Hi Guys,
We tried to create a detection rule using the following document for Detect silent hosts by hostname.
https://docs.cloud.google.com/chronicle/docs/ingestion/silent-host-monitoring
We have customized the query and make the following query.
rule Silent_Host_Detection {
meta:
description = "Detects hosts that have stopped sending logs for 5 minutes or more"
severity = "Medium"
category = "Host Monitoring"
events:
// Track events from the specific host in the last 60 minutes (scanning window)
$event.metadata.event_timestamp.seconds > timestamp.current_seconds() - 3600
$silent_hostname = $event.principal.hostname
$silent_hostname = "secops-local-testing-02"
match:
// Group by hostname over 60 minutes
$silent_hostname over 60m
outcome:
// Calculate the time difference in the outcome section
$max_event_time = max($event.metadata.event_timestamp.seconds)
$max_diff = timestamp.current_seconds() - $max_event_time
$hostname = array_distinct($silent_hostname)
$last_seen = $max_event_time
$severity = "Medium"
$description = "Host has stopped sending logs for 5+ minutes"
condition:
// Use the outcome variable in condition (5 minutes = 300 seconds)
$event and $max_diff > 300
}
We also set the run frequency as 1 hour.
After that we enabled the rule and started our test VM at 3:20 PM (Local Time) and a fake log generator to generate some fake logs. After that we turned off the VM at 5:05 PM (Local Time). when we check in the SecOps.
- We have noticed a alert is generated at 4:30 ( Rule running Window 3:30 PM to 4:30 PM) even though their are logs in Google SecOps
- But we did not see any alert for the rule running window 4:30 PM to 5:30PM even though their is no logs been ingested to google SecOps after 5:05 PM.
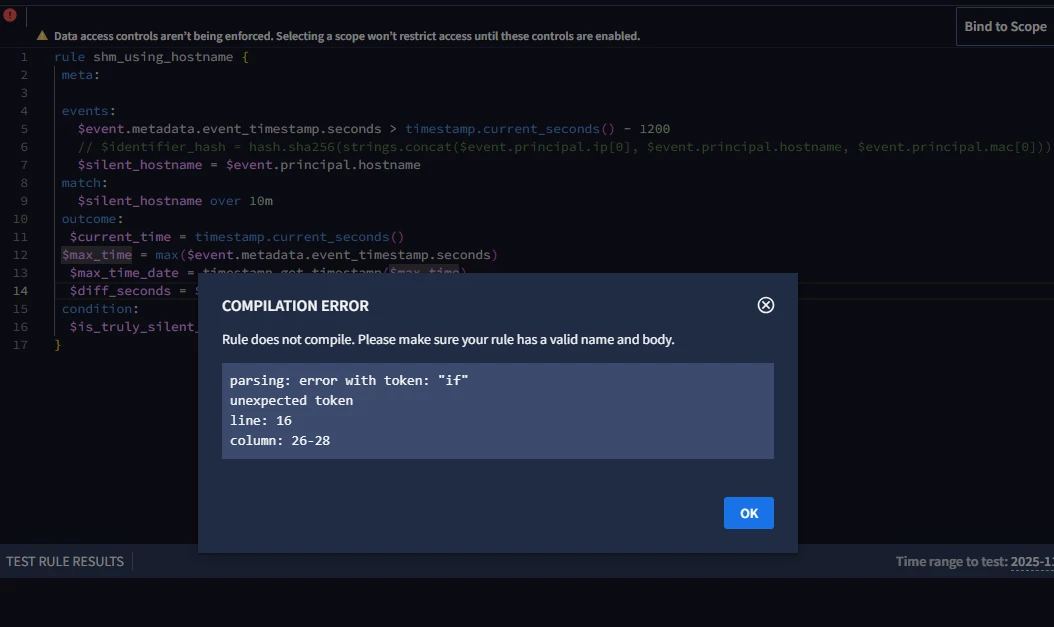
Please help me fix the issue we are facing.
Thank in Advanced.