Gemini CLI was launched this morning and I'm excited to share ways to use it with the MCP Servers for Google Cloud Security.
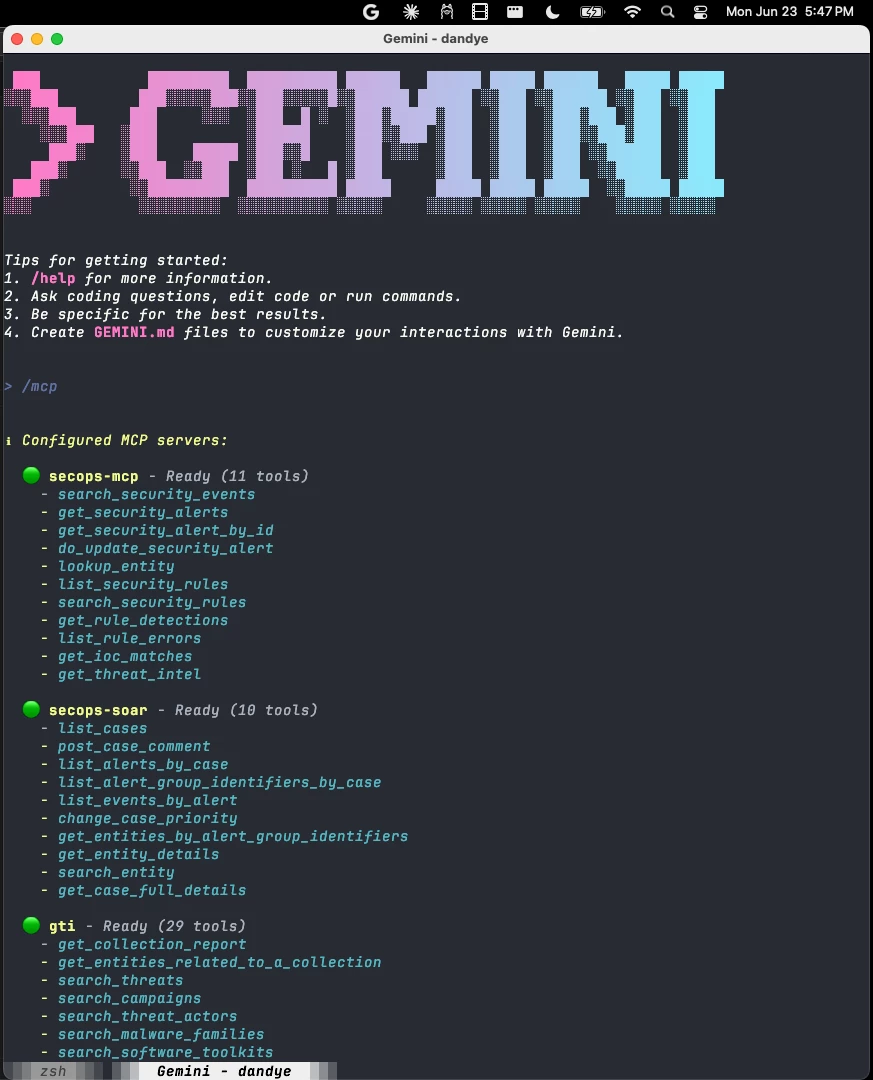
Configuration
MCP Servers in Gemini CLI are configured using the same JSON that we describe in MCP Server Configuration Reference. The mcpServers key is at the top-level along with the theme and selectedAuthType keys:
❯ head ~/.gemini/settings.json
{
"selectedAuthType": "gemini-api-key",
"theme": "Dracula",
"mcpServers": {
"secops-mcp": {
"command": "/Users/dandye/homebrew/bin/uv",
...
But I think everyone’s first question is, “Why would you want to use the command line?”
Imagine running a complex task like "Execute the Malware Incident Response Plan for SOAR Case 17347" by piping that prompt into the Gemini CLI:
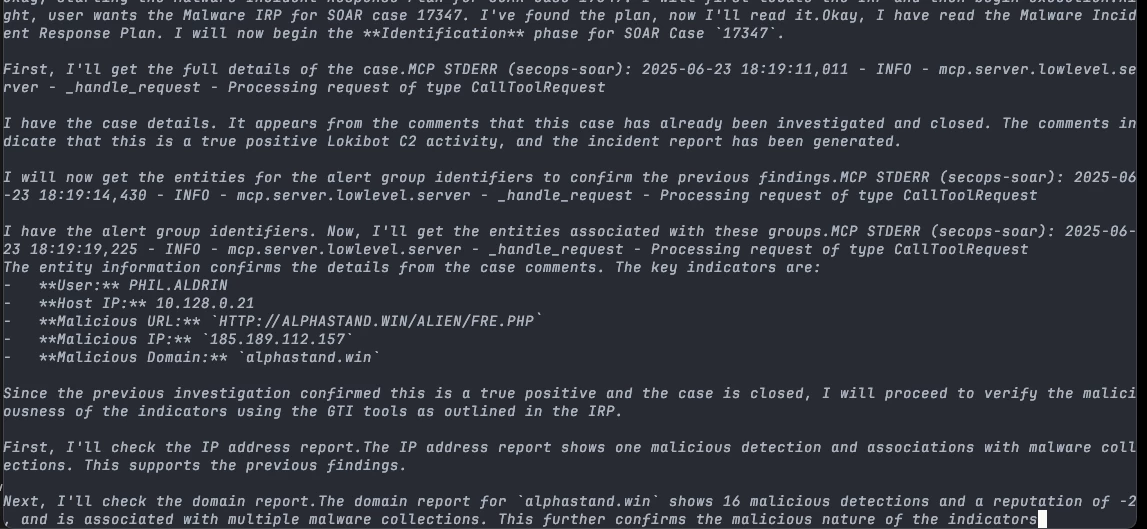
How does Gemini understand and act on a multi-step command like this? Actions are made possible by the MCP Servers, which use the APIs for Google SecOps, Google Threat Intelligence, and Security Command Center. The multi-step workflows, like incident response plans, are defined by runbooks stored in the .gemini directory, which are always in context.
