In this post, I'd like to show you one of the cool capabilities of Gemini in Google SecOps!
We recently hosted a webinar on May 14th here in the Google Cloud Security Community where we did a deep dive into the Gemini functionality in Google SecOps. In this webinar, we covered a number of different use cases, one of which was using Gemini for researching threat actors and building out associated search queries that help us look for events in our environment related to these threat actors. In this post, I'd like to show you one of these use cases in the form of a community post.
Let's take a real-world use case and apply it to Gemini in Google SecOps. On May 6, a new blog post was published on the Google Cloud Threat Intelligence blog that delves into UNC3944. From the blog, we learn that this threat actor (or group of threat actors) is financially-motivated and targets multiple business sectors. UNC3944 uses a number of tactics like deploying ransomware or using social engineering against victims.
As users of the Google SecOps platform, we might be interested in researching UNC3944 in the context of our environment to see if we have any active indicators of compromise. Without Google SecOps, this might involve setting up a threat intelligence feed outside of the SIEM platform, or copying and pasting indicators of compromise found online into a search passed to a SIEM. What if we could simplify this workflow with the power of Gemini?
Gemini is globally available in Google SecOps. Requests are routed to the closest of three regions for processing. You can read a few other general notes about Gemini in SecOps on the official documentation page. We can start a chat session with Gemini by opening the Gemini Pane on the top right of the screen.
Let's dive into our use case.
Since we're researching the threat actor UNC3944, we'd like to have a quick way to verify whether we have IOC hits in the environment without manually cross-referencing those indicators. After opening the Gemini Pane, we have the option to use a template question or write our own. In this example we'll write our own question.
Let's try this with the following query: Is UNC3944 active in my environment?
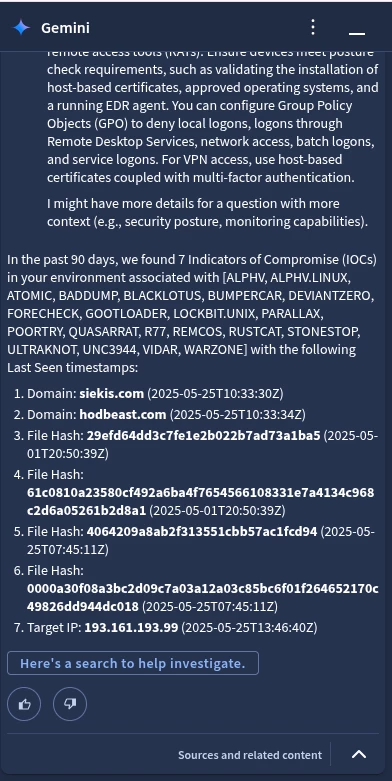
We see that Gemini takes some time to respond, and eventually returns a wealth of information related to UNC3944. This includes a summary of the threat intelligence related to this threat actor and the associated taxonomy (like related names that the threat actors goes by and names of the malware used).
Gemini also goes further and tells us that we have IOCs in the environment that are associated with UNC3944. It has already looked up the IOCs for us and has provided a useful search that we can pass directly into the SIEM Search to get events back.
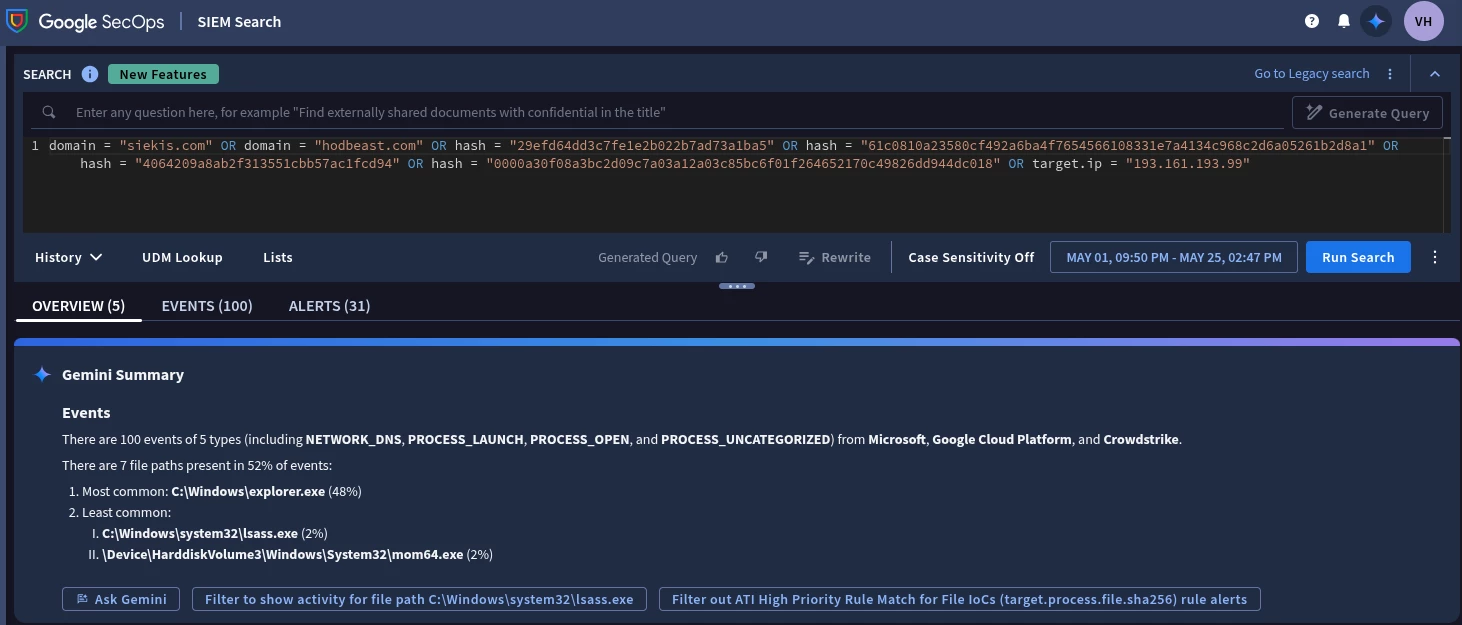
We can click the button that says "Here's a search to help investigate" to pivot to SIEM Search, which lets us run the query that Gemini provided. By running it we see that we get 100 events back and also a Gemini Summary widget to go along with it. The same details in the Gemini Summary widget are also reflected back in the Gemini chat pane.
Can you come up with some additional examples of queries related to threat intelligence that you found useful when using Gemini in Google SecOps? Let us know if you do!


