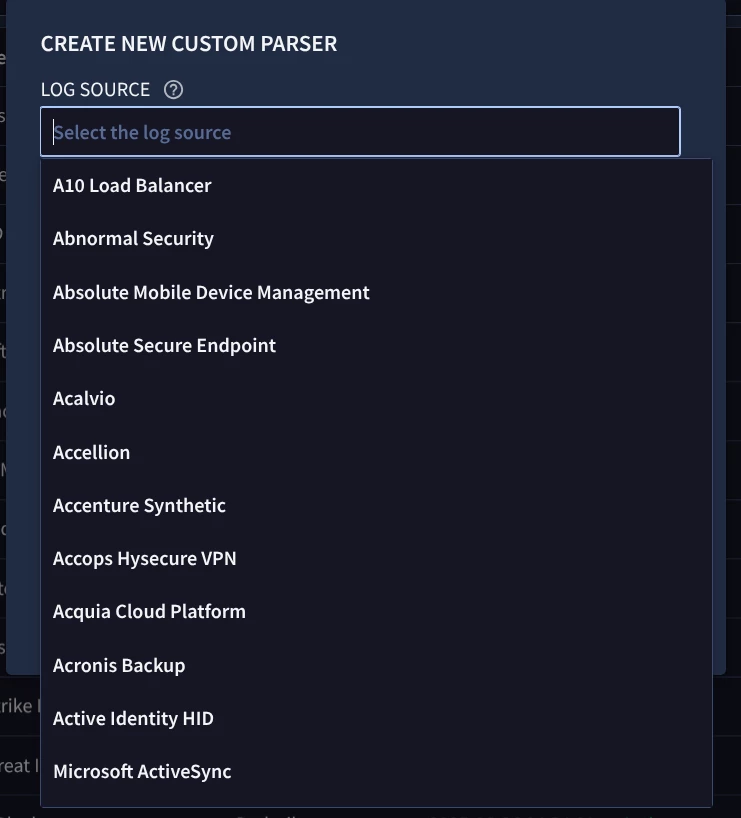
I have written a Generic JSON parser in Google SecOps and it works well when I paste test data and click on PREVIEW. The parser passes validation too.
However, I notice when I send data into Google SecOps SIEM, the parser doesn’t seem to be doing anything (we use Bindplane). This is because I have Alert rules created and no alerts are being raised.
We are sending custom JSON objects through Bindplane. My guess is it’s the ingestion label that is wrong (it’s currently set to SPLUNK using Bindplane Google SecOps Standardization Processor).
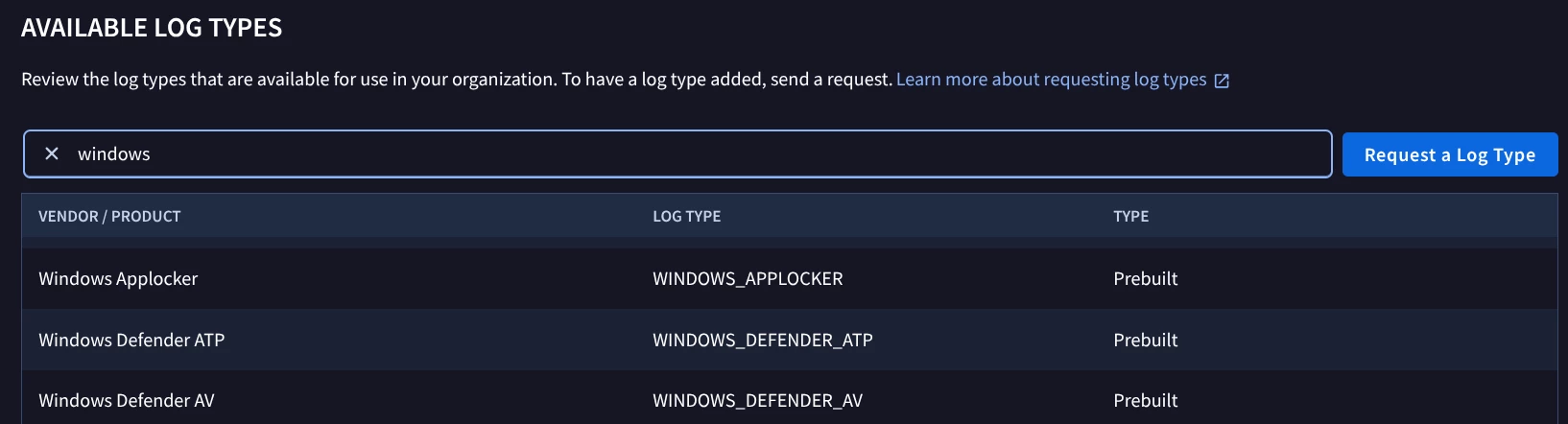
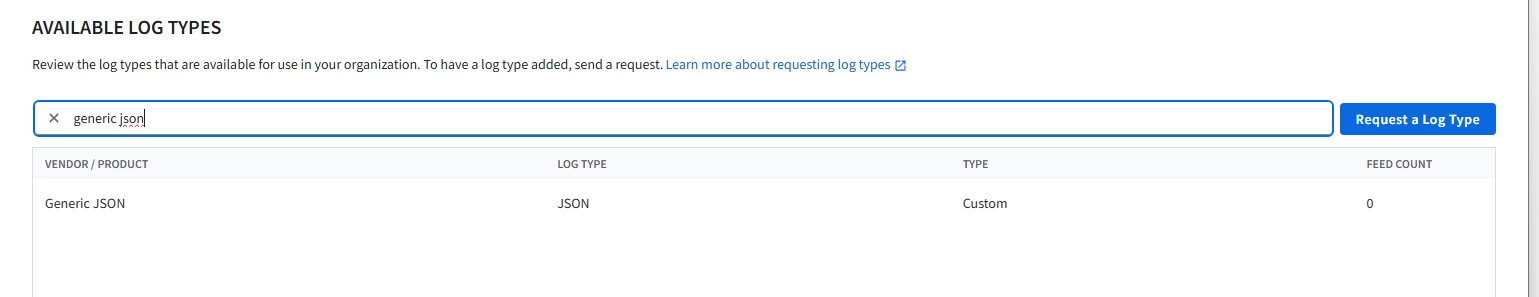
I have looked at https://cloud.google.com/chronicle/docs/ingestion/parser-list/supported-default-parsers and I do not see any ingestion label for “Generic JSON” - hence I do not know what to set the “log_type" field to in Bindplane’s Google SecOps Standardization Processor. But what confuses me is that when I choose to create a custom parser, I do have a “Generic JSON” in the drop down list in the SecOps UI.
So how can I achieve what I require?