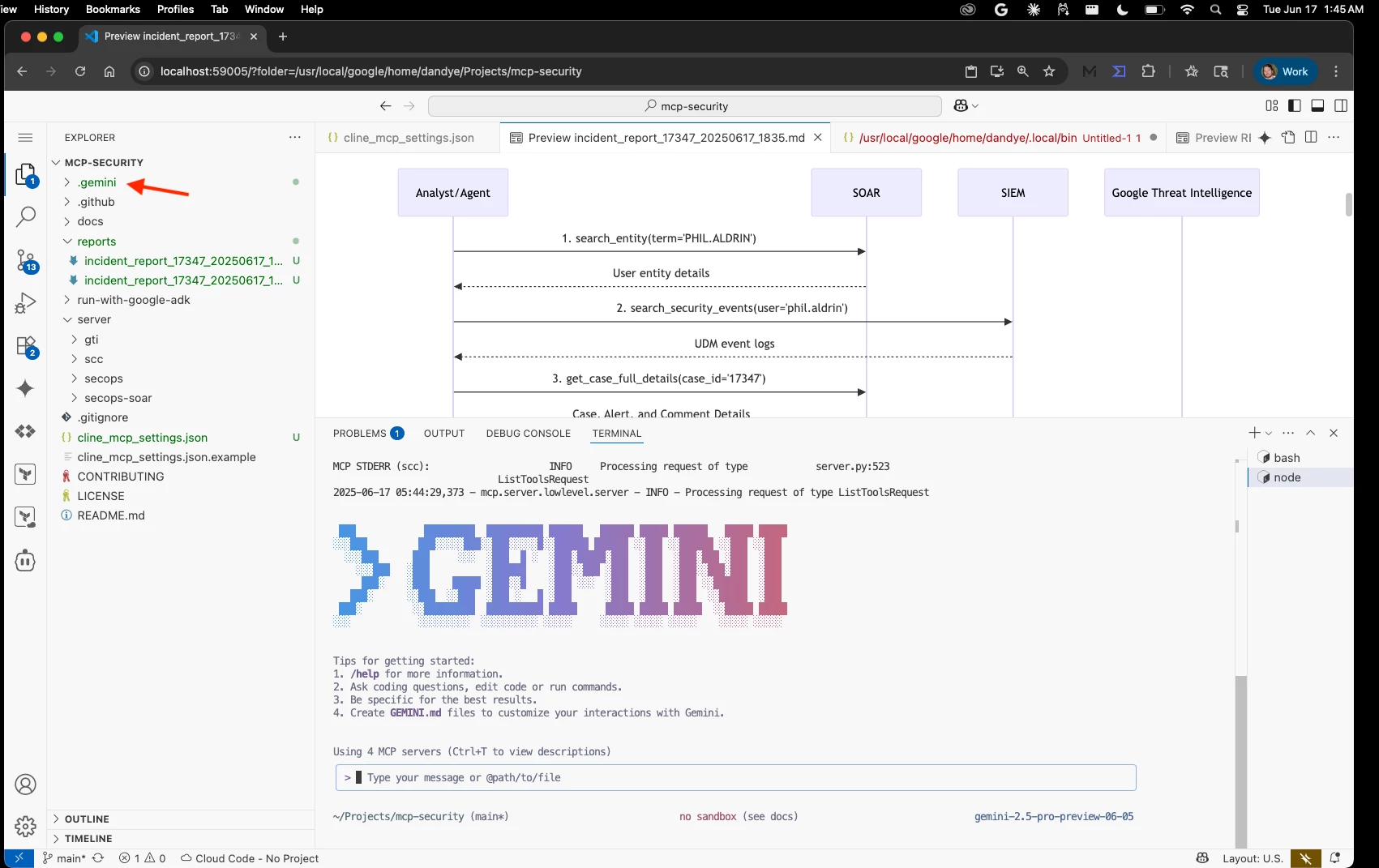
These runbooks provide the context and instructions necessary for Gemini to interpret and act on more complicated, multi-step instructions.
Gemini CLI + Google Cloud Security MCP Servers + Runbooks = an agentic command line that performs Security Operations tasks. You can pipe in, pipe out, cron, and even run continuous integration. CLI FTW!



