Hi, hope you are doing great!
I am asking this question because I found that some of the Sysmon event logs I am ingesting to Google SecOps are not being all parsed. This is a particular concern for me because Sysmon is a great source of events in Windows environments, and the Sysmon parsers is supposed to be a Built-in Golden Parser, which means it should be always updated.
Here is a video were I am showing the situation.
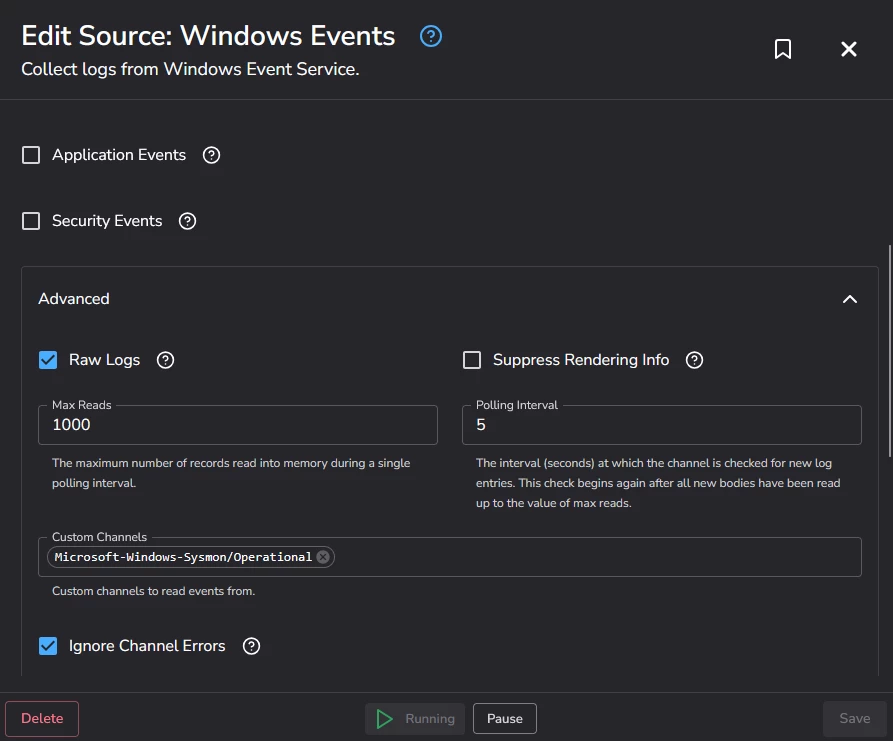
Regarding the context of the ingestion pipeline, I am testing a combination of centralized ingestion using Windows Event Forwarding and a few agents in the Windows Event Collectors. The ingestion is succeeding because I can query the raw event logs in the SIEM search, however, I may be doing something wrong or missing a limitation about the Golden Parsers that I should be aware of.
I tried also to compare two events. The following event was successfully parsed:
<Event xmlns='http://schemas.microsoft.com/win/2004/08/events/event'>
<System>
<Provider Name='Microsoft-Windows-Sysmon' Guid='{5770385f-c22a-43e0-bf4c-06f5698ffbd9}'/>
<EventID>
5
</EventID>
<Version>
3
</Version>
<Level>
4
</Level>
<Task>
5
</Task>
<Opcode>
0
</Opcode>
<Keywords>
0x8000000000000000
</Keywords>
<TimeCreated SystemTime='2025-05-12T00:30:27.6459103Z'/>
<EventRecordID>
8406
</EventRecordID>
<Correlation/>
<Execution ProcessID='360' ThreadID='4760'/>
<Channel>
Microsoft-Windows-Sysmon/Operational
</Channel>
<Computer>
WS-001.lab.ajrc.dev
</Computer>
<Security UserID='S-1-5-18'/>
</System>
<EventData>
<Data Name='RuleName'>
-
</Data>
<Data Name='UtcTime'>
2025-05-12 00:30:27.636
</Data>
<Data Name='ProcessGuid'>
{3b1ba004-411e-6821-f907-000000000800}
</Data>
<Data Name='ProcessId'>
7196
</Data>
<Data Name='Image'>
C:\\Windows\\System32\\notepad.exe
</Data>
<Data Name='User'>
LAB\\a.rodriguez
</Data>
</EventData>
<RenderingInfo Culture='en-US'>
<Message>
Process terminated:
RuleName: -
UtcTime: 2025-05-12 00:30:27.636
ProcessGuid: {3b1ba004-411e-6821-f907-000000000800}
ProcessId: 7196
Image: C:\\Windows\\System32\\notepad.exe
User: LAB\\a.rodriguez
</Message>
<Level>
Information
</Level>
<Task>
Process terminated (rule: ProcessTerminate)
</Task>
<Opcode>
Info
</Opcode>
<Channel>
</Channel>
<Provider>
</Provider>
<Keywords>
</Keywords>
</RenderingInfo>
</Event>
The next example wasn't parsed at all:
<Event xmlns='http://schemas.microsoft.com/win/2004/08/events/event'>
<System>
