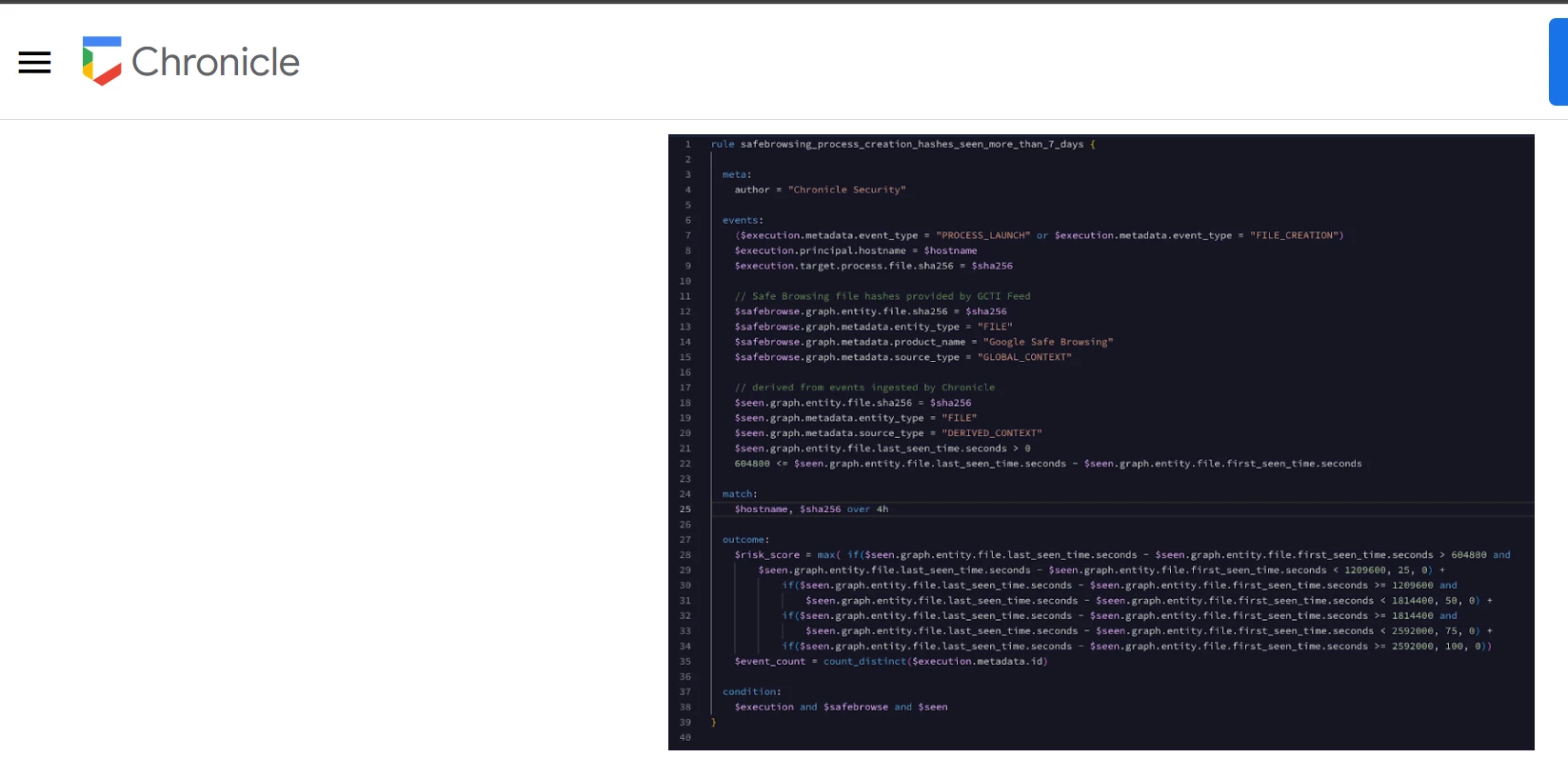
Hi @jstoner
I would like to create a YARA rule for the below condition " Discovers previously inactive accounts that are now being used. User account not logged in last 90 days and suddenly become active today".
Query i build so far is this ,however its not helping me to reach the desired result . I understand we need to save last 2 logs and compare the difference but how can we do that in YARA since we can export the value to a lookup. For testing purpose i have given 5 days and not 90 days.
rule Inactive_Account {
meta:
author = "Rahul"
description = "Discovers previously inactive accounts ."
severity = "Medium"
events:
$login.metadata.event_type = "USER_LOGIN"
$login.metadata.vendor_name ="Microsoft"
$login.metadata.product_event_type = "4624"
$login.security_result.action = "ALLOW"
$login.target.user.userid != /.*\\$/ nocase
$login.target.user.userid = $user
$login.principal.hostname =$host
match:
$user,$host over 24h
outcome:
$last_event = max($login.metadata.event_timestamp.seconds)
$inactive_time= (timestamp.current_seconds() - $last_event)
condition:
$login and $inactive_time > 432000
}
i do have the Splunk query for the same