature)
$activity_outcome_list = max(
if(any $event.security_result.action = "ALLOW" or any $event.security_result.action = "ALLOW_WITH_MODIFICATION" or any $event.security_result.action = "FAIL" or any $event.security_result.action = "UNKNOWN_ACTION" , 1, 0)
+ if(any $event.security_result.action = "BLOCK" or any $event.security_result.action = "QUARANTINE" or any $event.security_result.action = "CHALLENGE" , 2, 0)
)
$total_log_count = count_distinct($event.metadata.id)
condition:
#event > 500
}
@jstoner : Any assistance would be of great help