I took a quick look through the github repo and the only one that I found that matched the names on the list is community/microsoft/windows/port_proxy_forwarding_T1090_cisa_report.yaral.
That one is built based on the reference material cited from the CISA report and sections of the rule are commented that cover opportunities to tune and tweak the rule. The community rules are intended to be a starting point and it is assumed that they will require tuning for the specific environment they are deployed in.
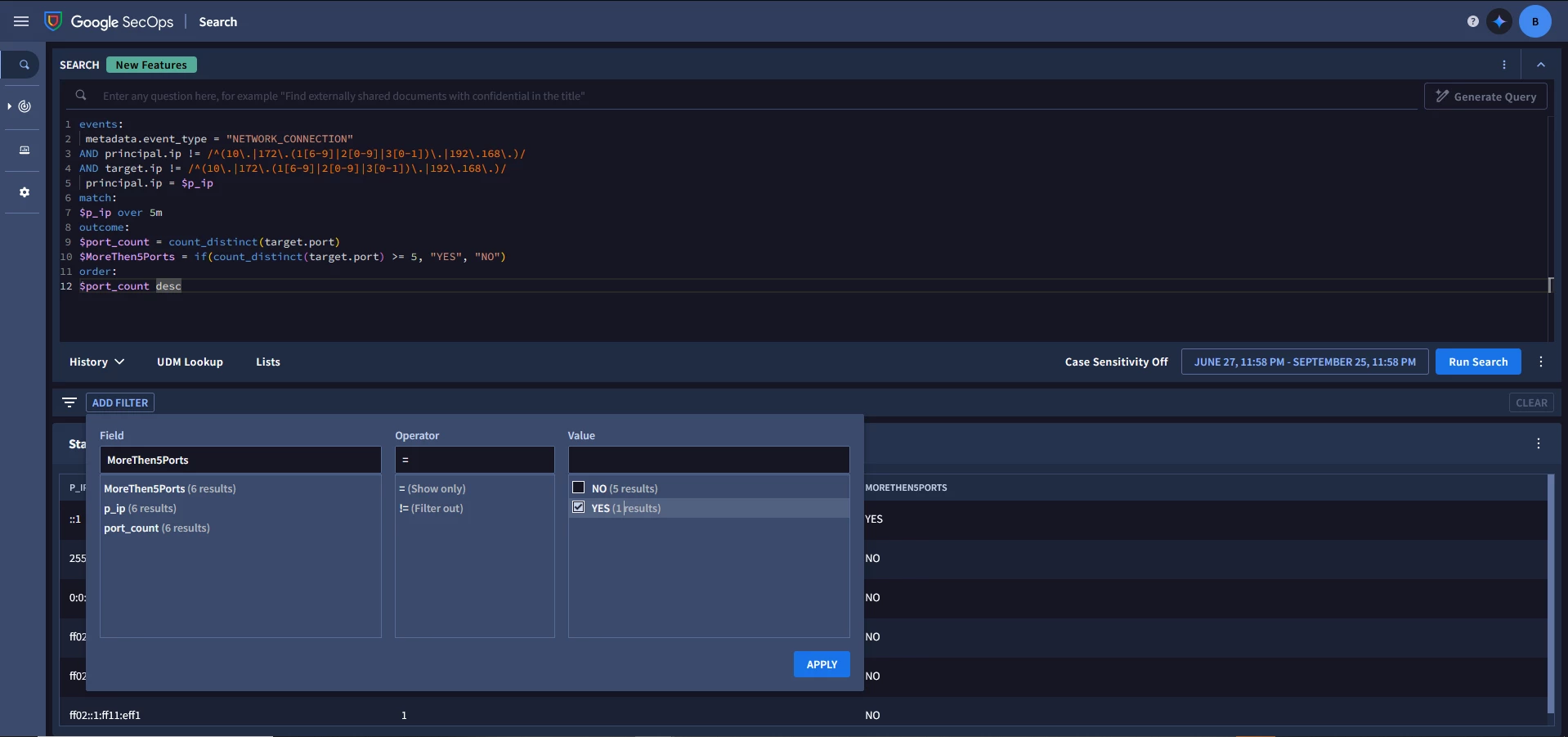
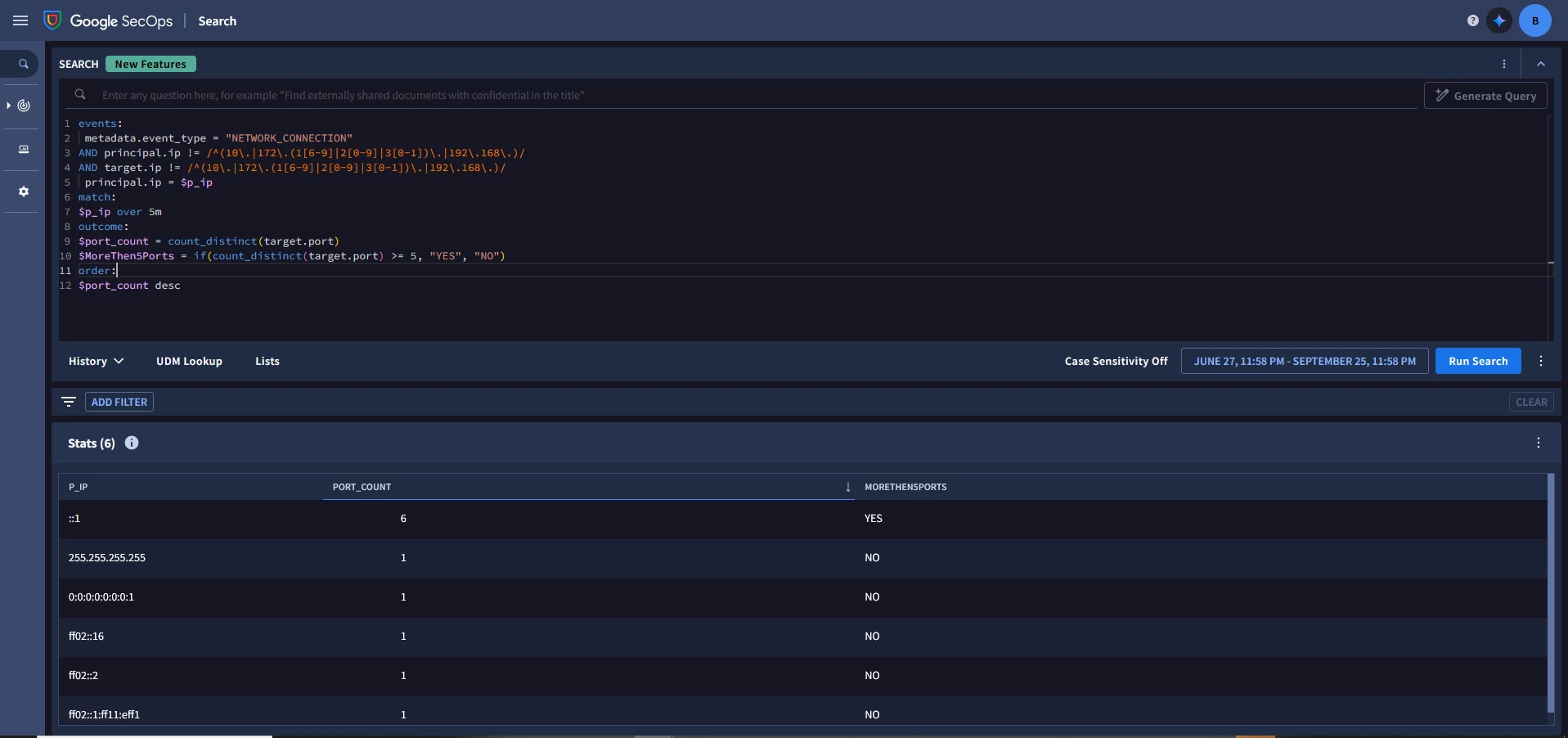
I pulled this example rule together for excessive port scanning that I think is a decent start for that use case though additional tuning may be required.
This example has IP netblocks for 10.0.0.0/8 defined as start and end so this would be internal scan activities but could be adapted to external to internal by adding a NOT to the principal.ip netblock (assuming the 10 block is the internal block of interest).
It's worth mentioning that if you are looking for ext to int scans that principal hostname likely won't exist for those systems so using IP address for external scans might be better. I mocked up an IP to IP example and commented it out as well as a match statement. You could also mix and match ip and hostname if you want.
Finally, we are using the outcome section to generate a count of the distinct ports seen in our 5 min match window and then using a threshold in the condition section to look for more than 50 distinct ports in that 5 min window. That number is something you will need to tune based on the kind of scan you are looking to detect. An nmap generic scan gave me 1001 ports in that window but that could vary.
