Hi Team,
In one of my widget query i was referencing a data table and i can see the required output.
This is my dashboard widget query,
metadata.log_type = /Fortinet/ nocase
principal.ip != ""
target.ip != ""
not principal.ip in %Private_IP_Ranges.cidr
match: security_result.action,principal.ip,principal.port,principal.ip_geo_artifact.location.country_or_region,target.ip,target.port,target.ip_geo_artifact.location.country_or_region,target.application,network.sent_bytes,network.received_bytes
outcome:
$event_time = timestamp.get_timestamp(max(metadata.event_timestamp.seconds), "%F %T", "GMT")
limit:
10000
after saving the query when i try to apply global filter i am unable to select my widget (it is greyed out)
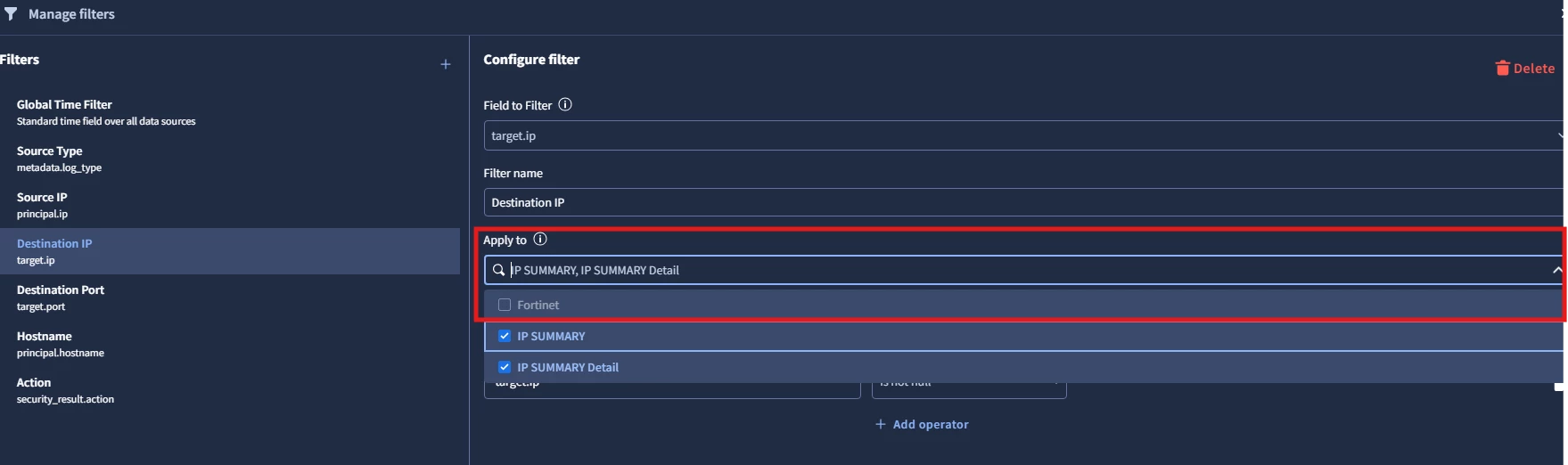
But when i dont reference a data table in the query i am able to add filter.
Just wondering if it is a limitation that dashboards has ?




