Hello,
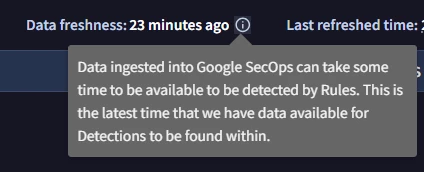
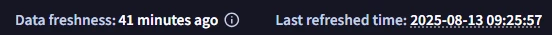
An associate of mine ran a SIEM search and got 4 results. They then ran a test of a YARA-L rule with the same logic and got 2 of those 4 results. 10 minutes later it showed 3 of the results. 30 minutes later it showed all 4 results. Is there a known lag when using the “RUN TEST” feature in the Detection Rules?
The logic used to search was straightforward -- just filtering on 4 UDM fields. No match section.
Thanks,
Eric