<Provider Name='Microsoft-Windows-Sysmon' Guid='{5770385f-c22a-43e0-bf4c-06f5698ffbd9}'/>
<EventID>
1
</EventID>
<Version>
5
</Version>
<Level>
4
</Level>
<Task>
1
</Task>
<Opcode>
0
</Opcode>
<Keywords>
0x8000000000000000
</Keywords>
<TimeCreated SystemTime='2025-05-12T00:30:35.5766940Z'/>
<EventRecordID>
17773
</EventRecordID>
<Correlation/>
<Execution ProcessID='3280' ThreadID='4624'/>
<Channel>
Microsoft-Windows-Sysmon/Operational
</Channel>
<Computer>
AD-AJRC.lab.ajrc.dev
</Computer>
<Security UserID='S-1-5-18'/>
</System>
<EventData>
<Data Name='RuleName'>
-
</Data>
<Data Name='UtcTime'>
2025-05-12 00:30:35.559
</Data>
<Data Name='ProcessGuid'>
{3bb234eb-412b-6821-5e13-000000000700}
</Data>
<Data Name='ProcessId'>
6376
</Data>
<Data Name='Image'>
C:\\Windows\\System32\\notepad.exe
</Data>
<Data Name='FileVersion'>
10.0.20348.1 (WinBuild.160101.0800)
</Data>
<Data Name='Description'>
Notepad
</Data>
<Data Name='Product'>
Microsoft® Windows® Operating System
</Data>
<Data Name='Company'>
Microsoft Corporation
</Data>
<Data Name='OriginalFileName'>
NOTEPAD.EXE
</Data>
<Data Name='CommandLine'>
"C:\\Windows\\system32\\NOTEPAD.EXE" \\\\AD-AJRC.lab.ajrc.dev\\Active Directory File Share\\Test File.txt
</Data>
<Data Name='CurrentDirectory'>
\\\\AD-AJRC.lab.ajrc.dev\\Active Directory File Share\\
</Data>
<Data Name='User'>
LAB\\Administrator
</Data>
<Data Name='LogonGuid'>
{3bb234eb-21ea-681c-6f6f-0b0000000000}
</Data>
<Data Name='LogonId'>
0xb6f6f
</Data>
<Data Name='TerminalSessionId'>
3
</Data>
<Data Name='IntegrityLevel'>
High
</Data>
<Data Name='Hashes'>
...
<Data Name='ParentProcessGuid'>
{3bb234eb-005b-6821-3012-000000000700}
</Data>
<Data Name='ParentProcessId'>
5540
</Data>
<Data Name='ParentImage'>
C:\\Windows\\explorer.exe
</Data>
<Data Name='ParentCommandLine'>
C:\\Windows\\explorer.exe /NoUACCheck
</Data>
<Data Name='ParentUser'>
LAB\\Administrator
</Data>
</EventData>
Both events appear to not have major syntactic differences, however, the first event was parsed while the second not. I could only find the second by using the raw search feature.
Something I try often but I am not sure if its reliable is using the parser extension option to verify if the parser is indeed working. I showed this in the video I mentioned before at the minute 1:25:00. I am confused because in the parser extension I have the option to preview the UDM output which actually succeeded.
If you could help me resolve this inquiry I would be very glad.
Thank you very much.