Hi,
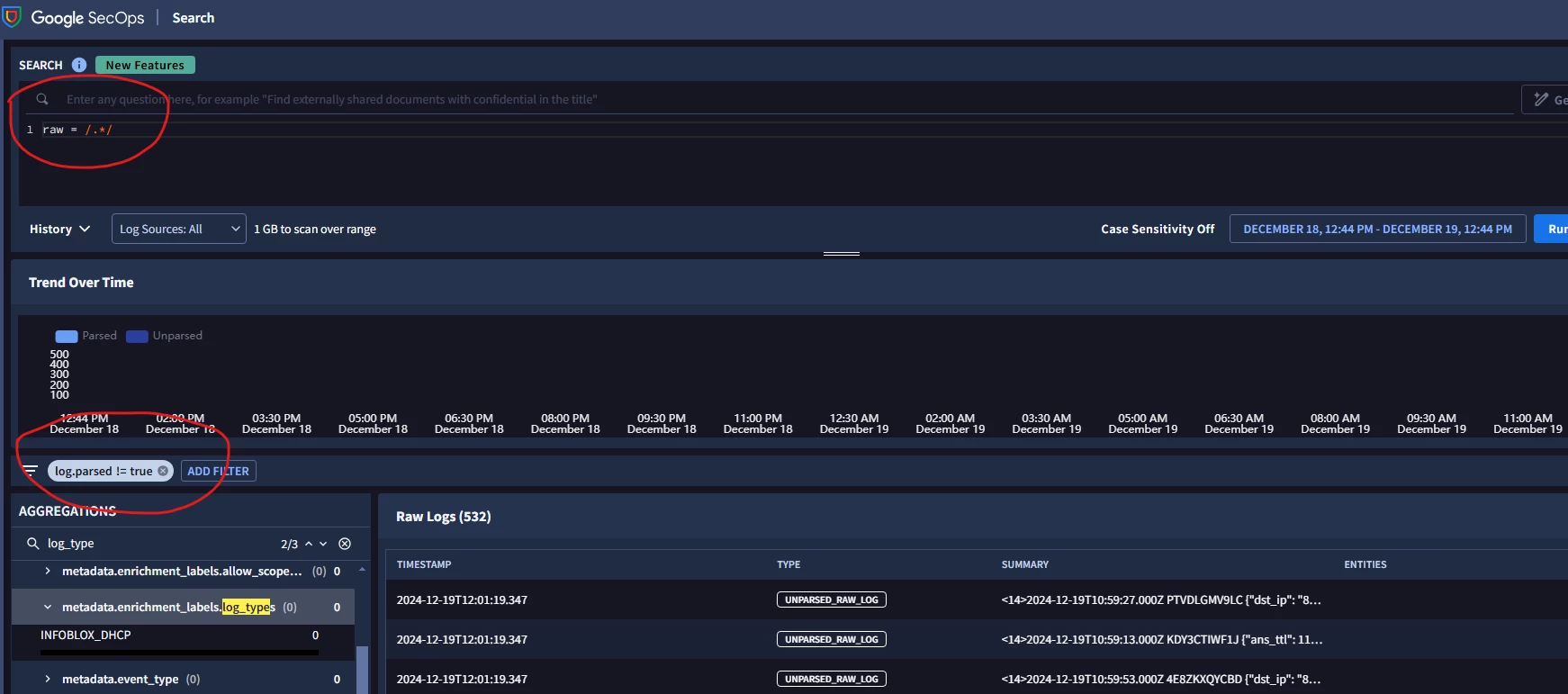
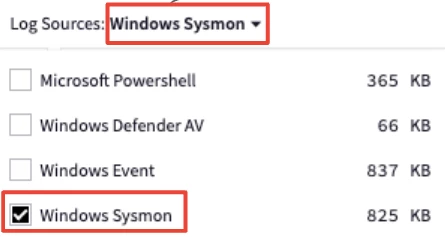
What is the best way to field unparsed events ingested in SecOps SIEM without it being a pain. I have so far been searching for raw log with regex and using Procedural Filtering for individual log source until I collect few hundreds and then try to work on parser extension. This has been painful and a lot of manual task and chances of missing unparsed event is high for us (considering the volume of data we ingest and search result capping the returned events to x result (10,000 default)
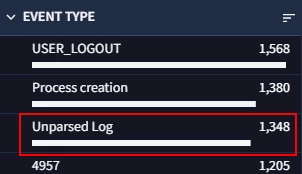
I believe there should be a way for searching for just unparsed logs so that we have better visibility of what we are missing out on.