Depending upon the data sets you have, there may be other rules that could pick this up too. For example my suricata rules fired when i ran the nmap for this example and I could write a rule against that to detect scanning activity perhaps. I also had a bunch of NETWORK_UNCATEGORIZED activity that touched a large number of ports as well so that might be another event type i might throw into this rule (separated with an OR) to broaden my rule if needed.
rule excessive_port_activity {
meta:
author = "Google Cloud Security"
description = "Detects excessive (defined by number of distinct ports logged) between the same hosts within an internal network within a designated time window"
type = "alert"
data_source = "gcp, corelight"
severity = "Low"
priority = "Low"
events:
$net.metadata.event_type = "NETWORK_CONNECTION"
//following two lines focus that this scan is happening internal to internal
net.ip_in_range_cidr($net.target.ip, "10.0.0.0/8")
net.ip_in_range_cidr($net.principal.ip, "10.0.0.0/8")
//looking for specific combination of target and principal hostname for scan
$net.principal.hostname = $p_host
$net.target.hostname = $t_host
//alternatively, looking for specific combination of target and principal IP for scan - if external scan, principal will not have a hostname
//$net.principal.ip = $p_ip
//$net.target.ip = $t_ip
match:
$p_host, $t_host over 5m
//$p_ip, $t_ip over 5m
outcome:
$port_count = count_distinct($net.target.port)
condition:
$net and $port_count > 50
}